2022 Activities Summary of SectorJ groups (ENG)
Summary
In 2022, hacking activities by a total of 32 SectorJ subgroups were identified. Unlike other government supported hacking groups, these groups mainly carry out hacking activities with the aim of securing financial resources. They steal online information with monetary value, or directly hacks specific companies and organizations to disseminate ransomware in the internal network, or steal critical industry secret and demand for ransom in return.
An analysis of hacking activities by SectorJ groups in 2022 showed that there was a total of 32 active subgroups in the year, with activities by SectorJ09 group being the most prominent out of all the subgroups.
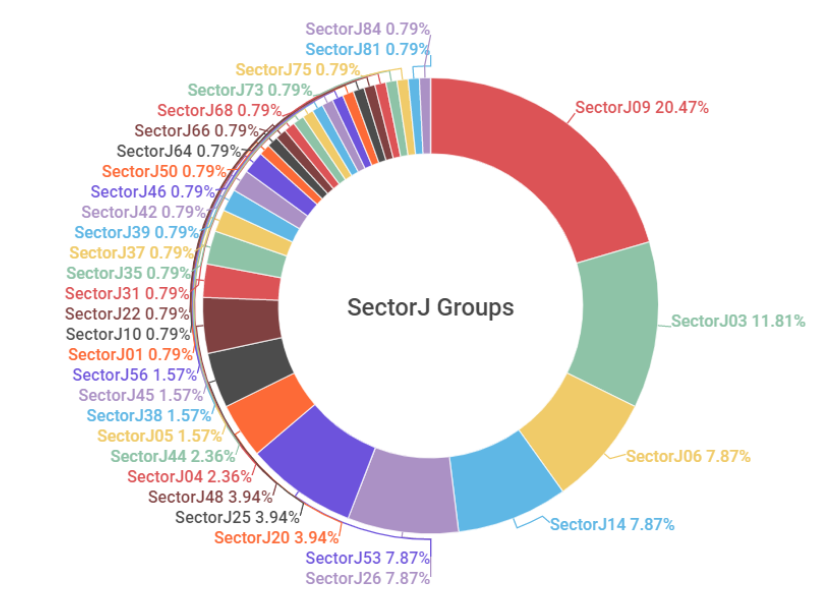
[Figure 1. Activity level of SectorJ subgroups in 2022]
The main targets of SectorJ groups were identified to be the commercial industry, including online marketplace and eCommerce. In the case of online marketplace and eCommerce, attacks included insertion of skimming scripts into vulnerable homepages to steal or sell data such as personal information, credit card details, address from the users, with the aim of securing financial resources.
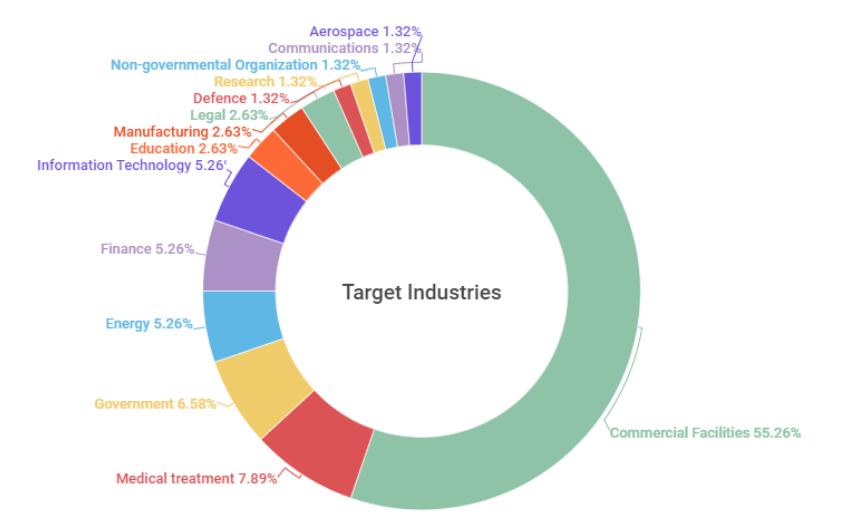
[Figure 2: Distribution of targeted industries in 2022]
The following figure is a map showing the countries that were targeted by SectorJ Groups in 2022, with a darker shade of red indicating a higher frequency of attacks. From the figure, it could be deduced that the group carried out the greatest number of hacking activities on the United States, located in the North American continent, as well as China, located in East Asia.
