In this article, we’ll explore the most common malware types found in the wild and frequently analyzed in our sandbox, complete with examples.
What are the 7 most common types of malware?
Based on ANY.RUN sandbox analysis of 14,000 daily submissions, the most prevalent malware types you’re likely to encounter are:
<thead> <tr>
<th>
Type </th>
<th>
Short description </th>
<th>
Example </th>
</tr>
</thead><tbody> <tr>
<td>
Loader </td>
<td>
Acts as the initial infection vector, downloading and installing other malware components. </td>
<td>
<a href="https://any.run/malware-trends/smoke" rel="noreferrer" target="_blank">Smoke Loader</a> </td>
</tr>
<tr>
<td>
Stealer </td>
<td>
Harvests sensitive information such as credentials, credit card numbers, and other personal data. </td>
<td>
<a href="https://any.run/malware-trends/azorult" rel="noreferrer" target="_blank">Azorult</a> </td>
</tr>
<tr>
<td>
RAT </td>
<td>
Gives an attacker remote control of a compromised system. </td>
<td>
<a href="https://any.run/malware-trends/asyncrat" rel="noreferrer" target="_blank">AsyncRAT</a> </td>
</tr>
<tr>
<td>
Ransomware </td>
<td>
Encrypts the user's data and demands payment for the decryption key. </td>
<td>
<a href="https://any.run/malware-trends/lockbit" rel="noreferrer" target="_blank">LockBit</a> </td>
</tr>
<tr>
<td>
Trojan </td>
<td>
Disguises itself as legitimate software but performs malicious actions. </td>
<td>
<a href="https://any.run/malware-trends/emotet" rel="noreferrer" target="_blank">Emotet</a> </td>
</tr>
<tr>
<td>
Installer </td>
<td>
Installs additional malicious software onto the infected system. </td>
<td>
InstallCore </td>
</tr>
<tr>
<td>
Keylogger </td>
<td>
Records keystrokes to capture sensitive user inputs like passwords. </td>
<td>
KeyBase </td>
</tr>
</tbody></table>
Let’s explore each malware type in more detail:
1. Loader
Loader malware, often referred to as a “dropper” or “downloader,” is a type of malicious software designed to download and install other malware onto a compromised system. Unlike many other forms of malware, loaders typically do not carry out the main malicious activity themselves. Instead, their primary function is to establish a foothold in the system and then retrieve additional, often more destructive, malware from a remote server.
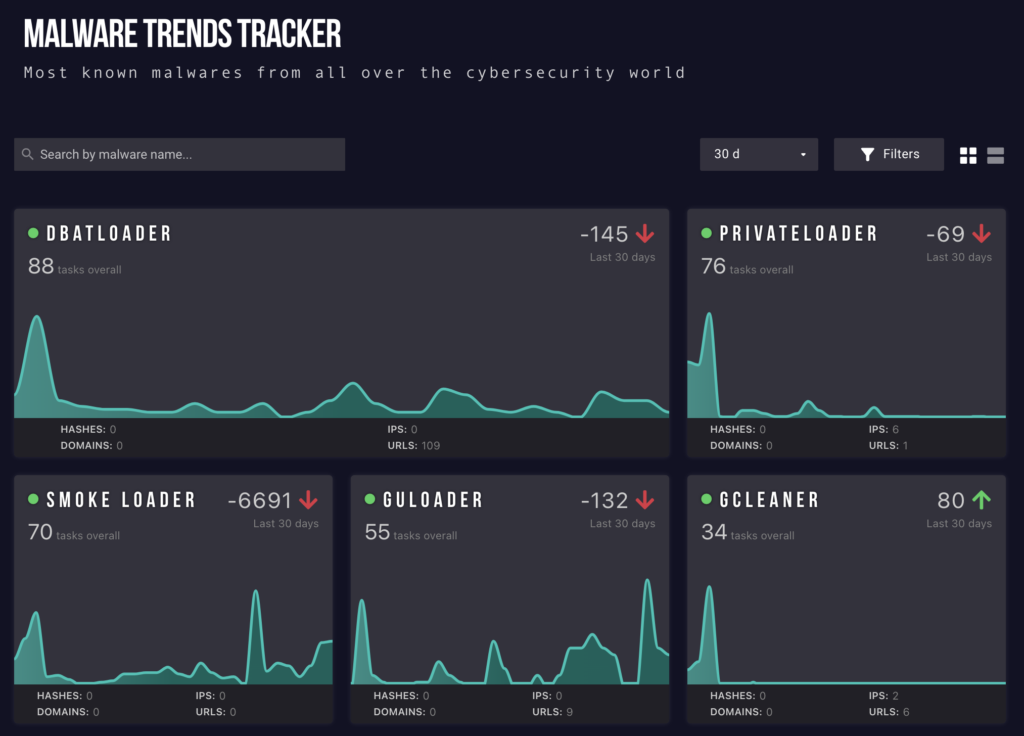 Most common loader malware in Malware trends tracker
Most common loader malware in Malware trends tracker As of this writing, the most frequently encountered loaders by ANY.RUN users are:
2. Stealer
Stealer malware is a type of malicious software designed to extract sensitive information from infected systems. This category of malware targets data like credentials, financial information, and personal data, which can include usernames, passwords, credit card details, and other private information.
