At ANY.RUN, we’re always striving to provide more powerful capabilities to bolster your security operations. That’s why we’re thrilled to announce our latest integration: OpenCTI, the open-source platform for cyber threat intelligence.
This integration allows you to enrich OpenCIT observations with malware labels, malicious score, and indicators like TTPs, file hashes, IP addresses, and domains taken directly from ANY.RUN sandbox, or import observations from ANY.RUN Threat Intelligence Feeds.
You won’t have to manually cross-check data sources anymore — you’ll have all the information you need for quick threat analysis in one central place. Additionally, you can now easily enrich those objects with data gathered from interactive analysis sessions in ANY.RUN, where the malware was actually executed in a virtual environment.
What is OpenCTI?
OpenCTI is a Threat Intelligence Platform (TIP) that assists SOCs or MDR teams in collecting and enriching threat data from various sources like feeds, sandboxes, lookup portals, and other security solutions.
So how does the platform work? First, it collects data from all the resources you connect to it, like ANY.RUN’s threat feeds or other sources of IOCs, using different connectors. It saves this data as “observations” — observable events like file hashes, IP addresses, and other indicators of potential malicious activity.
We’ve released connectors for MITRE ATT&CK techniques and tactics, an ANY.RUN TI Feeds connector that imports data into OpenCTI once every 24 hours, and an ANY.RUN sandbox connector that you can use to enrich observations with data from sandbox analysis tasks, like malware family labels and maliciousness scores.
 OpenCTI interface
OpenCTI interface Enrich OpenCTI observations with data from ANY.RUN sandbox
Imagine you want to add threat data to an OpenCTI observation such as related IOCs and event’s field details and turn it into an OpenCTI indicator.
Now, you can use the ANY.RUN sandbox connector to submit the observation into ANY.RUN sandbox. We’ll spin up an interactive virtual machine, process the artifact, and observe its behavior. We’ll collect IOCs from network traffic, memory dumps, and observed activity, and attach them to the analyzed object within OpenCTI.
After enriching the object with additional information, you can then submit it to your Security Information and Event Management (SIEM) or Security Orchestration, Automation, and Response (SOAR) systems, generating a ticket for incident responders to investigate further.
Sign up for ANY.RUN for free
Get startedHow to use ANY.RUN enrichment connector in OpenCTI
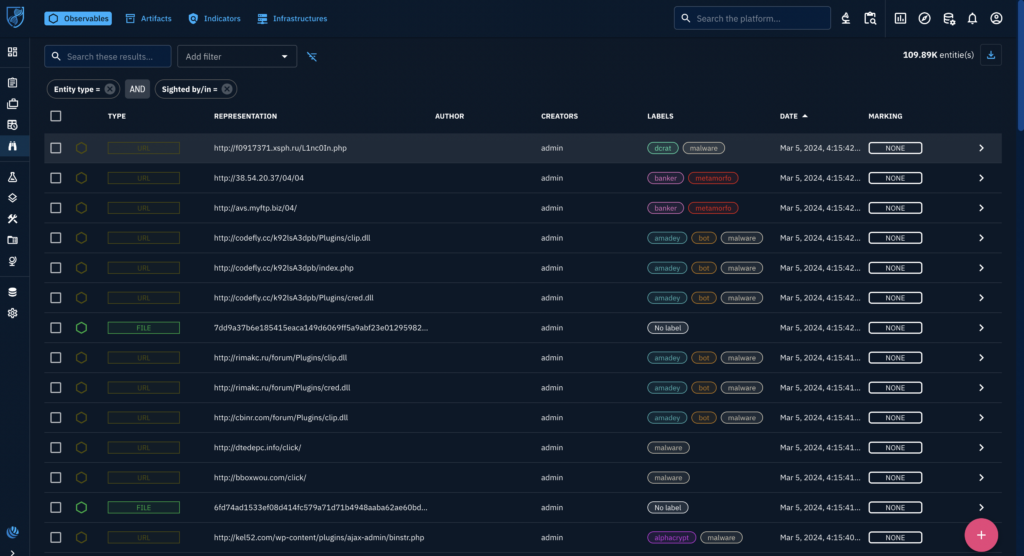
To use the enrichment connector, first go to the list of observables in the OpenCTI dashboard.