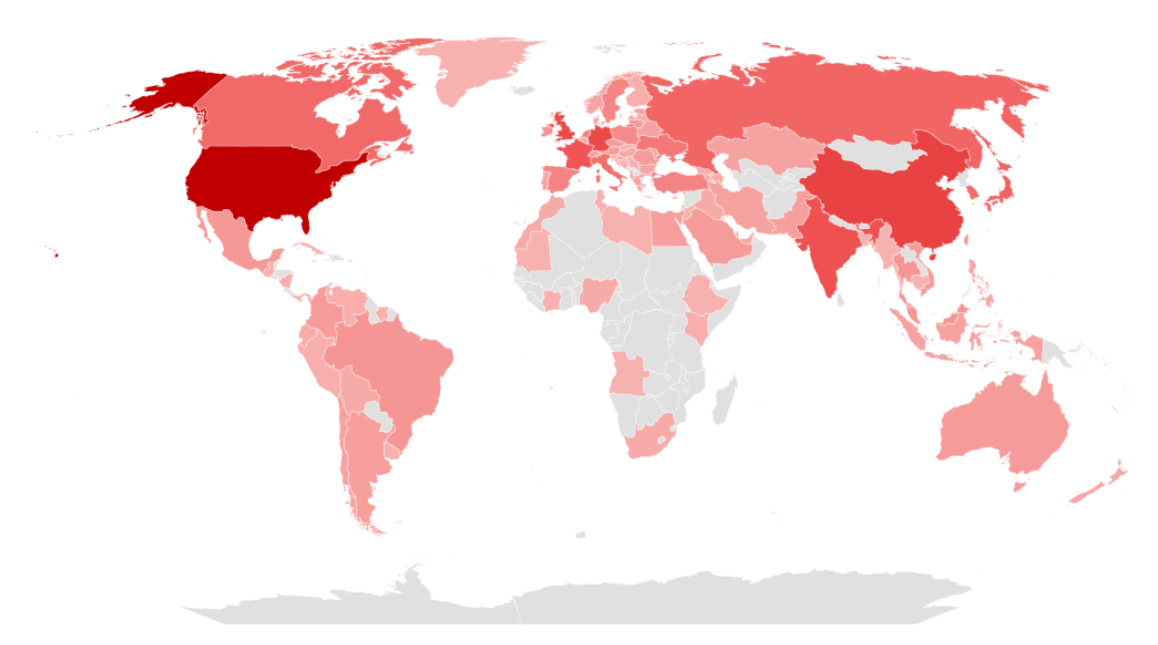
[Figure 3: Map of mainly targeted countries by SectorJ in 2022]
2022 Activities of SectorJ Groups
The following is a timeline of the hacking activities carried out by SectorJ groups as identified in 2022 and the detailed information of monthly activities of the group.
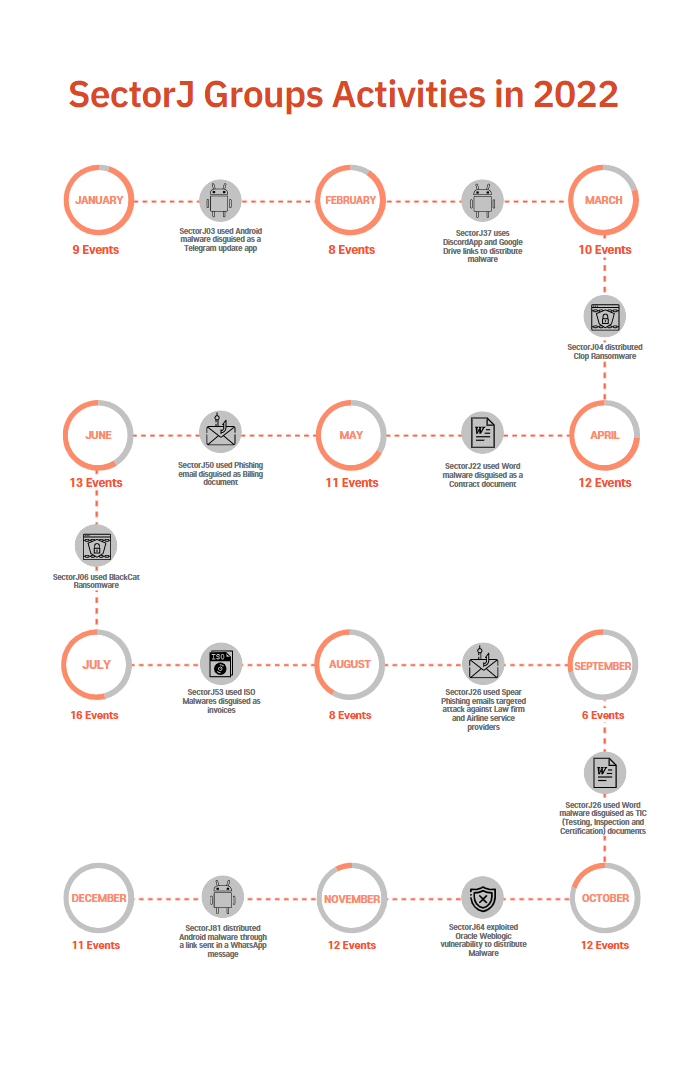
[Figure 4: Main activities and events by SectorJ groups in 2022]
JANUARY
In January 2022, activities by a total of 6 hacking groups were identified, and the groups were SectorJ03, SectorJ06, SectorJ09, SectorJ10, SectorJ20 and SectorJ26.
SectorJ03 group was found to be active in Spain, Palestine, China, Israel, and Jordan. The group used malware targeted on Android platforms to steal information of targets such as SMS information, photos and phone call recordings.
SectorJ06 group was found to be active in the United States and Israel. The group used the Diavol ransomware which encrypts data using RSA encryption key, and adds a “.lock64” file extension to the encrypted files.
SectorJ09 group continued to use their hacking tactics of inserting an obfuscated skimming script into the payment page of a website to collect information such as username, address, email, phone number and credit card details. In this activity, a JavaScript malware with a format identical to those that had been found previously was identified.
SectorJ10 group was found to be active in the United States. The group targeted on financial companies in the United States to disseminate a new type of ransomware called “White Rabbit”.
SectorJ20 group was found to be active in Germany. The group used shortcut files disguised as passports. When the shortcut file is executed, it downloads and executes a PDF file to seem legitimate, then downloads and executes an additional malware that carries out malicious activities such as information collection.
