 Rundll32
Rundll32
When threat hunting malware one of the key skills to have is an understanding of the platform and the OS. To make the distinction between the good and the bad one has to know what’s good first.
On windows this can be a little tricky to achieve because of the complexity of the OS (after all it’s a 30+ years’ operating system).
Knowing this fact, malware authors write their malware to mimic normal windows processes. So you’ll see malware disguising itself as an “svchost.exe”, “rundll32.exe” or “lsass.exe” process, exploiting the fact that the majority of people using windows don’t know how these system processes behave in normal conditions.
Last time we’ve talked about the “svchost.exe” process and its command line options.
Demystifying the “SVCHOST.EXE” Process and Its Command Line Options
Today however we’ll be taking a look at “rundll32.exe” and understanding a little bit more about it.
RUNDLL32.EXE
As the name suggest, the “rundll32.exe” executable is used to “RUN DLL’s” or Dynamic Link Libraries (Below is the definition of a DLL from MSDN).
A dynamic-link library (DLL) is a module that contains functions and data that can be used by another module (application or DLL) — MSDN
The most basic syntax for using “rundll32.exe” is the following.
rundll32 <DLLname>
The “rundll32.exe” executable can be a child or a parent process, it all depend on the context of the execution. And to determine if an instance of “rundll32.exe” is malicious or not we need to take a look at a couple of things. First is the path from which its being launched and second is its command line.
The valid “RUNDLL32.EXE” process is always located at:
\Windows\System32\rundll32.exe
\Windows\SysWOW64\rundll32.exe (32bit version on 64bit systems)
As for the command line of a “rundll32.exe” instance it all depends on what’s being launched whether be it a CPL file, a DLL install…etc.
For this let’s take a look at a couple of examples.
Running a DLL
In its basic form, “rundll32.exe” will just execute a DLL, so the first thing to check when seeing an instance of “rundll32.exe” is the legitimacy of the DLL being called.
Always check the location from where the DLL is called, for example kernel32.dll being called from %temp% is obviously malicious. And as a side note always check the hash on sites like VT.
SHELL32.DLL — “OpenAs_RunDLL”
“rundll32.exe” can also execute specific functions in DLL’s. For example, when selecting a file and performing a right click on it, a context menu will be shown that offers multiple options. One of the options is the “OpenWith” option. Once selected a pop-up will appear that’ll let’s select from a set of applications on the system.
Behind the scene this is actually launching the “rundll32.exe” utility with the “shell32.dll” and the “OpenAs_RunDLL” function.
C:\Windows\System32\rundll32.exe C:\Windows\System32\shell32.dll,OpenAs_RunDLL <file_path>
This behavior of calling specific functions in a DLL is very common and it can be tricky to know all of them in advance. Below is a list containing a batch of “rundll32.exe” calls and their meaning.
- https://www.tenforums.com/tutorials/77458-rundll32-commands-list-windows-10-a.html
- http://chagdali.free.fr/dcs/RunDll.htm
SHELL32.DLL — “Control_RunDLL”, “Control_RunDLLAsUser” and Control Panel Applets
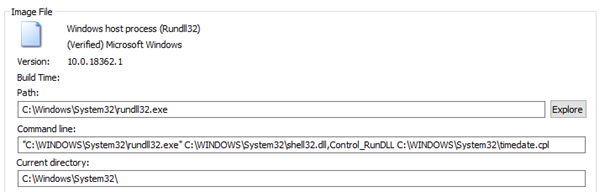
Another common function we’ll see used with the “shell32.dll” is “Control_RunDLL” / “Control_RunDLLAsUser”. These two are used to run “.CPL” files or control panel items.
For example, when we want to change the Date and Time of the computer we launch the applet from the control panel.
Behind the scene, windows launched a “rundll32.exe” instance with the following command line.
C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,Control_RunDLL C:\WINDOWS\System32\timedate.cpl
In addition to verifying the legitimacy of a DLL. When using the “Control_RunDLL” / “Control_RunDLLAsUser” functions, you should always check the legitimacy of a “.CPL” file.
Control Panel Items (.CPL)
CPL or Control Panel Items are programs that represent a functionality provided by the control panel or in other terms, they are DLL’s that exports the CPIApplet Function.
A “.CPL” file can contain multiple applets that can be referred to by an applet index and each applet can contain multiple tabs that can be referred to by a tab index.
We can access and request this information via the “rundll32.exe” utility as follow.
