Credit to this tweet:
https://twitter.com/Bing_Chris/status/993486151519494146
I thought it was worth sharing, enjoyed the read.
2017 showed that the cyber threat against the West is growing and that most of the malicious cyber activity originates in Russia.
RUSSIAN APTs
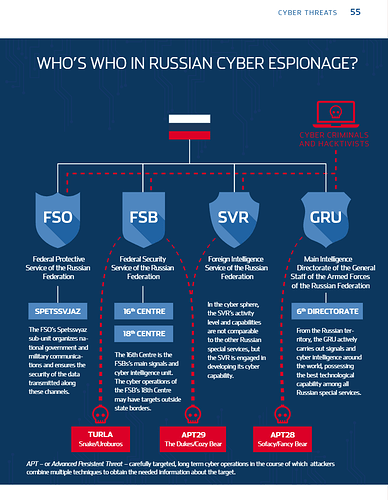
Last year, advanced persistent threats (APTs) of Russian origin received much attention . These are carefully target-ed, long-term cyber operations in the course of which attackers combine multiple techniques to get the desired information about the target . Such operations are complex and resource-in-tensive, which is why they are not within financial reach for smaller groups or lone actors . Russian state interests and implementers are usually behind APTs .CYBER THREATS2017 showed that the cyber threat against the West is growing and that most of the malicious cyber activity originates in Russia.Russian cyber groups – examples include APT28 (Sofacy/Fancy Bear) associated with the military intelligence GRU, SNAKE (Turla) tied to the federal security service FSB, and APT29 (Cozy Bear/The Dukes) associated with the FSB and the foreign intelligence service SVR – play the key role in Russia’s influence operations toolbox . These are long-term Russian cyber operations with a clear direction based on Russia’s interests and objectives . The selection of targets for the operations, techniques used and the long-term nature of the activities is consistent with the Russian Federation’s intelligence needs . Good examples of the use of these sorts of attacks for political purposes include the GRU cyber operations against the World Anti-Doping Agency (WADA) in September 2016 and against the International Olympic Committee (IOC) in January 2018 . It is not difficult to find Russia’s motivation behind such attacks due to the recent extensive dop-ing scandal that has affected Russian athletes .
See the full report here (cyber threat starts on page 52):
https://www.valisluureamet.ee/pdf/raport-2018-ENG-web.pdf