Thanks for reading Anchored Narratives on Threat Intelligence and Geopolitics! Subscribe for free to receive new posts and support my work.
Share Anchored Narratives on Threat Intelligence and Geopolitics

Disclaimer: The views, methods, and opinions expressed at Anchored Narratives are the author's and do not necessarily reflect my employer's official policy or position.
Introduction
We’re back with the first-course review of 2025! One that took me much longer than expected, to be honest. The reason why? There is a lot of material to go through. Like many things in life, sometimes I underestimate my challenges, but that is good (LOL) as long as I finish those goals. So why did I choose this Malware Analysis and Development training? Well, it’s being taught by no other than Pavel Yosifovich, a well-known guru in Windows Internals and (kernel) programming. You can find a lot of his books here. I find it crucial that teachers or course instructors are experts in the subject matter. The other goal is to get additional insights into what malware development looks like and where additional artifacts may be collected. In my daily work, I have to examine a lot of malware. Some are simple, but actually, a lot is rather complicated and frequently still beyond my reach.
What also intrigued me about this course was its price. It’s very reasonably priced compared to SANS courses, which last only a week, while this course will at least force you to finish it within several months.
In this anchored narrative, I will review the TrainSec Malware Analysis and Development training by course setup, learning objectives, and lessons learned. I will end it with a Q&A section with one of the course developers, Pavel Yosifovich. Let's go.
Course Setup
Once you onboard into the course, you will receive instructions via e-mail that provide you access to TrainSec's learning platform. They offer multiple interesting courses, which can be found here.
Before logging in to the learning platform, make sure you have set up your Virtual Machine for this course. I used my Virtual Machine for reversing. In this course, you will use the Visual Studio Community edition a lot as you need to complete different labs. Once you're settled, you log in to the portal where the instruction videos, PDFs of the PowerPoints, and a zip file with lab exercises reside. Students can also leverage the customer Discord Channel to ask questions or share solutions.