SectorJ26 group was found to be active in China, Bulgaria, Russia, United States, Saudi Arabia, India, Azerbaijan, Germany, Japan, Spain, Norway, Britain, Turkey, Iran, Egypt, Canada, Georgia, Italy, Pakistan, Mexico, Vietnam, Lithuania, Libya, Sweden, Malaysia, Poland, Netherlands, Colombia, France, Hong Kong, Ireland, Singapore, Myanmar, Qatar, and Moldova. The group used macro-inserted MS Word document malwares, which generates a hta format script for execution, to install a backdoor malware that compromises system authorizations.
FEBRUARY
In February 2022, activities by a total of 6 hacking groups were identified, and the groups were SectorJ03, SectorJ09, SectorJ14, SectorJ25 and SectorJ37.
SectorJ03 group was found to be active in Palestine, China, Israel, the United States, Saudi Arabia, and India. The group used malware targeted on Android platforms to steal information of targets such as SMS information, photos and phone call recordings.
SectorJ09 group continued to use their hacking tactics of inserting an obfuscated skimming script into the payment page of a website to collect information such as username, address, email, phone number and credit card details. In this activity, a JavaScript malware with a format identical to those that had been found previously was identified.
SectorJ14 group was found to be active in Japan. The group had been targeting multilanguage multi-platforms since 2018, and their hacking activities carry the sole aim of securing financial resources.
SectorJ25 group was found to be active in Vietnam, Russia, South Korea, Italy, the United States, Hong Kong, China, Ireland, and Lithuania. The group targeted on Linux based systems to carry out Crypto jacking attacks, and the malware installed through a downloader script conducts activities such as cryptocurrency mining, scanning, and information collection.
