Recently, Eclypsium worked with a customer and Lenovo to identify a end of manufacturing step that was not properly executed affecting some Lenovo ThinkSystem SR670V2 servers. In this case, all parties involved followed reporting and disclosure procedures to mitigate the risk of this incomplete process step for end users.
This case illustrates the benefit of third-party verification and assurance provided by Eclypsium working in conjunction with customers and OEMs. Together, we can harden the supply chain for IT infrastructure.
Intel ME firmware left in “manufacturing mode”
Lenovo issued a security advisory (LEN-150020) earlier this month making customers aware that the Intel Management Engine (ME) firmware on certain ThinkSystem SR670V2 system motherboards was left in “manufacturing mode.” Normally, manufacturing mode is turned off before the product is shipped to the customer.
The risk is that an attacker with privileged logical access to the host or physical access to server internals could modify or disable Intel Boot Guard firmware integrity or Intel Server Platform Services (SPS) security. In this case, this model of ThinkSystem contains a parallel NIST SP 800-193-compliant Platform Firmware Resiliency (PFR) security subsystem which significantly mitigates this issue by ensuring firmware integrity and maintaining most SPS settings in their intended state even if tamper has occurred.
Trust but verify your IT infrastructure products
This case illustrates the benefit of third-party validation and assurance for IT infrastructure products. The complexity of the supply chain ecosystem makes any misconfiguration or vulnerability difficult to mitigate for vendors—as they need to coordinate with numerous involved parties—but customers have an equally difficult time dealing with the fallout for those products in production. The danger is that if attackers can compromise your IT infrastructure at these fundamental levels, they can evade detection by traditional security tools. Even when detected, fully remediating compromised systems is not trivial.
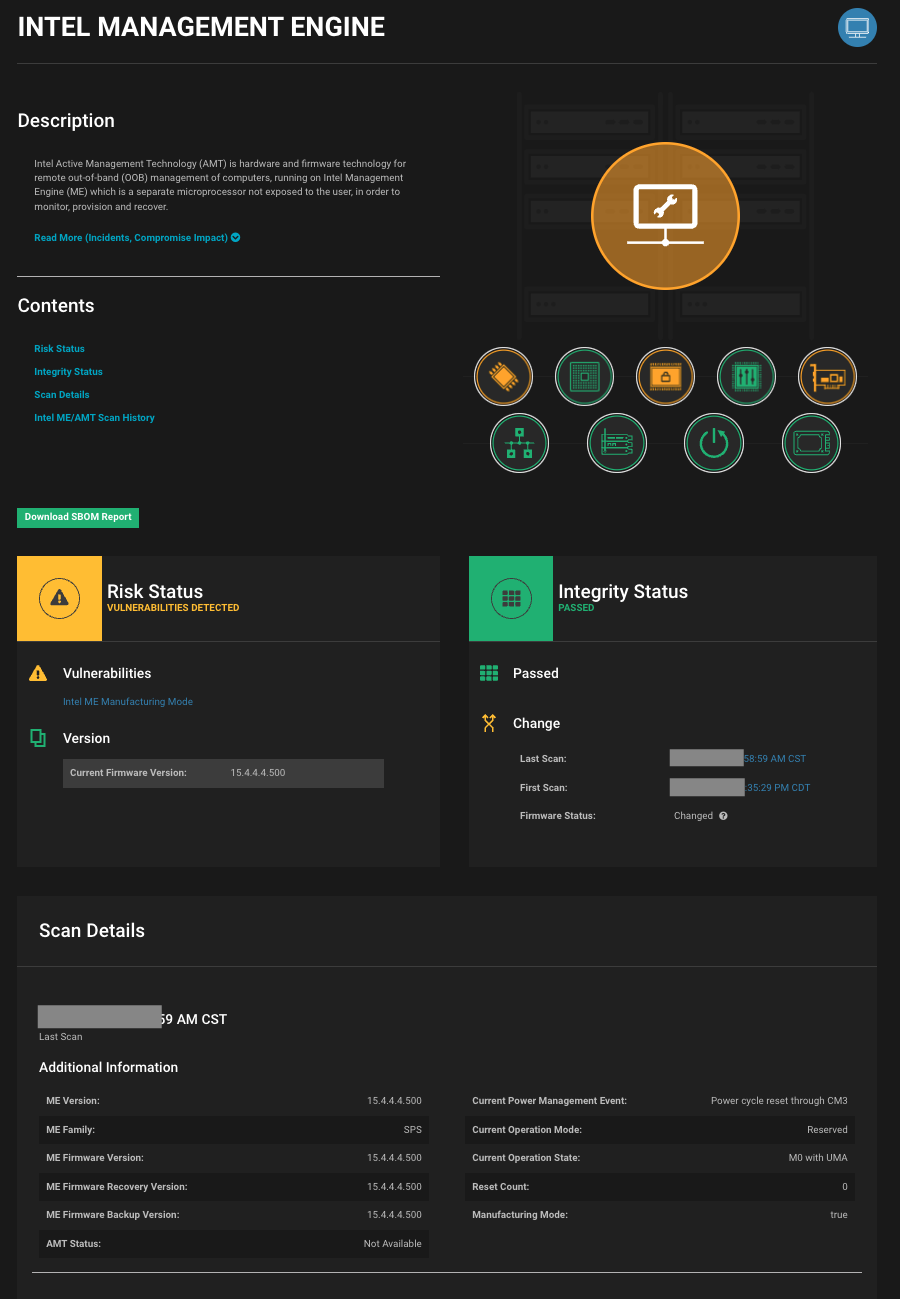
Eclypsium monitors production IT infrastructure assets for threats, vulnerabilities, and misconfiguration such as Intel ME firmware in manufacturing mode, shown here.
The Eclypsium supply chain security platform provides third-party validation and assurance for end-users of IT infrastructure products. Importantly, our platform is the only solution that can continuously monitor your production IT infrastructure assets at scale. In fact, Eclypsium partners with Lenovo to power the ThinkShield Firmware Defense offering as a software add-on for this reason. To learn more, we invite you to take a tour of the platform or to request a demo.
Further reading
- Press release: Eclypsium Collaborates with Lenovo on Digital Supply Chain Assurance
- Press release: Eclypsium Collaborates With Intel to Provide Enhanced Visibility Into Infrastructure Supply Chains
- Webinar: DON’T PANIC! How to Manage IT Product Risk with Supply Chain Intelligence
The post Building Trust: The Role of Third-Party Assurance in IT Infrastructure Supply Chains appeared first on Eclypsium | Supply Chain Security for the Modern Enterprise.