The course starts with the foundations of Windows internals and then gradually moves to Windows development, Processes, Memory, threads, etc. Every chapter begins with a video recording where Pavel explains the theory and demonstrates how to use different Windows API calls in C++. One thing I enjoyed was how Pavel probed the students for interaction during the course.
Why is there a function of WriteProcessMemory and Why is there a function of CreateRemoteThread?
During the course, you’ll also learn how to use Visual Studio and how to structure your solution in different projects. Pavel exhibits impressive expertise during the training.
During the training, Pavel will code some programs on the fly, like the code below, and probe the students.
HANDLE hThread = CreateRemoteThread(hProcess, nullptr, 0,
(LPTHREAD_START_ROUTINE)GetProcAddress(GetModuleHandle(L”Kernel32”, “LoadLibrary”) ,
buffer, 0, nullptr);
There is a bug here. Anyone can see the bug? Yes, it “LoadLibraryA or LoadLibraryW, but why is LoadLibraryW not prefered. Should I select A or W?
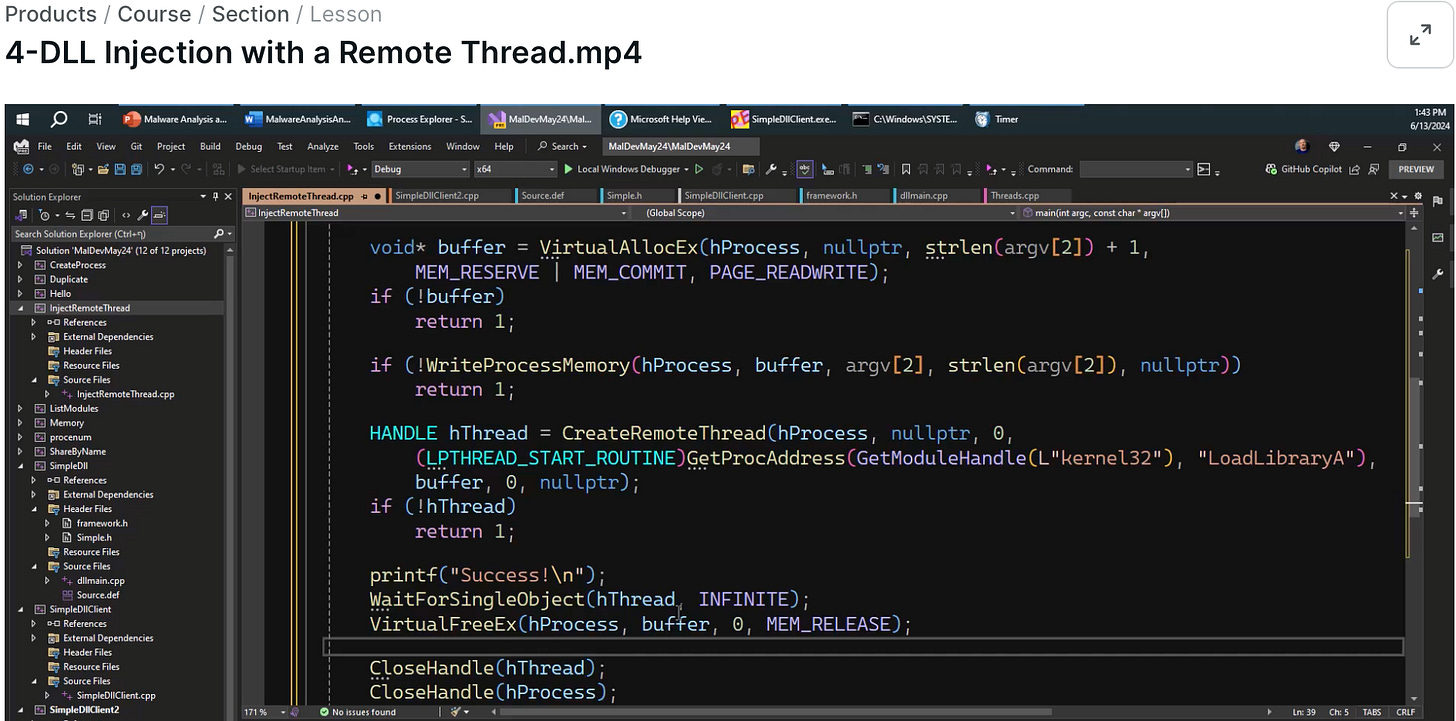
Through this constant probing, the students actively participate in the training but are also challenged on their assumptions. Some of the lessons take around 30 minutes, and some are a bit longer. When you move further in the course, you’ll get into malware development and different DLL injection techniques. Pavel constantly debugs his programs in Visual Studio so you can see what happens in memory or on the stack, for example.
In the example in Figure 2, Pavel emphasized that closing the thread using the VirtualFreeEx call is essential. Otherwise, you’re going to leave a trace of 4KB. This example is also interesting from a memory forensics perspective. VirtualFreeEx is freeing the buffer that contains argv[2], which is the path to the DLL to be injected, that would be gone from process memory. It may still exist in free memory, but you’d see a random dll path in the strings output. However, since it injects with a LoadLibraryA call, it will make a memory forensic artifact as the dll and its path are visible in the DLL lists Windows manages.
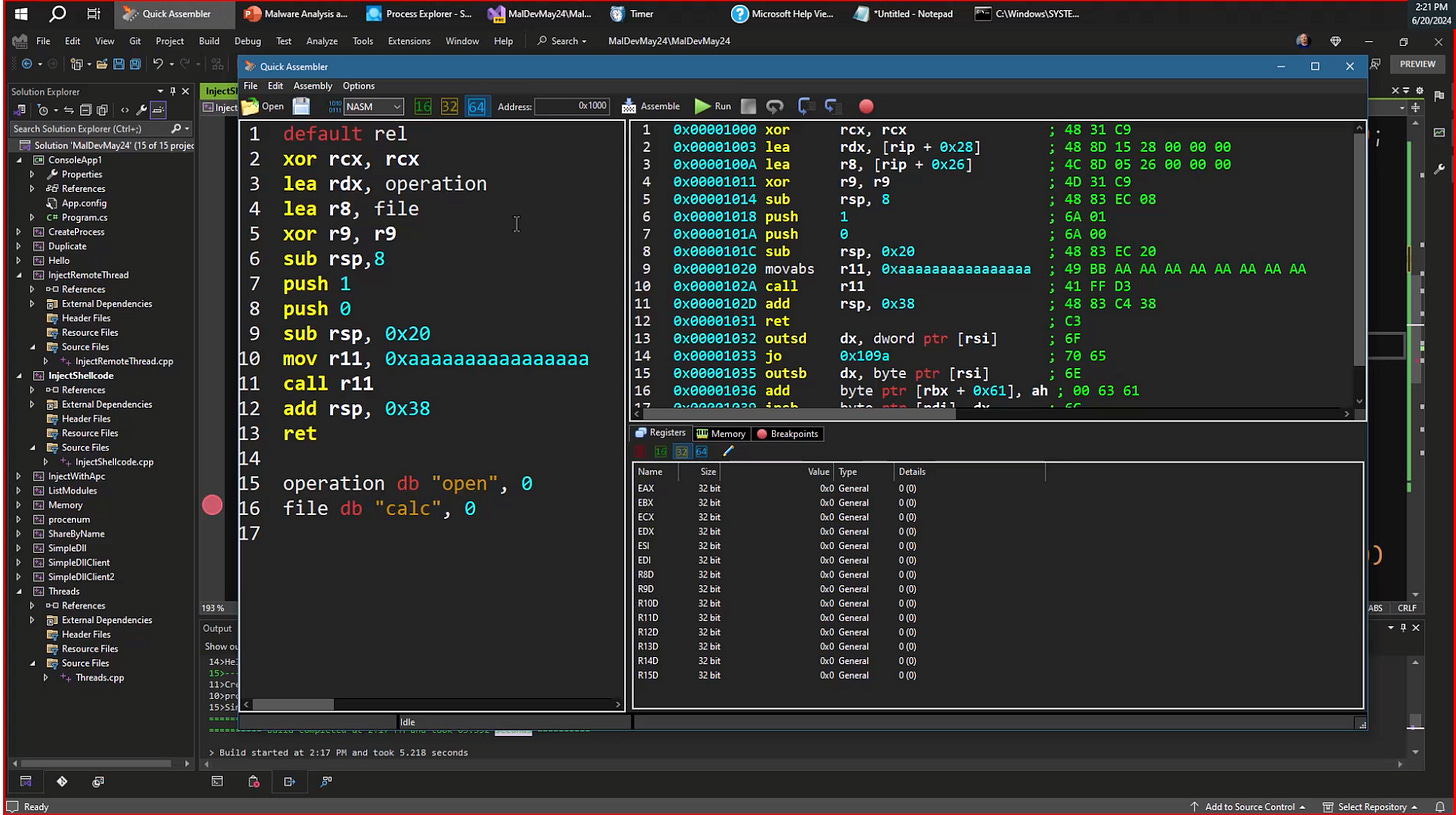
