CISA has issued three advisories on Industrial Control Systems (ICS), addressing the latest security vulnerabilities related to ICS products from Rockwell Automation, Mitsubishi Electric, and Unitronics.
The frequency of ICS attacks has been escalating, with Kaspersky reporting Western Europe, the US, and Canada as the primary regions experiencing heightened attacks on ICS computers. In response, the advisories from CISA offer timely information, urging users and administrators to thoroughly examine them for recommended mitigations and take action to protect their ICS environment.
Which Products Are Affected?
The affected products and versions are as follows:
Rockwell Automation
- Factory Talk: V4.00 (Utilizes Wibu-Systems CodeMeter <7.60c)
Mitsubishi
- GT SoftGOT2000: Versions 1.275M to 1.290C (CVE-2023-0286)
- OPC UA Data Collector: Versions 1.04E and prior (CVE-2023-0286)
- MX OPC Server UA: Versions 3.05F and later (CVE-2022-4304)
- OPC UA Server Unit: All versions (CVE-2022-4304)
- FX5-OPC: Versions 1.006 and prior (CVE-2022-4304, CVE-2022-4450)
Unitronics
- VisiLogic: Versions prior to 9.9.00
- OS: Versions prior to 12.38
Rockwell Automation’s FactoryTalk Vulnerable to Buffer Overflows with Potential for RCE Attacks (CVE-2023-38545, CVE-2023-3935)
 Rockwell Automation is known for industrial automation and information products.
Rockwell Automation is known for industrial automation and information products.
Rockwell Automation’s FactoryTalk is vulnerable to buffer overflows, posing a potential risk of Remote Code Execution (RCE).
The three advisories highlight two critical severity vulnerabilities, with one identified in Rockwell Automation FactoryTalk:
CVE-2023-38545 (CVSS Score: 9.8): Rockwell Automation FactoryTalk Activation Manager and Studio 5000 Logix Designer utilize affected Wibu-Systems’ products, internally employing a version of libcurl susceptible to a buffer overflow attack.
However, exploiting CVE-2023-38545 necessitates the configuration of curl to redirect traffic through a SOCKS5 proxy.
The second vulnerability affecting Rockwell Automation’s FactoryTalk has been identified as high-severity:
CVE-2023-3935 (CVSS Score: 7.5): Affecting the same products, CVE-2023-3935 represents a high-severity heap buffer overflow vulnerability in Wibu CodeMeter Runtime network service up to Version 7.60b. This vulnerability allows an unauthenticated, remote attacker to achieve Remote Code Execution (RCE) and gain full access to the host system.
High-Severity DoS Vulnerabilities in Mitsubishi Electric ICS Products (CVE-2022-4450, CVE-2023-0286, CVE-2022-4304)
 Mitsubishi is a global vendor, specializing in electrical and electronic products and systems.
Mitsubishi is a global vendor, specializing in electrical and electronic products and systems.
The vulnerabilities within Mitsubishi products are product-specific and do not affect them equally. The details regarding which vulnerability affects which products can be found in the previous section detailing affected products.
It is essential to highlight that none of the vulnerabilities in Mitsubishi have been rated as critical; instead, they encompass high and medium severity vulnerabilities. Let’s delve into their specifics:
CVE-2022-4450 (CVSS Score: 7.5): The affected products have a double-free vulnerability when reading a PEM file. An attacker could lead to a Denial-of-Service (DoS) on the product by prompting a legitimate user to import a malicious certificate.
CVE-2023-0286 (CVSS Score: 7.4): The affected products feature a type confusion vulnerability related to X.400 address processing within an X.509 GeneralName. An attacker could potentially disclose sensitive information from the product’s memory or initiate a DoS attack by leading it to load a specifically crafted Certificate Revocation List (CRL).
CVE-2022-4304 (CVSS Score: 5.9): The affected products encompass an observable timing discrepancy vulnerability in their RSA decryption implementation. By sending specially crafted packets and executing a Bleichenbacher-style attack, an attacker could decrypt ciphertext and expose sensitive information by observing the behavior when a padding error occurs.
Critical Vulnerability in Unitronics PLCs Could Enable Attackers to Take Control of Systems (CVE-2023-6448)
 Unitronics is a leading manufacturer of Programmable Logic Controllers (PLCs).
Unitronics is a leading manufacturer of Programmable Logic Controllers (PLCs).
