Committing a Sin, OpenJS Foundation and XZ Utils Incidents: Lessons in Open Source Security
Recent events have brought to light critical issues related to cybersecurity threats and social engineering tactics. The attempted backdoor incident involving XZ Utils and, a short time later, a credible takeover attempt was intercepted by the OpenJS Foundation.
Security researchers have uncovered a credible takeover attempt and a novel attack vector targeting the OpenJS Foundation in a manner that evokes similarities to the recently uncovered incident aimed at the open-source XZ Utils project.
The OpenJS Foundation received a suspicious series of emails with similar messages, bearing different names and overlapping GitHub-associated emails, the foundation said in a joint alert.
According to authorities at OpenSSF, the email messages urged OpenJS to take action to update one of its popular JavaScript projects to remediate critical vulnerabilities without providing any specifics.
Before diving into the details of the subject, let’s remember XZ Utils.
XZ Utils Incident: A Wake-Up Call
The very recent discovery of a potential backdoor CVE-2024-3094 in XZ Utils served as a reminder of the vulnerabilities that open-source projects can face. Although thwarted before reaching stable releases, the incident revealed a sophisticated social engineering strategy targeting the project’s lone maintainer, Jia Tan.
This event emphasized how important it is to carefully check and verify people who contribute to and look after open-source projects and the term maintainer burnout. While not the first instance, it left a lasting impact as a highly important event and a successful research outcome that demonstrated the severity of such incidents.
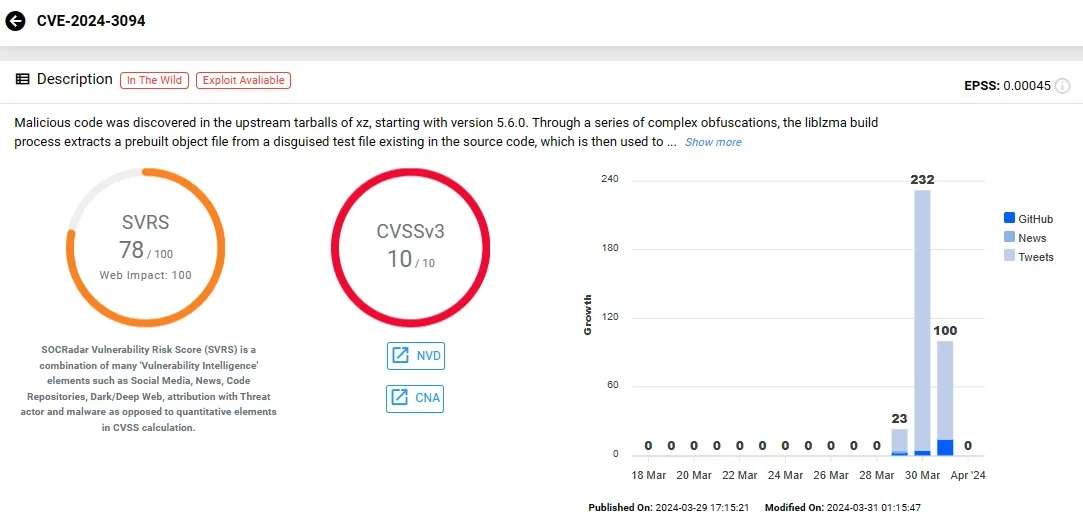
XZ Utils, CVE-2024-3094 in SOCRadar Platform
Be sure to check out “What Do You Need to Know About the Linux XZ Utils Vulnerability, CVE-2024-3094?”
OpenJS Foundation’s Alert
In a similar story, the OpenJS Foundation encountered a credible takeover attempt through suspicious emails urging immediate action on JavaScript projects. These emails, reminiscent of tactics seen in the XZ Utils incident, sought to gain privileged access as project maintainers without prior involvement or specific details on vulnerabilities.
As stated by the researchers, the email sender requested OpenJS to appoint them as a new maintainer of the project, even though they had little prior involvement. Additionally, two other popular JavaScript projects not hosted by OpenJS experienced similar activities.
