At ANY.RUN, we’ve recently released our new Threat Intelligence Lookup service.
This tool opens up incredible opportunities for leveraging our extensive threat intelligence database more effectively. In this article, we aim to demonstrate how our advanced search capabilities can help you respond to security incidents more quickly and accurately.
In this article, we’re going to walk you through a realistic example of a phishing attack. But before we dive into the specifics, let’s quickly recap: what is ANY.RUN Threat Intelligence Lookup and who is this service for?
What is ANY.RUN Threat Intelligence Lookup?
ANY.RUN Threat Intelligence Lookup is a contextual search service available online and through an API. It works by indexing and analyzing data from millions of public interactive analysis sessions, also called simply “tasks,” which our community of over 300,000 researchers and 300 enterprises runs in the ANY.RUN sandbox.
The main goal of this tool is to help your security team connect an isolated indicator to a specific threat.
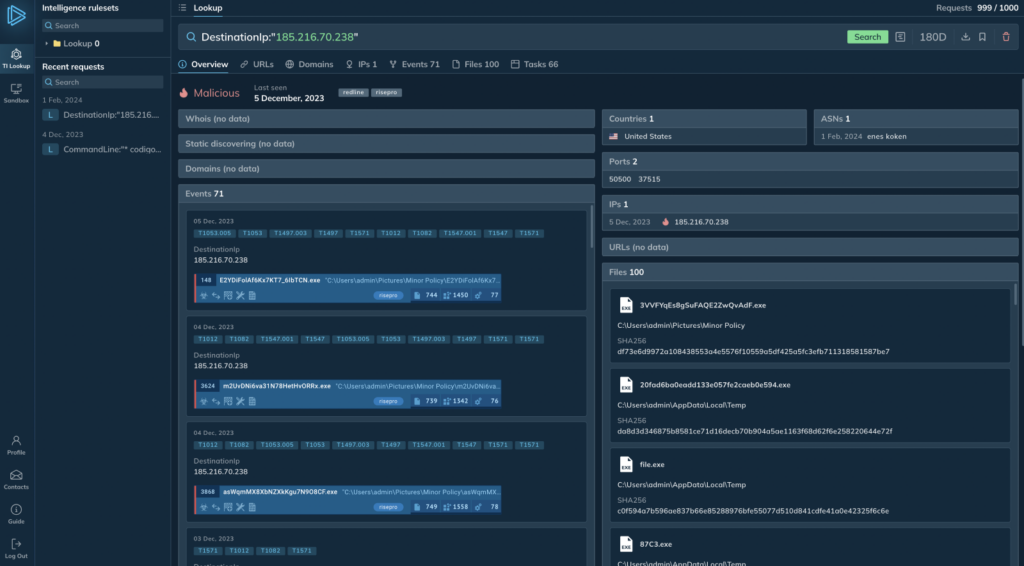 Search results show that IP “185.216.70.238” is linked to RisePro malware
Search results show that IP “185.216.70.238” is linked to RisePro malware For example, if you spot an unfamiliar IP in your network logs, figuring out its nature might take a while. However, it’s likely that this IP has already been recorded in a sandbox task. By querying for this IP in the Threat Intelligence Lookup, you can quickly find linked analysis sessions.
In many cases, this is enough to identify the malware family by name. You’ll also get related details such as ports, URLs, and file hashes in the search results.
ANY.RUN Threat Intelligence: Search for linked IOCs using over 30 fields
Contact salesOf course, besides IPs you can use many other parameters to query our Threat Intelligence database. There are over 30 parameters in total to help you build queries as wide or as specific as you need. Here are some of them:
- IOCs: file hashes, URLs
- Events: command line, registry path.
- Threat details: Suricata messages or Suricata id
- And many others
For a full list of supported parameters, read our TI Lookup introduction post.
Phishing attack: setting the stage for our case study
Let’s get back to the case study and outline the scenario our security team is facing.