The final vulnerability to highlight, and the second critical one, is found in Unitronics products:
CVE-2023-6448 (CVSS Score: 9.8): Unitronics Vision Series PLCs and HMIs utilize default administrative passwords. An unauthenticated attacker with network access to a PLC or HMI can use this to seize administrative control of the system.
This vulnerability is of particular concern due to Unitronics PLCs being a recently identified attack vector. The threat group known as Cyber Av3ngers exploited Unitronics PLCs to target the Municipal Water Authority of Aliquippa. As mentioned in our previous blog post, it is suggested that threat actors likely exploited cybersecurity weaknesses, such as poor password security and internet exposure, to gain access to the affected device.
 The hack of Municipal Water Authority of Aliquippa.
The hack of Municipal Water Authority of Aliquippa.
Therefore, CVE-2023-6448, involving the existence of default administrative passwords, poses the risk of a similar incident occurring if a potential attacker gains access to the network.
Recommendations; Keep Track of the Latest Vulnerabilities with SOCRadar
The primary recommendation from all vendors is to update to the latest versions for all listed ICS products. Acquiring the most recent versions of your products stands as a crucial security measure, serving to prevent the exploitation of vulnerabilities and mitigate the risk of falling victim to cyberattacks.
CISA strongly urges all administrators and users to visit the advisories and implement appropriate security measures. The advisories also provide mitigation measures in cases where updating is not immediately feasible. Applying these methods ensures a more robust security framework for your ICS environment.
Stay vigilant by reviewing the latest security vulnerabilities and keeping your products and software updated. SOCRadar continually monitors digital assets and issues alerts whenever a vulnerability emerges and infiltrates your organization’s system.
 SOCRadar Vulnerability Intelligence’s CVE trends
SOCRadar Vulnerability Intelligence’s CVE trends
SOCRadar’s Vulnerability Intelligence offers valuable assistance in managing security vulnerabilities and prioritizing patches. Users can search for vulnerabilities, access detailed information about them, and observe the lifecycle of a vulnerability.
Below is an example page illustrating the CVE-2023-6448 vulnerability in Unitronics.
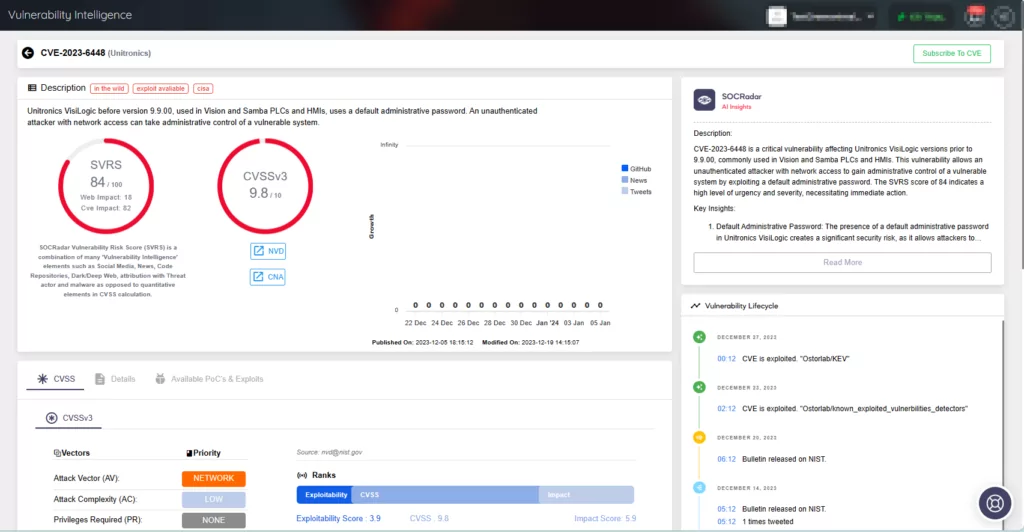 Intel card about CVE-2023-6448 (Source: SOCRadar)
Intel card about CVE-2023-6448 (Source: SOCRadar)
The post CISA Issues ICS Advisories for Vulnerabilities Affecting Rockwell Automation, Mitsubishi Electric, and Unitronics appeared first on SOCRadar® Cyber Intelligence Inc..
Article Link: CISA Issues ICS Advisories for Vulnerabilities Affecting Rockwell Automation, Mitsubishi Electric, and Unitronics