Therefore, this incident sheds light on the method used to target the sole maintainer of XZ Utils with fake identities, part of what seems to be a social engineering campaign aimed at making Jia Tan a co-maintainer of the project.
So, the point is that the attempt to compromise XZ Utils might not be an isolated event but rather part of a broader effort to undermine the security of multiple projects, according to statements from the two open-source groups. The specific JavaScript projects involved were not named.
Jia Tan has no digital presence beyond their project contributions, suggesting that the account was created solely to gain credibility within the open-source community over time and eventually introduce a hidden backdoor into XZ Utils.
The OpenJS Foundation swiftly responded, flagging the potential security risks and collaborating with relevant authorities such as the Cybersecurity and Infrastructure Security Agency (CISA).
OpenSSF also provided some tactics and recommendations, to summarize:
Recognizing Early Threat Patterns
The recent incidents involving attempted takeovers have unveiled certain recurrent patterns that signify potential social engineering threats, and these basically summarize the similarities and the dangerous attack vector:
- Friendly yet Aggressive Pursuit: In both instances, there was a notable trend of unknown individuals aggressively pursuing maintainer roles within the projects, despite lacking a substantial history or presence within the community.
- Endorsement by Unknown Entities: These individuals often garnered support from obscure or unfamiliar members, raising suspicions of fabricated identities or “sock puppets” employed to bolster their credibility and influence.
- Obfuscated Code and Security Concerns: The tactics employed included the use of convoluted and obscured code, a gradual escalation of security issues, and a departure from established project norms and protocols.
Lessons and Recommendations
These incidents have provided valuable insights, leading to the following key takeaways and recommendations:
- Heightened Vigilance and Strengthened Authentication: Maintaining a vigilant stance against social engineering tactics is critical, alongside the implementation of robust authentication measures for both contributors and maintainers.
- Collaborative Security Initiatives: Encouraging collaboration among open-source projects, foundations, and cybersecurity entities is crucial for effectively identifying and responding to potential threats in a coordinated manner.
- Embrace Best Practices and Utilize Resources: Adhering to industry-standard security practices, leveraging resources such as the OpenSSF Guides, and prioritizing routine security audits and thorough code reviews are essential steps in fortifying project security.
- Comprehensive Support for Maintainers: It is imperative to ensure that project maintainers receive comprehensive support, including technical assistance and access to funding initiatives. This not only bolsters project security but also contributes to its long-term sustainability and success.
As the open-source community navigates evolving cybersecurity challenges, collaboration, vigilance, and proactive security measures remain critical. By learning from recent incidents, implementing best practices, and fostering a supportive environment for maintainers, we can collectively enhance the security and sustainability of open-source projects for the benefit of all stakeholders. Therefore, another facet of the incident emerges when evaluated in the Supply Chain context, the project maintainer is not the only one responsible and in trouble.
How Can SOCRadar Help?
SOCRadar’s Supply Chain Intelligence is a powerful tool for safeguarding against software supply chain attacks. It offers a comprehensive view of vulnerabilities, exploits, and hacker trends across your entire supply network. With automated detection, you can swiftly identify third-party environments and prioritize analysis based on risk levels. The system’s data-driven approach helps in evaluating cyber exposure and directing security efforts where they’re most needed. Customizable alarms further enhance your ability to focus resources effectively, ensuring proactive protection against evolving threats in your supply chain.
