On July 26th, ThreatConnect published an analysis of a coordinated phishing attack against Bellingcat, an investigative journalism website that specializes in fact-checking and open-source intelligence. Known for their work investigating Russia, Bellingcat researchers were carefully chosen targets, as stated by Bellingcat’s Eliot Higgins on Twitter.
Highly focused, the phishing campaign targeted only ten individuals, who have been identified by investigative journalist Christo Grozev. These include some researchers who do not work for Bellingcat but do investigate Russia.
ProtonMail, the email service used in the attack, published a short statement, which included some fascinating details on the attack from their perspective.
Introduction
In this article, we’ll explore a different angle to this campaign by analyzing it from the unique outside-in perspective of RiskIQ. RiskIQ data reveals multiple phishing campaigns involving different tactics beyond the analysis by ThreatConnect.
The earliest threat activity we see for this campaign was when the attackers registered mailprotonmail.com on June 27th, 2019. They also issued a Lets Encrypt certificate on the same day which we observed on 193.33.61.199, the same IP to which the mailprotonmail.com domain pointed.
We then observed the same certificate being served from 217.182.13.249 at the beginning of July. This IP address was mainly used later in the campaign for other phishing domains (more on this in the infrastructure investigation portion of this article).
From lure to phish
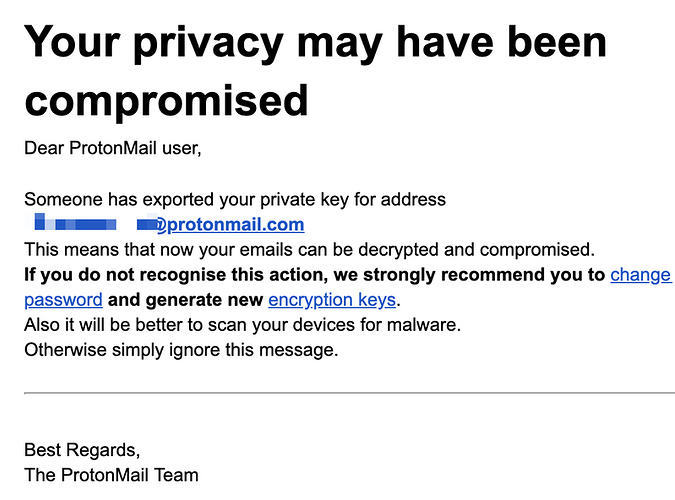
The attackers sent emails to a very select pool of targets indicating a possible breach of the integrity of the target’s ProtonMail account. Under the subject line, “Someone exported your encryption keys,” the attackers sent the following message:
In this article, we’ll explore a different angle to the phishing campaign against Bellingcat by analyzing it from the outside-in perspective of RiskIQ.
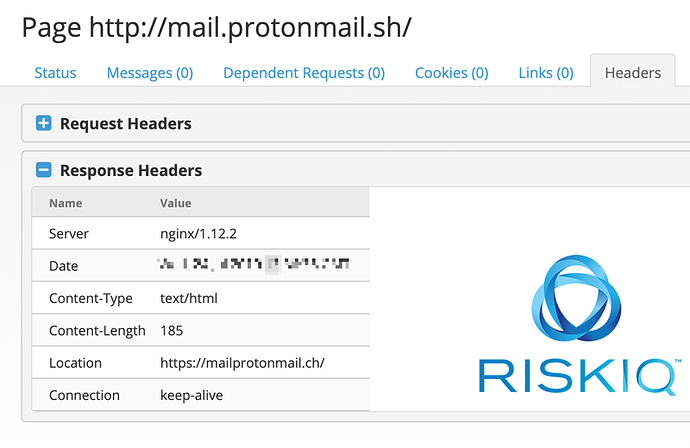
The July emails contained links to mail.protonmail.sh, with links to /password and /keys. These URLs redirected targets towards the final phishing pages on a new host, mailprotonmail.ch. Interestingly, the exact visited URLs wouldn’t matter; the server behind mail.protonmail.sh was instructed to always 301 redirect visitors to mailprotonmail.ch:
In this article, we’ll explore a different angle to the phishing campaign against Bellingcat by analyzing it from the outside-in perspective of RiskIQ.
