TL;DR – Citrix Bleed is but one vulnerability leveraged by ransomware actors that takes advantage of network device vulnerabilities to conduct operations. Eclypsium provides visibility into this otherwise hidden threat landscape.
Citrix Bleed (CVE-2023-4966) represents a perfect storm for threat actors as it allows:
- Exploitability from the Internet targeting a device that is typically exposed to the Internet in order to provide a service
- Access to anything the user whose session they stole has access to, including potentially Active Directory account permissions, to conduct ransomware operations
- Stealth and longevity in that detection is challenging in Netscaler and full remediation requires terminating all user sessions (not only patching)
First observed in August as a zero-day vulnerability by Mandiant, Citrix Bleed has quickly become an attack vector of choice for a number of threat groups, including Lockbit and ALPHV/BlackCat. Victims span financial services, logistics, manufacturing, and healthcare.
Citrix Bleed represents the latest event in a growing trend where threat actors target network devices and appliances for reasons that are well known (I’ve spoken about them several times in conference presentations and podcasts). The reason for this growing trend is pretty simple: network devices and appliances are typically connected to the rest of the network, they sometimes harbor credentials, visibility and monitoring capabilities are much less than with other types of systems, and the software/firmware that runs them typically contains the same style and classes of bugs we were dealing with in the 1990s (e.g. default credentials, command injection, and classic memory corruption attacks).
While there are many areas of improvement, I’d like to highlight some helpful tips for IT and security teams to deal with the security monitoring and administration of network devices and appliances:
- Log Analysis – Enable whatever logs you can on the device and (if possible) send them to a central logging facility for analysis.
- Discover Vulnerabilities – Scanning devices remotely is a good starting point, and most vulnerability scanners provide remote checks for the latest vulnerabilities. However, there are many ways a vulnerability scanner can miss the vulnerability: Did it even scan your devices or did it skip them? Was there a false positive? Authenticated scans help offset some of these problems and allow for more accurate vulnerability reporting.