SectorJ37 group was found to be active in Germany, the United States, Thailand, England, Singapore, France, Japan, Sweden, Lithuania, Russia, Greece, South Korea, Turkey, India, Saudi Arabia, Hong Kong, and Vietnam. The group continued to use flight and travel related topics to carry out cyber threat activities on airlines, transport, manufacturing and armory industries. In this activity, a phishing email containing a link to a Google Drive was disseminated, which installs a RAT malware in the system for malicious activities like system information collection, commands and control.
MARCH
In March 2022, activities by a total of 8 hacking groups were identified, and the groups were SectorJ03, SectorJ04, SectorJ06, SectorJ09, SectorJ14, SectorJ26, SectorJ42 and SectorJ44.
SectorJ03 group was found to be active in Palestine. The group modified the icon of the malware to a PDF icon to disguise it as a legitimate PDF document, and showed a PDF document about an opening ceremony schedule by impersonating the Palestine National Council.
SectorJ04 group was found to be active in the United States. The group used the tactics of delivering a remote access malware or a ransomware to the targets through phishing emails, with the aim of stealing company information and securing financial resources.
SectorJ06 group was found to be active in the United States, France, and Italy. The group attached a malicious macro-inserted MS Word or Excel format malwares to phishing emails for dissemination, and have continued to use the tactics of installing a ransomware in the system for the purpose of securing financial resources.
SectorJ09 group continued to use their hacking tactics of inserting an obfuscated skimming script into the payment page of a website to collect information such as username, address, email, phone number and credit card details. In addition, the group used a malware that collects credentials and cryptocurrency related data by advertising it as a DDoS tool for attacking Russian corporates.
SectorJ14 group was found to be active in Malaysia and Japan. The group had been targeting multilanguage multi-platforms since 2018, and their hacking activities carry the sole aim of securing financial resources.
SectorJ26 group was found to be active in Argentina, Ukraine, USA, Korea, UK, Australia, Philippines, Switzerland, China, Canada, Israel, Germany, Ireland, Netherlands, India, Suriname, Iran, Italy, France, and Sweden. The group attached a Backdoor malware with system authorization compromising function to a phishing email disguised as a business proposal, and the group was deduced to have been seizing system authorizations for ransomware infection purposes, in order to secure financial resources.
SectorJ42 group was found to be active in Singapore, Estonia, Hong Kong, South Korea, England, Indonesia, Japan, Israel, Taiwan, and China. The group used an ELF file format malware to accomplish their financial goals in UNIX and LINUX environments. In this activity, the ELF malware was used to withdraw unauthorized cash from ATM(Automated Teller Machine) devices.
SectorJ44 group was found to be active in China, Ukraine, Singapore, South Korea, India, Iran, and the United States. The group was deduced to have developed another ransomware and have been managing it.
APRIL
In April 2022, activities by a total of 9 hacking groups were identified, and the groups were SectorJ04, SectorJ09, SectorJ14, SectorJ22, SectorJ26, SectorJ35, SectorJ45, SectorJ46 and SectorJ48.
SectorJ04 group was found to be active in Israel, Italy, South Korea, Kazakhstan, France, India, Britain, Cuba, Australia, Japan, Czech Republic, the United States, Ireland, China and Saudi Arabia. The group used the tactics of delivering a remote access malware or ransomware through phishing emails to the targets, with the aim of stealing company information and securing financial resources. In this activity, an ISO format malware was attached to a phishing email disguised as a payment related message.
SectorJ09 group was found to be active in Turkey, Moldova, Palestine, Romania, and Denmark. The group continued to use their hacking tactics of inserting an obfuscated skimming script into the payment page of a website to collect information such as username, address, email, phone number and credit card details. In this activity, a JavaScript malware with a format identical to those that had been found previously was identified. In addition, attacks on corporates using ransomwares were discovered.
SectorJ14 group was found to be active in the United States, England, South Korea, Japan, Germany, and France. SectorJ14 group was found to be active in Malaysia and Japan. The group had been targeting multilanguage multi-platforms since 2018, and their hacking activities carry the sole aim of securing financial resources. In this activity, the group distributed an Android malware disguised as an app by the post office. The malware carried out the function of stealing information from Android-based smartphones.
SectorJ22 group was found to be active in Russia, the United States, and Hong Kong. The group sent out delicately structured phishing emails to Russian companies, which contained a Backdoor malware that downloaded and executed a malicious JavaScript. In this activity, phishing emails disguised under contents related to contracts were sent out.
