Critical HTTP File Server Vulnerability (CVE-2024-23692) Actively Exploited to Deploy Cryptomining Malware, RATs, Stealers
Researchers have identified active exploitation targeting a critical vulnerability in the HTTP File Server (HFS) to deploy cryptocurrency mining malware, Remote Access Trojans (RATs), backdoors, and infostealers.
Known as CVE-2024-23692, this critical vulnerability affects the Rejetto HTTP File Server (HFS). HFS allows file sharing through a web browser using just an executable file, eliminating the need to build a traditional web server. This simplicity makes it a popular choice for users looking to share files easily.
However, since HFS is publicly exposed to enable user connections, it becomes a target for external attacks if a vulnerability exists. This exposure makes it vital to address vulnerabilities such as CVE-2024-23692 promptly to prevent malicious exploitation.
What Is CVE-2024-23692?
CVE-2024-23692 (CVSS: 9.8) is a critical command injection vulnerability that allows remote, unauthenticated attackers to execute arbitrary commands on an affected system by sending a specially crafted HTTP request. Disclosed in late May 2024, the vulnerability quickly saw the release of a Proof-of-Concept (PoC) exploit, leading to numerous exploitation attempts observed by researchers.
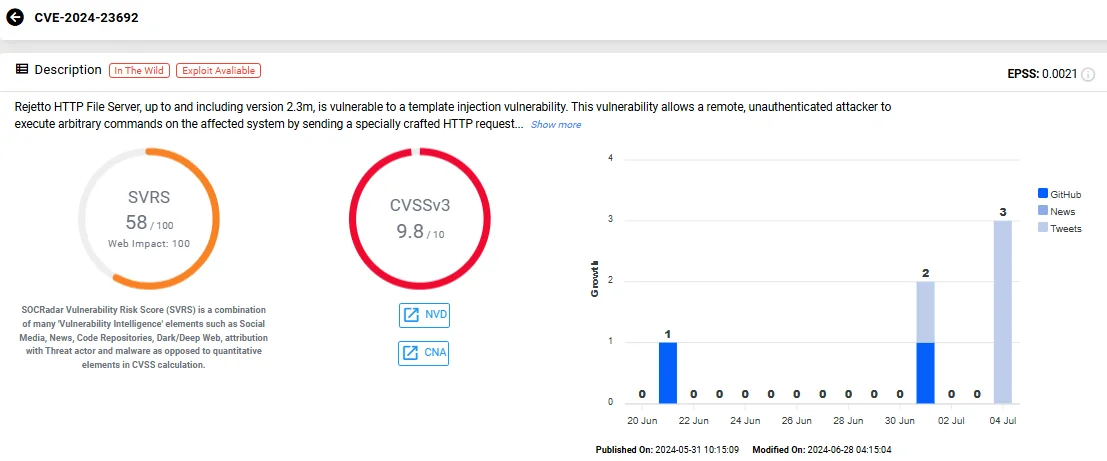
Vulnerability card of CVE-2024-23692 (SOCRadar Vulnerability Intelligence)
Researchers identified active exploitation by observing the HTTP File Server (HFS) process installing malware. The attacks targeted version 2.3m, which is widely used, although known to be vulnerable. It is believed that the CVE-2024-23692 vulnerability was exploited in these attacks.
With SOCRadar’s Vulnerability Intelligence, you can access detailed insights and updates on vulnerabilities, including information about available exploits, enabling a proactive and vigilant cybersecurity posture.
