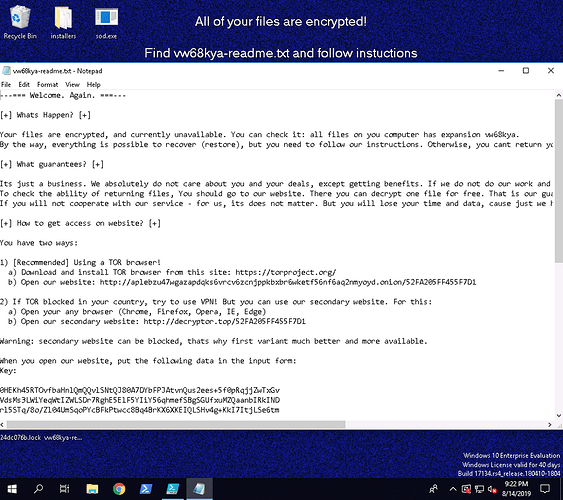
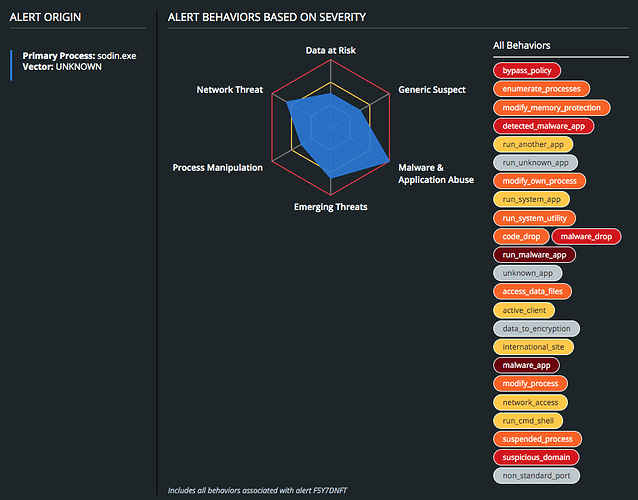
Sodinokibi (otherwise known as Sodin or REvil) is a ransomware variant that has recently been observed evolving its delivery techniques, leveraging fake antivirus software and PowerShell droppers. This malware appears to be related to GandCrab and is likely a result of their operation closing up shop, which was at one point responsible for 40% of all ransomware infections world wide. Once encrypted, this ransomware renames all files on the system with a randomized 7-character extension. Below is a screenshot of the ransomware message displayed following infection.
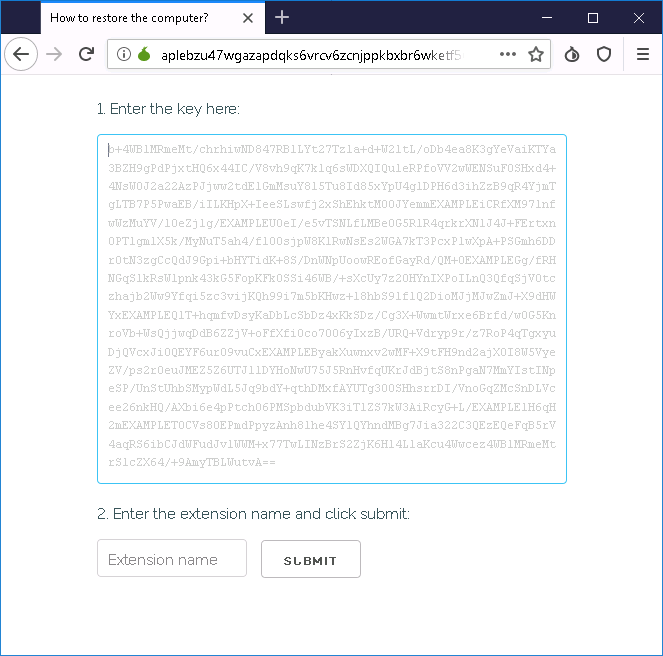
Once the victim has downloaded the TOR browser / alternate VPN and opened the website, they are presented with a key and file extension challenge to match up the infected system with the correct decryptor.
