Dark Peep #11: The Final Curtain for LockBit Ransomware (Operation Cronos)
Digital Olympians and seekers of cyber lore! “Dark Peep #11” unfurls its scroll to reveal tales of cunning, courage, and chaos in the digital Olympus, where modern-day Titans clash not with thunder but with code.
In this chapter, we witness the epic fall of LockBit, akin to a titan dethroned, brought low by the combined might of international cyber deities. Their realm? Not Olympus, but the shadowy valleys of the internet, where allegiances shift quicker than the winds of Aeolus.

Fig.1. An Illustration of Operation Cronos (generated using OpenAI’s DALL-E)
Witness the intrigue of The Five Families and Knight Ransomware, a drama that echoes the discord of Olympian factions, yet here, the thunderbolts are forged from malicious code, and the olive branches are offers of uneasy alliances quickly retracted.
In “Dark Peep #11,” each line of code is a thread in the tapestry of digital mythology. Prepare to navigate the labyrinth; the journey is perilous, but the tales are legendary.
Hunter X Hunted: The Takedown of LockBit by International Law Enforcement
In our latest installment, Dark Peep #11, we continue the intricate cyber narrative previously unfolded in Dark Peep #10, where we witnessed the dramatic banishment of LockBit ransomware from the prestigious XSS and Exploit forums, a staple of the Russian-speaking Deep/Dark web community. The tension escalated when LockBit audaciously announced a bounty for information on the XSS admin, leading to a tense standoff that felt ripped straight from a high-stakes cyber-thriller.
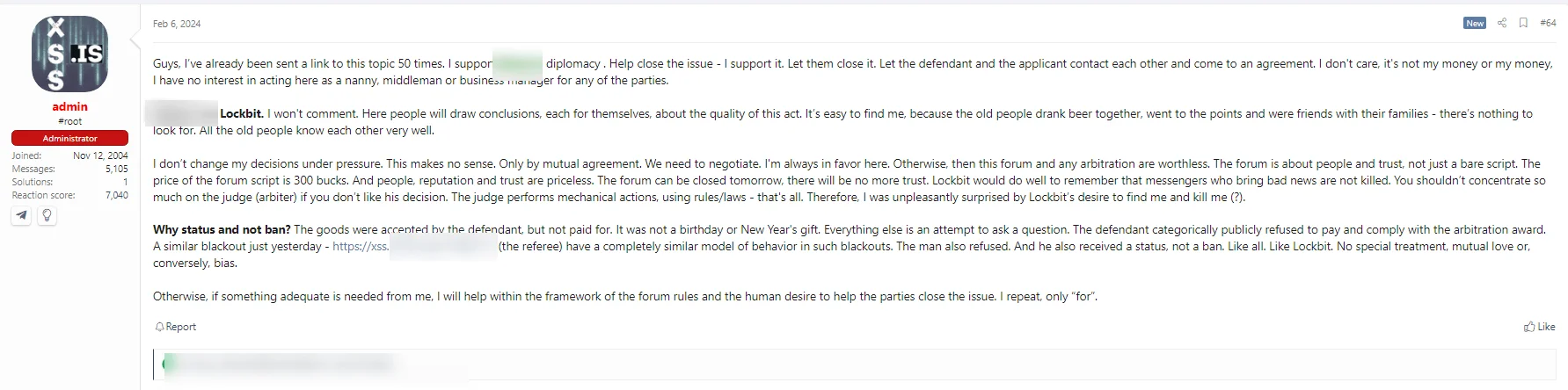
Fig. 2. XSS admin’s forum post about LockBit
The plot thickened as the XSS admin responded with a post hinting at LockBit’s ominous intentions towards him, adding a layer of intrigue and danger to the unfolding drama. Against this backdrop of threats, a sudden, unexpected twist occurred—a cameo scene, if you will, that seized everyone’s attention and redirected the storyline.
On February 20, Operation Cronos burst onto the scene in a coordinated effort by law enforcement across 11 countries, striking a decisive blow against the notorious LockBit ransomware operation. In collaboration with the FBI and other global partners, this international initiative saw the UK National Crime Agency seizing the reins of LockBit’s data exfiltration platform, akin to capturing the king in a chess game.
