This post is authored by Jeremiah O’Connor and Dave Maynor with contributions from Artsiom Holub and Austin McBride.
Executive Summary
Cisco has been tracking a bitcoin theft campaign for over 6 months. The campaign was discovered internally and researched with the aid of an intelligence sharing partnership with Ukraine Cyberpolice. The campaign was very simple and after initial setup the attackers needed only to continue purchasing Google AdWords to ensure a steady stream of victims. This campaign targeted specific geographic regions and allowed the attackers to amass millions in revenue through the theft of cryptocurrency from victims. This campaign demonstrates just how lucrative these sorts of malicious attacks can be for cybercriminals. Additionally, the revenue generated by these sorts of attacks, can then be reinvested into other cybercriminal operations.
The COINHOARDER Campaign
On February 24, 2017, Cisco observed a massive phishing campaign hosted in Ukraine targeting the popular Bitcoin wallet site blockchain.info with a client request magnitude of over 200,000 client queries. This campaign was unique in that adversaries leveraged Google Adwords to poison user search results in order to steal users’ wallets. Since Cisco observed this technique, it has become increasingly common in the wild with attackers targeting many different crypto wallets and exchanges via malicious ads.
Cisco identified an attack pattern in which the threat actors behind the operation would establish a “gateway” phishing link that would appear in search results among Google Ads. When searching for crypto-related keywords such as “blockchain” or “bitcoin wallet,” the spoofed links would appear at the top of search results. When clicked, the link would redirect to a “lander” page and serve phishing content in the native language of the geographic region of the victim’s IP address.
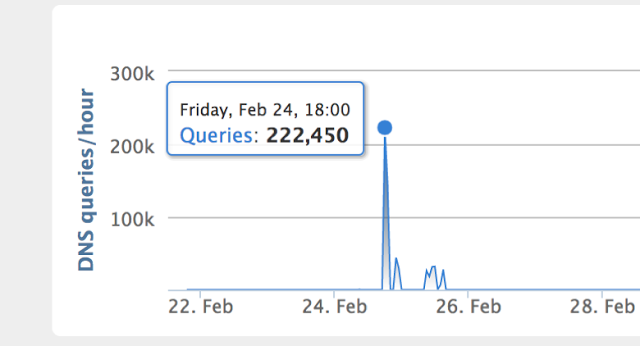
The reach of these poisoned ads can be seen when analyzing DNS query data. In February 2017, Cisco observed spikes in DNS queries for the fake cryptocurrency websites where upwards of 200,000 queries per hour can be seen during the time window the ad was displayed. Here are two examples.
DNS Statistics for block-clain[.]info
Here is what the actual lander phishing site looked like. Note how similar and convincing it is compared to a real site, with the exception of the URL:
Finding Additional Pivots
After discovering these domains and the activity on Google Adwords, Cisco implemented a system to flag similar domains as malicious. This resulted in DNS requests being blocked to said domains. Additionally, Cisco researchers were able to track and monitor related networks and info, such as WHOIS registrant data.
This information allowed Cisco to use DNS graph traversal techniques to uncover other phishing domains associated with the initial site. In this example, we can see the registrant dsshvxcnbbu@yandex[.]ru, which is also associated with many other phishing sites:
Cisco also monitored the networks these domains are hosted on. Here is a snapshot of 2 of the recently active IP addresses for this campaign, 91.220.101.106 and 91.220.101.141, and the ASN associated with these domains, Highload Systems, in Ukraine.
We can see the Second Level Domain (SLD) strings in these domains follow a similar pattern of targeting blockchain.info with many permutations of the string “blockchain”, along with co-occurrences of “http”, “https”, “wallet” in the SLD string. Here is a graph visualization of the domains on these infrastructures:
Geographic Targeting
One of the most interesting facets to these attacks are the geographic regions of the victims. Using data from Umbrella Client Requester Distribution queries to these malicious domains, we can see a significant number of DNS resolution requests coming from countries such as Nigeria, Ghana, Estonia and many more.
This threat actors appears to be standing up phishing pages to target potential victims African countries and other developing nations where banking can be more difficult, and local currencies much more unstable compared to the digital asset. Additionally, attackers have taken notice that targeting users in countries whose first language is not English make for potentially easier targets. Based on the number of queries, this campaign is one of the biggest targeting Blockchain.info to date. Blockchain.info has been very proactive in supporting users. Kristov Atlas, a security and privacy engineer at Blockchain.info, has even gone so far to say "phishing is one of our top areas of concern in protecting our users."
Quantifying Attacker’s Revenue
Cisco has evidence the COINHOARDER group has been actively pilfering Bitcoin since at least 2015. Based on our findings, we estimate this group has stolen tens of millions of USD in cryptocurrency. While working with Ukraine law enforcement, we were able to identify the attackers’ Bitcoin wallet addresses and thus, we could track their activity for the period of time between September 2017 to December 2017. In this period alone, we quantified around $10M was stolen.In one specific run, they made $2M within 3.5 week period. Here we have a screenshot of one of the wallets, 19yAR4yvGcKV3SXUQhKnhi43m4bCUhSPc, related to this actor group, which has received a total of $1,894,433.09.