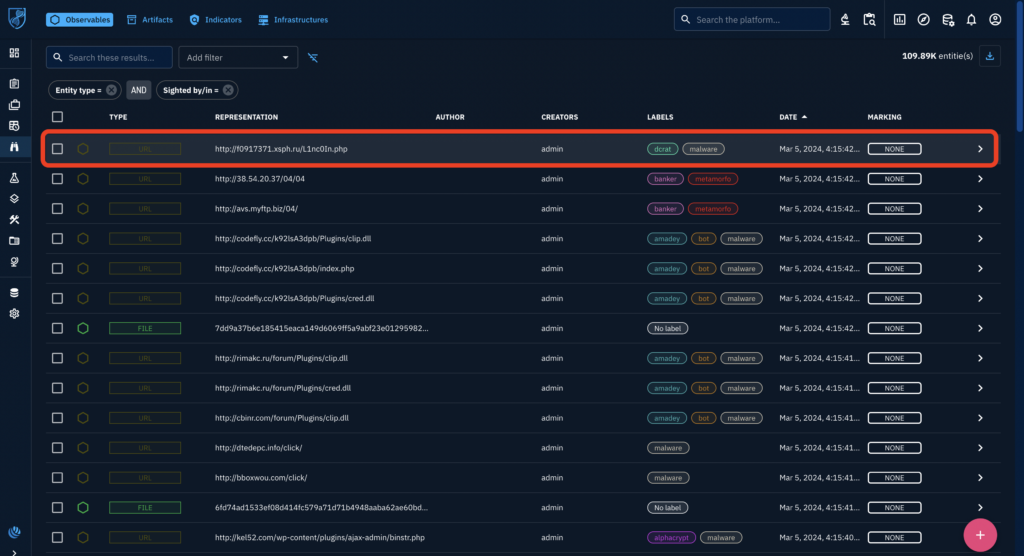
For a simple demonstration, we’ll select the first link in the list. Click on it to open the observable.
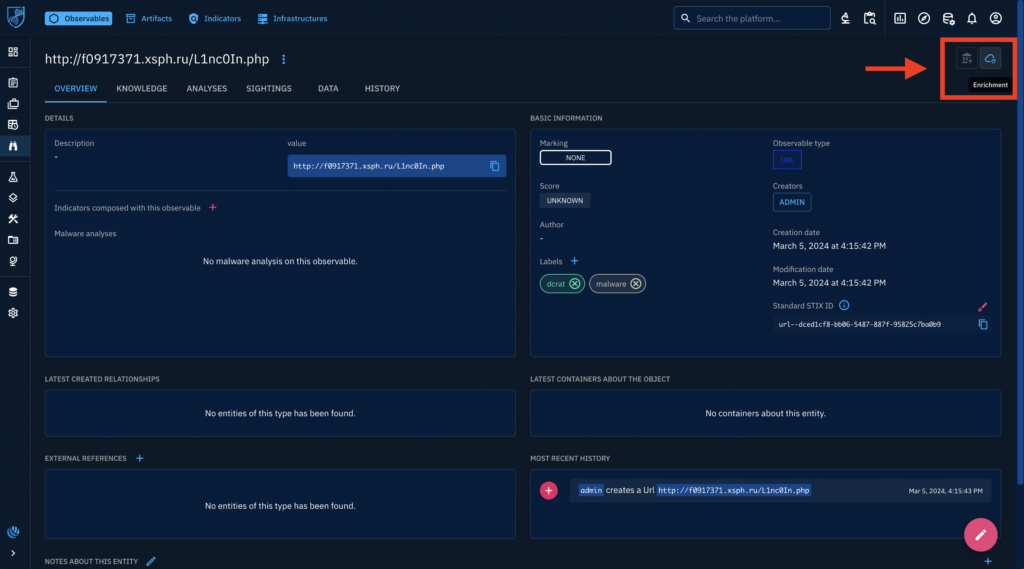
Note that the malware analysis panel (on the left) and references are empty. We will submit this task to ANY.RUN to gather more data. Click on the enrichment button on the top right of the screen.
