Critical Vulnerabilities in SolarWinds ARM, Serv-U, and Cisco SSM On-Prem, Secure Email Gateway Products
Technology giants SolarWinds and Cisco have recently released security advisories addressing several critical vulnerabilities in their product lines. These advisories focus on resolving issues that notably include Remote Code Execution (RCE) attacks and system takeovers.
The affected products include SolarWinds ARM (Access Rights Manager) and Cisco SSM On-Prem (Smart Software Manager On-Prem), as well as Cisco Secure Email Gateway.
What Are the Latest Critical Vulnerabilities in SolarWinds ARM?
SolarWinds has issued an urgent security advisory addressing multiple critical vulnerabilities discovered in its Access Rights Manager (ARM) product, used by businesses to control and audit access rights across their systems.
The company has disclosed 13 vulnerabilities in the same advisory, ranging from high to critical severity. Below are details of the critical vulnerabilities in the latest SolarWinds security update.
- CVE-2024-23475 (CVSS 9.6): An information disclosure and directory traversal vulnerability allowing an unauthenticated user to perform arbitrary file deletion and leak sensitive information.
- CVE-2024-23469 (CVSS 9.6): An RCE vulnerability that allows an unauthenticated user to perform actions with SYSTEM privileges.
- CVE-2024-23472 (CVSS 9.6): A directory traversal vulnerability that allows an authenticated user to arbitrarily read and delete files in ARM.
- CVE-2024-23466 (CVSS 9.6): An RCE stemming from a directory traversal vulnerability that allows an unauthenticated user to perform actions with SYSTEM privileges.
- CVE-2024-23467 (CVSS 9.6): A directory traversal and information disclosure vulnerability that allows an unauthenticated user to perform RCE.
- CVE-2024-28074 (CVSS 9.6): This is from a previously disclosed RCE vulnerability in SolarWinds ARM, which was not fully fixed. The implemented controls could be bypassed and exploited using a different method.
- CVE-2024-23470 (CVSS 9.6): A pre-authentication RCE vulnerability allowing unauthenticated users to run commands and executables.
- CVE-2024-23471 (CVSS 9.6): A vulnerability enabling authenticated users to abuse a SolarWinds service for remote code execution.
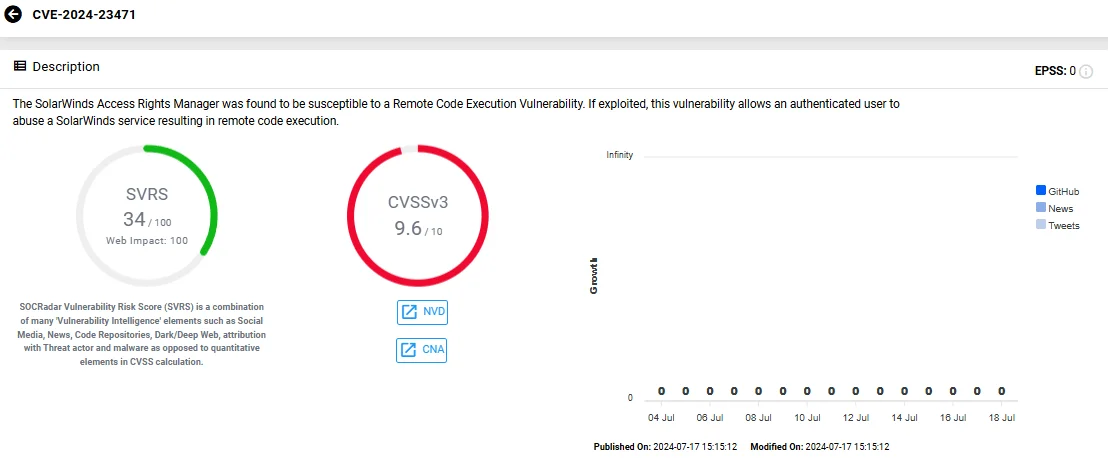
Vulnerability card of CVE-2024-23471 (SOCRadar Vulnerability Intelligence)
The remaining high-severity vulnerabilities in the advisory involve authentication bypass and directory traversal issues, which could allow domain admin access and file deletion/information disclosure, respectively.
How to Address SolarWinds ARM Vulnerabilities
Fixes for the mentioned set of vulnerabilities are available in SolarWinds ARM version 2024.3. It is recommended that organizations using ARM update to this latest version immediately to avoid exploitation.
While SolarWinds has not received reports of these vulnerabilities being exploited in the wild, any organization using SolarWinds ARM is potentially at risk, and immediate action is vital.
You can simplify vulnerability management with SOCRadar’s advanced solutions, maintaining a proactive approach to emerging threats. The SOCRadar Vulnerability Intelligence module provides a detailed view of identified security vulnerabilities, delivering real-time alerts and comprehensive insights.