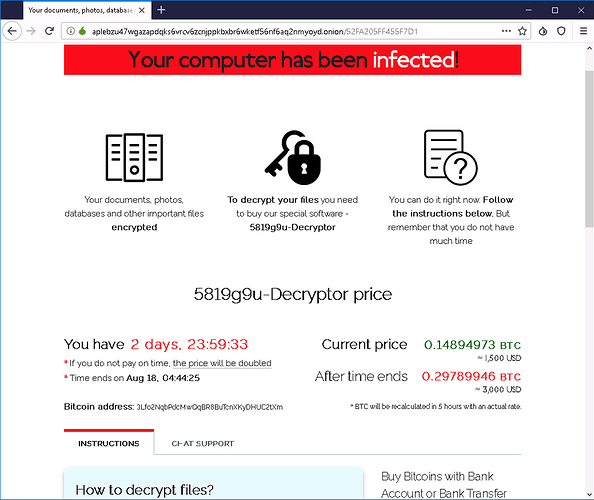
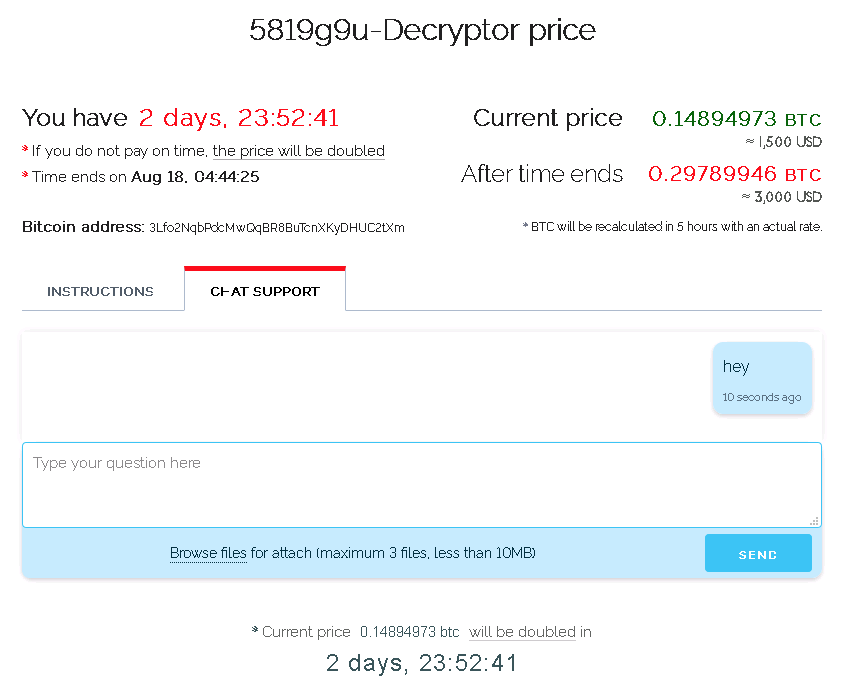
Once they key has been entered, the victim is presented with instructions to pay the attackers in bitcoin (currently at $1500 USD) within two days before the price doubles.
The site even comes equipped with a chat feature and lets you test the decryption of up to three image files.
Behavioral Summary
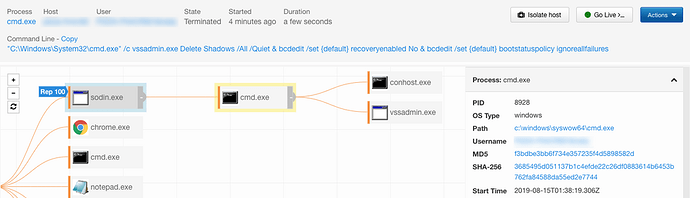
The first activity observed during infection is the malware leveraging cmd.exe to execute vssadmin.exe to delete all existing shadow copies and bcdedit.exe to disable Windows automated recovery and error recovery via the following command:
"C:\Windows\System32\cmd.exe" /c vssadmin.exe Delete Shadows /All /Quiet & bcdedit /set {default} recoveryenabled No & bcdedit /set {default} bootstatuspolicy ignoreallfailures
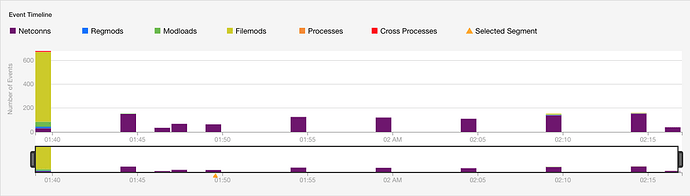
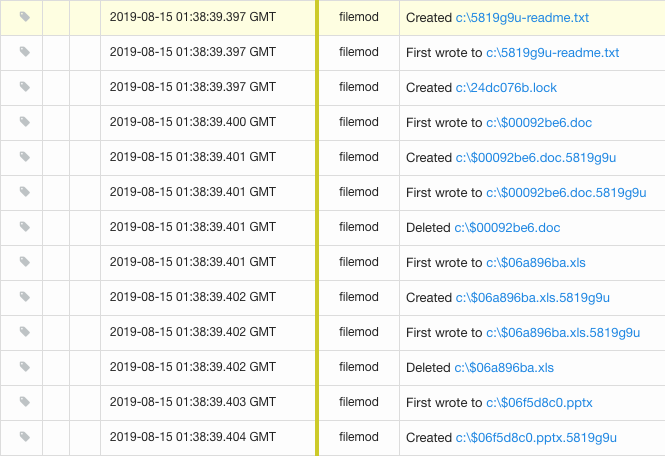
Following the configuration changes to the host which will prevent restoring from a local backup, the malware begins to encrypt all files on the system – targeting user directories where important files are likely stored first, then moving on to encrypt additional files across additional directories.