(Note: This case study is based on our real-world experience, but it does not reflect a specific attack on our clients or anyone else.)
The security team received an alert from an employee about a possible phishing attempt. The employee downloaded an Office attachment from an email, and despite observing odd behavior, followed instructions to enable Macros. In hindsight, it triggered an alarm, which led to the report.
Now, it’s up to the security analysts to examine the employee’s workstation, which may have been compromised.
Step 1: Explaining a Suspicious Command Line
As usual in situations like this, let’s begin by examining the logs from the intrusion detection and response (IDR) system.
By going through these logs we come across a highlighted PowerShell process, with the term $codigo in the command line.
The term $codigo seems unfamiliar, but what exactly could it be? An analyst lacking access to Threat Intelligence Lookup might turn to a generic internet search to answer this question, which could either be time-consuming, or unfruitful, or both.
Fortunately, we have a better tool at our disposal: Threat Intelligence Lookup.
ImagePath:”powershell” AND CommandLine:”$codigo”
By searching with the query ImagePath:”powershell” AND CommandLine:”$codigo”, as the video above shows, we uncover numerous command lines from tasks containing the $codigo keyword. By exploring the Events tab, we get a more detailed view of these command lines and notice that some tasks are tagged with “stegocampaign.”
This indicates the workstation might have been compromised by a cyberattack. However, we need more detailed information to identify the specific malware family involved.
Get a demo of Threat Intelligence Lookup from our team
Get demoStep 2: Identifying the Malware Family
We’re making progress but need to refine our search. Another hint from the IDR logs is that the suspected infected machine connected to port 2404, which isn’t typically used in our network infrastructure.
To incorporate this new information, we’ll adjust our query as follows: ImagePath:”powershell” AND CommandLine:”$codigo” AND DestinationPort:”2404″.
ImagePath:”powershell” AND CommandLine:”$codigo” AND DestinationPort:”2404″
As the video above shows, this updated search gives us fewer tasks but most of them are clearly linked to the Remcos malware family. Remcos, a well-known Remote Access Trojan and it frequently uses PowerShell, which matches the symptoms we found earlier.
Threat Intelligence Lookup also displays malicious IP addresses that were discovered in the tasks. We can use these IPs to investigate further and better understand the malware’s behavior.
Bundle ANY.RUN TI Lookup and sandbox to get best price
Contact salesStep 3: Using IP address to investigate Remcos
To confirm that we’re dealing with Remcos, we’ll write a query that merges a network rule name with the IP address linked to port 2404. Also, we’ll refine our search to show only tasks from the last 7 days. It will look like this: RuleName:”remcos” AND DestinationIp:”107.172.31.178″
RuleName:”remcos” AND DestinationIp:”107.172.31.178″
The query returns one task linked to the specified IP tagged with Remcos. At this point, we can conclusively identify Remcos as the malware on the infected workstation.
Let’s open the task in the ANY.RUN sandbox
But let’s not stop here. By opening this sandbox task we can dissect all malicious TTPs associated with Remcos, utilizing ANY.RUN’s MITRE ATT&CK Matrix. We can also examine the details of malicious processes initiated by the malware.
We can then collect IOCs provided by the sandbox, with options to download a report in HTML or JSON formats to configure firewalls, SIEM and SOAR systems against this Remcos variant.
This illustrates just one of the many ways ANY.RUN’s Threat Intelligence Lookup can be a critical asset for cybersecurity analysts.
If you want the ultimate benefit, consider using ANY.RUN sandbox and Threat Intelligence Lookup together.
We’re also offering a trial with 20 search queries for existing ANY.RUN clients, who have purchased Searcher plan or above. Reach out to our sales team to gain access to the trial, find out more about the platform, or discuss pricing options.
The post ANY.RUN TI Lookup: a Phishing Case Study appeared first on ANY.RUN's Cybersecurity Blog.
Article Link: ANY.RUN TI Lookup: a Phishing Case Study - ANY.RUN's Cybersecurity Blog