With SOCRadar Vulnerability Intelligence, your organization can stay ahead of potential breaches by tracking new exploits and updates across multiple platforms.
Severe SolarWinds Vulnerability Enters the CISA KEV Catalog (CVE-2024-28995)
The Cybersecurity and Infrastructure Security Agency (CISA) has recently added another SolarWinds vulnerability, disclosed in early June 2024, to its Known Exploited Vulnerabilities (KEV) Catalog due to evidence of active exploitation.
The vulnerability, tracked as CVE-2024-28995 (CVSS: 7.5), is a Path Traversal in SolarWinds Serv-U File Server. Proof-of-Concept (PoC) exploits for this vulnerability have been publicly available since June, according to data from SOCRadar’s Vulnerability Intelligence module.
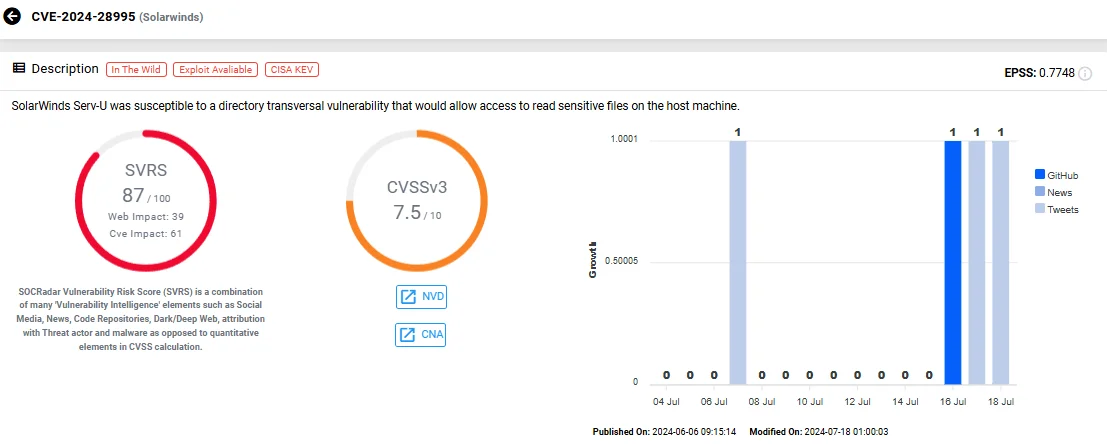
Vulnerability card of CVE-2024-28995 (SOCRadar Vulnerability Intelligence)
As of June 15, 2024, over 900 SolarWinds Serv-U instances exposed online are vulnerable to CVE-2024-28995, according to Shadowserver. Most of these instances are based in the US.
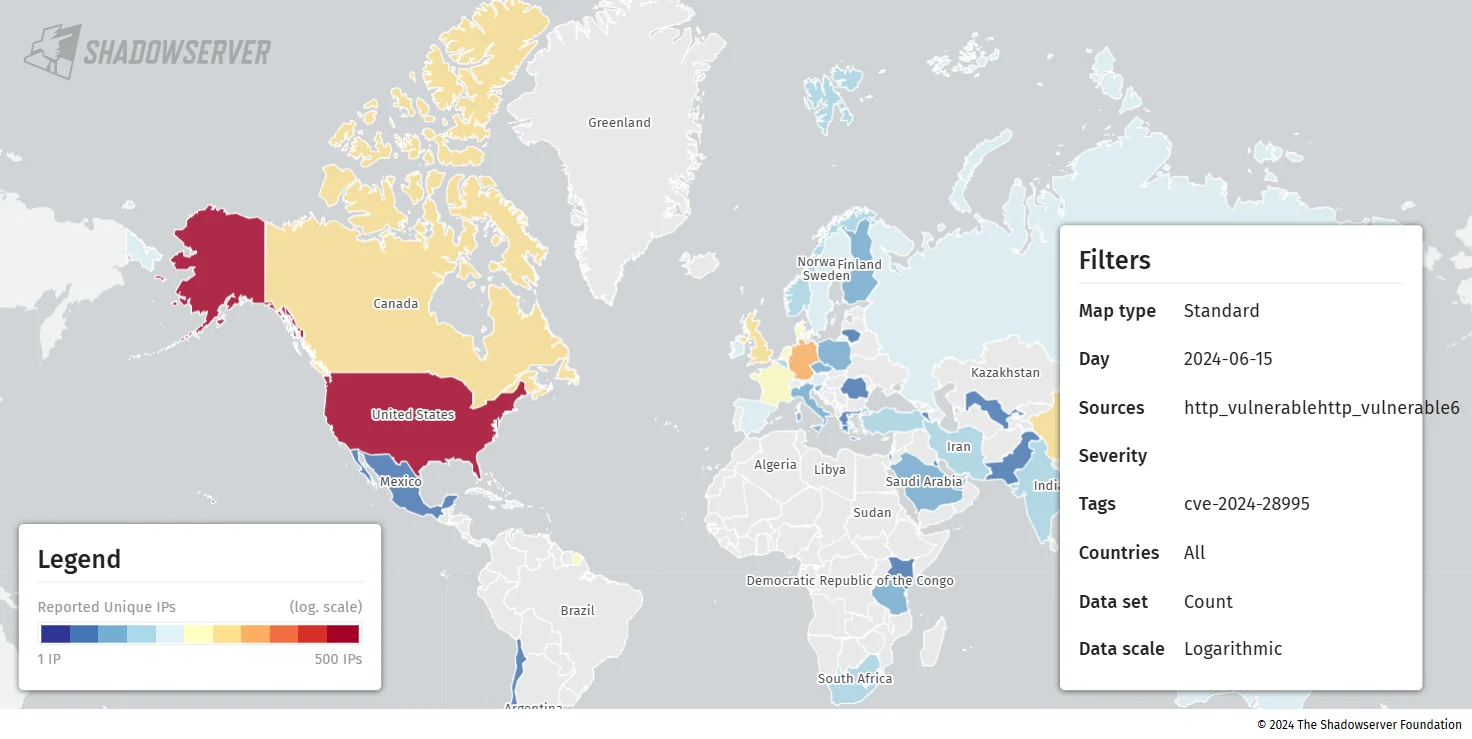
A map view of exposed Solarwinds Serv-U instances (Shadowserver)
Additionally, two other vulnerabilities have been added to the catalog:
- CVE-2024-34102 (CVSS: 9.8): Adobe Commerce and Magento Open Source Improper Restriction of XML External Entity Reference (XXE) Vulnerability
- CVE-2022-22948 (CVSS: 6.5): VMware vCenter Server Incorrect Default File Permissions Vulnerability
