“Enough Ripples, And You Change The Tide. For The Future Is Never Truly Set.” X-Men: Days of Future Past

In January, I dedicated some time to examine threat data from 2024, comparing it with the previous years to identify anomalies, spikes, and changes.
As anticipated, the number of Common Vulnerabilities and Exposures (CVEs) rose significantly, from 29,166 in 2023 to 40,289 in 2024, marking a substantial 38% increase. Interestingly, the severity levels of the CVEs remained centered around 7-8 for both years.
When taking a closer look at the known exploited vulnerabilities reported by the Cybersecurity and Infrastructure Security Agency (CISA), I observed that the numbers remained relatively stable, with 186 in 2024 compared to 187 in 2023. However, there was a noteworthy 36% increase for the critical vulnerabilities scored (9-10).
There is more to uncover from this data, and the analysis is still ongoing.
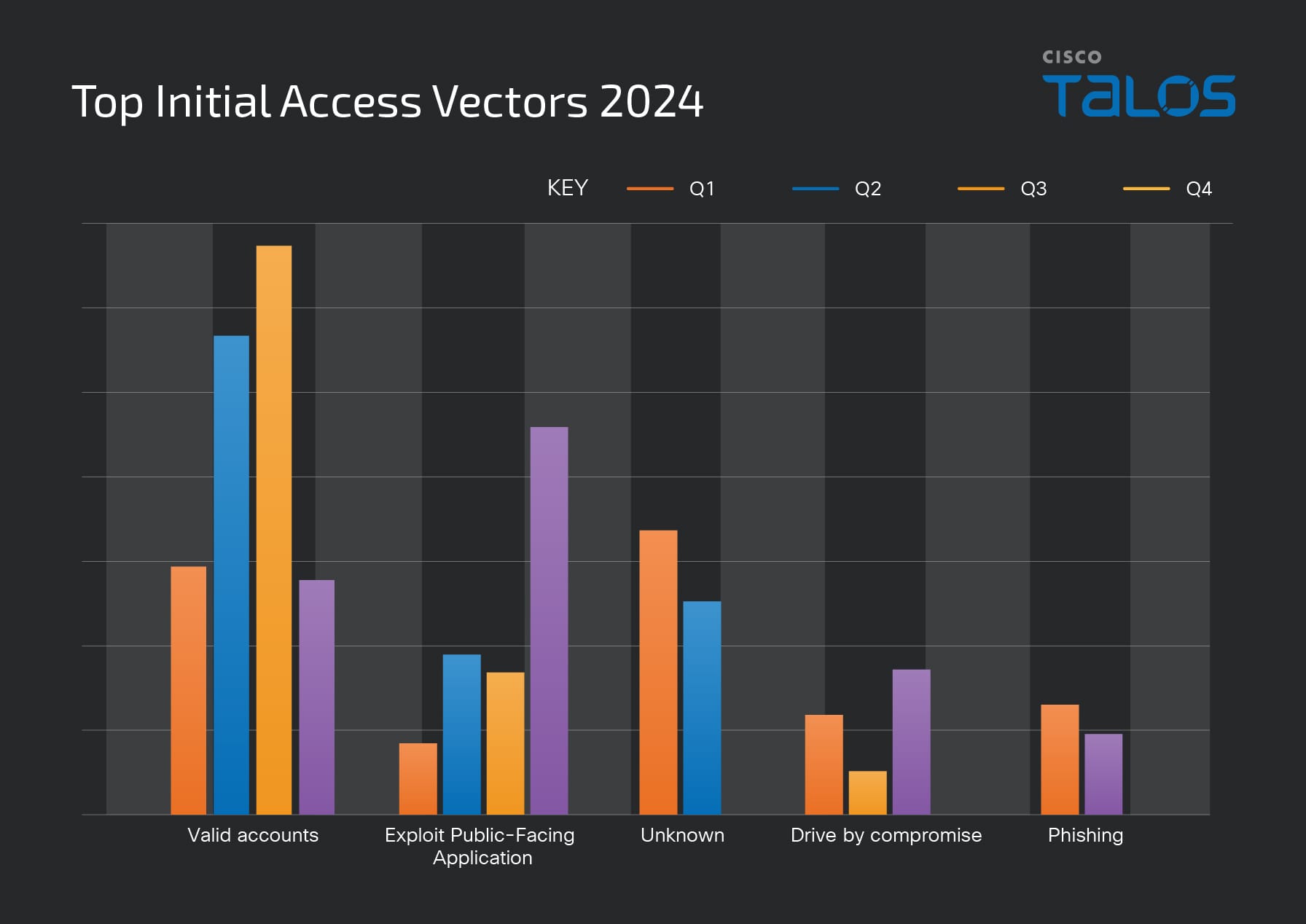
It was also time to “stack” the data of our Quarterly Incident Response Reports. The standout aspects are the initial access vectors to me. "Exploiting Public Facing Applications" and "Valid Accounts" were dominant, outperforming other methods. This serves as a timely reminder to implement (proper) MFA and other identity and access control solutions as well as patch regularly and replace end-of-life assets.