SectorJ26 group was found to be active in Ukraine, Ireland, New Zealand, Spain, China, Israel, the United States, Japan, Malaysia, Canada, Hong Kong, England, and South Korea. The group attached a MS Word format malware to a phishing email on habitat exploration.
SectorJ35 group was found to be active in Austria and Ireland. The group compromised system authorizations and attempted data leakage for financial purposes, without the usage of ransomwares. In this activity, open-source tools such as Metasploit and Impacket were used for data leakage and lateral movement.
SectorJ45 group was found to be active in Japan, the United States, Egypt, England, Singapore, Italy, China, the Philippines, Taiwan, Hong Kong, and Russia. The group distributed malware disguised as popular programs such as Chrome and Telegram, to build a large-scale botnet infrastructure. In this activity, the group used malware disguised as WhatsApp and Adobe related programs.
SectorJ46 group was found to be active in Argentina, Ukraine, Japan, Belarus, Bulgaria, Chile, the United States, Vietnam, Lithuania, Kenya, Panama, Poland, Turkey, Germany, France, Croatia, Denmark, Israel, and Russia. The group distributed malware through phishing emails and vulnerable webpages, and stole finance related data such as cryptocurrency and credit cards, for the aim of securing financial resources. In this activity, the group distributed a phishing email impersonating a government institution, and attached a password-encrypted compressed file to the mail.
SectorJ48 group was found to be active in India, Russia, Australia, Canada, Ukraine, England, the United States, Singapore, Germany, and China. The group disguised themselves as a steel manufacturing company to attach a macro-inserted MS Excel document to emails and distributed them. The group also attempted to attack a specific government institution by exploiting a vulnerability of an email server related software.
MAY
In May 2022, activities by a total of 8 hacking groups were identified, and the groups were SectorJ03, SectorJ09, SectorJ14, SectorJ20, SectorJ38, SectorJ48, SectorJ50 and SectorJ53.
SectorJ03 group was found to be active in Palestine and Israel. The group targeted on Android platforms to use malware disguised as chat or dating apps to steal information such as SMS information, photos, phone call recordings of the targets.
SectorJ09 group was found to be active in Turkey, Moldova, Palestine, Romania, and Denmark. The group continued to use their hacking tactics of inserting an obfuscated skimming script into the payment page of a website to collect information such as username, address, email, phone number and credit card details. In this activity, a JavaScript malware with a format identical to those that had been found previously was identified.
SectorJ14 group was found to be active in South Korea, Japan, and Denmark. The group used malware disguised as Android apps related to the Japanese post office and media to collect information such as SMS information, photos, phone call recordings from the targets.
SectorJ20 group was found to be active in Malta and the United States. The group used images exploiting the steganography technique, in which a loader malware was used to execute the backdoor malware hidden in the image.
SectorJ38 group was found to be active in England, the United States, Australia, and Pakistan. The group exploited the fact that virtual machine utilities were vulnerable to DLL side loading to load a malicious DLL within the virtual machine utility, and executed Cobalt Strike in the final stage to take over system controls.
SectorJ48 group was found to be active in Finland, China, Ukraine, India, Canada, the United States, and Argentina. The group sent out spear phishing emails about security measures to distribute a PE (Portable Executable) format backdoor malware developed using Metasploit.
SectorJ50 group was found to be active in Ukraine, the United States, Hungary, Malaysia, South Korea, and Japan. The group sent out a payment related spear phishing email to distributed backdoor malwares developed using .NET.
SectorJ53 group was found to be active in Netherlands, Russia, France, Czech Republic, South Africa, England, India, the United States, Malaysia, Luxembourg, South Korea, Canada, and China. The group sent out spear phishing emails on invoices to distribute a downloader malware that allows the download and execution of pentesting tools such as Cobalt Strike and Sliver.
JUNE
In June 2022, activities by a total of 10 hacking groups were identified, and the groups were SectorJ03, SectorJ06, SectorJ09, SectorJ20, SectorJ25, SectorJ38, SectorJ44, SectorJ48, SectorJ53 and SectorJ56.
SecotrJ03 group was found to be active in Palestine. The group used a MS Word format malware containing a malicious macro, and disguised it as a Palestine-related document to prompt the targets to execute the file.