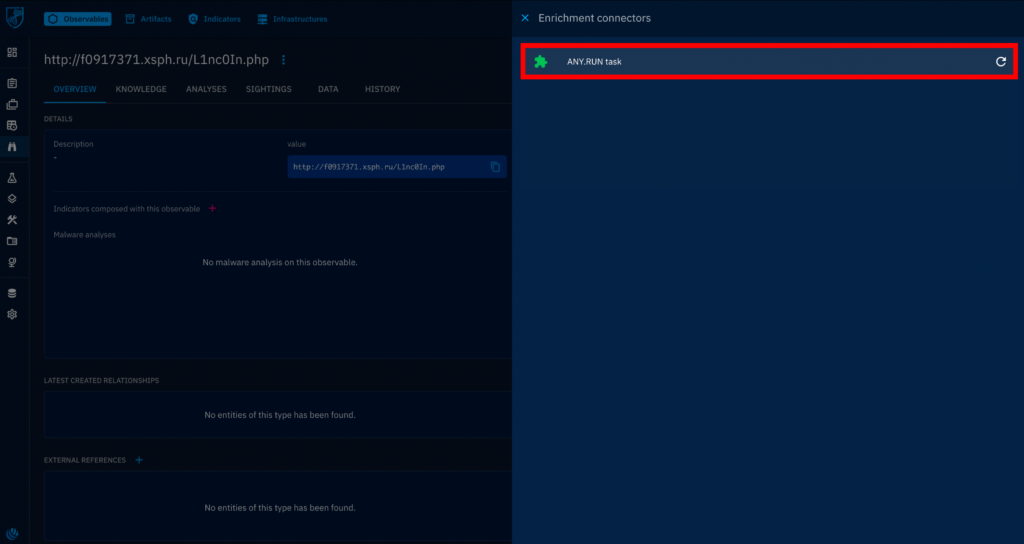
You will see a list of enrichment connectors. Choose ANY.RUN and click on the refresh button on the right.
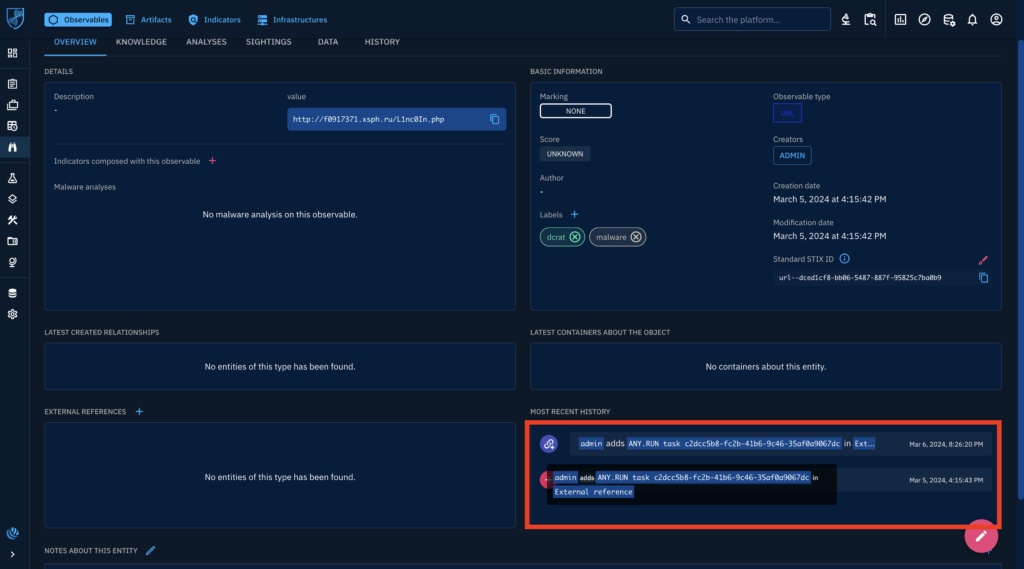
Now that we’ve used the connector, the enrichment is already happening behind the scenes, and you can see that a history item appeared. Sometimes you need to refresh the page if nothing happens immediately to see the results.