Reflecting on CVEs, patching, initial access vectors and also lateral movement, it's important to remember that the "free" support for Windows 10 will end on October 14, 2025.
Mark.your.calendars. Please. And plan accordingly to ensure your systems remain secure.
Introduction to Malware Binary Triage (IMBT) Course
Looking to level up your skills? Get 10% off using coupon code: MWNEWS10 for any flavor.
Enroll Now and Save 10%: Coupon Code MWNEWS10
Note: Affiliate link – your enrollment helps support this platform at no extra cost to you.
<div>
<div>
<h2>Newsletter reader survey</h2>
<p><i><em>We want your feedback! Tell us your thoughts and five lucky readers will receive Talos Swag boxes.</em></i></p>
<a href="https://forms.office.com/r/PhJ1FFRfHe" rel="noreferrer" target="_blank">Launch survey</a>
</div>
</div>
</div><p></p><h3>The one big thing</h3><p>Cisco Talos’ Vulnerability Research team recently <a href="https://blog.talosintelligence.com/whatsup-gold-observium-offis-vulnerabilities/" rel="noreferrer" target="_blank"><u>disclosed</u></a> three vulnerabilities in Observium, three vulnerabilities in Offis, and four vulnerabilities in Whatsup Gold. </p><h3>Why do I care?</h3><p>Observium and WhatsUp Gold can be categorized as Network Monitoring Systems (NMS). A NMS as such holds a lot of valuable information such as Network Topology, Device Inventory, Log Files, Configuration Data and more, making them an attractive for the bad guys. </p><h3>So now what?</h3><p>The vulnerabilities mentioned in this blog post have been patched by their respective vendors, make sure your installation is up to date. </p><h3>Top security headlines of the week</h3><p>The Cybersecurity and Infrastructure Security Agency analyzed a patient monitor used by the Healthcare and Public Health sector and discovered an embedded backdoor. (<a href="https://www.cisa.gov/resources-tools/resources/contec-cms8000-contains-backdoor" rel="noreferrer" target="_blank"><u>CISA</u></a>) </p><p>Apple has released software updates to address several security flaws across its portfolio, including a zero-day vulnerability that it said has been exploited in the wild. (<a href="https://thehackernews.com/2025/01/apple-patches-actively-exploited-zero.html" rel="noreferrer" target="_blank"><u>Hacker News</u></a>) </p><p>Nearly 100 journalists and other members of civil society using WhatsApp were targeted by a “zero-click” attack (<a href="https://www.theguardian.com/technology/2025/jan/31/whatsapp-israel-spyware" rel="noreferrer" target="_blank"><u>Guardian</u></a>) </p><p>DeepSeek AI tools impersonated by infostealer malware on PyPI (<a href="https://www.bleepingcomputer.com/news/security/deepseek-ai-tools-impersonated-by-infostealer-malware-on-pypi/" rel="noreferrer" target="_blank"><u>Bleeping Computer</u></a>) </p><h3>Can't get enough Talos?</h3><ul><li><a href="https://talostakes.talosintelligence.com/2018149/episodes/16538703-web-shell-frenzies-the-first-appearance-of-interlock-and-why-hackers-have-the-worst-cybersecurity-ir-trends-q4-2024" rel="noreferrer" target="_blank"><u>Web shell frenzies, the first appearance of Interlock, and why hackers have the worst cybersecurity: IR Trends Q4 2024</u></a> </li><li><a href="https://blog.talosintelligence.com/new-tornet-backdoor-campaign/" rel="noreferrer" target="_blank"><u>New TorNet backdoor seen in widespread