SectorJ06 group was found to be active in China, Israel, Singapore, France, and the United States. The group targeted vulnerable MS Exchange servers, or used stolen credentials to penetrate into the internal system. Various open-source tools were utilized in the process.
SectorJ09 group continued to use their hacking tactics of inserting an obfuscated skimming script into the payment page of a website to collect information such as username, address, email, phone number and credit card details. In this activity, a JavaScript malware with a format identical to those that had been found previously was identified.
SectorJ20 group was found to be active in Russia, Finland, Belarus, Romania, Japan, Estonia, France, Italy, Hong Kong, Nigeria, Bangladesh, Indonesia, Albania, Belgium, Armenia, Israel, England, India, Malta, Colombia, Canada, Ukraine, the United States, the Netherlands, Switzerland, Philippines, Poland, Spain, and Germany. The group used images exploiting the steganography technique, and a loader malware was used to execute the backdoor malware hidden in the image.
SectorJ25 group was found to be active in China, Hong Kong, the United States, Taiwan, England, Russia, and South Korea. The group targeted on servers with the 2375 port open, which allows for remote access from Docker Engine. Afterwards, a crypto-mining software was installed in the system for a Crypto jacking attack.
SectorJ38 group was found to be active in Germany, Ukraine, the United States, and China. The group exploited a vulnerability to carry out ransomware attacks on unpatched targets.
SectorJ44 group was found to be active in Peru. The group used a new ransomware that shares a similar code to the REvil ransomware, which they had been using previously, and encrypted the network resources and ransom note strings using the RC4 algorithm, like their previous ransomware.
SectorJ48 group was found to be active in the United States, Australia, Ireland, France, England, Russia, and Ukraine. The group disguised a compressed file as a fine from the National Tax Service, and used Cobalt Strike, a pentesting tool in the final stage.
SectorJ53 group was found to be active in China, New Zealand, Italy, Poland, Spain, Turkey, Sweden, Estonia, Ireland, India, Russia, the United States, Canada, France, Hong Kong, Slovenia, England, Thailand, Norway, Germany, Taiwan, Singapore, Japan, Kazakhstan, Egypt, Maldives, and South Korea. The group sent out spear phishing emails related to invoices, to distribute a downloader malware that allows for download and execution of pentesting tools such as Cobalt Strike and Sliver.
SectorJ56 group was found to be active in Japan, Singapore, Ireland, Romania, France, Italy, England, Malaysia, Argentina, India, Canada, Serbia, Poland, Estonia, Germany, Sweden, the United States, and Israel. The group led their targets to execute malware through thread hijacked emails that were disguised to have been sent from acquaintances, and the malware executed in the final stage has the function of stealing financial information and credentials from the internal system.
JULY
In July 2022, activities by a total of 4 hacking groups were identified, and the groups were SectorJ06, SectorJ09, SectorJ14 and SectorJ53.
SectorJ06 group was found to be active in Canada, Saudi Arabia, Japan, Spain, Singapore, Brazil, Egypt, France, Mexico, Qatar, United States, India, Czech Republic, Ecuador, Vietnam, Chile, Sweden, China, Italy, Indonesia, Thailand, Croatia, Hong Kong, Malaysia, Germany, Russia, Norway, Cambodia, and Ukraine. The group used a malware disguised as a customs declaration, which was compressed as an ISO file and had a Ukrainian filename. In the final stage, a pentesting tool, Cobalt Strike, was used.
SectorJ09 group continued to use their hacking tactics of inserting an obfuscated skimming script into the payment page of a website to collect information such as username, address, email, phone number and credit card details. In this activity, a JavaScript malware with a format identical to those that had been found previously was identified.
SectorJ14 group was found to be active in Japan, Poland, South Korea, England, China, the United States, France, and Germany. The group used Android malwares disguised as apps from a Japanese transport company and a Japanese AI chat application, and attempted to steal information from Android based smartphones.
