Did you know we’re running a Bug Bounty Extravaganza again?
Earn over 6x our usual bounty rates, up to $10,000, for all vulnerabilities submitted through May 27th, 2024 when you opt to have Wordfence handle responsible disclosure!
On February 25th, 2024, during our second Bug Bounty Extravaganza, we received a submission for a Privilege Escalation vulnerability in MasterStudy LMS, a WordPress plugin with more than 10,000 active installations. This vulnerability makes it possible for an unauthenticated attacker to grant themselves administrative privileges by updating user metadata during registration. The next day on February 26th, 2024, and later on March 31st, we also received submissions for a Local File Inclusion vulnerability in the MasterStudy LMS WordPress plugin. This vulnerability makes it possible for unauthenticated attackers to include and execute arbitrary files on the server, allowing the execution of any PHP code in those files.
Props to Hiroho Shimada who discovered and responsibly reported these vulnerabilities through the Wordfence Bug Bounty Program. This researcher earned a bounty of $625.00 for the Privilege Escalation and $312.00 for the Local File Inclusion during our Bug Bounty Program Extravaganza. Our mission is to Secure the Web, which is why we are investing in quality vulnerability research and collaborating with researchers of this caliber through our Bug Bounty Program. We are committed to making the WordPress ecosystem more secure, which ultimately makes the entire web more secure.
All Wordfence Premium, Wordfence Care, and Wordfence Response customers, as well as those using the free version of our plugin, are protected against any exploits targeting these vulnerabilities by the Wordfence firewall’s protection.
We contacted StylemixThemes on March 13, 2024, and received a response on the same day. After providing full disclosure details, the developer released the first patch on March 20, 2024, the second patch on March 27, 2024, and the third patch on April 4, 2024. We would like to commend StylemixThemes for their prompt response and timely patches.
We urge users to update their sites with the latest patched version of MasterStudy LMS, which is version 3.3.4, as soon as possible.
Vulnerability Summary from Wordfence Intelligence
Affected Plugin: MasterStudy LMS
Plugin Slug: masterstudy-lms-learning-management-system
Affected Versions: <= 3.3.1
CVE ID: CVE-2024-2409
CVSS Score: 9.8 (Critical)
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Researcher/s: Hiroho Shimada
Fully Patched Version: 3.3.2
Bounty Award: $625.00
The MasterStudy LMS plugin for WordPress is vulnerable to Privilege Escalation in all versions up to, and including, 3.3.1. This is due to insufficient validation checks within the _register_user() function called by the ‘wp_ajax_nopriv_stm_lms_register’ AJAX action. This makes it possible for unauthenticated attackers to register a user with administrator-level privileges when MasterStudy LMS Pro is installed and the LMS Forms Editor add-on is enabled.
Affected Plugin: MasterStudy LMS
Plugin Slug: masterstudy-lms-learning-management-system
Affected Versions: <= 3.3.0
CVE ID: CVE-2024-2411
CVSS Score: 9.8 (Critical)
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Researcher/s: Hiroho Shimada
Fully Patched Version: 3.3.1
Bounty Award: $312.00
The MasterStudy LMS plugin for WordPress is vulnerable to Local File Inclusion in all versions up to, and including, 3.3.0 via the ‘modal’ parameter. This makes it possible for unauthenticated attackers to include and execute arbitrary files on the server, allowing the execution of any PHP code in those files. This can be used to bypass access controls, obtain sensitive data, or achieve code execution in cases where images and other “safe” file types can be uploaded and included.
Affected Plugin: MasterStudy LMS
Plugin Slug: masterstudy-lms-learning-management-system
Affected Versions: <= 3.3.3
CVE ID: CVE-2024-3136
CVSS Score: 9.8 (Critical)
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Researcher/s: Hiroho Shimada
Fully Patched Version: 3.3.4
The MasterStudy LMS plugin for WordPress is vulnerable to Local File Inclusion in all versions up to, and including, 3.3.3 via the ‘template’ parameter. This makes it possible for unauthenticated attackers to include and execute arbitrary files on the server, allowing the execution of any PHP code in those files. This can be used to bypass access controls, obtain sensitive data, or achieve code execution in cases where images and other “safe” file types can be uploaded and included.
Technical Analysis #1: Privilege Escalation via stm_lms_register AJAX Action
MasterStudy LMS is a WordPress plugin, which includes many features, such as user-friendly course builder, and the MasterStudy LMS Pro plugin provides a lot of premium add-ons for the free plugin.
