The Android worm Oji (2020) has recently re-surfaced with a fake app to register for COVID-19 vaccine.
 Splash screen for Android/Oji.G!worm (April 29, 2021)
Splash screen for Android/Oji.G!worm (April 29, 2021)The behavior of this family is well detailed here. This article only focuses on the new sample of late April 2021. This new sample begins a new campaign: it claims to register users for COVID-19 vaccination. If you are in doubt: this is totally fake, the app does not contact any vaccination center, its goal is merely to display ads and spread to the victims contacts via SMS.
Targeting end-users in India
As prior Oji campaigns, this one also targets end-users in India:
- The SMS message says “Register for Covid-19 Vaccine*\n*from age 18+ today.*\n\n*No Fees will be taken.*\n*It\’s absolutely Free in India.*[..]”
- The malware only spreads via SMS to contacts in India (+91 indicator)
3. More precisely, it only spreads to contacts who are using the indian JIO operator. The implementation knows JIO is used with 2 different techniques: (a) the phone number corresponds to ones JIO serves, or (b) it queries a public web API of JIO.
// Connect to public Web API to test if the phone number is affected to JIO
HttpsURLConnection conn = (HttpsURLConnection)new URL("https://www.jio.com/api/jio-recharge-service/recharge/mobility/number/" + number).openConnection();
conn.setRequestProperty("User-Agent", this.user_agent);
[..]
conn.setRequestMethod("GET");
conn.connect();
// Test response
String result = "";
int statusCode = conn.getResponseCode();
InputStream is = statusCode < 200 || statusCode >= 400 ? conn.getErrorStream() : conn.getInputStream();
BufferedReader in = new BufferedReader(new InputStreamReader(is));
// Read all answer lines and concatenate into result
while(true) {
String line = in.readLine();
if(line == null) { break; }
result = result + line;
}
// Check if result contains message NOT_SUBSCRIBED_USER
String fresult = result;
return fresult.contains("NOT_SUBSCRIBED_USER") ? false : fresult.contains(number);
Conclusion: if you have no contacts from India, the malware will not send any SMS — only display ads.
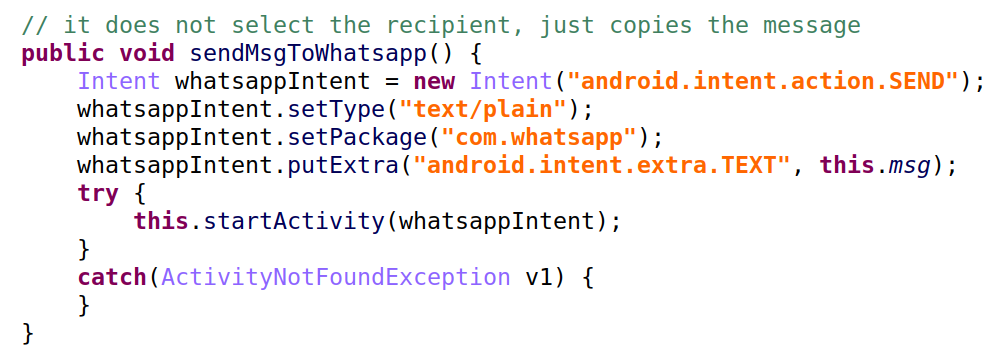
Spreading via WhatsApp
Contrary to SMS, the malware does not automatically spread via WhatsApp, it relies on the end-user to do so.

When the end-user clicks on the button “Share on WhatsApp”, the malware copies the message to the clipboard.
The shared message is “*Register for Covid-19 Vaccine*\n*from age 18+ today.*\n\n*No Fees will be taken.*\n*It\’s absolutely Free in India.*\n\n*Download Covid-19 android app*\n*and Register for COVID-19*\n*vaccine today.*\n\n*Link:* http://tiny.[REDACTED]CINE”The malware does not go as far as checking that the message is actually shared on WhatsApp. Actually, it does not even check WhatsApp is installed, it merely counts how many times the share button is clicked.
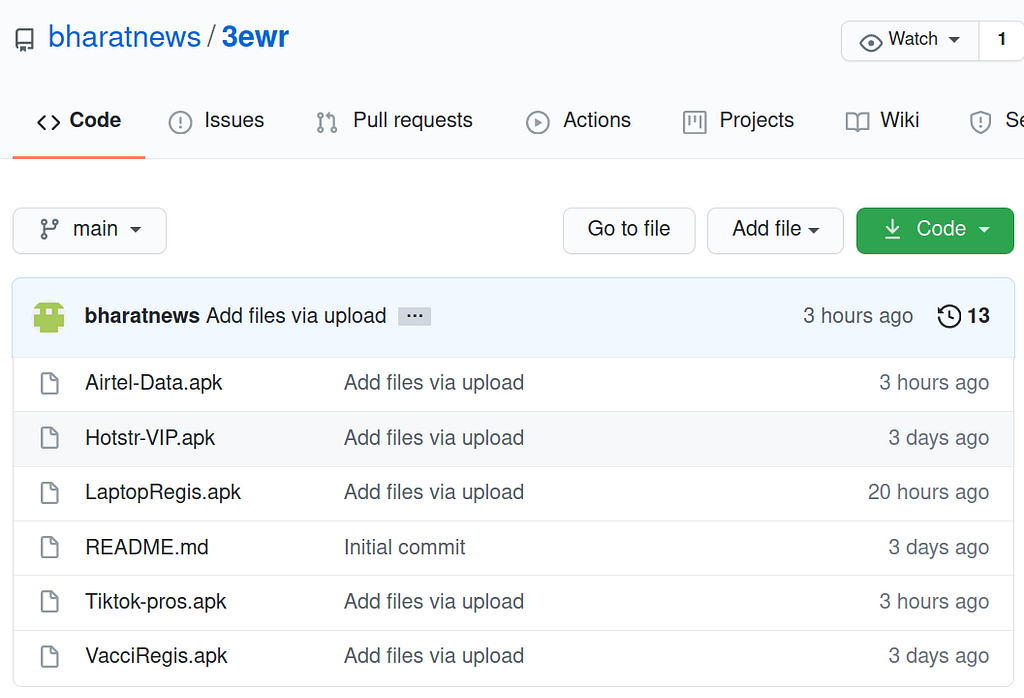
The malware is hosted on a malicious GitHub account
The URL in the SMS or WhatsApp message forwards to a website where new victims can download the Android application.
Malicious web page — when you click on Download now, you get Android/Oji wormThis application is downloaded from a malicious account on GitHub (GitHub has been notified of this abuse).
All samples on this account are Android/Oji worm, for various campaigns. The COVID-19 vaccine campaign is among the most recent ones.IOC
5522a7cc358b4193eac53e620d3baa47f385a04bf3d15d1850076cce9456d5f4
c03c89b2b95f44018eb3d4d7812e4a9efa44c563f331a36a24cad2f70af27f5b
d85330ff17c8d2f8d461c384b9eb3411c2f1f4d33fecd3acf127a5d9336c4e93
98c7390a248f3f06c12272439eaf8fa185634aceaae28612b5b231ca39faf8ae
2f21d6b5330aa5e74e632068908c0b11fa4d76fc7b67bce88bfef71171aa2e6e
07f40ac2ddd54b70cbd9760718feaa13f6b758414ec70ea4c88167ced33eba4d
a25363b68faa8188b99622d8909921a4026ea7241df6377d0a6374d2b2b4e08c
New malicious GitHub account: hxxps://github.com/bharatnews/3ewr
— Cryptax
PS. Kudosto @malwrhunterteam, @LukasStefanko and @banxen.