In the realm of digital communication and collaboration, Zimbra Collaboration Suite has been a trusted ally for many. However, a shadow has been cast over its security recently. A one-click security vulnerability, capable of granting unauthorized access to Zimbra accounts, has surfaced across all versions of the platform. This alarming discovery underscores the critical importance of proactive security measures to safeguard sensitive information and communications.
One-Click Vulnerability in Zimbra Collaboration Suite
The vulnerability, identified as CVE-2023-41106, represents a one-click security flaw that poses a significant threat. A potential attacker could exploit this vulnerability by enticing Zimbra users with malicious links. When a user clicks on such a link, they inadvertently surrender their Zimbra credentials. These ill-gotten credentials provide the attacker with unrestricted access to the victim’s Zimbra account, potentially compromising confidential communications and data.
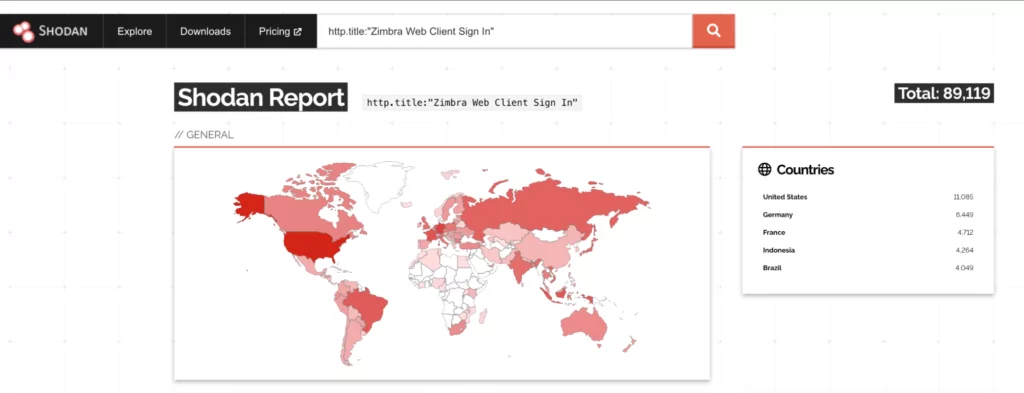 Servers that host Zimbra web client (Source: Shodan).
Servers that host Zimbra web client (Source: Shodan).
The impact of this vulnerability is far-reaching, affecting all iterations of the Zimbra Collaboration Suite, including even the latest versions. The patches listed below have successfully addressed this vulnerability:
- Daffodil 10.0.3
- 9.0.0 Kepler Patch 35
- 8.8.15 Joule Patch 42
For users employing an impacted Zimbra Collaboration Suite, immediate action is imperative. The patches are readily available on the official Zimbra website, standing as the first line of defense against this threat.
Mitigating the Risk
While patching remains a vital step in thwarting the vulnerability, there are interim measures that users can adopt to enhance their security posture.
Exercise Caution with Links: Vigilance should be exercised while interacting with links from untrusted sources. By refraining from clicking on suspicious links, users can significantly reduce the risk of falling victim to exploitation.
Mindful Form Input: Carefully scrutinize the information entered into online forms. By sharing information only with verified and reputable sources, users can curtail opportunities for attackers to exploit personal data.
Implement Two-Factor Authentication: The implementation of two-factor authentication adds an additional layer of security to Zimbra accounts. This practice enhances the authentication process, making it considerably more challenging for attackers to breach accounts even if they possess the login credentials.
Safeguarding Your Zimbra Experience with SOCRadar
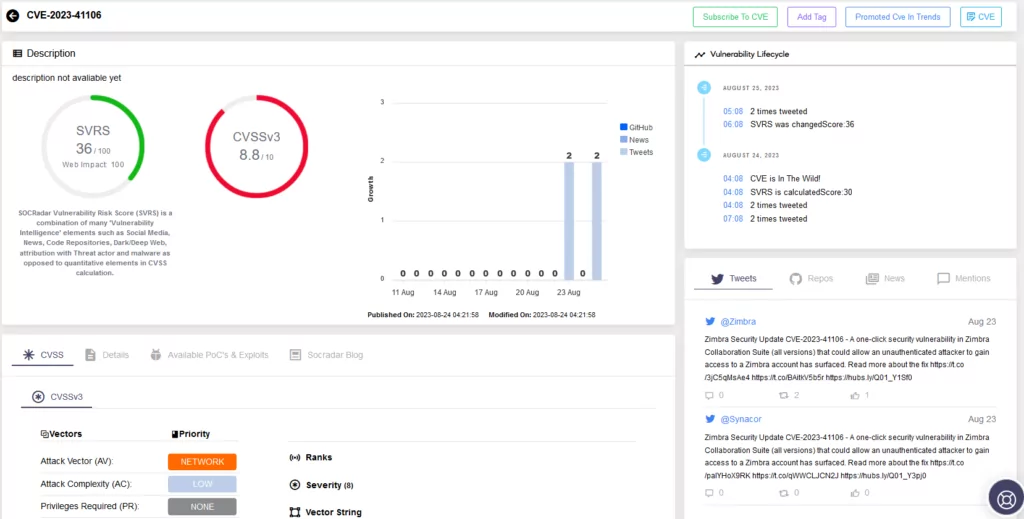 Vulnerability Intelligence page for CVE-2023-41106 in SOCRadar Platform.
Vulnerability Intelligence page for CVE-2023-41106 in SOCRadar Platform.
In a digital landscape marked by evolving threats, the responsibility of safeguarding our online experiences rests upon the collective efforts of users and security professionals alike. Companies like SOCRadar play a pivotal role in vulnerability intelligence, providing essential insights into emerging threats.
Vulnerabilities, like the one discovered in Zimbra Collaboration Suite, highlight the pressing need for continuous vigilance and prompt action. By promptly updating to the latest patches and adhering to security best practices, we collectively bolster our defenses against cyber threats.
The post A One-Click Security Vulnerability in Zimbra Collaboration Suite: CVE-2023-41106 appeared first on SOCRadar® Cyber Intelligence Inc..
Article Link: A One-Click Security Vulnerability in Zimbra Collaboration Suite: CVE-2023-41106