The cyber community buzzed with rumors and speculation in the whirlwind that followed the seizure. A prevailing question emerged, casting a shadow of doubt: “Did the XSS guy betray LockBit?” Yet, this web of conjecture was soon overshadowed by the sheer magnitude and significance of Operation Cronos. This critical operation reportedly hinged on exploiting CVE-2023-3824, a vulnerability within LockBit’s PHP server, showcasing the intricacies and dangers of cyber vulnerabilities.

Fig. 3. Announcement of a seizure on LockBit’s dark web platform
Our dedicated blog post offers comprehensive insights and analysis for those seeking a deeper understanding of Operation Cronos and its implications for the cybersecurity landscape.
Once again, the impact and importance of updating and vulnerability management becomes apparent! Think Like a Hacker, Defend Like a Pro (or don’t think like some hackers). You don’t want your security posture to be weak when things change dynamically in your organization’s digital environment.
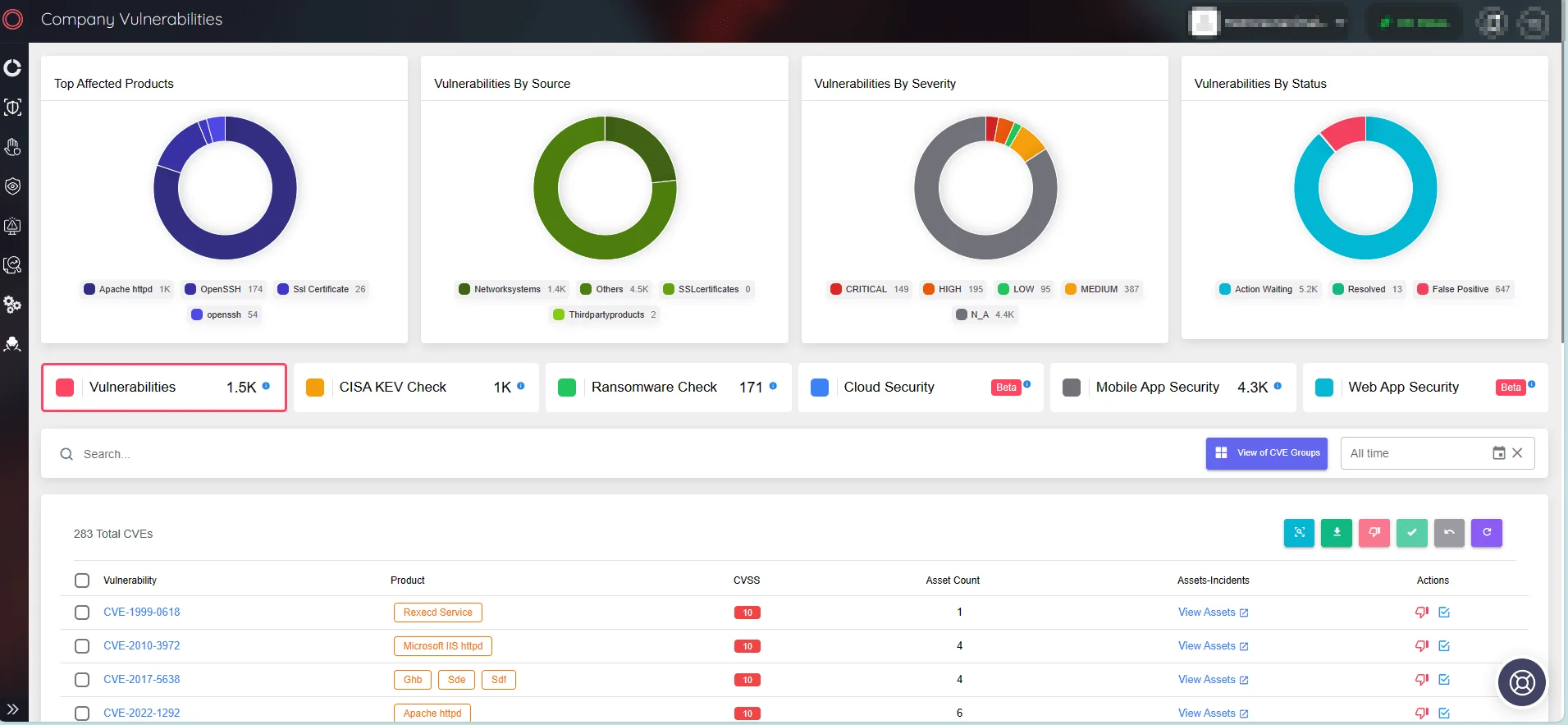
Fig. 4. SOCRadar Attack Surface Management, Company Vulnerabilities
You can see the unseen with SOCRadar’s wizard-level EASM continuous monitoring magic. Imagine having an x-ray vision of your digital domain’s present and future risks without the hassle of listing your assets manually.
