Introduction
Organizations are shifting towards cloud-native architectures to meet the efficiency and scalability needs of today. But along with the adoption of containers, microservices, and Kubernetes comes increased risks such as poor visibility, ineffective vulnerability management, and inadequate run time protection.
CrowdStrike provides security coverage throughout the CI/CD pipeline and continuously manages cloud risk by delivering complete security for cloud-native applications. By shifting left and proactively assessing containers, CrowdStrike can identify any vulnerabilities, embedded malware, stored secrets, or CIS benchmark recommendations even before they are deployed.
In addition to ensuring containers are secure before deployment, CrowdStrike enables runtime protection that stops active attacks by providing continuous detection and prevention. This allows security teams to provide security for their cloud estate both before and after the deployment of a container.
Video
<span data-mce-type="bookmark" style="display: inline-block; width: 0px; overflow: hidden; line-height: 0;" class="mce_SELRES_start"></span><span data-mce-type="bookmark" style="display: inline-block; width: 0px; overflow: hidden; line-height: 0;" class="mce_SELRES_start"></span><span data-mce-type="bookmark" style="display: inline-block; width: 0px; overflow: hidden; line-height: 0;" class="mce_SELRES_start"></span>
Shifting Container Security to the Left
Before an image is deployed, CrowdStrike can analyze an image and surface any security concerns that may be present.
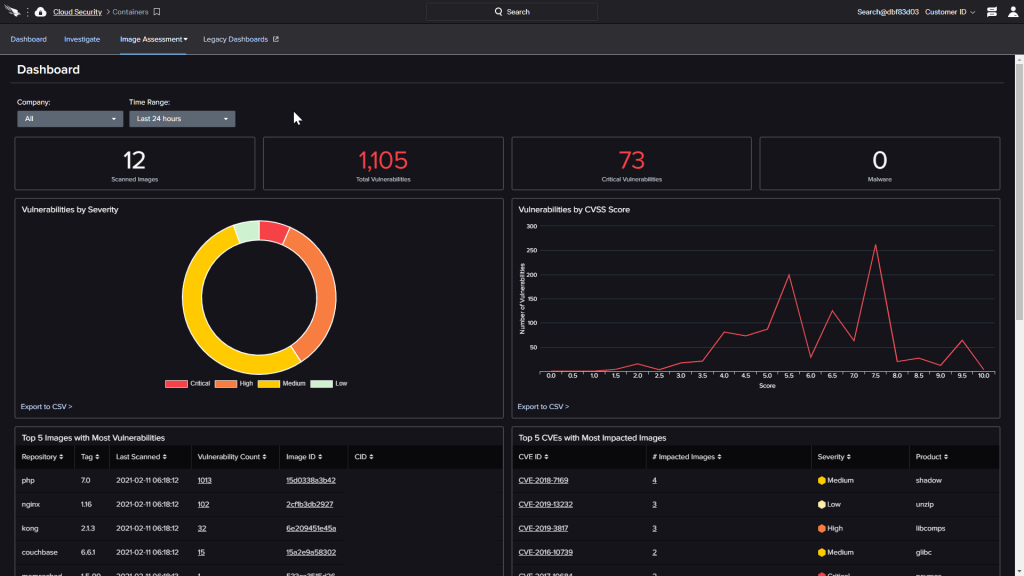
Easy to read dashboards shows high value data such as vulnerabilities by CVE severity and the 5 images with the most vulnerabilities. It is critical that images with a large number of severe vulnerabilities are remediated before deployment.
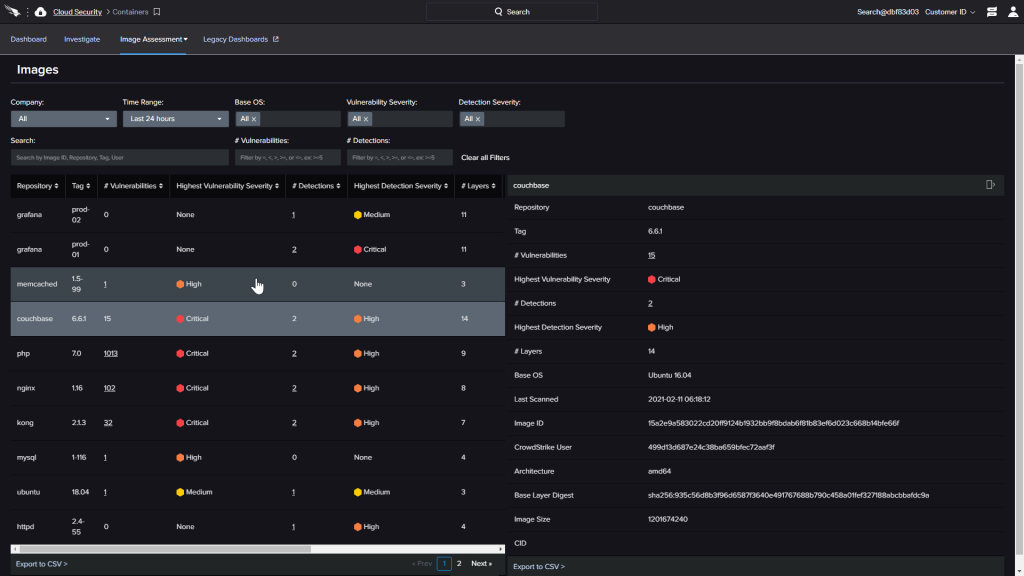
There is also a view that displays a comprehensive list of all the analyzed images. Additional details include the severity of any detections or vulnerabilities found on the image.
