Crimson is a Remote Access Trojan — a malware that is used to take remote control of infected systems and steal data. This particular RAT is known to be used by a Pakistani founded cybergang that targets Indian military objects to steal sensitive information.
MD5: f940e886a40783deb4e97fe6d842da7a
File Type: MS Excel Spreadsheet
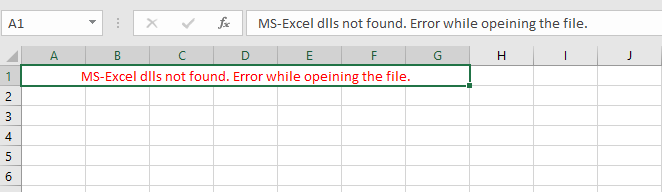 Excel file screenshot
Excel file screenshotVT Score: 35/62

I am using OLETools to get the property of excel file.
 cmd > olemeta.py <file name>
cmd > olemeta.py <file name>Next OLETool command I am running is to get the OLE details.
 cmd > olevba.py -a <filename>
cmd > olevba.py -a <filename>Suspicious Indicators:
- VBA code will auto execute on opening excel workbook.
- Create directory on the system.
- Write a file on the system.
- Execute shell command.
- hex string used for obfuscation.
Now, I am extracting VBA from excel file and dumping it to txt file. For that command I am running is
cmd> olevba.py --deofb <filename> > Path\output.exe
From the VBA code, I can see the subroutine creates a folder and drop executable file at location C:\ProgramData\Rlmdias\Rlmdias.exe

I opened excel and navigate to VBAProject by clicking Alt+F11. Porject was password protect. I removed password using GitHub code and check out my previous blog how it can be done. Post password removal, I can see there is a userForm1 which has two text box and has a hex values which are PE files will dropped depends on the OS version of the victim 32bit or 64bit

I debugged the VBA code and it dropped a zip file at location “C:\ProgramData\Rlmdias\drngervia.zip” and unzip it using function unSadozip


Dropped zip file has drngervia.exe file. and Shell command execute the executable file

when Shell executed, it opens Windows features and ask to download and Install .Net Framework 3.5

Due to dependency on .net framework, I have installed above Windows feature.
Dropped File:
MD5: 10F955EF9F398E91CA9AE4F34CECD873
File Type: Win32 EXE
File Name: drngervia.exe
Signature: Microsoft Visual C# v7.0 / Basic .NET
Family: Crimson also knows as SEEDOOR and Scarimson
Type: Trojan
VT Score: 47/72

I have used dnSpy to debug the PE file. Looking at the code, it creates persistence creating a registry entry.
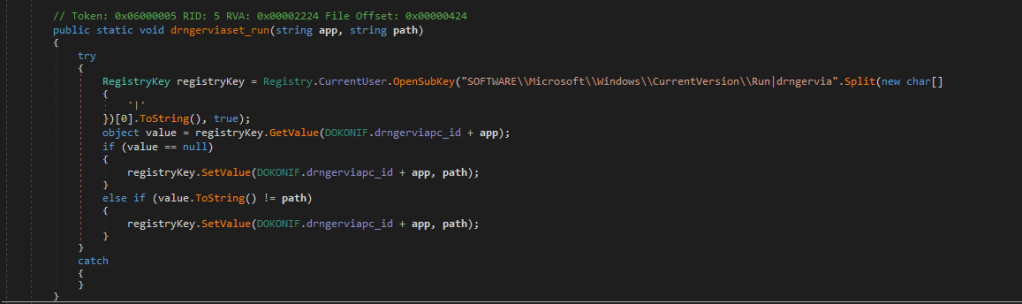
It gets the list of running process on the system
 Collecting list of running process.
Collecting list of running process.It looks for antivirus software running on the system.
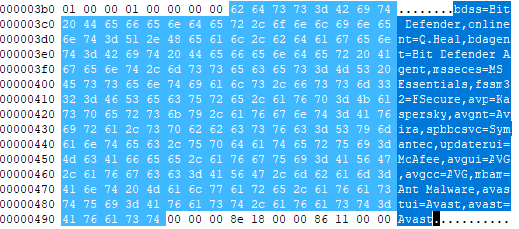
It searches for the antivirus software from the below list.
- Bit Defender
- Quick Heal
- Microsoft Essentials
- F-Secure
- Kaspersky
- Avira
- Symantec
- MacAfee
- AVG
- Avast
Capabilities of this RAT observed from code:
- Get the running process on the system.
- Get the drives, directories and files on the system.
- Get the host name, User id.
- Capture screenshots.
- Get the data from C2 server.
- Using custom ports to connect to C2 server.
On execution, drngervia.exe try to establish connection with C2 server which IP and ports are hard coded in the code. IP address is in the form decimal values. C2 server didnt respond.
| IP Address | Ports |
| 107.175.64.[251] | 6286, 4486, 8249, 11447, 16865 |
I have also found the hard coded IP address, username. Malware never hit to this ip [124.115.201. 118]

Behavior:
- Excel file dropped PE file.
- PE has dependency on .net framework 2.0.
- PE file tried to connect to C2 server but C2 server didn’t respond.
Execution flow:

Download Sample: f940e886a40783deb4e97fe6d842da7a
References:
Article Link: Crimson RAT Malware Analysis – Malware Analysis