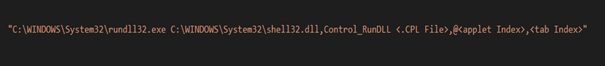
For example, the “main.cpl” file in the System32 folder contains two applets. The “Mouse” and “Keyboard” properties. If we want to access the mouse properties and change the pointer, we’ll do it like this.
C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,Control_RunDLL C:\WINDOWS\System32\main.cpl,@0,1As you can see, one can easily replace the “main.cpl” file with a malicious version and come by unnoticed to the untrained eye. In fact, that’s what malware authors have been doing to infect users.
In a normal case scenario, the parent process of a “rundll32.exe” instance with the “Control_RunDLL” function should be “explorer.exe” or “control.exe”
Other processes can also launch “rundll32.exe” with that function. For example, it can be a child of “Google Chrom”, “MSGEDGE” or “IE” when launching the “inetcpl.cpl” for proxy / network configuration.
If you want more details about CPL and how malware is using it, you can read this trend micro research paper called CPL Malware.
DEVCLNT.DLL — “DavSetCookie” (Web Dav Client)
One of the mysterious command lines in a “rundll32.exe” instance that’ll show up a lot in the logs, takes the following format.
C:\WINDOWS\System32\rundll32.exe C:\Windows\system32\davclnt.dll,DavSetCookie <Host> <Share>
When using the “file://” protocol, whether be it in a word file, or via share windows will sometimes use (if SMB is disabled in some cases) the WebDav Client to request these files. When that happens a request will be made via the “rundll32.exe” utility.
The parent process of such requests will be “svchost.exe” like so. (The “-s WebClient” is not obligatory)
C:\Windows\system32\svchost.exe -k LocalService -p -s WebClient
Malware like Emotet has already used this technique in the past. So always analyze the host that is present in this type of command line and make sure that everything is legitimate.
RUNDLL32.EXE — “-sta” / “-localserver” Flags
A lesser known command line arguments are the “-sta” and “-localserver”. Which both can be used to load malicious registered COM objects.
If you see in your logs or a process running with one of the following command line arguments.
rundll32.exe –localserver <CLSID_GUID>
rundll32.exe –sta <CLSID_GUID>
You need to verify the corresponding registry key [\HKEY_CLASSES_ROOT\CLSID<GUID>] and its sub-keys and values for any malicious DLL or SCT script.
I highly suggest you read @bohops blog post for a detailed explanation on this technique and check hexacorn blog for the “-localserver” variant.
Abusing the COM Registry Structure: CLSID, LocalServer32, & InprocServer32
RUNDLL32.EXE — Executing HTML / JAVASCRIPT
One other command line argument that attackers may use with “rundll32.exe” is the “javascript” flag.
In fact a “rundll32.exe” instance can run HTML / JavaScript code using the “mshtml.dll” and the “javascript” keyword (See Below).
rundll32.exe javascript:"..\mshtml,RunHTMLApplication <HTML Code>
I’ve never seen this used in a legitimate way. So if you spot this in your logs, it is worth investigating.
You can check the following resources to learn more about this technique.
- https://pentestlab.blog/2017/05/23/applocker-bypass-rundll32/
- https://oddvar.moe/2017/12/13/applocker-case-study-how-insecure-is-it-really-part-1/
- https://lolbas-project.github.io/lolbas/Binaries/Rundll32/
Conclusion
Thanks for reading and I hope you enjoyed this quick look at Rundll32.
If you have any feedback or suggestions, send them my way via twitter @nas_bench
References
- https://bohops.com/2018/06/28/abusing-com-registry-structure-clsid-localserver32-inprocserver32/
- https://threathunterplaybook.com/evals/apt29/report.html
- https://www.hexacorn.com/blog/2020/02/13/run-lola-bin-run/
- https://www.trendmicro.de/cloud-content/us/pdfs/security-intelligence/white-papers/wp-cpl-malware.pdf
- https://support.microsoft.com/en-us/help/149648/description-of-control-panel-cpl-files
- https://isc.sans.edu/forums/diary/Lets+Trade+You+Read+My+Email+Ill+Read+Your+Password/24062/
- https://blog.didierstevens.com/2017/11/13/webdav-traffic-to-malicious-sites/
Article Link: A Deep Dive Into RUNDLL32.EXE. Understanding “rundll32.exe” command… | by Nasreddine Bencherchali | Medium