While identifying the individual who owns a specific wallet is extremely difficult, we still can look for open source intelligence surrounding the wallet. In December 2017, Cisco found posts on Reddit and Stack Exchange with addresses associated with stolen funds from this campaign, 13wahvu3FP8LK8P51UmEkhBUhyC7mzkrn3.
The wallet address in the screenshot above was also mentioned in a Reddit post in October 2017.
Based on our findings associated with this syndicate, we estimate the COINHOARDER group to have netted over $50M dollars over the past three years. It is important to note that the price of Bitcoin has shot up drastically over 2017, starting around $1,000 in January and hitting a high point just under $20,000 in December. While criminals were able to profit from this, it also adds a new level of complexity for criminals to convert their cryptocurrency funds to a fiat currency like US dollars. The historic price of Bitcoin during the height of this campaign would have made it very difficult to move these ill-gotten finances easily.
Ukraine: A Hotbed For Crypto Theft
Ukraine is a hotbed for many types of attacks and a home for known bulletproof hosting providers. In the past year, Cisco has witnessed a substantial rise in financial motivated campaigns coming from and targeting this region. One of Cisco’s goals is to collaborate with countries worldwide and use our global visibility on attacks to asses their security posture and help improve it.
Some other observed IPs are 176.119.1.88 and 176.119.5.227, which host domains targeting many currencies using IDN and SSL certs and are hosted on VServer in Ukraine. We also observed AS 58271 hosting multiple search engine poisoning attacks on Google and Bing:
New Effective Attack Techniques
Cisco has observed this threat actor evolve over time. Not only have we seen the COINHOARDER group abuse Google Adwords to generate traffic to their phishing servers, but we have also observed this group evolve to make their sites appear more legitimate. A few months after we began tracking this particular group, we observed them starting to use SSL certs issued by Cloudflare and Let’s Encrypt. SSL certificate abuse has been a rising trend among phishing campaigns in general. Below is an example of a wildcard SSL certificate issued by Cloudflare for the domain bockchain[.]info.
Here is an example of one of these SSL certificates issued by Let’s Encrypt associated with this campaign and the site blockcharin[.]info.
The COINHOARDER group has made heavy use of typosquatting and brand spoofing in conjunction SSL signed phishing sites in order to appear convincing. We have also observed the threat actors using internationalized domain names. These domains are used in what are called homograph attacks, where an international letter or symbol looks very similar to one in English. Here are some examples from this campaign.
The Punycode (internationalized) version is on the left, the translated (homographic) version on the right:
xn–blockchan-d5a[.]com → blockchaìn[.]com
xn–blokchan-i2a[.]info → blokchaín[.]info
These attacks can be nearly impossible to spot with the human eye, especially when delivered on a mobile platform and using these techniques helps coax users into handing over their funds.
Conclusion
Crypto assets have proven to be a new, valuable financial commodity targeted by varying degrees of cyber criminals. In 2017, we observed phishers advance their tactics by utilizing new attack vectors such as Google Adwords combined with the use of IDNs and rogue SSL certificates to improve their probability of success, and generate millions in profit.
What is clear from the COINHOARDER campaign is that cryptocurrency phishing via Google Adwords is a lucrative attack on users worldwide. Phishers are significantly improving their attack techniques by moving to SSL and employing the use of IDNs to fool victims into handing over their credentials. We can expect to see more of these realistic looking phishes with Let’s Encrypt releasing full wildcard certificate support at the end of this month. Cisco will continue to monitor the landscape and coordinate with international law enforcement teams in 2018 to help protect users and organizations.
IOCs
The following IP address are known to have been used in these phishing attacks:
- 91.220.101.11
- 91.220.101.109
- 91.220.101.106
- 91.220.101.104
- 91.220.101.111
- 91.220.101.112
- 91.220.101.113
- 91.220.101.115
- 91.220.101.117
- 91.220.101.141
- 91.220.101.48
- 91.220.101.115
Coverage
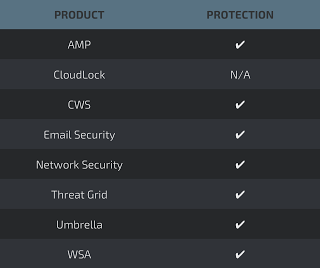
Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware used by these threat actors.
CWS or WSA web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
Network Security appliances such as NGFW, NGIPS, and Meraki MX can detect malicious activity associated with this threat.
AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella, our secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network.
Open Source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
Appendix
Here you can view more about how Cisco Security has worked hard on helping securing the cryptocurrency landscape:
- Record Setting Bitcoin Price Sparks Another Global Phishing Attack
- Malicious XMR Mining
- Bitcoin Wallet Phishes Reveal Rogue Hosts
- Bitcoin Phishing Next Wave
- New attacks on wallets and AdWords correlate with Bitcoin price surge
- Bitcoin Phishing Gains Traction
Article Link: http://feedproxy.google.com/~r/feedburner/Talos/~3/huL9lit8B6Q/coinhoarder.html