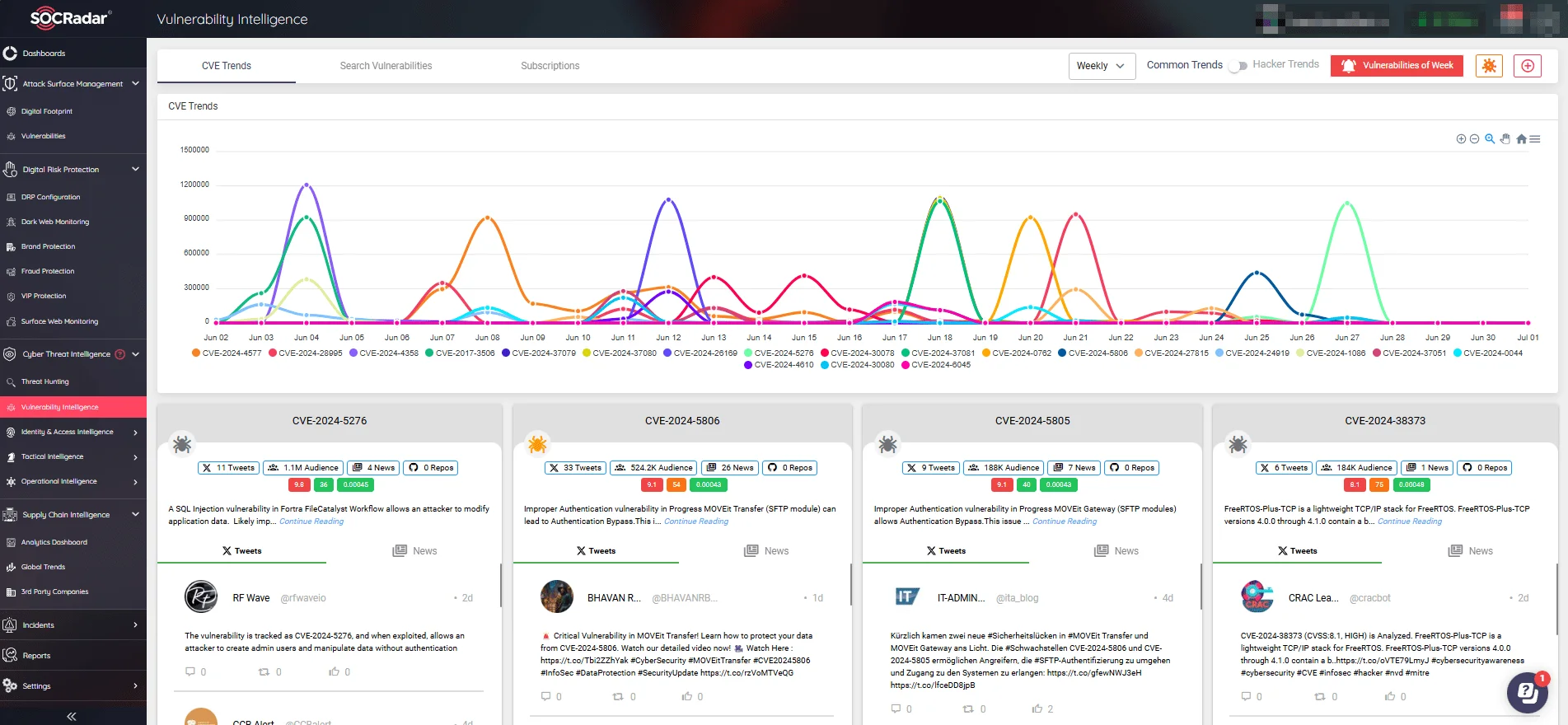
Keep track of new CVEs, hacker trends, and exploits (SOCRadar’s Vulnerability Intelligence)
Which Software and Versions Are Affected?
The CVE-2024-23692 vulnerability affects Rejetto HTTP File Server versions up to and including 2.3m.
How Do Attackers Exploit CVE-2024-23692 in HTTP File Server Attacks?
Attackers exploit CVE-2024-23692 by deploying cryptomining malware, backdoors, Remote Access Trojans (RATs), and other malware like “GoThief” to exfiltrate sensitive data.
After gaining initial access, attackers run commands like ‘whoami’ and ‘arp’ to gather system information. They then create hidden backdoor accounts to establish persistence via RDP (Remote Desktop Protocol).
In the attacks, attackers were frequently observed terminating the HTTP File Server (HFS) process after their activities, likely to reduce the risk of detection and prevent other threat actors from using the compromised system. Moreover, based on the malware strains and commands used in these attacks, researchers believe most of them are carried out by Chinese-speaking threat actors.
Which Malware Were Used in Attacks?
Researchers stated that there has been a range of attacks targeting HFS servers with the CVE-2024-23692 vulnerability, and they predominantly involved cryptomining malware, namely the XMRig CoinMiner to mine Monero cryptocurrency.