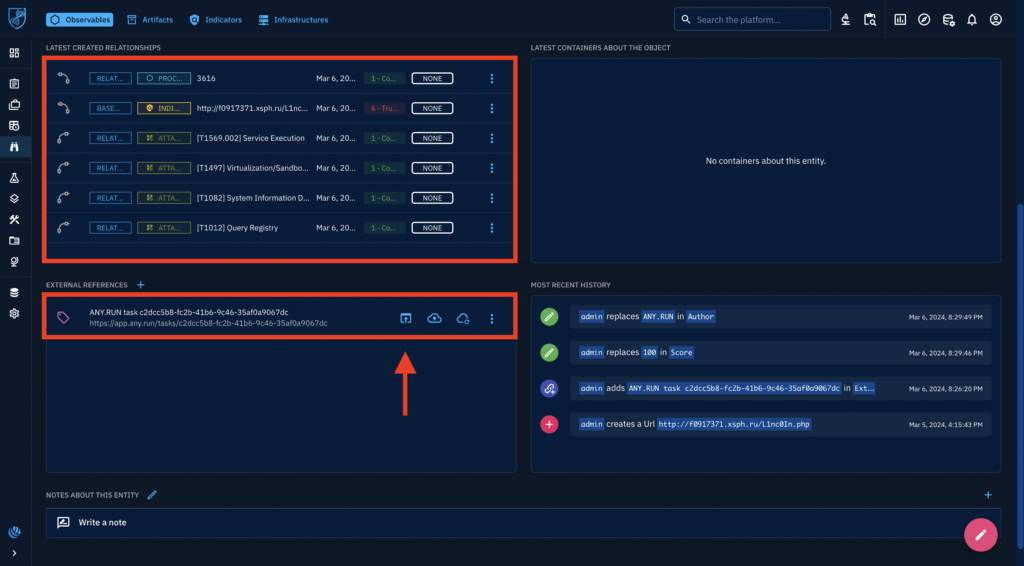
Now, you can see that multiple relationships were created, and we’ve enriched this observable with TTPs. There’s also an external reference — that’s the sandbox task. You can navigate to it to investigate further if you want, by clicking on the external link icon.
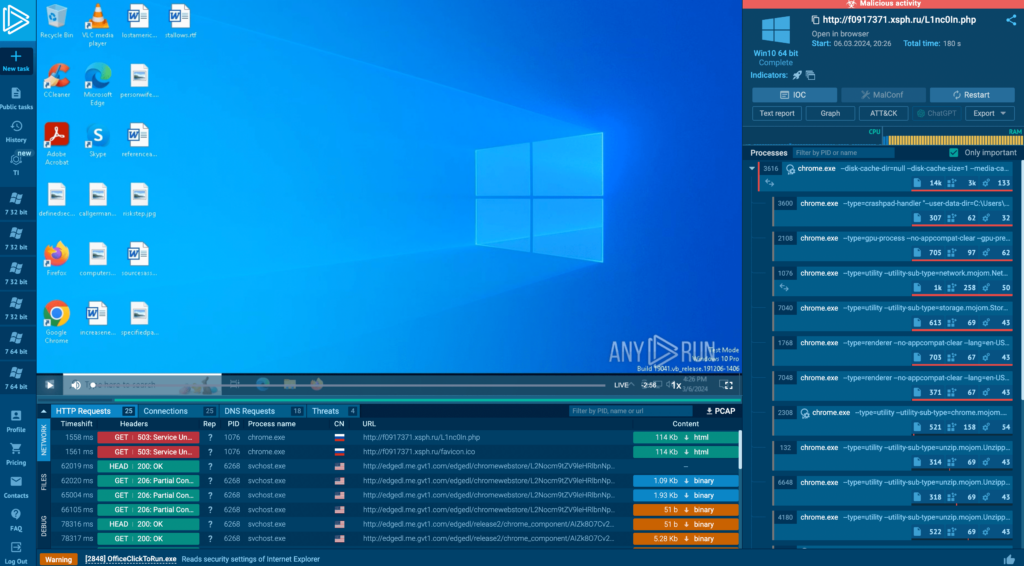
And here’s the task that we launched in ANY.RUN.
Get a personal demo of ANY.RUN for your SOC team
Book a callIn case you’re new here
What is ANY.RUN?
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of security teams. Every day, 400,000 professionals use our platform to investigate incidents and streamline threat analysis on Windows and Linux cloud VMs.
Advantages of ANY.RUN
- Real-time detection: Within roughly 40 seconds of uploading a file, ANY.RUN can detect malware and automatically identify many malware families using YARA and Suricata rules.
- Interactive analysis: Unlike many automated solutions, ANY.RUN allows you to interactively engage with the virtual machine directly through your browser. This interactive capability helps prevent zero-day exploits and sophisticated malware that can evade signature-based detection.
- Cost-Effective: For businesses, ANY.RUN’s cloud nature translates into a cost-effective solution, as it doesn’t require any setup or maintenance effort from your DevOps team.
- Great for onboarding new security team members: ANY.RUN’s intuitive interface allows even junior SOC analysts to quickly learn how to analyze malware and extract indicators of compromise IOCs.
If these capabilities sound beneficial for you or your team, give ANY.RUN a try. The best part is — we offer a completely free starter plan.
The post ANY.RUN Now Integrates with OpenCTI appeared first on ANY.RUN's Cybersecurity Blog.
Article Link: https://any.run/cybersecurity-blog/opencti-integration/