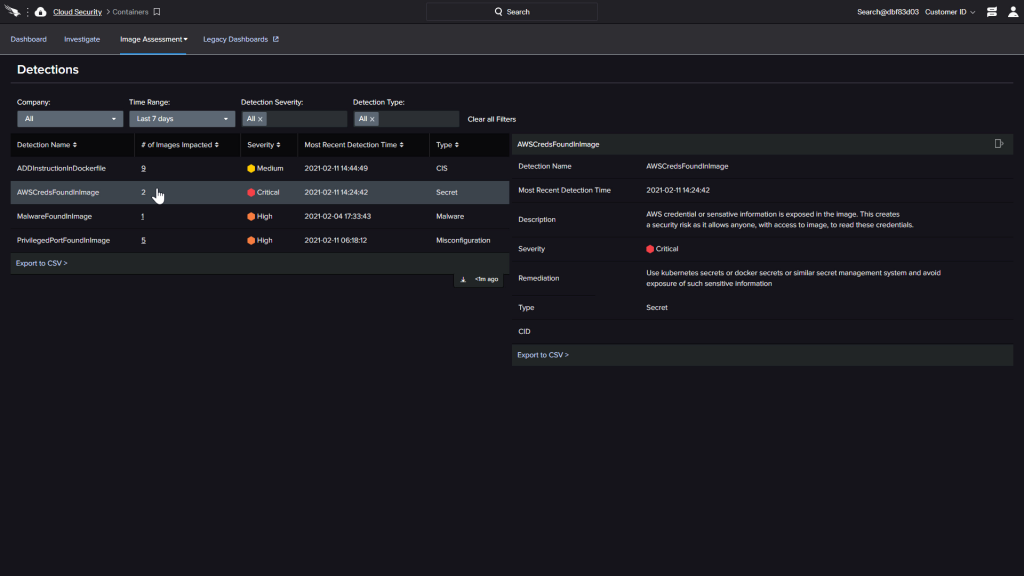
Detections will show us any CIS benchmarks deviations, Secrets identified, malware detected, and CrowdStrike identified misconfigurations within the image. Any issues identified here signal a security issue and should be investigated.
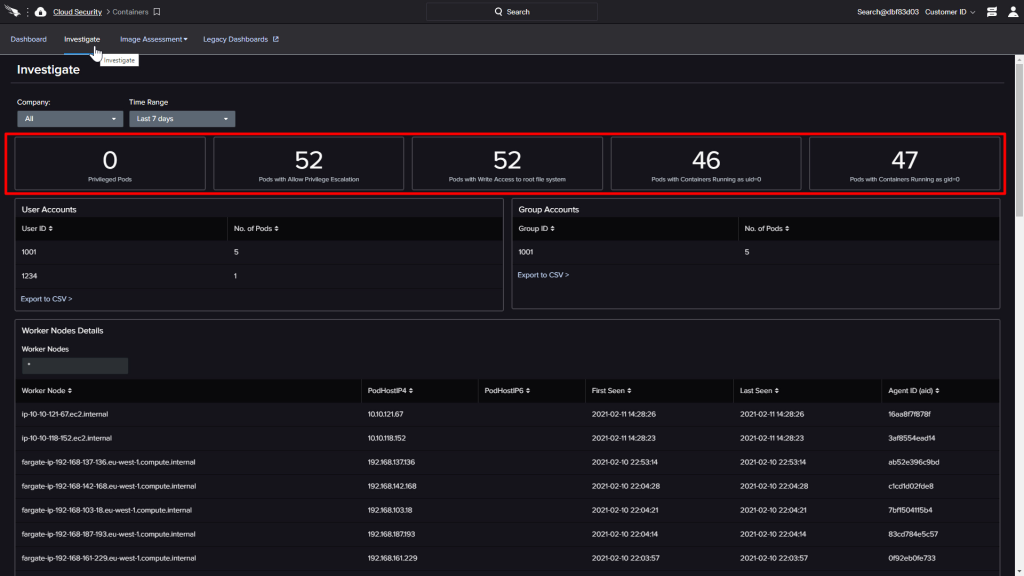
Also available are investigations. At the top, investigations will highlight pods running with potentially insecure configurations that might not be readily apparent within the Kubernetes interface.