The malware also beacons out over port 443, and begins rotating through hundreds of IP addresses to establish a persistent connection.
Once established, the malware beaconing will continue once every 5-minutes.
TTP Detail
If you are a Carbon Black customer looking to learn how Carbon Black solutions helps defend against this attack, click here.
Additional Protection
Once the variant is initially executed, it will decode several different areas of embedded data, as well as dynamically resolving APIs that are required. Portions of code are also decrypted in memory and then executed, as additional threads. The image below depicts the function that is responsible for decrypting the configuration information. The configuration information is decrypted using the RC4 algorithm and the key “MdqKE9cdV83HnVQciEF2Tz7wdcheqoEu” which will be different depending on the variant.
The decrypted configuration data contains several fields that are noted in the table below. A python script hosted on the TAU-Tools GitHub, can be used to decrypt the configuration information. Carbon Black threat researchers extracted that configuration information for hundreds of samples. This showed that public keys were created for each sub identifier. At the time this research was originally done in June there were approximately 40 different pid identifiers which were sequential numbers, it should be noted that not all numbers were located in samples in the wild.
| Config Field | Description |
|---|---|
| pk | This field contains a base64 encoded public key which is used for encryption. |
| pid | Believed to be a Public Identifier, most likely related to a specific group using the variant. This value is a 1 to many of the next value, where 1 group can use several different sub ID’s to differentiate different campaigns. |
| sub | This is a sub identifier, which can be used by a group, when different variants are created for different campaigns or targets. |
| dbg | A True or False field for debugging purposes. |
| fast | A True or False field,the purpose of this field is still being determined. |
| wipe | A True or False field, that enables a wiping component. |
| wht | The wht field contains several sub fields. This field appears to be a whitelist of data that will not be affected by the encryption process, with one exception below. |
| wht:fld | This is a list of folders that will not be included during the encryption process. |
| wht:fls | This is a list of files that will not be included during the encryption process. |
| wht:ext | This is a list of extensions that will not be included during the encryption process. |
| wht:wfld | This appears to contain a list of folders what are wiped or deleted, with the assumption that the wipe field list above is set to True. |
| wht:prc | This is a list of processes that will be killed prior to the encryption process. |
| dmn | This is a list of domains, that may be used to check for internet connectivity, if the net field below is set to True. |
| net | A True or False field, that determines whether to check for network connectivity. |
| nbody | This is the body of the ransomware note, that is base64 encoded. |
| nname | This is the name that the ransomware note will be saved as. |
| exp | A True or False field,the purpose of this field is still being determined. |
| img | Data that will be displayed to the user. |
Download the Sodinokibi configuration extraction script at the following link:
https://github.com/carbonblack/tau-tools/tree/master/malware_specific/Sodinokibi
MITRE ATT&CK TIDs
| TID | Tactic | Description |
|---|---|---|
| T1027 | Defense Evasion | Obfuscated Files or Information |
| T1045 | Defense Evasion | Software Packing |
| T1064 | Defense Evasion | Scripting |
| T1083 | Discovery | File and Directory Discovery |
| T1086 | Execution | PowerShell |
| T1107 | Defense Evasion | Shadow Copy Deletion by WMIC or VSSAdmin |
Indicators of Compromise (IOC)
YARA Signatures available here:
Sodinokibi Ransomware:
https://github.com/carbonblack/tau-tools/blob/master/threat_hunting/yara/sodinokibi_ransomware_2019_…
PowerShell Reflective Injection:
https://github.com/carbonblack/tau-tools/blob/master/threat_hunting/yara/powershell_reflective_injec…
IOC lists available here:
The post CB TAU Threat Intelligence Notification: Sodinokibi Ransomware appeared first on Carbon Black.
Article Link: https://www.carbonblack.com/2019/08/16/cb-tau-threat-intelligence-notification-sodinokibi-ransomware/