Another thing that makes this course interesting is the use of all the tools Pavel wrote. In the example below, Pavel teaches assembly and using Quick Assembler to handle shellcode. The nice thing about his tools is that the results of your compiled code are actually presented live, providing you with a better understanding of why something will or will not work.
Once you’ve finished the last Windows Malware Development lesson 8, The Native API, Uriel Kosayev takes over the practical Malware section of the course. That section will teach real-life malware cases like SolarWinds Sunburst, Darkside ransomware, unpacking, dynamic API resolving, and other known malware techniques. For those who do not know Uriel, he is the author of the Antivirus Bypass Techniques book, which teaches how many antivirus engines work and how to bypass them.
Course instructors
Pavel teaches most of this course and does it exceptionally well. He will easily take you from minimal knowledge to (advanced) malware development topics. The different labs that you need to complete can still be very challenging for non-developers (me), but you get all the information to pass them. As mentioned in the introduction of this review, Pavel did not disappoint for a second.
Once the practical malware section begins, Uriel will take over. Uriel is very hands-on and pragmatic during the course. Also, Uriel will guide the students on the best approaches to reverse certain malware.
Course Review and Lessons Learned
Like many video courses, it’s sometimes hard to concentrate, but I enjoyed the malware development aspect of this course. I learned a lot about why I’m not a developer, but this course matured me in understanding which techniques a malware author will likely leverage. The course is a recording of a live training session provided by Pavel and Uriel to students, and the quality is good. Sometimes, you'll hear some people entering the MS Teams meetings, but you’ll get used to that. The course content and learning environment is excellent.
After lesson 8, I was used to Pavel’s teaching style and methods, and for me, it was a bit of a strange transition to get to the actual malware techniques and cases presented by Uriel. Although Uriel does a nice job, it is much more practical, and I missed actual challenges there.
Overall, the course is well structured, and if you’re interested in malware development or Windows Internals, this course is for you.
If you want to subscribe to this course, you can find it here on the TrainSec website. Good luck.