SectorJ53 group was found to be active in Australia, Thailand, China, Kazakhstan, Singapore, Netherlands, Hong Kong, Turkey, Russia, India, the United States, Germany, France, Israel, Norway, Ukraine, Belarus, South Africa, New Zealand, Poland, England, Slovenia, Italy, Switzerland, Canada, South Korea, Nicaragua, Taiwan, Slovakia, Austria, Brazil, Bosnia and Herzegovina, Egypt, Chile, Japan, Colombia, Nigeria, Spain, Cyprus, Greece, Albania, Azerbaijan, Estonia, Malaysia, Morocco, Sweden, Iran, Bulgaria, Mauritania, Georgia, and Indonesia. The group sent out emails leading their targets to click on a Google storage link with a malicious ISO file uploaded, and attempted to steal financial information including online banking account credentials, in the final stage.
AUGUST
In August 2022, activities by a total of 6 hacking groups were identified, and the groups were SectorJ01, SectorJ04, SectorJ14, SectorJ20, SectorJ26 and SectorJ31.
SectorJ01 group was found to be active in the United States. The group used an XLL (Microsoft Excel extension for add-ins) format malware disguised as an invoice related file to collect various information such as system general information and list of processes, and sent them to the C2 server.
SecotrJ04 group was found to be active in Austria and Germany. The group targeted on medical and health related companies to send out phishing emails attached with an IMG format compressed file containing a shortcut (LNK) file disguised as a resume.
SectorJ14 group was found to be active in France and the United States. The group targeted on multiple countries to use an Android malware with the aim of collecting information from Android smartphones.
SectorJ20 group was found to be active in Malaysia, the United States, China, Netherlands, Lithuania, Bulgaria, and Nigeria. The group delivered a spear phishing email containing a OneDrive link to the targets, leading them to download a compressed ISO file containing a shortcut (LNK) format malware.
SectorJ26 group was found to be active in the United States, Germany, and France. The group targeted on law firms and airline companies to deliver a spear phishing email attached with a MS Word format malware disguised as Invoice, resume, or legal documentations.
SectorJ31 group was found to be active in Germany, Hungary and Netherlands. The group acquired personal Google account credentials of the targeted organization, then used authentication of an exposed VPN server to gain access to the internal system of the organization.
SEPTEMBER
In September 2022, activities by a total of 4 hacking groups were identified, and the groups were SectorJ09, SectorJ25, SectorJ26 and SectorJ48.
SectorJ09 group continued to use their hacking tactics of inserting an obfuscated skimming script into the payment page of a website to collect information such as username, address, email, phone number and credit card details. In this activity, a JavaScript malware with a format identical to those that had been found previously was identified.
SectorJ25 group was found to be active in the United States and England. The group targeted on LINUX based systems to use Shell format malware, attempting to carry out additional commands and Crypto jacking attacks.
SectorJ26 group was found to be active in the United States, Canada, Germany, and Luxembourg. The group used an MS Word format malware disguised as a TIC (Testing, Inspection and Certification) document, and attempted to seize system authorization and information by installing Cobalt Strike.
SectorJ48 group was found to be active in Turkey, France, England, the United States, Italy, Russia, Vietnam, Thailand, and Japan. The group targeted on various industries including accommodation, NGO (Non-governmental Organization), and government institutions, and attempted to seize system authorization and information by installing Cobalt Strike.
OCTOBER
In October 2022, activities by a total of 9 hacking groups were identified, and the groups were SectorJ03, SectorJ06, SectorJ09, SectorJ25, SectorJ45, SectorJ53, SectorJ64, SectorJ66 and SectorJ68.
SectorJ03 group was found to be active in Palestine, India, and Iraq. The group attempted to steal information such as SMS information, photos, and phone call recordings of victims through using a malware targeted on Android platforms.
SectorJ06 group was found to be active in Spain, Portugal, Greece, Russia, Ukraine, Germany, Turkey, Denmark, England, the United States, Armenia, Brazil, Czech Republic, Mexico, Uruguay, Peru, India, Israel, United Arab Emirates, Saudi Arabia, Lithuania, Iraq, Angola, Moldova, and South Korea. The group exploited the DLL side-loading vulnerability of OneDrive to use Crypto jackers that carry out cryptocurrency mining activities.
SectorJ09 group continued to use their hacking tactics of inserting an obfuscated skimming script into the payment page of a website to collect information such as username, address, email, phone number and credit card details. In this activity, a JavaScript malware with a format identical to those that had been found previously was identified.
SectorJ25 group was found to be active in China, the United States, Russia, and Singapore. The group targeted on cloud and container environments to use Crypto jackers that carries out cryptocurrency mining activities.