Examining the code reveals that the plugin uses the stm_lms_register() function in the STM_LMS_User class to handle registration. If a user is successfully added, this function calls the _register_user() function. Unfortunately, this function was implemented insecurely, allowing unauthenticated users to modify their capabilities, including granting themselves administrator capabilities.
public static function _register_user( $user, $data, $user_email ) { // phpcs:ignore PSR2.Methods.MethodDeclaration.Underscore
$login_data = array(
'user_login' => $data['register_user_login'],
'user_password' => $data['register_user_password'],
'remember' => false,
);
wp_signon( $login_data, is_ssl() );
if ( class_exists( 'STM_LMS_Form_Builder' ) ) {
$default_fields = self::_user_profile_fields();
}
/*If everything is right, check for Instructor application*/
STM_LMS_Instructor::become_instructor( $data, $user );
if ( ! empty( $default_fields ) && ! empty( $data['profile_default_fields_for_register'] ) ) {
foreach ( $data['profile_default_fields_for_register'] as $index => $field ) {
if ( isset( $field['value'] ) && in_array( $field['label'], array_column( $default_fields, 'label' ) ) ) { // phpcs:ignore WordPress.PHP.StrictInArray.MissingTrueStrict
update_user_meta( $user, $index, $field['value'] );
}
}
}</pre>
The user meta is only updated for fields belonging to profile_default_fields_for_register if the $default_fields value is not empty. This only happens if the STM_LMS_Form_Builder class exists, which is a pro add-on class. This means that the vulnerability can only be exploited when MasterStudy LMS Pro is installed and the LMS Forms Editor add-on is enabled.
The most significant problem and vulnerability is caused by the fact that there are no restrictions on the profile fields, so the user’s metadata can be specified arbitrarily, and there is no sanitization on the field value, so any value can be set, including an array value, which is necessary for the capability meta option.
This made it possible for unauthenticated users to supply the ‘wp_capabilities’ array parameter with any desired capabilities, such as administrator, during the registration.
As with any Privilege Escalation vulnerability, this vulnerability can be used for a complete site compromise. Once an attacker has gained administrative user access to a WordPress site, they can then manipulate anything on the targeted site as a normal administrator would. This includes the ability to upload plugin and theme files, which can be malicious zip files containing backdoors. Additionally, they could modify posts and pages which can be leveraged to redirect site users to other malicious sites or inject spam content.
Wordfence Firewall
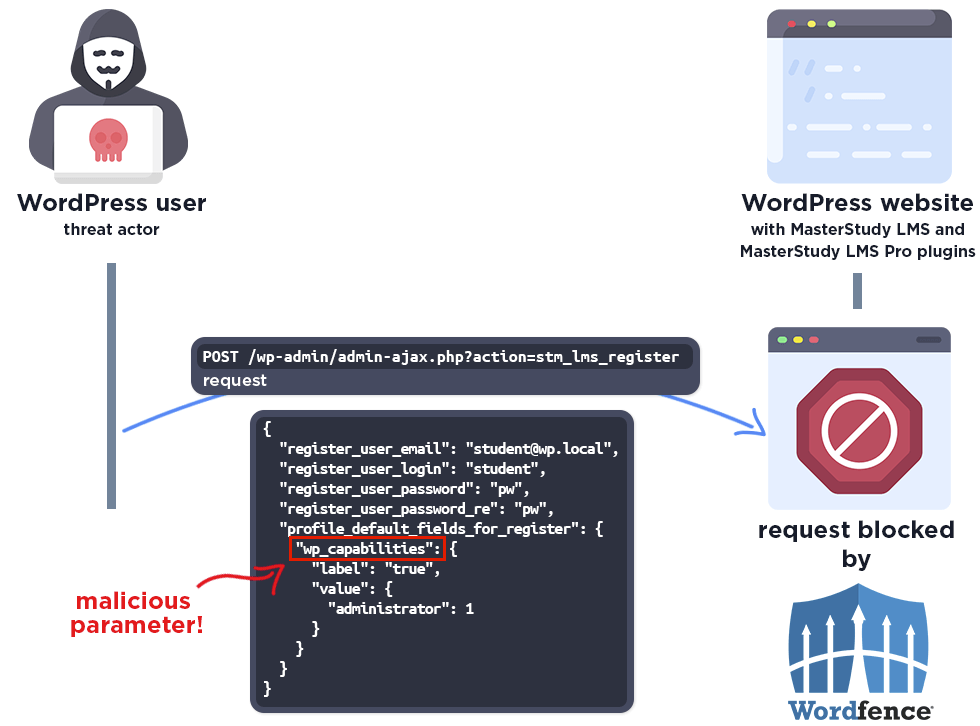
The following graphic demonstrates the steps to exploitation an attacker might take and at which point the Wordfence firewall would block an attacker from successfully exploiting the vulnerability.
