Hotsauce | S2W TALON
Executive Summary
- Analyze the bitcoin payment address of the Ragnarok ransomware
- Ragnarok transfers bitcoin to renBTC, performs a coin swap, and finally withdraws to Binance and Huobi exchanges
- Confirmation of 5 Bitcoin addresses used by Ragnarok ransomware to send renBTC and 2 Ethereum addresses used for coin swap
Detailed analysis
1. Abstract
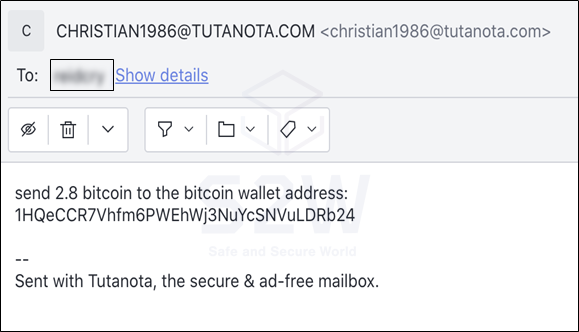
- Ragnarok ransomware negotiates with victims via email
- Confirm payment address through the ransom notes email contact (2021–07–28)
- Payment address : 1HQeCCR7Vhfm6PWEhWj3NuYcSNVuLDRb24
- Price : 2.8 BTC
- Contact mail : [email protected]
2. Analysis of payment address
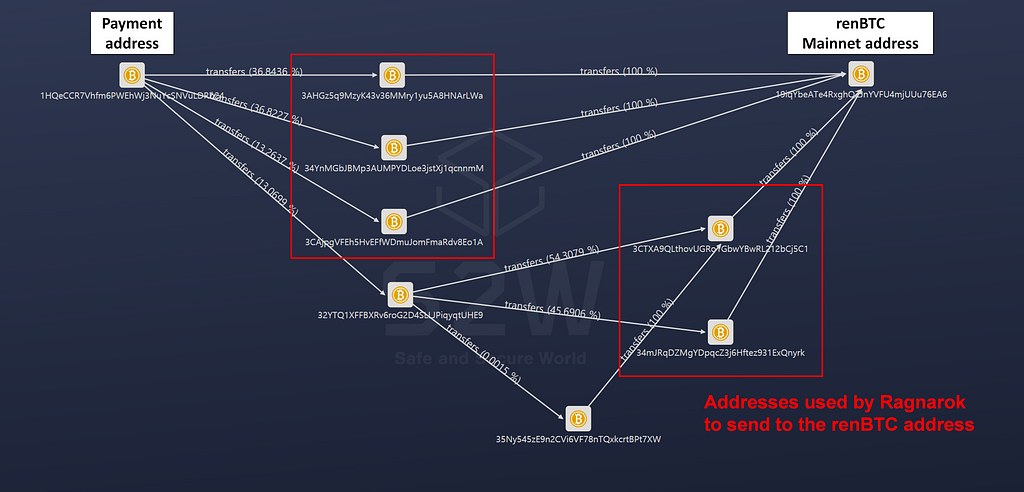
- The 2.8 BTC requested by the Ragnarok ransomware was not deposited, but while monitoring the payment address, it was confirmed that small deposits and withdrawals of less than 1 BTC were continuously occurring
- The deposited amount goes through several addresses and is finally sent to the address below
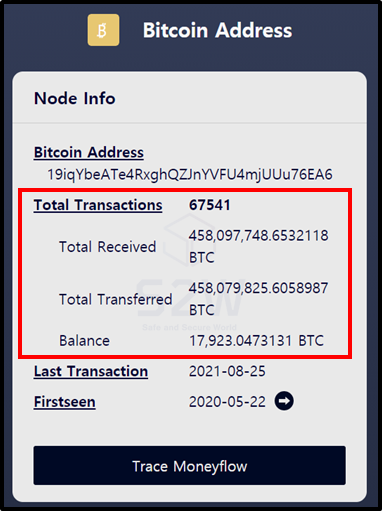
- This address is a Mainnet address of the network managed by renBTC
- renBTC Mainnet Address : 19iqYbeATe4RxghQZJnYVFU4mjUUu76EA6
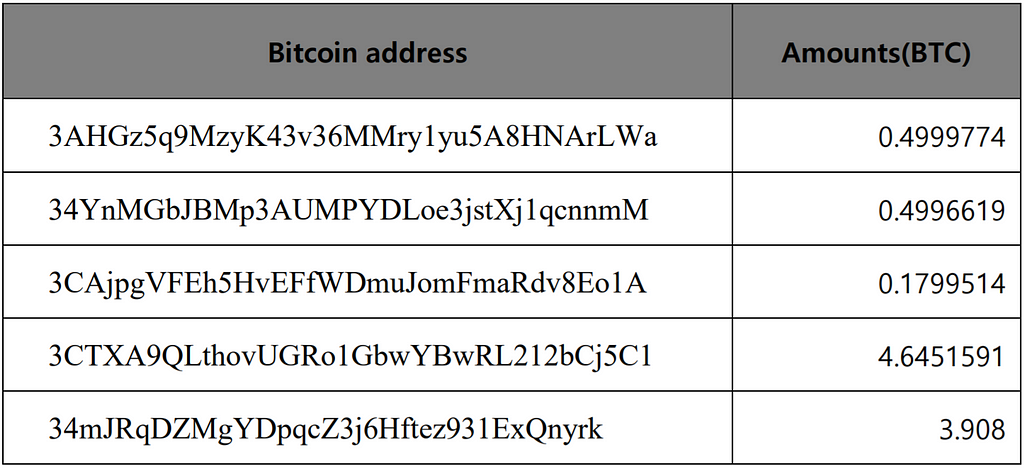
- List of Bitcoin addresses used by Ragnarok ransomware to send to renBTC addresses
2.1 What is renBTC

- ERC20 based DeFi coin created by Taiyang Zhang in May 2020 to provide liquidity on different blockchains
- When 1 BTC is sent to renBTC, 1 renBTC of the same value as 1 BTC is received. Using renBTC, transactions between ERC20-based coins including Ethereum are possible
- It can also be used for money laundering by using coin-to-coin transactions, such as swapping BTC to Ethereum (ERC20) or Ethereum (ERC20) to Bitcoin
- Similar DeFi coins include wBTC, tBTC, pBTC, etc.
2.2 Coin swap flow of Ragnarok ransomware
- Ragnarok performs a coin swap with ERC20-based coin (Tether, wETH) with the amount transferred to renBTC, and finally transfers it to Binance and Huobi exchanges
Conclusion
- The ransomware payment address is generally used for one-time use to prevent tracking, but the payment address presented by Ragnarok may have been used for other purposes as 14 transactions were made from July 29, 2021 to August 16, 2021.
- Recently, ransomware operators are demanding payment with Monero, which is difficult to trace compared to Bitcoin, but victims are paying with Bitcoin due to the Anti-Money Laundering Act (AML)
- Therefore, ransomware operators attempt money laundering by performing mixing using Wasabi wallet, ChipMixer, etc, or by swapping Bitcoin to another coin to avoid tracking Bitcoin
- It seems that it is necessary to track and analyze not only the Bitcoin addresses of ransomware operators, but also the transactions that are swapped with other coins such as Ethereum
Analysis of Ragnarok Ransomware Money Laundering Case Using DeFi Coin was originally published in S2W BLOG on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: Analysis of Ragnarok Ransomware Money Laundering Case Using DeFi Coin | by S2W | S2W BLOG | Aug, 2021 | Medium