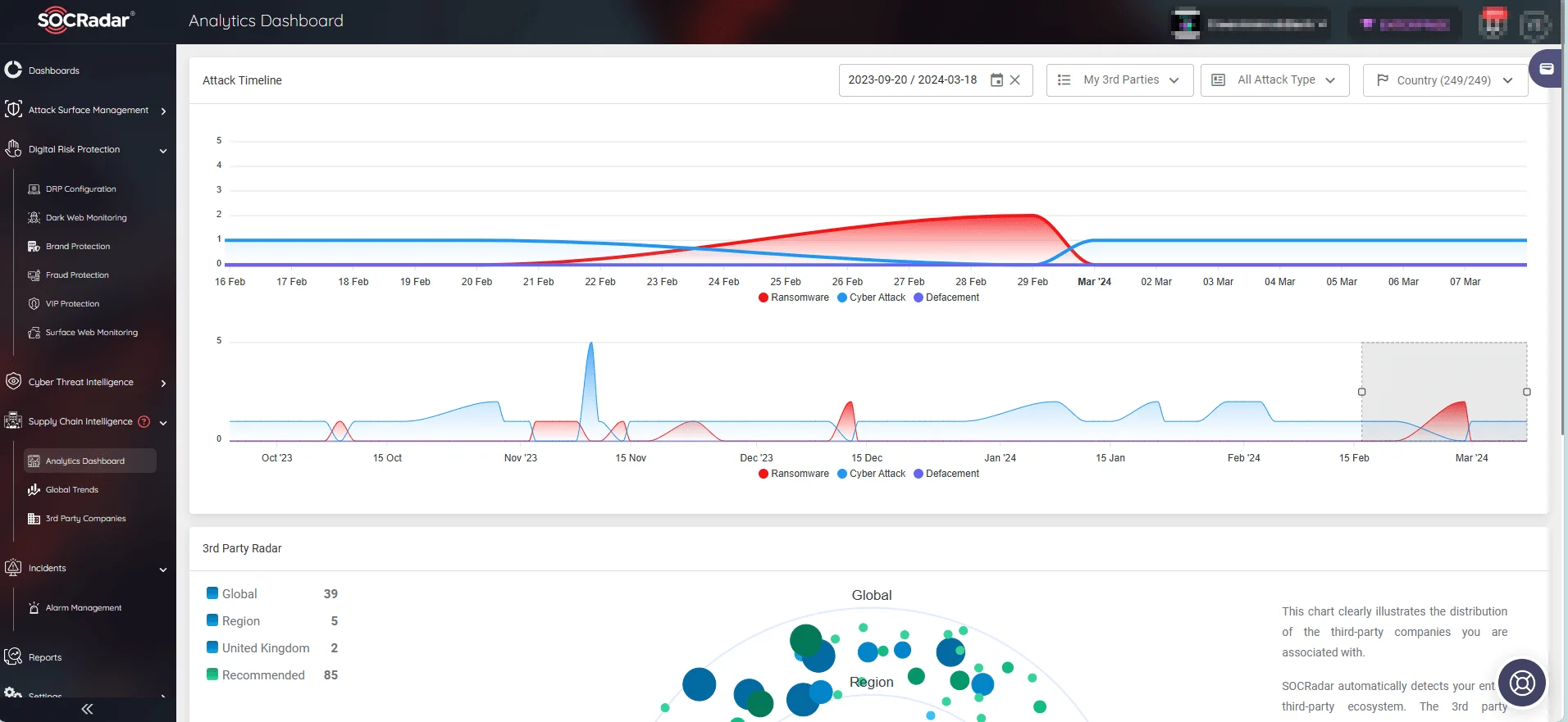
SOCRadar, Supply Chain Intelligence
Moreover, SOCRadar extends support in phishing defense efforts through its Malware Analysis module. This feature allows users to conduct in-depth analysis of a wide range of file types, from binaries to Office files, including EML files, and receive immediate reports on uploaded files.
SOCRadar’s Malware Analysis tool is specifically designed to provide users with a comprehensive understanding of malware samples, facilitating rapid identification and analysis. With a host of functionalities aimed at assisting security teams in combating and mitigating potential threats, SOCRadar stands out as a valuable asset in enhancing cybersecurity measures. Additionally, users can access the EML analyzer and Grader features separately within SOCRadar Labs at no cost.
Article Link: https://socradar.io/committing-a-sin-openjs-foundation-and-xz-utils-incidents-lessons-in-open-source-security/