The Wordfence firewall rule detects the malicious parameter and blocks the request.
Technical Analysis #2: Local File Inclusion via modal
Examining the code reveals that the plugin uses the load_modal() function in the STM_LMS_Helpers class to load the modal template file via AJAX.
public static function load_modal() {
check_ajax_referer( 'load_modal', 'nonce' );
if ( empty( $_GET['modal'] ) ) {
die;
}
$r = array();
$modal = 'modals/' . sanitize_text_field( $_GET['modal'] );
$params = ( ! empty( $_GET['params'] ) ) ? json_decode( stripslashes_deep( $_GET['params'] ), true ) : array();
$r['params'] = $params;
$r['modal'] = STM_LMS_Templates::load_lms_template( $modal, $params );
wp_send_json( $r );
}
This function calls the load_lms_template() in the STM_LMS_Helpers class.
public static function load_lms_template( $template_name, $stm_lms_vars = array() ) {
ob_start();
extract( $stm_lms_vars ); // phpcs:ignore WordPress.PHP.DontExtract
$tpl = self::locate_template( $template_name, $stm_lms_vars );
if ( file_exists( $tpl ) ) {
include $tpl;
}
return apply_filters( "stm_lms_{$template_name}", ob_get_clean(), $stm_lms_vars );
}
The code reveals that there is no file path sanitization anywhere in these functions. This makes it possible to include arbitrary PHP files from the server through the 'modal' parameter.
The file inclusion is limited to PHP files in the vulnerability. This means that threat actors cannot exploit one of the most popular remote code execution methods via a log file poisoning attack. In addition, since the plugin also uses the file_exists() function for file checking, the other popular remote code execution method using wrappers is also not possible. Nevertheless, an attacker has several options to include and exploit a malicious PHP file and execute it on the server. This can be achieved by chaining the attack and exploiting vulnerabilities in other plugins. However, it’s worth mentioning that the attack possibilities are limited. This vulnerability would likely be leveraged in a scenario where an attacker has access to upload a PHP file, but does not have direct access to the file to execute it.
The researcher presented to us an exploit where pearcmd.php is used for remote code execution, which is also a common attack method for local file inclusion vulnerabilities.
Wordfence Firewall
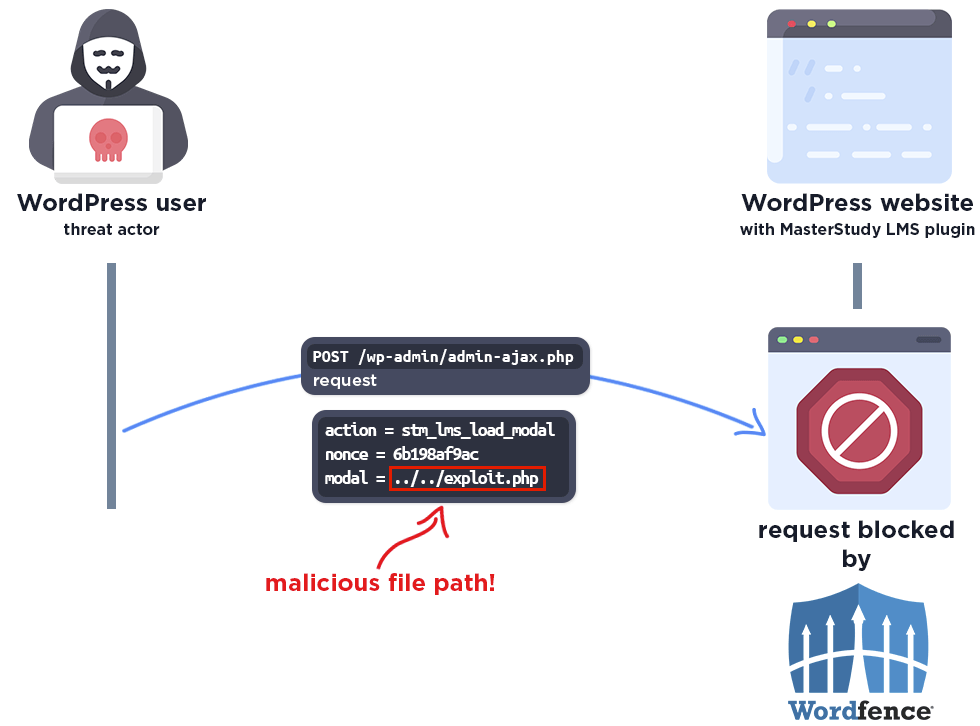
The following graphic demonstrates the steps to exploitation an attacker might take and at which point the Wordfence firewall would block an attacker from successfully exploiting the vulnerability.