- Patching – While it’s easy to say, it’s hard to do. However, I always recommend getting ahead of the problems and proactively patching versus only when there is a problem. Breaking up your patching into smaller jobs and patching more often means you may not even have to respond to the latest threat because you’ve already patched.
- Device Monitoring – While you can monitor the network traffic, it can be difficult to perform forensics without any other type of monitoring. Monitoring the firmware/software for changes (baselining) and for suspicious files or changes to files (integrity checking) provides the ability to know if a system has been compromised.
How Eclypsium helps
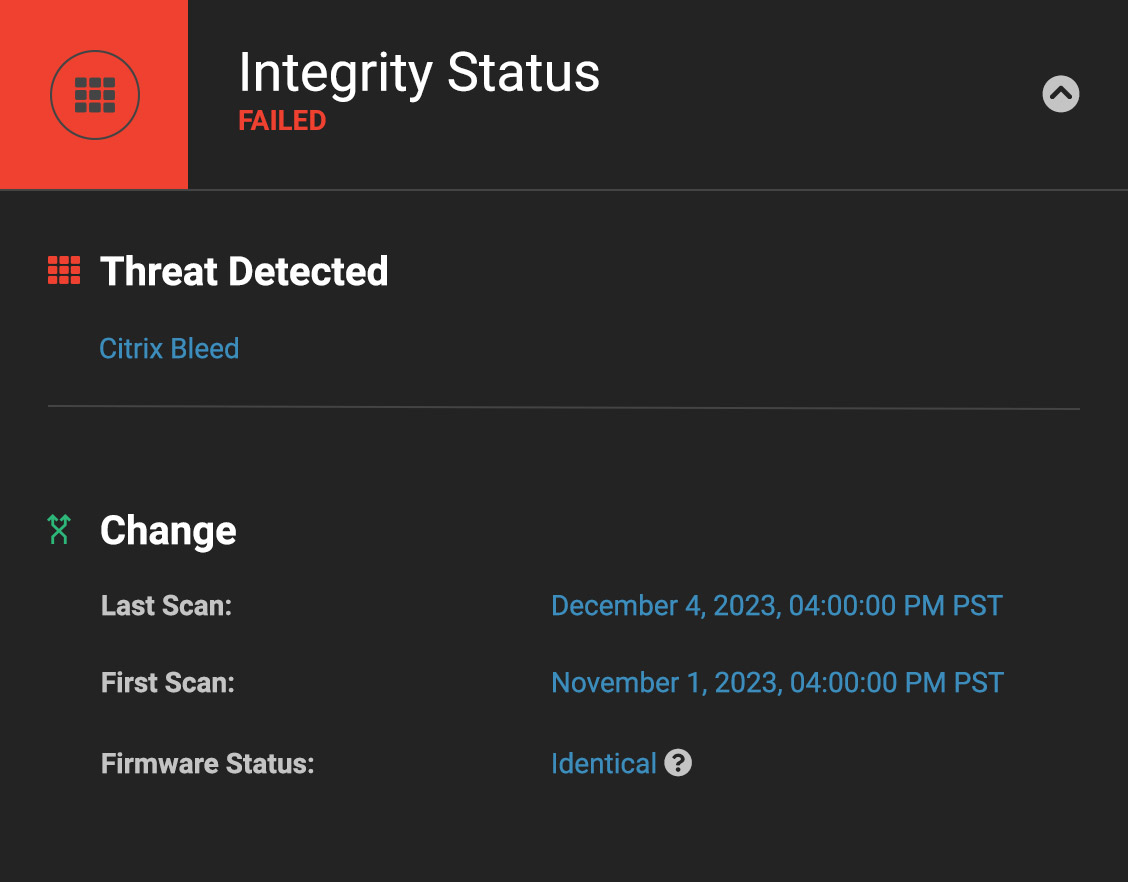
We recently made several updates to the Eclypsium supply chain security platform to help enterprises gain more visibility into network devices and appliances. For Citrix Bleed specifically, the platform has the ability to authenticate to Netscaler devices and parse the logs to look for evidence of compromise based on published indicators of compromise.
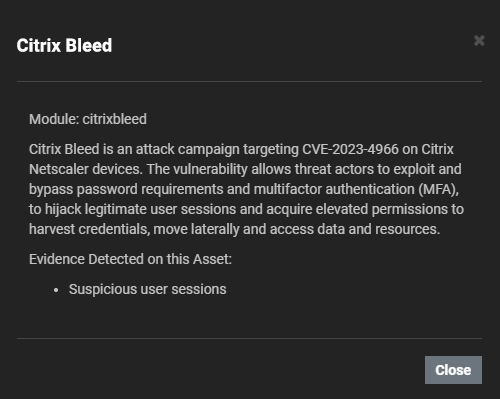
For certain devices (Netscalers and select devices from Cisco, F5, Juniper, and Fortinet), we can use authenticated access to detect changes in the firmware over time (baselining) and identify specific components that show evidence of tampering or backdoors (integrity checking). Leveraging the authentication to access the device also allows us to detect known vulnerabilities in the firmware of these devices as well.
Conclusion
While ransomware threat actors are targeting your network devices, you do have options to protect your environment. The Eclypsium supply chain security platform helps you discover vulnerabilities and identify intrusions and backdoors on network equipment that otherwise provide terrible visibility. To see it in action you can request a full demo here: https://eclypsium.com/demo/.
Additional Resources
- Webinar: Network Infrastructure in Ransomware’s Crosshairs: Addressing Supply Chain Threats
- Blog post: A New Approach to Defending Network Infrastructure from Ransomware Groups and APTs
- White paper: Network Infrastructure on the Front Line
The post Citrix Bleed and Monitoring Network Devices appeared first on Eclypsium | Supply Chain Security for the Modern Enterprise.
Article Link: Citrix Bleed and Monitoring Network Devices - Eclypsium | Supply Chain Security for the Modern Enterprise