CISA notes that these vulnerabilities are common attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Therefore, federal agencies are mandated to patch these vulnerabilities by August 7, 2024.
Cisco Fixed Critical Vulnerabilities in Cisco SSM On-Prem and Secure Email Gateway
Cisco released 10 security advisories on July 17, 2024, two of which resolved critical severity vulnerabilities: CVE-2024-20419 and CVE-2024-20401.
What Is CVE-2024-20419? Details of the Critical Cisco SSM On-Prem Vulnerability
One of the advisories highlighted a maximum severity vulnerability affecting the Cisco SSM On-Prem (Smart Software Manager On-Prem) license server, which is a component of Cisco Smart Licensing.
The advisory notes that Cisco SSM On-Prem versions earlier than Release 7.0 were referred to as Cisco SSM Satellite. From Release 7.0 onward, the product is known as Cisco SSM On-Prem. This vulnerability also affects Cisco Smart Software Manager Satellite (SSM Satellite).
Tracked as CVE-2024-20419 (CVSS: 10), this critical vulnerability in SSM On-Prem’s authentication system allows an unauthenticated remote attacker to change any user’s password, including administrative users, without knowing their actual credentials.
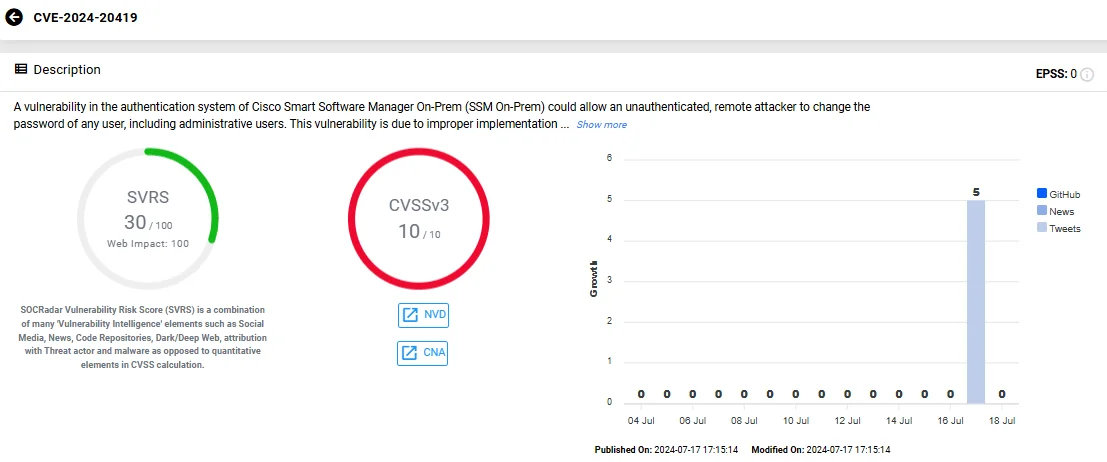
Vulnerability card of CVE-2024-20419 (SOCRadar Vulnerability Intelligence)
Exploiting this flaw involves sending crafted HTTP requests to an affected device. This grants the attacker access to the web UI or API with the compromised user’s privileges.