Runtime Security
In addition to analyzing images before deployment, CrowdStrike also provides runtime security to detect and prevent threats while the container is running.
For systems that allow applications to be installed on the underlying Operating System, the Falcon Sensor can be installed to protect the underlying OS as well as any containers running on top of it.
But for situations where the underlying OS is locked down, such as a serverless container environment like AWS Fargate, CrowdStrike has designed a solution to work with any Kubernetes deployment that only requires a single Falcon Container within a pod to provide security and doesn’t require a full agent within each individual container.
With this approach, the Falcon Container can provide full activity visibility, including process, file, and network information while associating that with the related Kubernetes metadata.
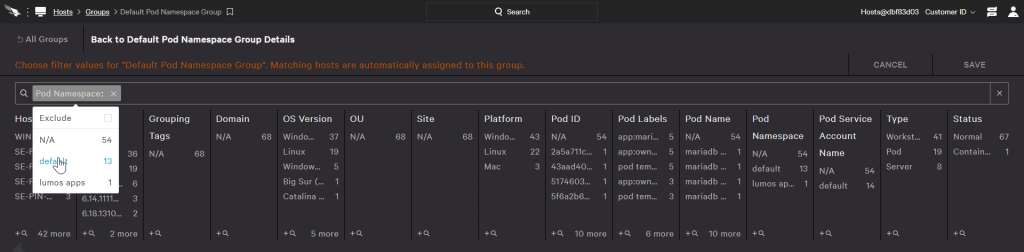
A filter can use Kubernetes Pod data to dynamically assign systems to a group. This allows policies to be assigned to systems based on Pod details, such as the Pod Namespace.
After the policies are assigned, when a new threat is detected within a container, it will be visible in the Falcon console just like any other detection and provide a unified experience for the security teams.
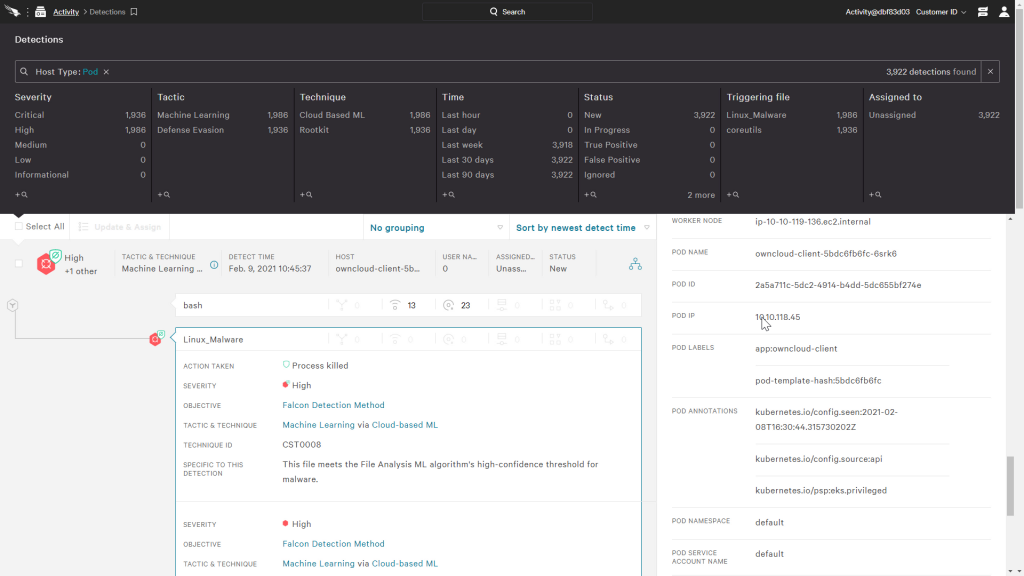
This ensures that a seamless workflow experience is provided for all detected threats, but we can still view just the detections within pods by filtering with the host type, pod. And when we look at detections within pods, CrowdStrike is about to provide additional details that are unique to pods.
Not only is the process tree available to analyze the attack behavior, additional host details provide important pod information, such as the pod name, pod id, and pod namespace.
Conclusion
CrowdStrike provides advanced container security to secure containers both before and after deployment.
By shifting security to the left, this enables security teams to save valuable time by proactively defending against threats. And after deployment, Falcon Container will protect against active attacks with runtime protection.
More resources
- CrowdStrike Tech Center
- Sign up for a weekly Falcon demo
- Request a 1:1 Demo
- Guide to AV Replacement
- CrowdStrike Products
The post Container Security with CrowdStrike appeared first on .
Article Link: https://www.crowdstrike.com/blog/tech-center/container-security/