 Browser-based cyberthreats have become one of the biggest concerns facing cybersecurity professionals today. It’s critical for organizations to implement effective protection from these hard-to-detect attacks.
Browser-based cyberthreats have become one of the biggest concerns facing cybersecurity professionals today. It’s critical for organizations to implement effective protection from these hard-to-detect attacks.
Introduction
Of all the software in use, browsers are the most exposed. They are constantly connecting to the outside world, and frequently interacting with websites and applications that cybercriminals have infected with malware. Browsers are powerful, data-rich tools that if compromised, can provide an attacker with a vast amount of information about you, including your personal address, phone number, credit card data, emails, IDs, passwords, browsing history, bookmarks etc.
Browsers are also perfect instruments for cybercriminals to establish a foothold on your device, your personal network, and your business systems. Browsers rely on a number of third-party plug-ins like JavaScript, Flash, and ActiveX to perform various tasks. However, these plug-ins often come with security flaws that cybercriminals exploit to get access to your systems. These vulnerabilities allow attackers to wreak havoc by, for example, installing ransomware, exfiltrating data, and stealing intellectual property.
During the past year or so, we’ve seen a sharp increase in web threats that are specifically designed to leverage browser-based vulnerabilities. This increase in popularity is not only because browsers are strategically desirable as hacking targets, but because browser-based web threats are difficult to detect. Most malware detection and prevention technologies work by examining files such as downloads or attachments. However, browser-based threats don’t necessarily use files, so conventional security controls have nothing to analyze. Unless organizations implement advanced tools that don’t rely on analyzing files, browser-based attacks will likely go undetected.
Given that browser-based attacks are powerful and difficult to discover, it’s easy to understand why they have become so prominent. They simply work.
How Browser-Based Cyberthreats Operate
As an example of how a browser-based attack works, consider a scenario where a Windows user visits a seemingly benign but now malicious website, possibly one he or she has visited before, or as the result of an enticing email. As soon as a connection occurs, the user’s browser begins interacting with the site. Assuming the system is using JavaScript, which according to research firms like Web Technology Surveys, 94% of all websites do and over 90% of browsers have it enabled, the browser will immediately download and start executing JavaScript files from the malicious website.
The JavaScript can harbor malicious code that’s capable of capturing the victim’s data, altering it, and injecting new or different data into their web applications—all in the background and invisible to the user. For instance, one method malware authors use to accomplish this is by embedding an obfuscated Adobe Flash file within the JavaScript. Flash is frequently used due to its seemingly never-ending set of vulnerabilities. The following is representative of what typically occurs:
- The Flash code invokes PowerShell, a powerful OS tool that can perform administrative operations and exists on every Windows machine.
- Flash feeds instructions to PowerShell through its command line interface.
- PowerShell connects to a stealth command and control server owned by the attackers.
- The command and control server downloads a malicious PowerShell script to the victim’s device that captures or finds sensitive data and sends it back to the attacker.
- After the attacker has met his objectives, the JavaScript, Flash, and PowerShell scripts are wiped from memory, leaving essentially no trace of the breach.
Combatting Browser-Based Cyberthreats
Most malware detection systems work by verifying the reputation or safety of links and evaluating files such as attachments and downloads for known threats. In browser-based attacks as described here, the security systems may not have any links or files to analyze, so traditional anti-malware technologies are often ineffective. Nonetheless, there are ways of combatting browser-based attacks. The latest and most advanced malware detection technologies can evaluate JavaScript and Flash data even when no files are present. These innovative tools extract the JavaScript and Flash content from the device’s memory and examine it for both static and dynamic abnormalities such as:
Static – Structural Abnormalities
- Unusual shellcode existing within arrays or character strings
- Missing or added segments
- Embedded files
- Suspicious function arguments
- Evidence of code injection like hidden iframes or unusual tags
- Signs of code obfuscation such as encodings, or specific JavaScript functions like encryption or fingerprinting
- Indications of exploit – structural similarities, signatures
Dynamic – Behavioral Abnormalities
- Abnormal process behaviors – the code may not be dropping files but might make abnormal network connections, or attempt to start abnormal processes
- Heap spraying – inserting code into predetermined locations by exploiting browser vulnerabilities
- Attempts to modify system files or components
- Connections to known malicious sites or command and control centers
- Evasion tactics such as stalling
Although it is certainly possible to look for all of the possible abnormalities listed above by analyzing every bit of JavaScript and Flash content that an organization’s employees encounter, it’s just not practical. Fully testing each instance requires at least some degree of behavioral analysis, which may take 60 seconds or more. Given the enormous amount of JavaScript and Flash that a typical company’s employees encounter every day, it’s just not feasible to perform full behavioral analysis on all of it. Fortunately, we don’t have to.
Filtered Approach Makes Evaluating Browser-Based Threats Feasible
Instead of subjecting every instance of JavaScript to full static and dynamic analysis, a good malware detection engine can evaluate the code in phases. In the initial phase, the engine performs only a static analysis, which doesn’t require the code to execute. Since the malware detection system can do this in real time, it’s feasible to evaluate all JavaScript and Flash content at this level. Code that successfully passes this filter and most will during normal operations, need not undergo additional testing.
In those cases where the malware detection engine encounters abnormalities during the initial static analysis phase, it can examine the code more closely. The most rigorous and time-consuming tests need only happen in those rare situations where all previous tests indicate a substantial risk of malware.
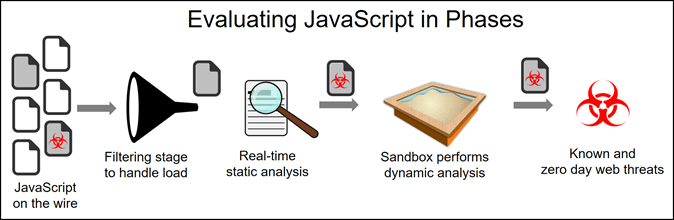
For example, static analysis might identify capabilities that could potentially be malicious, like data encryption. Code that can encrypt data could be ransomware. In this case, the system will also perform dynamic analysis to determine if the code does, in fact, behave maliciously, or if it uses the encryption capabilities in benign and appropriate ways.
Static analysis efficiently detects a wide variety of anomalies such as abnormal macros, missing or added structures or segments, correspondence with command and control servers used by cybercriminals, and more. Some of these capabilities are very indicative of malicious intent and the system can immediately score the object as high-risk. If there’s any doubt, the system also performs dynamic analysis to test what the code actually does when it executes.
If static analysis uncovers nothing suspicious, the system can, with a high rate of accuracy, score the object as low-risk and bypass dynamic analysis.
By using this phased approach, the system fully tests all suspicious objects, essentially eliminating false positives. That, combined with the efficiencies gained by only performing dynamic analysis when necessary, it becomes feasible to test all JavaScript and Flash files for the presence of malware.
Malware Evolves, and So Must We
Cybercriminals are constantly working to find new and more effective ways to infiltrate our computers, devices, and networks. The recent evolution in browser-based cyberthreats is a poignant example of malicious new techniques that are both difficult to detect and effective.
Because it’s virtually impossible for conventional anti-malware products to effectively evaluate all JavaScript and similar browser-based objects, businesses are often vulnerable to these new threats. To effectively protect themselves, organizations must also evolve and constantly upgrade their threat prevention tools to combat the latest evolutions in malware. One way of doing that is to implement a filtered approach that evaluates all code in real-time, and tests suspicious code with full dynamic analysis.
The post Browser-Based Cyberthreats: How They Attack, and How to Protect Against Them appeared first on Lastline.
Article Link: https://www.lastline.com/blog/browser-based-cyberthreats/