Patch Available for CVE-2024-20419
While Cisco’s advisory for CVE-2024-20419 does not list any workarounds, the company strongly advises administrators to upgrade to a fixed release as soon as possible to prevent exploitation.
For Cisco SSM On-Prem Release 8-202206 and earlier versions, a fix has been implemented in Release 8-202212.
Critical Cisco Secure Email Gateway Vulnerability (CVE-2024-20401) Allows RCE
Another critical advisory highlights a vulnerability in Cisco Secure Email Gateway, tracked as CVE-2024-20401 (CVSS: 9.8).
The vulnerability arises from improper handling of email attachments in content scanning and message filtering features. It allows attackers to overwrite arbitrary files on the operating system, potentially leading to unauthorized user creation with root privileges, configuration changes, remote code execution, or a Denial-of-Service (DoS) condition.
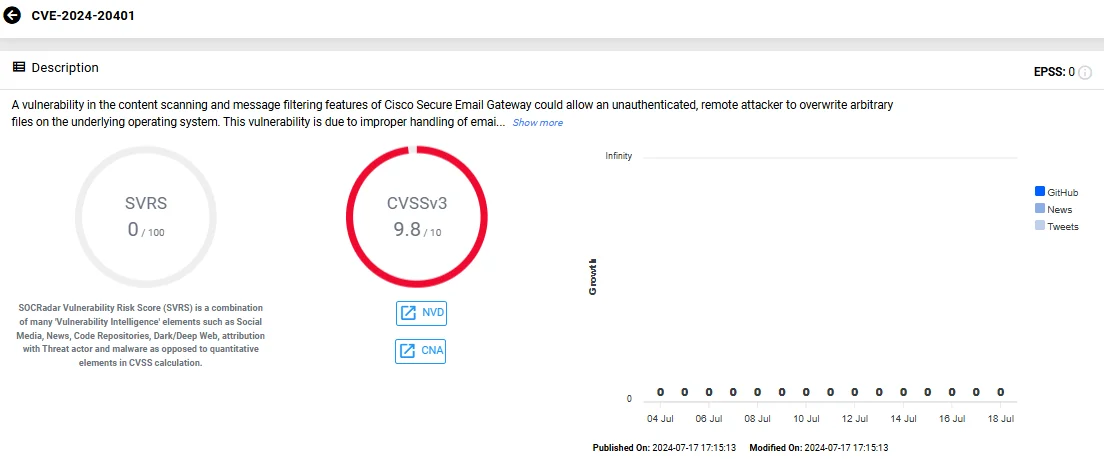
Vulnerability card of CVE-2024-20401 (SOCRadar Vulnerability Intelligence)
It is important to note that the issue affects systems running a vulnerable version of Cisco AsyncOS with file analysis or content filter enabled, and using Content Scanner Tools earlier than version 23.3.0.4823. If your system uses these configurations, an attacker can exploit CVE-2024-20401 by sending a specially crafted email attachment.
Secure Your Cisco Secure Email Gateway Against CVE-2024-20401
Cisco has resolved the CVE-2024-20401 vulnerability with an updated Content Scanner Tools package, included by default in Cisco AsyncOS for Cisco Secure Email Software versions 15.5.1-055 and later. It is advised for administrators to promptly upgrade to the latest version of the Content Scanner Tools to mitigate this vulnerability. You can visit Cisco’s official advisory for more information.
Additionally, by using SOCRadar LABS’ Email Security Grader, you can quickly assess the vulnerability of your email server and identify ways to improve its security measures.
Free Email Security Grader tool available on SOCRadar LABS
Learn more about the vulnerabilities that affect secure email gateways in SOCRadar blog: Defending the Inbox: Vulnerabilities of Secure Email Gateways.
Monitor Assets and Identify Security Vulnerabilities via SOCRadar’s ASM
SOCRadar’s Attack Surface Management (ASM) module provides continuous monitoring of your digital assets, allowing you to quickly identify and respond to security incidents and new vulnerabilities.
Leverage SOCRadar’s ASM to stay ahead of potential threats and ensure your digital environments remain secure and resilient against evolving cyber threats.
The ASM module delivers real-time threat alerts with rapid, actionable insights, enabling you to take preemptive actions that enhance your cybersecurity stance.
Article Link: https://socradar.io/critical-vulnerabilities-in-solarwinds-arm-serv-u-and-cisco-ssm-on-prem-secure-email-gateway-products/