Key characteristics of stealer malware include:
- Data extraction: Its primary function is to steal sensitive data from compromised systems.
- Stealth: It often operates quietly in the background to avoid detection.
- Transmission of stolen data: The stolen data is usually transmitted back to the attacker to a command-and-control server.
- Multiple data sources: Stealers can extract data from web browsers, file systems, FTP systems, and other software where sensitive data might be stored.
If you want to learn more about how stealers work, and, specifically, how they transmit data back over to the attacker, read our in-depth analysis of RisePro communication.
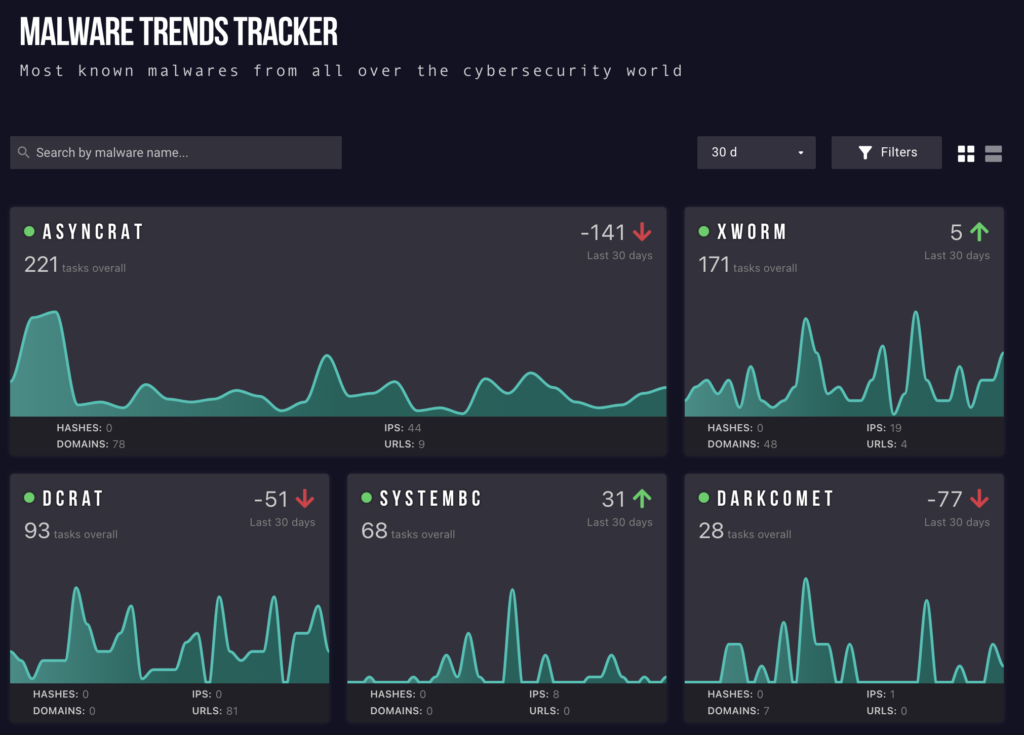 Most common RAT malware in Malware trends tracker
Most common RAT malware in Malware trends tracker
At the time of writing, the most commonly encountered Remote Access Trojans include:
3. Remote Access Trojan (RAT)
Remote Access Trojan (RAT) malware is a type of malicious software designed to provide an attacker with control over a victim’s system. RATs are particularly insidious because they enable unauthorized remote access, allowing attackers to perform various malicious activities discreetly. Key features and capabilities of RAT malware include:
- Remote control: RATs allow attackers to remotely control a system as if they have physical access to it.
- Covert operation: They often operate hidden in the background, avoiding detection by users and security software.
- Surveillance: Some RATs can capture keystrokes (keyloggers), take screenshots, or activate cameras and microphones for spying purposes.
- System manipulation: Attackers can modify system settings, install additional malware, or even delete or encrypt files.
RATs pose a significant threat to both individual and organizational cybersecurity. Their ability to give attackers extensive control over infected systems makes them a preferred tool for espionage, data theft, and sabotage.
Easily analyze RATs and other malware in ANY.RUN sandbox
Register for free4. Ransomware
Ransomware is a type of malicious software designed to block access to a computer system or data, typically by encrypting files, until a sum of money is paid. This form of malware targets individuals, small-medium businesses, corporations and government institutions. Here are its key characteristics:
- Data encryption: Ransomware encrypts the victim’s files, making them inaccessible without a decryption key.
- Ransom demand: Victims are typically demanded to pay a ransom, often in cryptocurrencies like Bitcoin, to receive the decryption key.
- Time limit: Many ransomware variants include a countdown timer, threatening to delete the decryption key or increase the ransom amount if not paid within the set time frame.
- Attack vectors: Common infection methods include phishing emails, exploiting vulnerabilities in software, or visiting compromised websites.