campaign</u></a> </li></ul><h3>Upcoming events where you can find Talos</h3><p>Talos team members: Martin LEE, Thorsten ROSENDAHL, Yuri KRAMARZ, Giannis TZIAKOURIS, and Vanja SVAJCER will be speaking at <a href="https://www.ciscolive.com/emea.html" rel="noreferrer" target="_blank"><u>Cisco Live EMEA</u></a>. Amsterdam, Netherlands, 9-14 February. </p><p><a href="http://s4xevents.com/agenda/" rel="noreferrer" target="_blank">S4x25</a> (February 10-12, 2025)<br />Tampa, FL</p><p><a href="https://www.rsaconference.com/usa" rel="noreferrer" target="_blank">RSA</a> (April 28-May 1, 2025)<br />San Francisco, CA</p><p><a href="https://www.cyberthreatalliance.org/tips-conference/" rel="noreferrer" target="_blank">TIPS 2025</a> (May 14-15, 2025)<br />Arlington, VA </p><h3>Most prevalent malware files from the week</h3><p>SHA 256: 9f1f11a708d393e0a4109ae189bc64f1f3e312653dcf317a2bd406f18ffcc507 </p><p>MD5: 2915b3f8b703eb744fc54c81f4a9c67f </p><p>VirusTotal: <a href="https://www.virustotal.com/gui/file/9f1f11a708d393e0a4109ae189bc64f1f3e312653dcf317a2bd406f18ffcc507" rel="noreferrer" target="_blank"><u>https://www.virustotal.com/gui/file/9f1f11a708d393e0a4109ae189bc64f1f3e312653dcf317a2bd406f18ffcc507</u></a> </p><p>Typical Filename: VID001.exe </p><p>Claimed Product: N/A </p><p>Detection Name: Win.Worm.Coinminer::1201 </p><p> </p><p>SHA256: 47ecaab5cd6b26fe18d9759a9392bce81ba379817c53a3a468fe9060a076f8ca </p><p>MD5: 71fea034b422e4a17ebb06022532fdde </p><p>VirusTotal: <a href="https://www.virustotal.com/gui/file/47ecaab5cd6b26fe18d9759a9392bce81ba379817c53a3a468fe9060a076f8ca" rel="noreferrer" target="_blank"><u>https://www.virustotal.com/gui/file/47ecaab5cd6b26fe18d9759a9392bce81ba379817c53a3a468fe9060a076f8ca</u></a> </p><p>Typical Filename: VID001.exe </p><p>Claimed Product: n/a </p><p>Detection Name: Coinminer:MBT.26mw.in14.Talos </p><p> </p><p>SHA256:873ee789a177e59e7f82d3030896b1efdebe468c2dfa02e41ef94978aadf006f </p><p>MD5: d86808f6e519b5ce79b83b99dfb9294d </p><p>VirusTotal: </p><p><a href="https://www.virustotal.com/gui/file/873ee789a177e59e7f82d3030896b1efdebe468c2dfa02e41ef94978aadf006f" rel="noreferrer" target="_blank"><u>https://www.virustotal.com/gui/file/873ee789a177e59e7f82d3030896b1efdebe468c2dfa02e41ef94978aadf006f</u></a> </p><p>Typical Filename: n/a </p><p>Claimed Product: n/a </p><p>Detection Name: Win32.Trojan-Stealer.Petef.FPSKK8 </p><p> </p><p>SHA 256:7b3ec2365a64d9a9b2452c22e82e6d6ce2bb6dbc06c6720951c9570a5cd46fe5 </p><p>MD5: ff1b6bb151cf9f671c929a4cbdb64d86 </p><p>VirusTotal: https://www.virustotal.com/gui/file/7b3ec2365a64d9a9b2452c22e82e6d6ce2bb6dbc06c6720951c9570a5cd46fe5 </p><p>Typical Filename: endpoint.query </p><p>Claimed Product: Endpoint-Collector </p><p>Detection Name: W32.File.MalParent </p><p> </p><p>SHA 256: 744c5a6489370567fd8290f5ece7f2bff018f10d04ccf5b37b070e8ab99b3241 </p><p>MD5: a5e26a50bf48f2426b15b38e5894b189 </p><p>VirusTotal: <a href="https://www.virustotal.com/gui/file/744c5a6489370567fd8290f5ece7f2bff018f10d04ccf5b37b070e8ab99b3241" rel="noreferrer" target="_blank"><u>https://www.virustotal.com/gui/file/744c5a6489370567fd8290f5ece7f2bff018f10d04ccf5b37b070e8ab99b3241</u></a> </p><p>Typical Filename: a5e26a50bf48f2426b15b38e5894b189.vir </p><p>Claimed Product: N/A </p><p>Detection Name: Win.Dropper.Generic::1201 </p>
Article Link: Changing the tide: Reflections on threat data from 2024