Stay ahead with SOCRadar, catching vulnerabilities in software, leaks of sensitive info, third-party app risks, out-of-date SSL certificates, DNS mysteries, and cloud assets still playing hide and seek. Dive into SOCRadar’s External Attack Surface Management for the coolest, most proactive way to say “not today” to cyber threats.
The Curious Case of The Five Families and Knight Ransomware
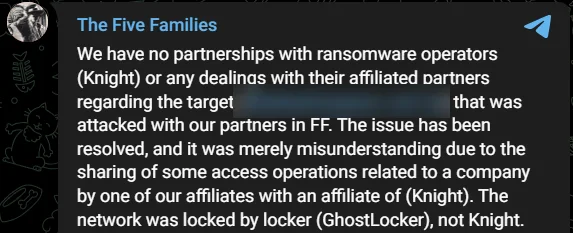
Fig. 5. The Five Families’ announcement
The Five Families – ThreatSec, GhostSec, Stormous, and Blackforums, with SiegedSec (they’ve left the chat) – a collective name that sounds like they should be sitting around a table in a dimly lit room but are actually sprawled across keyboards, made waves by claiming they’ve sneaked into the digital vaults of an Argentine company. But before the virtual ink dried on their announcement, Knight ransomware popped up, echoing, “Us too!”
Now, The Five Families, in a move that’s less mafia and more high school drama, were quick to clarify, “Nope, we didn’t partner with those Knight folks.” This raises the eyebrows of the cyber sleuths: Are we looking at a case of shared tools, or did they swipe right on the same dark web forum or initial access broker?
It’s like discovering two people bought the same unique gift for a party from the same obscure online store. Coincidence?
By the way, the Knight ransomware gang is closed, and the Knight ransomware source code is being sold on a hacker forum.
SiegedSec Claims Breach of TheTruthSpy, Exposing 140,000 Mobile Devices
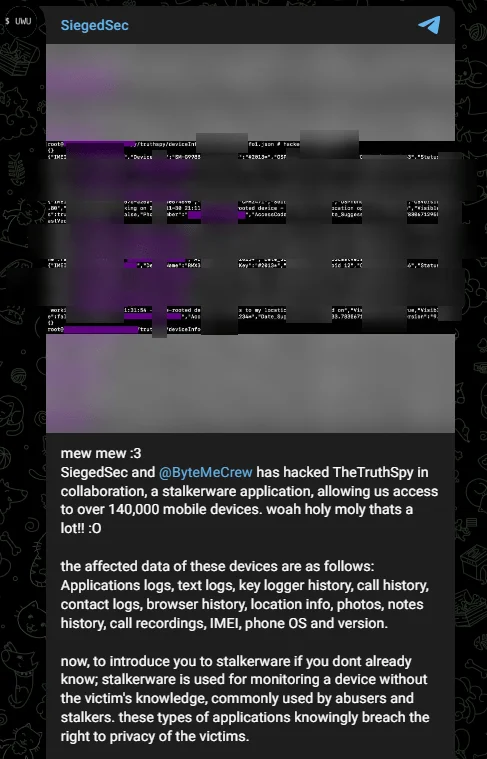
Fig. 6. Threat actor’s statement
The threat group SiegedSec claimed that they revealed a collaboration with ByteMeCrew, resulting in a significant breach of TheTruthSpy, a stalkerware application.
Stalkerware is spyware designed for unauthorized surveillance within personal relationships, often installed secretly, and operates without the user’s knowledge. It can monitor phone calls, messages, internet activity, location, and even surroundings through the camera or microphone. Typically downloaded from unofficial app stores or directly from websites, it requires physical access to the target device.
According to SiegedSec, the compromised data from these devices includes a plethora of sensitive information such as application logs, text logs, keylogger history, call history, contact logs, browser history, location info, photos, notes history, call recordings, IMEI, phone OS, and version.
