For the roughly three decades that the commercial cybersecurity industry has existed, it has struggled with a fundamental problem – a lack of realistic attack testing to determine whether the products that companies and consumers buy actually work in stopping real “in-the-wild” threats. The problem is a challenging one: If you want to test a security technology against a specific threat, by definition, that threat must already be known to someone and, thus, cannot qualify as a “zero-day” attack. It is the cybersecurity equivalent of Heisenberg’s uncertainty principle: The more precisely you can determine the efficacy of a security product against tested malware and exploits, the less realistic that result is, since to be tested, those threats have to be already known and widely available.
This was the reason I was so excited last summer when CrowdStrike® was approached by MITRE (a federally funded research and development center) with a request to evaluate our Falcon endpoint protection solution in the first realistic public adversary emulation. Unlike other public tests, this evaluation was not going to rely on known malware and exploits, but instead mimic the tradecraft of a real and sophisticated nation-state adversary on a cyber range setup at MITRE. CrowdStrike did not pay MITRE to conduct this evaluation. MITRE’s independence and nonprofit status is yet another important differentiation and enhances the credibility of their testing process.
The goal of the simulation was to not just detect an adversary, but to comprehensively determine what level of visibility the product provides against all of the tradecraft utilized, and to map those results to MITRE’s ATT&CK framework. The adversary picked in our evaluation was GOTHIC PANDA (also known as APT3), a sophisticated hacking team linked to the Chinese government’s Ministry of State Security (MSS) and whose contractors were recently indicted by U.S. Justice Department. The group is known for leveraging zero-day exploits, use of common websites such as GitHub for command and control channels to evade blacklisting, and for targeting numerous industries, including Aerospace and defense, chemicals, energy, finance, healthcare, industrial goods, NGO/international organizations, technology and transportation.
framework. The adversary picked in our evaluation was GOTHIC PANDA (also known as APT3), a sophisticated hacking team linked to the Chinese government’s Ministry of State Security (MSS) and whose contractors were recently indicted by U.S. Justice Department. The group is known for leveraging zero-day exploits, use of common websites such as GitHub for command and control channels to evade blacklisting, and for targeting numerous industries, including Aerospace and defense, chemicals, energy, finance, healthcare, industrial goods, NGO/international organizations, technology and transportation.
Today I’m thrilled to announce that CrowdStrike Falcon, backed by our elite Falcon OverWatch team, aced the simulation – detecting and providing visibility into nearly every technique tested by the MITRE team. This should be no surprise to our customers, who observe our unmatched ability to stop breaches in their environments daily. Our OverWatch team detects, stops and notifies our customers of about 400 serious breach attempts every single week – two per hour, on average.
team, aced the simulation – detecting and providing visibility into nearly every technique tested by the MITRE team. This should be no surprise to our customers, who observe our unmatched ability to stop breaches in their environments daily. Our OverWatch team detects, stops and notifies our customers of about 400 serious breach attempts every single week – two per hour, on average.
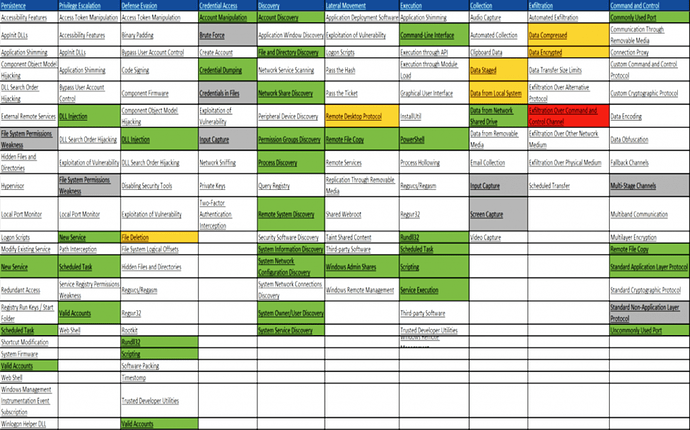
The ATT&CK framework matrix results for CrowdStrike are below. The green and yellow cells indicate all of the techniques that Falcon had detection or visibility for. The white and grey cells are those techniques that were not part of the testing, as they were either not part of GOTHIC PANDA’s suite of tactics or were out-of-scope for this simulation. The one red cell below – “Exfiltration Over Command and Control Channel” (in this case, DNS) – was the only one missed by Falcon. This one small visibility gap has since been corrected and added to our platform.
CrowdStrike Falcon’s ATT&CK evaluation of GOTHIC PANDA tactics and techniques
We are very pleased that in the months following our testing, we have worked closely with MITRE to receive approval to publish our results for public viewing. The report is available for download here: Download the Report.
We believe that this emulation test is an important step forward for our industry, providing the first comprehensive and easily discernible evaluation of the real-world efficacy of security products. We encourage all vendors to participate in this type of testing going forward, and applaud MITRE’s Leveraging External Transformational Solutions (LETS) program for this important and groundbreaking achievement. We are also very grateful to the MITRE team for the valuable feedback they have provided to us in the course of this simulation, and for the opportunity to improve our technology to benefit all of our customers. We believe in open and transparent testing by credible and independent organizations like MITRE. We also encourage all customers and analysts to demand this type of independent testing to enable our industry to improve and develop more effective solutions.
The results of this emulation come on the heels of CrowdStrike being positioned highest for “ability to execute” and furthest for “completeness of vision” in the Visionary Quadrant of the 2018 Gartner Magic Quadrant for endpoint protection platforms, further validating our leadership position in the endpoint protection space. I would encourage you to think beyond vendors that wave their hands and try to misdirect customers that independent testing and independent analyst reports are not relevant when they don’t suit their narrative. They are critical to separating the marketing talk from the solutions that can protect customers from real-world threats.
The post CrowdStrike Falcon Defeats GOTHIC PANDA in MITRE Nation-State Emulation Test appeared first on .
Article Link: https://www.crowdstrike.com/blog/crowdstrike-falcon-defeats-gothic-panda-in-mitre-nation-state-emulation-test/