In a recent alert, the Cybersecurity and Infrastructure Security Agency (CISA) highlighted that the Apache Software Foundation has issued security updates to fix a vulnerability identified as CVE-2023-50164, which affects Apache Struts 2.
CISA cautions that malicious actors could potentially exploit this vulnerability remotely, gaining control over the targeted system. The agency strongly advises administrators and users to promptly implement the required measures to mitigate this risk.
Vulnerability Details
CVE-2023-50164 is a critical vulnerability with a CVSS score of 9.8, impacting Apache Struts – a widely used, free, open-source MVC (Model-View-Controller) framework for development of modern Java web applications.
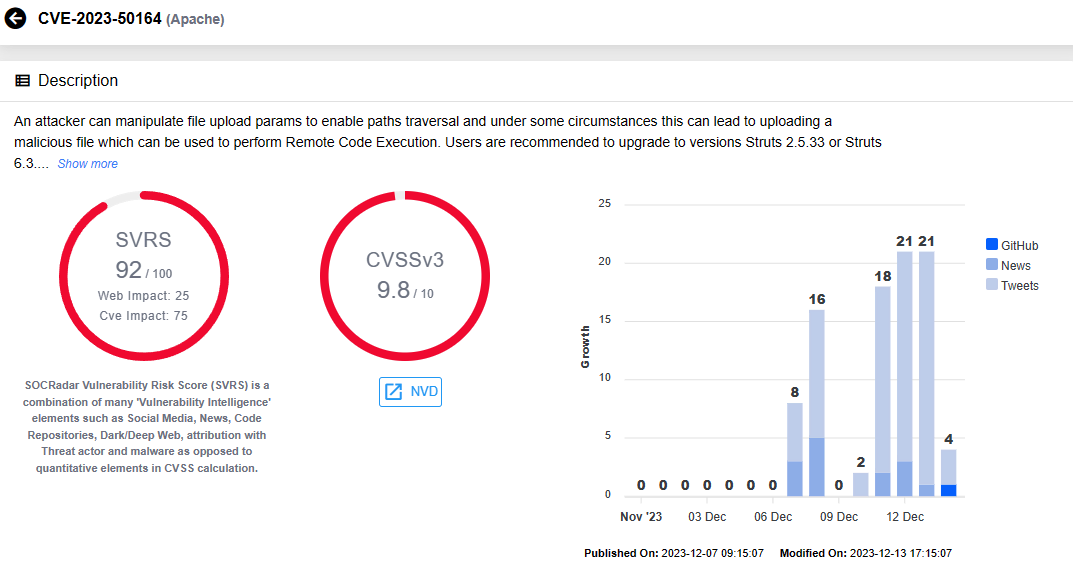 Vulnerability card for CVE-2023-50164 (SOCRadar Vulnerability Intelligence)
Vulnerability card for CVE-2023-50164 (SOCRadar Vulnerability Intelligence)
Exploiting this vulnerability in Apache Struts enables an attacker to manipulate file upload parameters, facilitating paths traversal under specific circumstances. This manipulation opens the door to uploading a malicious file, potentially leading to Remote Code Execution (RCE). The consequences of such an exploit could range from unauthorized access to sensitive data to lateral movement within the compromised network.
The vulnerability affects the following versions of Apache Struts:
- Struts 2.0.0 – Struts 2.3.37 (has reached End-of-Life)
- Struts 2.5.0 – Struts 2.5.32
- Struts 6.0.0 – Struts 6.3.0
Exploitation Attempts for CVE-2023-50164 in Apache Struts
Shadowserver has identified some IP addresses involved in exploitation attempts, aiming to capitalize on the CVE-2023-50164 vulnerability.
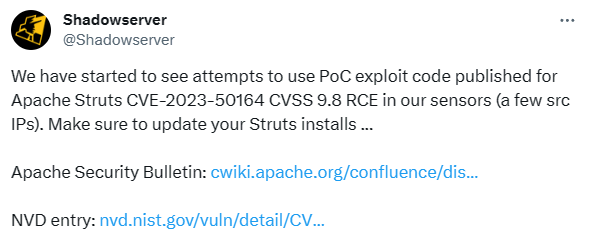 Tweet by Shadowserver (X)
Tweet by Shadowserver (X)
PoC Exploit Code for CVE-2023-50164 Is Publicly Available
There is a likelihood that these threat actors are leveraging a publicly available PoC exploit code in their attempts related to CVE-2023-50164. However, it is uncertain whether any of these attempts have been successful.
The PoC author proposes two mitigation strategies, in addition to patching the vulnerability:
- Refrain from exposing unauthorized file upload paths.
- Integrate an interceptor at the file upload location for validation.
Numerous Cisco Products That Use Apache Struts Are Potentially Affected by the Vulnerability
Significantly, Cisco has raised concerns about potential impacts on its products that utilize the Apache Struts. In a security advisory, the company disclosed an ongoing investigation to identify affected products and assess the impact.
