VMware recently issued an advisory (VMSA-2023-0026) regarding a critical authentication bypass vulnerability in its VMware Cloud Director Appliance (VCD Appliance). Identified as CVE-2023-34060, this vulnerability poses a significant risk with a CVSSv3 score of 9.8, indicating its critical severity. The issue was first disclosed on November 14, 2023 to VMware by Dustin Hartle from Ideal Integrations Inc.
 CISA’s alert for the vulnerability, VMware Cloud Director Appliance – CVE-2023-34060
CISA’s alert for the vulnerability, VMware Cloud Director Appliance – CVE-2023-34060
CISA, the Cybersecurity and Infrastructure Security Agency, has issued a security alert to caution users about the issue and recommends implementing patch updates as soon as possible.
Details of the Vulnerability in VMware Cloud Director Appliance, CVE-2023-34060
CVE-2023-34060 is an authentication bypass vulnerability found in VMware Cloud Director Appliance, particularly in instances where the appliance was upgraded to version 10.5 from an older version. VMware’s evaluation categorizes this issue in the critical severity range, with a maximum CVSSv3 base score of 9.8, underscoring its potential impact.
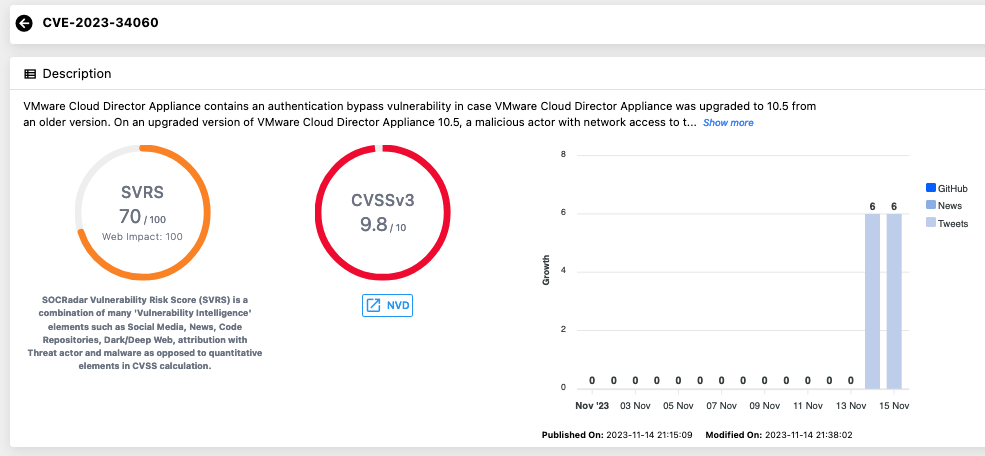 CVE-2023-34060 vulnerability card from Vulnerability Intelligence module of SOCRadar
CVE-2023-34060 vulnerability card from Vulnerability Intelligence module of SOCRadar
The vulnerability is critical due to its potential to allow malicious actors with network access to bypass login restrictions. The bypass is specifically feasible on ports 22 (SSH) and 5480 (appliance management console) on upgraded versions of VMware Cloud Director Appliance 10.5. Interestingly, according to details shared in VMware’s advisory, it is not present in new installations of version 10.5, nor on port 443 (VCD provider and tenant login).
Which Versions of VMware Cloud Director Are Affected?
The affected product is VMware Cloud Director Appliance, particularly version 10.5 that has been upgraded from version 10.4.x or below. New installations of version 10.5 and versions 10.4.x and below are not impacted by this vulnerability.
Mitigation and Remediation
To address CVE-2023-34060, VMware has provided guidance in KB95534, available in the ‘Fixed Version’ column of the ‘Response Matrix’. Users of impacted systems should follow this guidance promptly to mitigate the vulnerability.
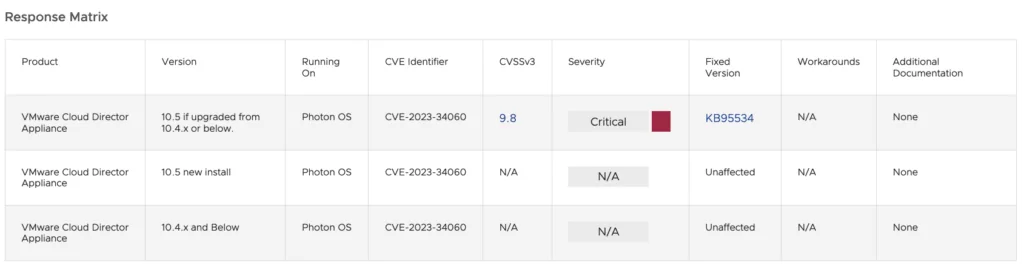 Response Matrix from VMware’s blog post
Response Matrix from VMware’s blog post
Workarounds and Additional Documentation
Currently, there are no workarounds available for this vulnerability. Users are advised to refer to the original VMware security advisory and the associated knowledge base article for detailed instructions on remediation.
Notes and Additional Information
It is important to note that only deployments upgraded to version 10.5 from an older release are impacted. The underlying issue stems from a version of sssd in Photon OS, which is utilized by VMware Cloud Director Appliance and is affected by CVE-2023-34060. More information can be found in the VMware Photon OS security advisory, on GitHub.
Stay vigilant and Always Updated with SOCRadar Extended Threat Intelligence
The discovery of CVE-2023-34060, a critical vulnerability in VMware Cloud Director Appliance, underscores the ever-present need for robust cybersecurity measures. In today’s rapidly evolving threat landscape, merely reacting to security threats is no longer sufficient. Proactive measures are essential, and this is where SOCRadar’s Extended Threat Intelligence (XTI) plays a pivotal role.
 SOCRadar XTI’s Vulnerability Intelligence Module.
SOCRadar XTI’s Vulnerability Intelligence Module.
Proactive Vulnerability Management
- Real-Time Alerts: SOCRadar’s XTI offers real-time alerts on emerging vulnerabilities with its Attack Surface Management (ASM) module, such as CVE-2023-34060. This ensures that organizations are not just aware of potential threats, but are also provided with timely and actionable intelligence.
- Comprehensive Vulnerability Database: With access to an extensive database of known vulnerabilities, SOCRadar’s Vulnerability Intelligence helps organizations stay ahead of threats by providing detailed insights into vulnerabilities, their severity, and the affected systems.
- Risk Prioritization: Not all vulnerabilities pose the same level of threat to every organization. SOCRadar’s XTI helps in prioritizing vulnerabilities based on their relevance and potential impact on your specific environment. This way, resources can be allocated effectively to address the most critical threats first, such as CVE-2023-34060.
The post Critical CVE-2023-34060 Vulnerability in VMware Cloud Director Appliance: CISA Advises Immediate Patching appeared first on SOCRadar® Cyber Intelligence Inc..
Article Link: Critical CVE-2023-34060 Vulnerability in VMware Cloud Director Appliance: CISA Advises Immediate Patching