Reportedly, at least four threat actors are attacking HFS servers, including the known “LemonDuck.”
The attacks also utilize Remote Access Trojans (RATs) and backdoor malware like XenoRAT, Gh0stRAT, and PlugX, which allow attackers to maintain persistent control over compromised systems.
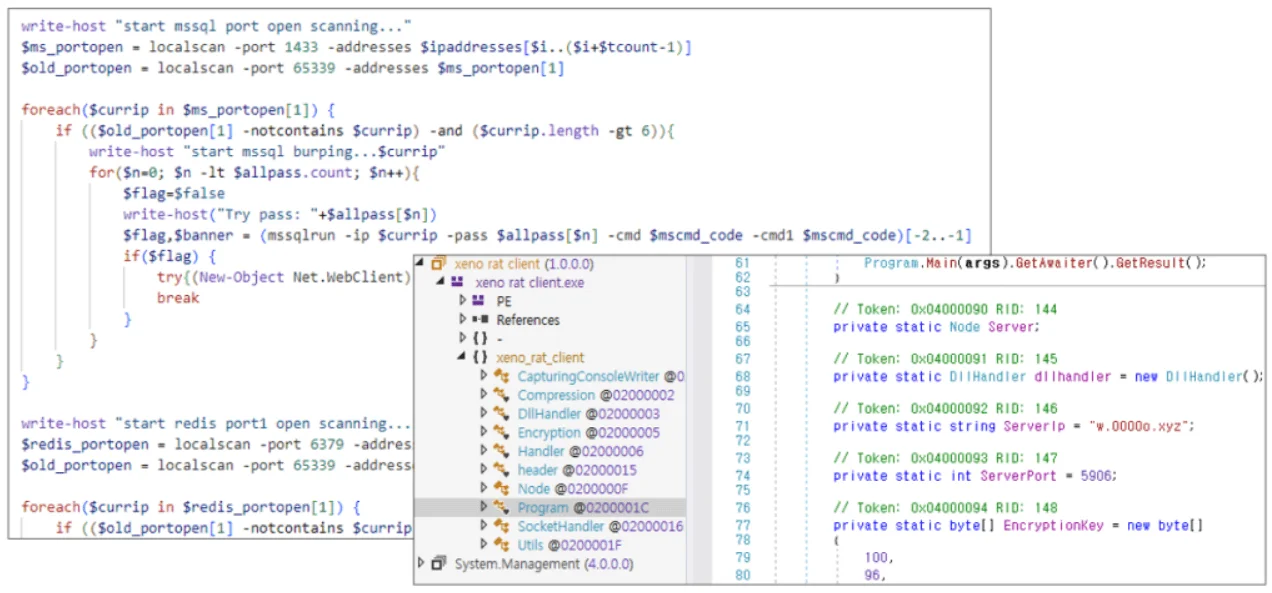
Vulnerability scanner malware and XenoRAT used in attacks attributed to LemonDuck (ASEC)
Another significant piece of malware involved is GoThief, an infostealer developed in the Go language. Attackers use GoThief to exfiltrate data via Amazon AWS. After capturing screenshots, GoThief employs the Amazon S3 service to collect desktop files, uploaded screenshots, and IP address information, which is then sent to the attacker’s Command and Control (C2) server.
With SOCRadar’s Malware Analysis module, you can analyze various file types, from binary to office files, including EML files, and receive immediate reports.
With SOCRadar’s Malware Analysis module, you can analyze a variety of files, from binary to office files, including EML files, and receive immediate reports.