Among the products currently under scrutiny are Cisco Customer Collaboration Platform (formerly SocialMiner), Identity Services Engine (ISE), and various other products related to network management, as well as voice and unified communications devices.
Cisco intends to update its advisory with the outcomes of the investigation, providing specific Cisco bug IDs for each affected product. The updates will also include information on available workarounds and patches.
Apply the Patch for Apache Struts
Apache has made the patch for CVE-2023-50164 available on December 7. To fortify against potential exploitation attempts, users are strongly recommended to upgrade to Struts 2.5.33 or Struts 6.3.0.2, or later versions.
See the security bulletin for CVE-2023-50164 here.
For the latest updates, visit the official website of the Apache Struts project.
Proactive Vulnerability Monitoring with SOCRadar
To proactively address critical vulnerabilities, SOCRadar XTI delivers real-time alerts and comprehensive Vulnerability Intelligence. This service is valuable for organizations to stay informed about vulnerabilities targeted by threat actors, providing actionable insights and context to streamline the response process.
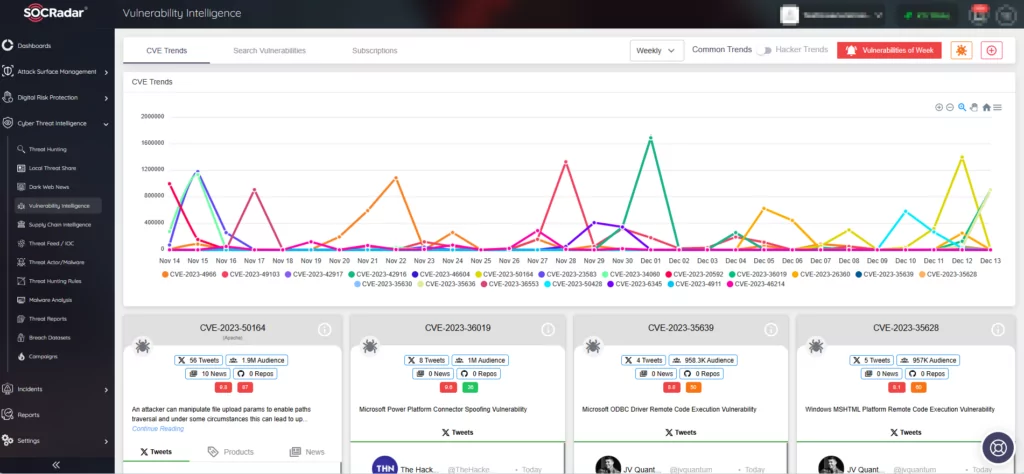 SOCRadar’s Vulnerability Intelligence
SOCRadar’s Vulnerability Intelligence
With SOCRadar’s Attack Surface Management (ASM) module, your digital assets are continuously monitored for emerging threats. Through the module, you can access information about your asset inventory and receive alerts regarding security vulnerabilities that may potentially impact your organizational assets.
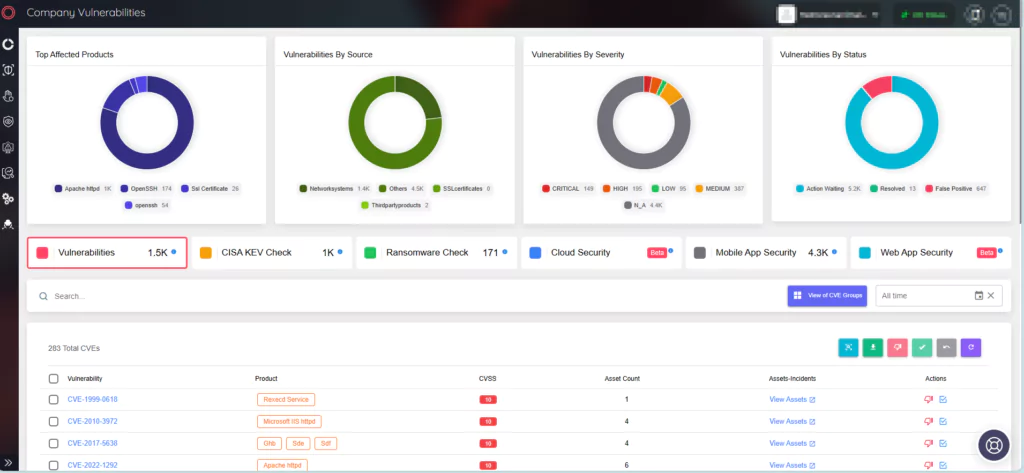 SOCRadar’s Attack Surface Management
SOCRadar’s Attack Surface Management
The post CISA Urges Organizations to Patch the Critical Apache Struts RCE Vulnerability, CVE-2023-50164 appeared first on SOCRadar® Cyber Intelligence Inc..
Article Link: CISA Urges Organizations to Patch the Critical Apache Struts RCE Vulnerability, CVE-2023-50164