The Wordfence firewall rule detects the malicious file path and blocks the request.
Technical Analysis #3: Local File Inclusion via template
Examining the code reveals that the plugin uses the load_content() function in the STM_LMS_Helpers class to load the courses with the specified template via AJAX.
public static function load_content() {
check_ajax_referer( 'load_content', 'nonce' );
if ( empty( $_GET['template'] ) ) {
die;
}
$tpl = stripslashes( $_GET['template'] );
$tpl = sanitize_text_field( $tpl );
$tpl = addslashes( $tpl );</pre>
$content = STM_LMS_Templates::load_lms_template(
$tpl,
array(
'args' => $args,
'query_result' => $query_result,
)
);
The code reveals that there is no file path sanitization in this function which again makes it possible to include arbitrary PHP files from the server through the 'template' parameter.
Disclosure Timeline
February 25, 2024 – We receive the submission of the Privilege Escalation vulnerability in MasterStudy LMS via the Wordfence Bug Bounty Program.
February 26, 2024 – We receive the submission of the Local File Inclusion via modal vulnerability in MasterStudy LMS via the Wordfence Bug Bounty Program.
February 28, 2024 – We validate the Local File Inclusion via modal vulnerability in MasterStudy LMS report and confirm the proof-of-concept exploit.
March 1, 2024 – We validate the Privilege Escalation vulnerability in MasterStudy LMS report and confirm the proof-of-concept exploit.
March 13, 2024 – We initiate contact with the plugin vendor asking that they confirm the inbox for handling the discussion.
March 13, 2024 – The vendor confirms the inbox for handling the discussion.
March 14, 2024 – We send over the full disclosure details. The vendor acknowledges the report and begins working on a fix.
March 20, 2024 – The fully patched version for the Local File Inclusion via modal vulnerability of the MasterStudy LMS plugin, 3.3.1, is released.
March 27, 2024 – The fully patched version for the Privilege Escalation vulnerability of the MasterStudy LMS plugin, 3.3.2, is released.
March 31, 2024 – We receive the submission of the Local File Inclusion via template vulnerability in MasterStudy LMS via the Wordfence Bug Bounty Program.
April 1, 2024 – We validate the Local File Inclusion via template vulnerability in MasterStudy LMS report and confirm the proof-of-concept exploit.
April 1, 2024 – We send over the full disclosure details. The vendor acknowledges the report and begins working on a fix.
April 4, 2024 – The fully patched version for the Local File Inclusion via template vulnerability of the MasterStudy LMS plugin, 3.3.4, is released.
Conclusion
In this blog post, we detailed a Privilege Escalation vulnerability affecting versions 3.3.1 and earlier of the MasterStudy LMS plugin. This vulnerability makes it possible for an unauthenticated attacker to grant themselves administrative privileges by updating user metadata during registration. The vulnerability has been fully addressed in version 3.3.2 of the plugin. We also detailed Local File Inclusion vulnerabilities affecting versions 3.3.3 and earlier of the MasterStudy LMS plugin. These vulnerabilities allow unauthenticated threat actors to include and execute PHP files on the server, allowing the execution of any PHP code in those files, which can be used for complete site compromise. The vulnerabilities have been fully addressed in version 3.3.4 of the plugin.
We encourage WordPress users to verify that their sites are updated to the latest patched version of MasterStudy LMS.
All Wordfence Premium, Wordfence Care, and Wordfence Response customers, as well as those using the free version of our plugin, are protected against any exploits targeting this vulnerability by the Wordfence firewall’s protection.
If you know someone who uses this plugin on their site, we recommend sharing this advisory with them to ensure their site remains secure, as these vulnerabilities pose a significant risk.
The post $937 Bounty Awarded for Privilege Escalation and Local File Inclusion Vulnerabilities Patched in MasterStudy LMS WordPress Plugin appeared first on Wordfence.