Little Red Riding Hood Meets the Big Bad XML Wolf: CVE-2024-22024
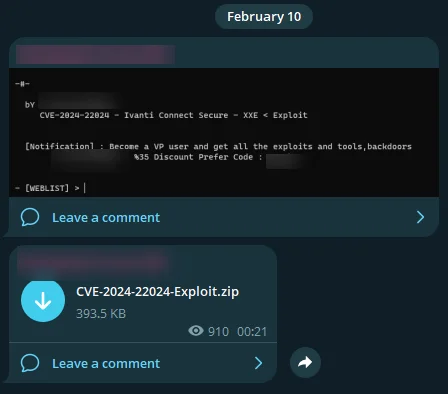
Fig. 7. Threat actor’s announcement on Telegram channel
On February 10, a cunning threat actor took to a Telegram channel, unveiling an exploit for CVE-2024-22024 just a day after the vulnerability’s Proof of Concept (PoC) debuted. This rapid response highlights how eagerly cybercriminals lurk for any crack in digital defenses, reminiscent of the wolf eyeing Little Red Riding Hood—minus the fairy tale ending.
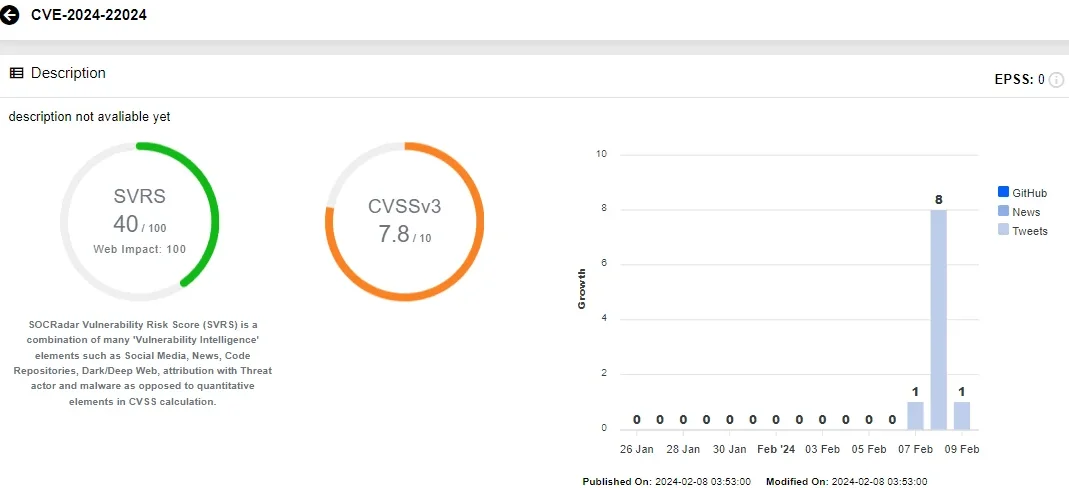
Fig. 8. SOCRadar Vulnerability Card for CVE-2024-22024
CVE-2024-22024, unearthed in an investigation of Ivanti Connect Secure, Ivanti Policy Secure, and ZTA gateways, carries a CVSS score of 8.3. This XML External Entity (XXE) vulnerability lurks in the SAML component, affecting Ivanti products’ versions 9.x and 22.x. If exploited, attackers could sneak into restricted resources without a key, making it a critical security concern for organizations relying on these Ivanti products.
Brushing Up on Cybersecurity: When 3 Million Toothbrushes Almost Cleaned Up the Internet

Fig. 9. (Source: X)
February brought a buzz to the cybersecurity world that was as bristling as the idea of using 3 million toothbrushes to construct a botnet. This concept bubbled over in the media like toothpaste squeezed out too fast, capturing headlines and imaginations alike.
Initially feared as a looming cyber threat, this toothbrush tale was eventually brushed off as mere speculation. Yet, it left behind a minty fresh reminder of the burgeoning impact of IoT (Internet of Things) devices on cybersecurity.
As technology evolves, so does the variety of IoT devices infiltrating our homes and lives, stretching from the bathroom to the kitchen. This rapid proliferation, coupled with their integration into daily routines, dramatically broadens the potential attack surface for cyber threats. The convenience of having our toothbrushes, refrigerators, smart grills, and thermostats connected to the internet comes with a caveat: these devices are often equipped with basic, default security measures that might not hold up against sophisticated attacks.
Moreover, the lag in rolling out security updates—or in some cases, their complete absence—leaves these smart devices hanging like low-hanging fruit for cybercriminals to pluck.