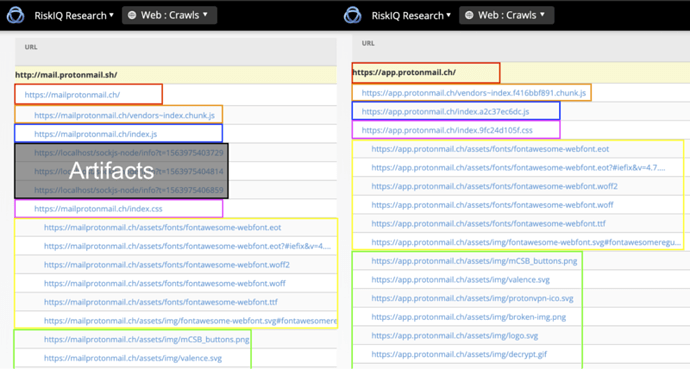
The final landing page was a copy of the real ProtonMail app. We can see they didn’t depend on the caching mechanism ProtonMail has in place typically, but all other resources will match up perfectly:
In this article, we’ll explore a different angle to the phishing campaign against Bellingcat by analyzing it from the outside-in perspective of RiskIQ.
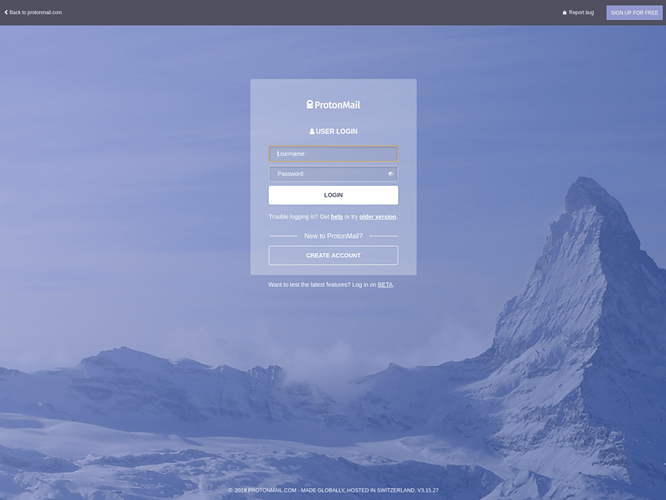
The design of the phishing page shown to the visitor matched the ProtonMail app login prompt:
In this article, we’ll explore a different angle to the phishing campaign against Bellingcat by analyzing it from the outside-in perspective of RiskIQ.
As we stated at the beginning of this article, the recent coverage looked explicitly at the July campaign and its activity and associated infrastructure. We can confirm these spear-phishing attacks have been happening since late June.
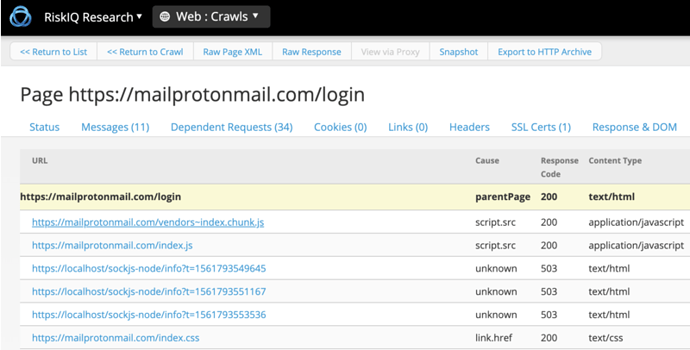
On June 27th, we observed the above registration, for mailprotonmail.com, which the attackers used in earlier spear-phishing emails. The lure in these emails was slightly different from the July campaign: simple log in pages. The emails contained links to /login on the mailprotonmail.com.
We observed our first hits for these phishing emails soon after the domain was set up. Here is a crawl from the end of June:
In this article, we’ll explore a different angle to the phishing campaign against Bellingcat by analyzing it from the outside-in perspective of RiskIQ.
