On July 1st, the Qualys’s security team announced CVE-2024-6387, a remotely exploitable vulnerability in the OpenSSH server. This critical vulnerability is nicknamed “regreSSHion” because the root cause is an accidental removal of code that fixed a much earlier vulnerability CVE-2006-5051 back in 2006. The race condition affects the default configuration of sshd (the daemon program for SSH).
OpenSSH versions older than 4.4p1 – unless patched for previous CVE-2006-5051 and CVE-2008-4109) – and versions between 8.5p1 and 9.8p1 are impacted. The general guidance is to update the versions. Ubuntu users can download the updated versions.
According to OpenSSH infosec researchers, this vulnerability may be difficult to exploit.
Their investigation disclosed that under lab conditions, the attack requires, on average, 6-8 hours of continuous connections until the maximum amount accepted by the server is met.
Why Is CVE-2024-6387 Significant?
This vulnerability allows an unauthenticated attacker to gain root level privileges and remotely access your glibc-based Linux systems, where syslog() (a system logging protocol) itself calls async-signal-unsafe functions via the SIGALRM handler. Researchers believe that OpenSSH on OpenBSD, a notable exception, is not vulnerable by design as the SIGALRM handler calls syslog_r(), an async-signal-safer version of syslog().
Read the advisory issued by OpenSSH and the report disclosed by Qualys for the technical background.
What Is The Impact?
OpenSSH researchers believe the attacks will improve over time –thanks to the advancements in deep learning – and impact other operating systems, including the non-glibc systems. The net effect of exploiting CVE-2024-6387 is full system compromise and takeover, enabling threat actors to execute arbitrary code with the highest privileges, subvert security mechanisms, data theft, and even maintain persistent access. The team at Qualys have already identified no less than 14 million potentially vulnerable OpenSSH server instances exposed to the internet.
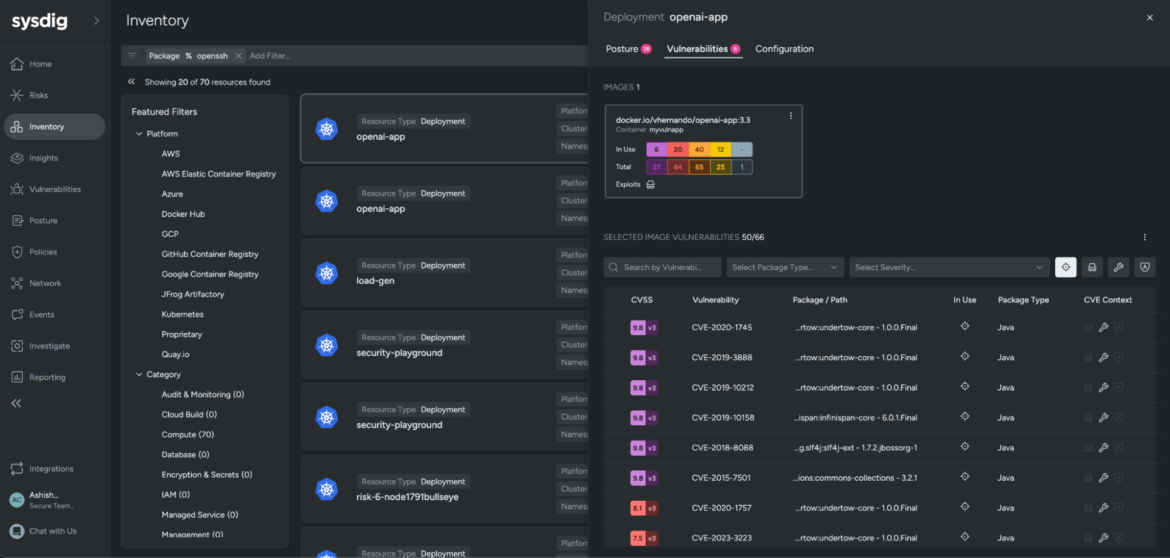
How To Find Vulnerable OpenSSH Packages with Sysdig
You can use your inventory workflows to get visibility into resources and security blindspots across your cloud (GCP, Azure and AWS), Kubernetes, and container images. Besides patching, you should also limit SSH access to your critical assets.
Here’s how you can look for the vulnerable OpenSSH package within your environment using Sysdig Secure:
- Navigate to the Inventory tab
- In the Search bar, enter the following query:
Package contains opensshThe results show all the resources across your cloud estate that have the vulnerable package. Sysdig provides an overview of all the blind spots that may have gone unchecked within your environment. You can interact with the filters and further reduce your investigation timelines from within a single unified platform.
The Need For Stateful Detections
Exploitation of regreSSHion involves multiple attempts (thousands, in fact) executed in a fixed period of time. This complexity is what downgrades the CVE from “Critical” classified vulnerability to a “High” risk vulnerability, based mostly on the exploit complexity.
Using Sysdig, we can detect drift from baseline sshd behaviors. In this case, stateful detections would track the number of failed attempts to authenticate with the sshd server. Falco rules alone detect the potential Indicators of Compromise (IoCs). By pulling this into a global state table, Sysdig can better detect the spike of actual, failed authentication attempts for anonymous users, rather than focus on point-in-time alerting.
At the heart of Sysdig Secure lies Falco’s unified detection engine. This cutting‑edge engine leverages real‑time behavioral insights and threat intelligence to continuously monitor the multi‑layered infrastructure, identifying potential security incidents.
Whether it’s anomalous container activities, unauthorized access attempts, supply chain vulnerabilities, or identity‑based threats, Sysdig ensures that organizations have a unified and proactive defense against evolving threats.
Reference:
https://thehackernews.com/2024/07/new-openssh-vulnerability-could-lead-to.html
https://blog.vyos.io/cve-2024-6387-regresshion
https://www.openssh.com/releasenotes.html
https://github.com/acrono/cve-2024-6387-poc
The post CVE-2024-6387 – Shields Up Against RegreSSHion appeared first on Sysdig.
Article Link: CVE-2024-6387 - Shields Up Against RegreSSHion | Sysdig