The $15 Million Global Hunt for ALPHV/BlackCat’s
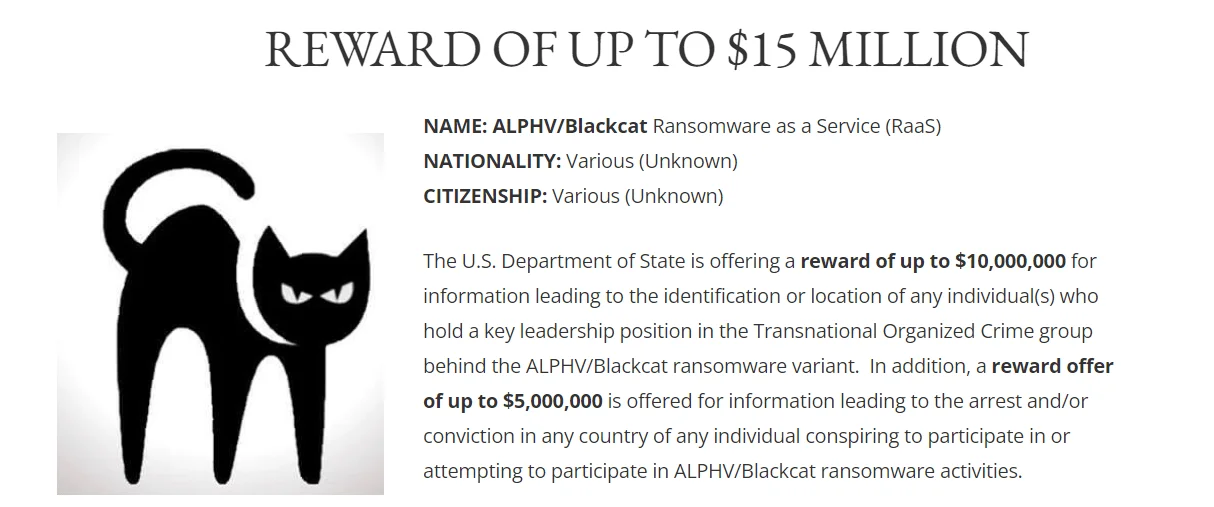
Fig. 10. Reward for Information on ALPHV/BlackCat (Source: state.gov)
The U.S. Department of State transforms cybersecurity into a high-stakes game, allowing players to hunt digital outlaws for real-world rewards. Amidst the backdrop of ALPHV/BlackCat ransomware’s audacious cyber assaults, including the alleged breach of Canada’s Trans-Northern Pipelines, players are summoned to the forefront of digital justice. A bounty of up to $10 million awaits those savvy enough to uncover the identities or hideouts of the masterminds occupying the top echelons behind the menacing ALPHV/BlackCat ransomware variant.
But the challenge doesn’t stop there. The Department throws in an additional pot of up to $5 million for intelligence that leads to the arrest and/or conviction, anywhere in the world, of any conspirator entangled in the web of ALPHV/BlackCat ransomware operations. This game of shadows casts players as cyber sleuths, navigating the murky waters of the internet to clamp down on the architects of chaos, turning the tide in the global fight against cybercrime. Will you join the hunt and etch your name in the annals of cyber guardians?
From Smokescreens to SOS Signals
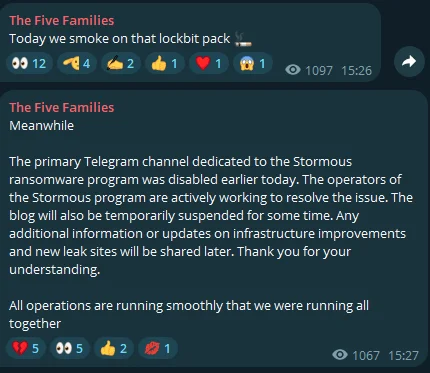
Fig. 11. The Five Families’ statements
Following the law enforcement takedown of LockBit, the Five Families, a known cybercriminal alliance, responded with mixed reactions on their Telegram channels. Initially, they mocked LockBit’s downfall with a message, “Today we sm*ke on that lockbit pack.” However, the tone shifted when they faced their own troubles, announcing the disabling of the Stormous Ransomware‘s primary Telegram channel and a temporary halt to their operations and communications.
