Estimated reading time: 4 minutes
Openfire is an open-source, real-time collaboration server based on the XMPP (Extensible Messaging and Presence Protocol) protocol. It facilitates instant messaging, group chat, and other real-time communication services. Openfire is popular for its flexibility, scalability, and robust security features. It is commonly used in organizations and educational institutions, and even as a foundation for building custom chat and collaboration applications. Its ease of use and extensive plugin support have contributed to its widespread adoption for both internal team communication and customer-facing chat solutions.
A recent discovery in May unveiled a fresh security concern (CVE-2023-32315) associated with the Openfire console. This vulnerability, characterized as a path traversal flaw, explicitly targets the setup environment. Exploiting this weakness empowers unauthorized users to compromise the unauthenticated Openfire Setup Environment within an established configuration. Subsequently, malicious actors can infiltrate admin setup files usually confined to the Openfire Admin Console’s access. This could lead to two significant actions: adding an admin user to the console or uploading a plugin, potentially securing complete control over the server.
CVE-2023-32315
The cause of vulnerability CVE-2023-32315 stemmed from an existing path traversal protection mechanism that was in place to guard against precisely this type of attack. However, it could not fend off specific non-standard URL encoding techniques involving UTF-16 characters. These particular encoding methods were not supported by the embedded web server in use at the time, rendering the path traversal defenses ineffective in such scenarios.
This vulnerability impacts all Openfire versions released since April 2015, beginning with version 3.10.0. The issue has been addressed in Openfire releases 4.7.5 and 4.6.8, with additional enhancements planned for the upcoming initial release of the 4.8 branch, expected to be named version 4.8.0.
Path Traversal to Remote Code Execution
After a thorough examination of publicly accessible exploits, we proceed to deconstruct the attack sequence as follows:
- Token Acquisition Phase:
Obtain the necessary session tokens, such as the JSESSION ID and CSRF.
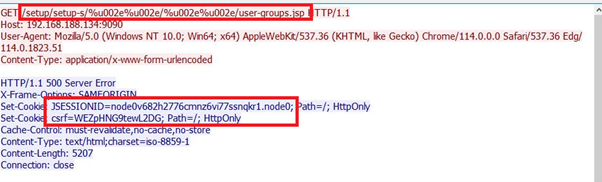
Acquiring session token
- Directory Traversal and Administrative Action Phase:
Utilize these acquired tokens with directory traversal techniques to carry out administrative actions. One common action is the creation of an admin user without requiring authentication.
![]()
Creating admin user
- Administrator-Level Access Phase:
After successfully executing administrative actions, gain elevated access to the system.
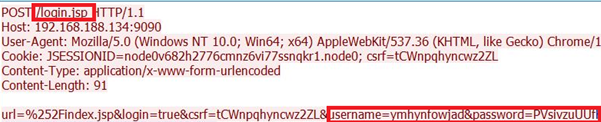
Admin login
- Malicious Plugin Deployment Phase:
This plugin can serve dual purposes, acting as a web shell or establishing a covert connection to the attacker-controlled machine.
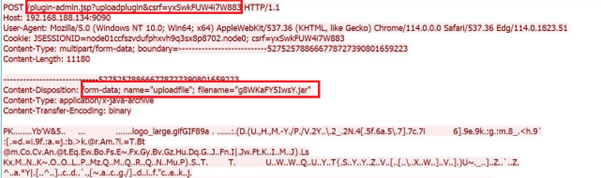
Upload malicious plugin
Real-world Consequences:
CVE-2023-32315 represents a significant authentication bypass vulnerability within Openfire, a widely adopted XMPP server. This flaw empowers malicious actors to gain unfettered access to the Openfire administrative console without a valid username and password. Once inside, attackers wield the ability to seize control of the server and unleash a range of malevolent actions, including:
- Altering the server’s configuration settings.
- Installing malicious software, such as malware.
- Pilfering sensitive data
- Disrupting the server’s normal operations.
This vulnerability has already been exploited in real-world scenarios, with reported instances of attackers leveraging it to deploy Kinsing malware and crypto miners.
Countermeasures for CVE-2023-32315
To fortify your Openfire server against the risks associated with CVE-2023-32315, it is crucial to implement the following comprehensive measures:
Update Openfire to the Latest Version: Ensure that your Openfire installation is promptly updated to the most recent release, which includes critical security patches. Versions 4.7.5 or 4.6.8 are recommended, as they specifically address this vulnerability.
Implement Firewall Restrictions: Utilize a firewall to restrict access to your Openfire server. Configure it to only allow connections from trusted IP addresses or networks. This extra layer of security helps mitigate the risk of unauthorized entry.
Leverage Reputable IPS and AV Solutions: Enhance your security posture by incorporating reputable Intrusion Prevention Systems (IPS) and Antivirus (AV) solutions. Regularly scan your server environment for any signs of compromise. These tools can provide proactive protection against emerging threats.
Monitor and Analyse Server Logs: Implement a robust log monitoring and analysis system to detect unusual or suspicious activities on your Openfire server. Timely detection can enable swift responses to potential threats.
By implementing these measures and staying proactive in your security efforts, you can significantly reduce the risk of falling victim to CVE-2023-32315 and other potential threats.
Quick Heal Protection
All Quick Heal customers are protected from this vulnerability by following signatures:
- HTTP/CVE-2023-32315!VS.48114
- HTTP/CVE-2023-32315!VS.48144
The post Critical Security Alert: CVE-2023-32315 Vulnerability in Openfire XMPP Server appeared first on Blogs on Information Technology, Network & Cybersecurity | Seqrite.
Article Link: https://www.seqrite.com/blog/critical-security-alert-cve-2023-32315-vulnerability-in-openfire-xmpp-server/