- Targeting: Ransomware can target both large and small organizations, with many variants specifically designed to infiltrate enterprise networks.
- Data exfiltration: Advanced ransomware may also steal data before encryption, threatening data leaks if the ransom isn’t paid, a tactic known as “double extortion.”
Some ways to protect against ransomware include regular data backups, up-to-date security software, and user awareness training to recognize and avoid common attack vectors.
5. Trojan
A trojan, or trojan horse, in the context of cybersecurity, is a type of malware that misleads users of its true intent. Named after the ancient Greek story of the deceptive wooden horse that led to the fall of the city of Troy, trojans typically masquerade as legitimate and harmless software to trick users into installing them.
Here are key aspects of trojan malware:
- Deception: Trojans present themselves as useful, interesting, or necessary software to entice users into downloading and installing them.
- Hidden malicious functionality: While appearing benign, trojans perform malicious actions once activated. These actions can vary widely, from stealing data to installing other malware.
- Delivery of other malware: trojans often act as a delivery vehicle for other malicious software, including ransomware and spyware.
There are many subcategories of trojans, each designed for specific malicious purposes: for example, banking trojans steal financial information, while backdoor trojans bypass security mechanisms to create a vulnerability in the system.
6. Installer
Installer malware is a type of malicious software that disguises itself as a legitimate installation program. In this sense, it is similar to a trojan. However, unlike trojans, which can pose as any type of software, this category specifically mimics installers.
Users are typically tricked into downloading and executing installers, thinking they’re getting a genuine application. Once executed, the malware can perform various actions, such as:
1) Stealing sensitive information
2) Installing additional malware
3) Providing remote access to the infected system.
This type of malware often exploits the trust users place in legitimate installers and can be distributed via phishing emails, malicious websites, or bundled with pirated software.
7. Keylogger
Keylogger malware is a program designed to covertly record the keystrokes made on a victim’s device. Here’s a breakdown of its characteristics:
- Functionality: Keyloggers capture every keystroke, including passwords, messages, and other sensitive data.
- Data Exfiltration: Recorded keystrokes are typically sent to an attacker-controlled server.
- Purpose: Used for espionage, identity theft, corporate sabotage, or gaining unauthorized access.
- Types: Software-based keyloggers are most common, but hardware variants exist, often as USB devices or keyboard attachments.
- Distribution: Spread via phishing, malicious downloads, or as part of a multi-component attack.
Malware analysis with ANY.RUN
ANY.RUN‘s interactive malware sandbox is a top choice for SOC, DFIR, and malware analysis teams. It simplifies the analysis of all malware types mentioned in this article by displaying behavior, artifacts, and IOCs in real time. Users can interact with a secure virtual machine directly through their browser.
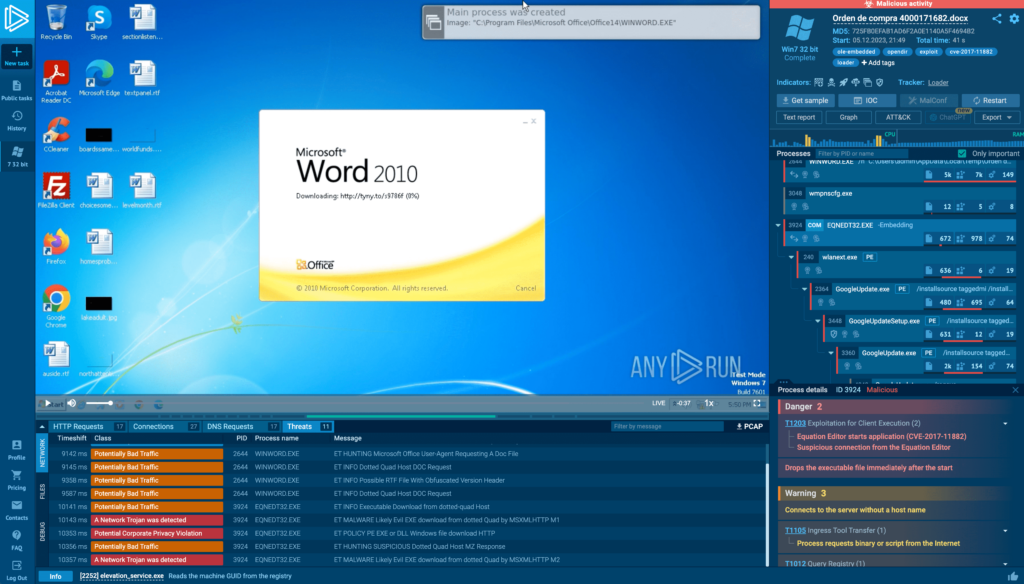 Example of a loader analysis task in ANY.RUN
Example of a loader analysis task in ANY.RUN Interested in exploring ANY.RUN further? Request a demo for a hands-on experience and enjoy 14 days of free access to our most feature-rich plan.
The post 7 most common malware types appeared first on ANY.RUN's Cybersecurity Blog.
Article Link: 7 most common malware types - ANY.RUN's Cybersecurity Blog