This one-two-punch of messages highlights the fluid dynamics of the cyber underworld. The shutdown of Stormous’ channel, following close on the heels of LockBit’s woes, raises the question: Are cybercriminals starting to feel the heat from increased cybersecurity efforts? It seems the takedown of LockBit’s infrastructure might be causing a domino effect, sending a wave of caution through the ranks of other threat actors.
From Cyber BFFs to Frenemies
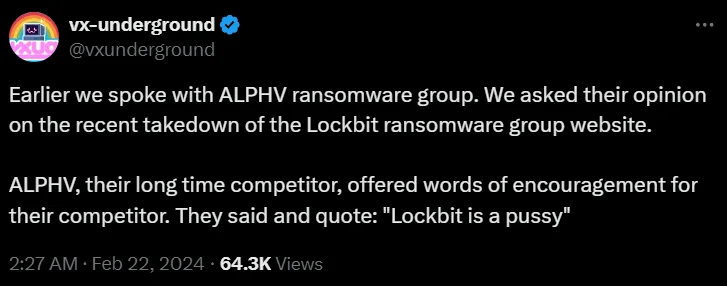
Fig. 12. VX-Underground’s tweet’
In the evolving dynamics of cybercrime, LockBit once stood by ALPHV/BlackCat during an FBI operation, suggesting a form of alliance. However, a tweet from VX Underground shed light on a stark shift in sentiment post-Operation Cronos. When VX asked ALPHV/BlackCat about the LockBit takedown, their blunt response was, “Lockbit is a p****” This comment underscores the fragile nature of relationships among cybercriminal groups, where support can quickly turn into rivalry.
The ‘Not-So-Anonymous’ Pranksters
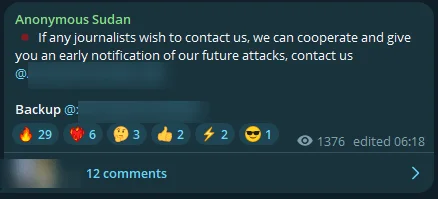
Fig. 13. Anonymous Sudan invites journalists
The group called Anonymous Sudan has made an unusual offer to journalists. Their proposition? A backstage pass to their upcoming cyber-attacks. It’s like inviting reporters to a carnival sideshow, but with a potential sting in the tail. Anonymous Sudan seeks new directors for advertising.
Who Knew Cybercrime Had a Dress Code?
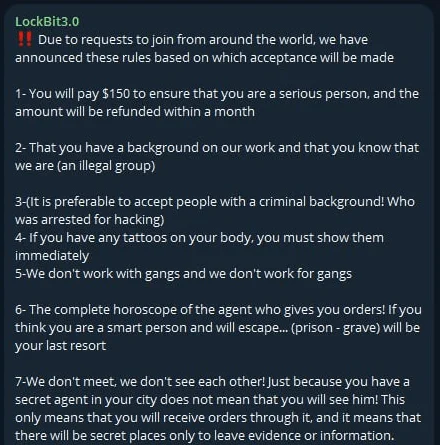
Fig.14. The scammer’s telegram announcement
Considering joining LockBit for $150? Well, it turns out the real LockBit ransomware group might have left the chat, but their fan club of scammers hasn’t gotten the memo. There’s a quirky membership rule: if you get inked, you might just be too cool for cybercrime school. Who knew tattoos were the latest cybersecurity measure?
Another Day, Another Alliance of Russian Threat Actors

Fig.15. Banner of Darknet Senate
Russian threat actors have decided to form a band again. They’re calling themselves the Darknet Senate, a motley crew of six, including pro-Russian threat groups like NoName057(16) and UserSec. Interestingly, a Yemeni hacktivist group has also joined this alliance. Is the name ‘Darknet Senate’ referencing the Darknet Parliament (KillNet, Anonymous Sudan, and REvil)?
Conclusion
As we wrap up this edition of Dark Peep, we find ourselves on the brink of the digital realm, echoing the epic tales of Greek mythology. SOCRadar stands as our beacon of insight, much like the wise counselors who guided heroes through their quests. In this world where cyber threats lurk like old monsters, SOCRadar’s Cyber Threat Intelligence acts as our map and compass, revealing the hidden dangers and guiding us through the cyber wilderness with clarity and foresight.
Fig. 16. SOCRadar Dark Web News
Article Link: https://socradar.io/dark-peep-11-the-final-curtain-for-lockbit-ransomware-operation-cronos/