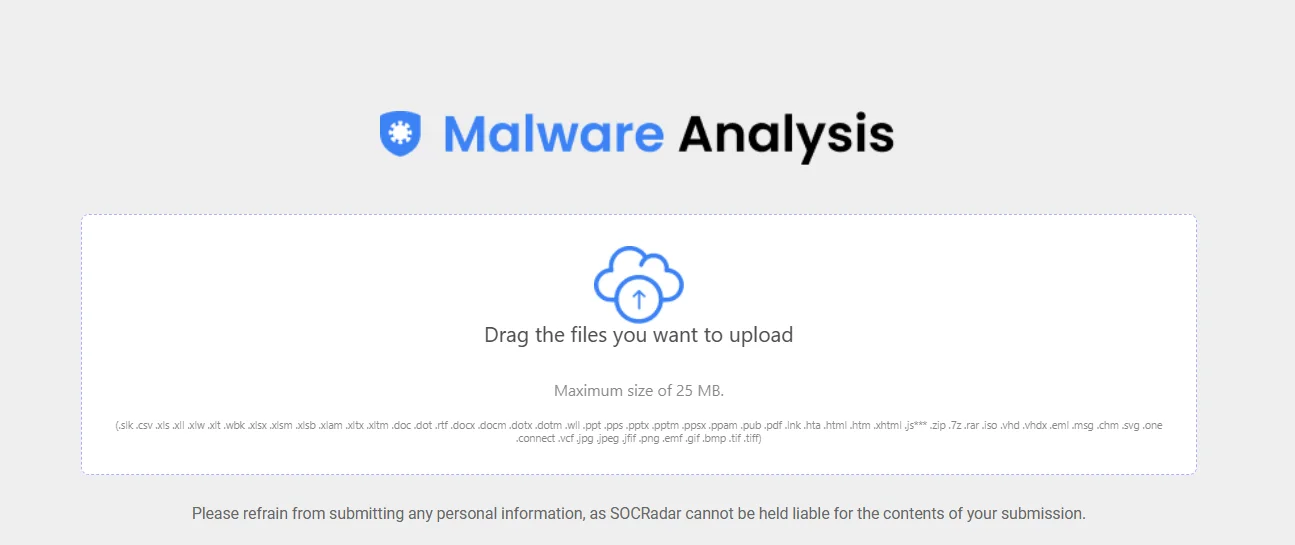
Malware Analysis (available on the SOCRadar XTI platform) aims to provide users with a thorough understanding of malware samples, enabling quick detection and analysis.
How Can You Address CVE-2024-23692?
To prevent the exploitation of CVE-2024-23692, update to the latest version of HTTP File Server (HFS).
For those using a vulnerable version, it is advised to examine your system for any signs of unauthorized access or suspicious activities as you update. Also, see the Indicators of Compromise (IoCs) section at the end of this blog post.
In addition to manual checks, use SOCRadar’s Vulnerability Intelligence module for in-depth insights. Complementing this, you can leverage the Attack Surface Management (ASM) module to monitor your digital assets in real-time. SOCRadar’s alerts provide timely notifications about emerging security issues and vulnerabilities, helping you protect your organization proactively.
SOCRadar’s Attack Surface Management, Company Vulnerabilities
Indicators of Compromise (IoCs)
Below are the Indicators of Compromise (IoCs) associated with the active exploitation of the CVE-2024-23692 vulnerability, as identified by ASEC.
MD5 Hashes
- ce7dc5df5568a79affa540aa86b24773 – Gh0st RAT (2345.exe)
- 8f0071027d513867feb3eb8943ccaf05 – Gh0st RAT (systeminfo.exe)
- 77970a04551636cc409e90d39bbea931 – PlugX Loader (Roboform.dll)
- 6adaeb6543955559c05a9de8f92d1e1d – PlugX (Encoded) (WindowsWatcher.key)
- 4383b1ea54a59d27e5e6b3122b3dadb2 – GoThief (conost.exe)
Command and Control (C2) Servers
- 154.201.87[.]185:999 – Gh0st RAT
- 164.155.205[.]99:999 – Gh0st RAT
- support.firewallsupportservers[.]com:80/443/53/8080 – PlugX
- hxxp://188.116.22[.]65:5000/submit – GoThief
Download URLs
- hxxp://121.204.249[.]123/2345.exe – Gh0st RAT
- hxxp://121.204.249[.]123:8077/systeminfo.exe – Gh0st RAT
- hxxp://185.173.93[.]167:13306/Roboform.dll – PlugX Loader
- hxxp://185.173.93[.]167:13306/WindowsWatcher.key – PlugX (Encoded)
- hxxps://imgdev.s3.eu-west-3.amazonaws[.]com/dev/20210623/conost.exe – GoThief