Buy or Not
This course aims to teach malware development skills in Visual Studio by leveraging C++, and I find its strength in the challenging labs that accompany it.
The malware practical session was less interesting for me because it has been covered by other courses I have written on this blog. I really think that a lot of SOC and DFIR analysts will mature their development and reversing skills. The pricing of this course ($890) is very competitive, especially compared to industry-recognized training, which usually end up in 4k to 5k.
So, this course is a buy, but you have to be disciplined enough to fulfill the challenges. As mentioned previously, the learning environment is very nice, but add some actual samples for the students to investigate in the later section of the course.
That said, I’m very happy that I took this course, as it confronted me with several assumptions. I also enjoyed using Visual Studio a lot and learned new tools that are good to use in actual malware cases. TrainSec also provides other training that covers Kernel Programming, Windows Internals, and Malware Analyst Professional—Level 1 and 2. By looking at the course outline of the Malware Analyst Professional 1 and 2, actual malware samples, process injection and malware unpacking techniques will be taught in those courses.
Q&A with Pavel Yosifovich
During the malware course, I asked Pavel if he would be interested in an interview for the Anchored Narratives site. He agreed and responded directly to my questions. You can read it below.
Tell us about yourself and why you started the Trainsec platform.
I've been in the IT space for almost 30 years now. I like programming, writing and teaching. I felt there was a lack of good courses on programming and Windows Internals topics, both I am passionate about. So I decided (with Uriel), to create Trainsec, and have some of my passion, knowledge and experience available to a larger audience than a single class can provide.
2. You have made several tools, like Total PE, that you demonstrated in the malware analysis and development course. Where can users download your tools, and are there release versions of them?
All my tools are available in my Github repos at https://github.com/zodiacon. They are all open source and free. The “AllTools” repo is convenient for getting everything, although not all binaries there are up to date.
3. During the course, you clearly repeat the students' questions and code examples on the fly. Could you share a picture of your instruction setup?
4. Why did you start this malware analysis and development course, as there are many already, and why do you think students should prefer it?
I am not very familiar with other such courses, similar or otherwise. I felt Uriel and I have something significant and unique to contribute, so we decided to create this course. I think the course doesn't shy from details, which I think are very important, understanding exactly what is going on. Other courses I heard about are vague in that regard, demonstrate things with partial explanations. I want my courses to increase participants understanding. As the saying goes, give someone a fish, they will be hungry again tomorrow; teach someone to fish - they will have food for a lifetime.
5. What is the most advanced malware you have seen or analyzed?
I don't usually analyze malware, it's just not something I like doing. I did some analysis on samples Uriel provided, but it was just for basic understanding of the malware's behavior. My focus is on creation, rather than analysis.
6. During the course, you often give advice on stealthy techniques, but if you make advanced malware, can you explain which potential flaws in EDR technology you would leverage to avoid detection and how you remain stealthy for at least a longer time?
Well, I could talk about potential ways to bypass EDRs, but each EDR is different, different techniques may work on different EDRs. I'd rather not go into that.
7. If you were to write your most advanced Windows malware, how would you approach it, and which less-known API functions would you use?
I'd rather not discuss these kinds of things publicly.
8. You mentioned during the course that you do not like reverse engineering. Can you elaborate on that?
Reverse engineering is a difficult art and science - it requires a lot of base knowledge in so many areas, like OS internals, assembly, reversing tools, CPU architecture, C programming, and possibly more. Not to mention concentration and perseverence. My focus is on building new things rather than reversing existing code. I love writing code much more than I do reversing binaries. Sometimes I do that to better understand something an OS is doing, but I don't enjoy that.
9. Any practical advice you would like to give malware reversers in their goal to become better reversers?
I always say start with the foundations. I encounter people who want to be reverse engineers, or malware developers, but they try to take shortcuts like using existing tools with little understanding. This will not make anyone truly great. You have to do the work - learn how computers work, CPU and system architecture, OS internals, C programming (at least), assembly for x86/x64 (at least) - only then can you truly be productive and reach new heights. It's like building a house. If you start with the roof, you won't get far; start with the foundations.
Introduction to Malware Binary Triage (IMBT) Course
Looking to level up your skills? Get 10% off using coupon code: MWNEWS10 for any flavor.
Enroll Now and Save 10%: Coupon Code MWNEWS10
Note: Affiliate link – your enrollment helps support this platform at no extra cost to you.
Article Link: Course Review - TrainSec Malware Analysis and Development