The ShadowServer foundation has recently released a report showing that there are about 3.6 million MySQL servers exposed to outside. Along with MS-SQL server, MySQL server is one of the main database servers that provides the feature of managing large amounts of data in a corporate or user environment. MS-SQL is mainly used in Windows environments, but MySQL is still being used by many in Linux environments.
https://www.shadowserver.org/news/over-3-6m-exposed-mysql-servers-on-ipv4-and-ipv6/
ASEC analysis team is constantly monitoring malware distributed to vulnerable database servers. In Windows environment, the majority of the attacks were done against MS-SQL server, and this can be confirmed in AhnLab’s ASD log. Various attack cases were introduced in the previous ASEC blogs, such as Cobalt Strike, Remcos RAT, and CoinMiner.cjdmacjdmwk
Although the number of confirmed attacks is relatively low, attacks that target MySQL servers are constantly being discovered. There were also cases of Gh0stCringe attacking MS-SQL servers along with MySQL servers.
 Figure 1. Gh0stCringe RAT generation logs
Figure 1. Gh0stCringe RAT generation logs
According to AhnLab’s ASD log, the majority of the malware distributed to vulnerable MySQL servers are variant malware of Gh0st RAT, including Gh0stCringe above. In this blog, an analysis of attack methods used against vulnerable MySQL servers and AsyncRAT found in these recent attacks will be discussed.
First, attackers conduct scanning to search for a target to attack. Among externally exposed systems, the scanner searches for system that has 3306/TCP port revealed, used by MySQL server. After then, upon using brute-force attacks and dictionary attacks against the system, attackers can obtain root user account credentials if the system was being managed in improper ways.
Normally, multiple methods to execute OS commands are provided in MS-SQL environment. The most well-known command is xp_cmdshell, and there are other various methods such as OLE Store Procedure, MS-SQL Agent Jobs, Extended Stored Procedure, and CLR Stored Procedure. Being able to execute a user’s command using OS commands (e.g. cmd) or powershell means that the control over the system can be obtained.
In other words, logging in to the data server can execute the Windows command, eventually gaining control of the system. Thus, for security policy reasons, admin accounts should be able to use the features above. Also, additional security settings need to be changed.
MySQL does not support direct OS commands such as xp_cmdshell like MS-SQL, but it can eventually be executed by an attacker using a feature called User Defined Function (UDF). UDF is an implementation of the features desired by the user in DLL, and the attackers upload a UDF library, or DLL, containing malicious commands to the infected system and then load it into the MySQL server. After then, malicious commands can be delivered to an infected system by executing the command explained above.
 Figure 2. Metasploit’s UDF attack feature
Figure 2. Metasploit’s UDF attack feature
The following are features exported by Metasploit’s UDF library DLL file, including features such as command execution (sys_exec) and environment variable return (sys_get).
 Figure 3. Features provided by Metasploit UDF library
Figure 3. Features provided by Metasploit UDF library
Taking a look into the infection log of the actual attack target system, malicious UDF DLL is also installed along with AsyncRAT (see Figure below). This malware only has the feature of simply executing the command received from the attacker.
 Figure 4. UDF DLL malware used for the attack
Figure 4. UDF DLL malware used for the attack
As this malware has continuously been used in the past, it has infected various systems. The following are the path names found in the infection log, and the history created in the plugin folder where UDF is installed by default can be found.
%SystemDrive%\mysql 5.1\lib\plugin\djxjj.dll
%ProgramFiles%\mysql\mysql server 5.1\lib\plugin\gxpem.dll
%ProgramFiles%\mysql\mysql server 5.5\lib\plugin\nhhxt.dll
%ProgramFiles% (x86)\mysql\mysql server 5.4\lib\plugin\bggrt.dllSince the system is in a vulnerable environment, there are already cases in which it was infected with malware by numerous attacks. Thus, we do not know whether it was installed by attacker that uses AsyncRAT, or its relations.
AsyncRAT used in the attack is an open-source RAT malware developed with .NET, and it can perform various malicious actions such as remote shell, keylogging, and account credentials theft by receiving the attacker’s commands from the C&C server.
 Figure 5. AsyncRAT GitHub
Figure 5. AsyncRAT GitHub
As AsyncRAT is open-source, it is being distributed in various ways. Recently, it disguised itself as a crack program of commercial software and was distributed via malicious websites. In the past, it was distributed via spam email. In addition, there were cases of distribution of illegal pornography through Discord, which was introduced in the previous ASEC blog.
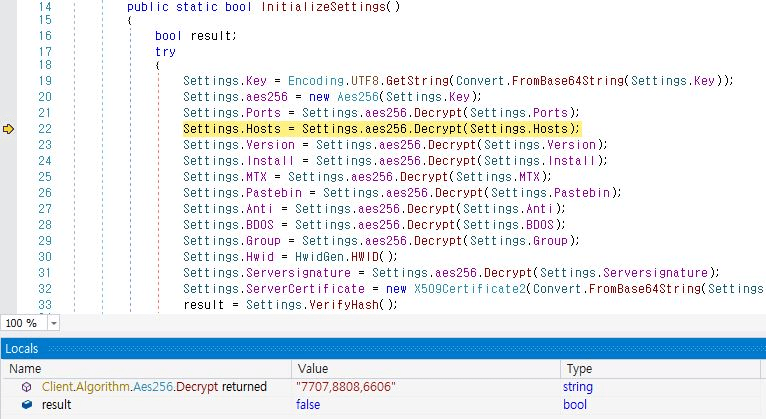 Figure 6. AsyncRAT setting data used for the attack
Figure 6. AsyncRAT setting data used for the attack
Typical attacks that target database servers (MS-SQL, MySQL servers) include brute force attacks and dictionary attacks on systems where account credentials are poorly being managed. Although it seems like these methods make up the majority of the attacks, there can be vulnerability attacks against systems where their vulnerability has not been patched.
Because of this, administrators should use passwords that are difficult to guess for their accounts and change them periodically to protect the database server from brute force attacks and dictionary attacks, and update to the latest patch to prevent vulnerability attacks. Administrators should also use security programs such as firewalls for database servers accessible from outside to restrict access of external attackers.
AhnLab’s anti-malware software, V3, detects and blocks the malware using the following aliases:
[File Detection]
– Trojan/Win32.RL_Generic.C4239825 (2020.11.26.01)
– Trojan/Win32.Inject.C500093 (2014.08.08.04)
[IOC]
MD5
AsyncRAT
– 46d552cd04ff2b41be06ba1478a97ced
UDF DLL
– f23b2905bf872b4a6495cecde290fd2d
Download URLs
AsyncRAT
– hxxp://154.19.203[.]208/Mini.exe
C&C
AsyncRAT
– 154.19.203[.]208:7707
– 154.19.203[.]208:8808
– 154.19.203[.]208:6606
Subscribe to AhnLab’s next-generation threat intelligence platform ‘AhnLab TIP’ to check related IOC and detailed analysis information.
The post AsyncRAT Being Distributed to Vulnerable MySQL Servers appeared first on ASEC BLOG.
Article Link: AsyncRAT Being Distributed to Vulnerable MySQL Servers - ASEC BLOG