The setup for this phishing page was the same as the later attacks in July, the lure sent to the targets was just slightly different. The targets identified in the July attacks might be part of a broader set, but we do not think it will expand beyond individuals who investigate Russia.
There was another campaign before the June and July campaigns using phishing pages hosted through my.secure-protonmail.com. This continuation of phishing attempts tells us the attackers were highly focused on their targets. The duration of their campaign might also tell us they weren’t quite finished.
Associated Infrastructure (IOCs)
While there are a lot of suspected infrastructure points to this group, including those used in other threat campaigns, we will only list the infrastructure confirmed by RiskIQ crawlers.
Additionally, all infrastructure pieces provided here are also available in a RiskIQ Community project (no need to register or authenticate) here:
https://community.riskiq.com/projects/c0975eea-b821-07d5-a20e-da04b6758bf7
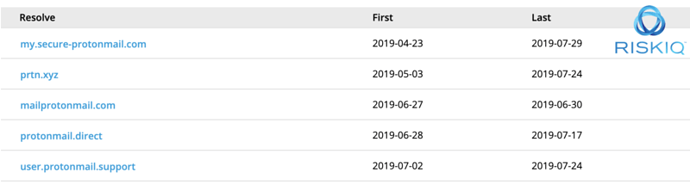
The earliest IP infrastructure we have pinned down this campaign was in April when 193.33.61.199 started to be used for a few domains:
In this article, we’ll explore a different angle to the phishing campaign against Bellingcat by analyzing it from the outside-in perspective of RiskIQ.
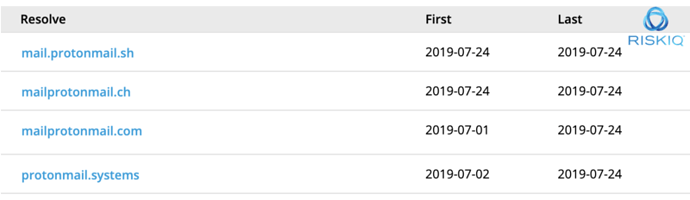
The second IP address 217.182.13.249 started to get used by the actors between half of June into early July:
In this article, we’ll explore a different angle to the phishing campaign against Bellingcat by analyzing it from the outside-in perspective of RiskIQ.
The domains registered by the attackers tell a different story, however. Domain infrastructure was being registered back in March of this year. Here is the full set of associated domains sorted on registration/creation date with the registrar used:
| Domain | Registration date | Registrar |
| mailprotonmail.ch | 2019-07-22 | epag domainservices gmbh |
| mailprotonmail.co | 2019-07-22 | tucows domains inc. |
| mailprotonmail.com | 2019-06-27 | tucows domains inc. |
| protonmail.sh | 2019-06-27 | epag domainservices gmbh |
| prtn.app | 2019-06-27 | tucows domains inc |
| protonmail.direct | 2019-06-21 | tucows domains inc. |
| protonmail.gmbh | 2019-06-21 | tucows domains inc. |
| protonmail.systems | 2019-06-21 | tucows domains inc. |
| protonmail.support | 2019-05-06 | tucows domains inc. |
| protonmail.team | 2019-05-06 | tucows domains inc. |
| protonmail.earth | 2019-04-22 | web4africa inc. |
| secure-protonmail.com | 2019-04-11 | web4africa inc. |
| prtn.xyz | 2019-04-11 | web4africa inc. |
| prtn.email | 2019-03-12 | tucows domains inc. |
Additionally, the attackers make use of the free Let’s Encrypt certificate service. You can track parts of the infrastructure by looking up the domain names against our expansive SSL certificate database. For example, here are two serial numbers for two of the domains that can be tracked through infrastructure (serial numbers will not be updated/changed for extending certificates with Let’s Encrypt):
https://community.riskiq.com/search/certificate/serialNumber/285200805608237752767204219352640170865
The post A Deeper Look at the Phishing Campaigns Targeting Bellingcat Researchers Investigating Russia appeared first on RiskIQ.
Article Link: https://www.riskiq.com/blog/labs/bellingcat-phishing/