SectorJ45 group was found to be active in Netherlands, Sweden, South Korea, Germany, France, Norway, Thailand, Japan, Singapore, and Spain. The group targeted on users of the Internet Explorer service that is no longer supported to carry out malvertising techniques that exploits advertising services. In the final stage, they collected information from the system and mined for cryptocurrencies.
SectorJ53 group was found to be active in Canada, Italy, United Arab Emirates, the United States, Iran, China, Germany, Turkey, India, England, Israel, France, South Africa, Hong Kong, South Korea, Russia, Gibraltar, Denmark, Portugal, Ethiopia, Cote d’Ivoire, Kazakhstan, Australia, Sweden, Taiwan, Japan, Argentina, Poland, Estonia, Netherlands, Romania, Georgia, Hungary, Bulgaria, Thailand, Belgium, Iraq, Qatar, Mexico, Greece, and Spain. The group used a malware disguised as an invoice, and used a downloader malware to set the base for downloading and executing pentesting tools such as Cobalt Strike and Sliver.
SectorJ64 group was found to be active in China, Sweden and England. The group targeted on vulnerable servers to carry out Crypto mining activities.
SectorJ66 group was found to be active in Vietnam, Spain, Portugal, Russia, Germany, Canada, Czech Republic, Japan, Chile, Turkey, Ukraine, Brazil, Poland, India, Italy, Hong Kong, Romania, Colombia, England, Venezuela, France, Tunisia, China, and the United States. The group uses the BPH (Bulletproof hosting) services that provides network infrastructure for carrying out malicious activities without restriction.
SectorJ68 group was found to be selling malwares with various functions such as Crypto mining and information collection as a Maas (Malware-as-a-Service), for financial purposes.
NOVEMBER
In November 2022, activities by a total of 10 hacking groups were identified, and the groups were SectorJ03, SectorJ05, SectorJ06, SectorJ25, SectorJ26, SectorJ39, SectorJ44, SectorJ73, SectorJ75 and SectorJ81.
SectorJ03 group was found to be active in Palestine and Qatar. The group used a bait MS Word document disguised under the theme of Hamas, and attempted to steal information from the target’s system.
SectorJ05 group was found to be active in India, Netherlands, Switzerland, Ireland, the United States, and Romania. The group used malware disguised as a Google update file, which carries out functions such as collecting system information from the target, or downloading and executing additional malware depending on the attacker’s commands.
SectorJ06 group was found to be active in Brazil and the United States. The group targeted on servers with known vulnerabilities that were unpatched to carry out ransomware attacks with the aim of securing financial resources.
SectorJ25 group was found to be active in China and Israel. The group targeted on cloud and container environments to use Crypto jackers that carries out Crypto mining activities.
SectorJ26 group was found to be active in South Korea, India, Canada, the United States, Germany, Lithuania, Mexico, Thailand, Columbia, Kenya, Italy, Sweden, Hong Kong, Singapore, Netherlands, Pakistan, and England. The group used malware disguised as tax invoice PDF documents, and uses a backdoor malware to take over system controls in the final stage.
SectorJ39 group was found to be active in Ukraine, China, Spain, Canada, United Arab Emirates, England, Palestine, and Czech Republic. The group used malware disguised as PDF Reader update files, and uses a backdoor malware to take over system controls in the final stage.
SectorJ44 group was found to be active in South Korea. The group used the Surtr ransomware with the aim of securing financial resources, which encrypts files in the system and generates a ransom note to deliver a contact point for discussing about financial issues.
SectorJ73 group was found to be active in the United States, Denmark, and Cyprus. The group targeted on education industry to use Zeppelin ransomware with the aim of securing financial resources, together with a backdoor malware for attempting data collection and leakage.
SectorJ75 group was found to be active in Sweden, Bolivia, and the United States. The group used malware disguised as Network Scanning Software, and used the Somnia ransomware in the final stage.
SectorJ81 group was found to be active in Indonesia and China. The group used phishing sites that attracted users with prize winnings in order to lead them into clicking the links. When the target clicked on the link, they were either redirected to advertisement websites that generated advertisement profits for the group, or was disseminated with Android malwares.
DECEMBER
In December 2022, activities by a total of 6 hacking groups were identified, and the groups were SectorJ03, SectorJ05, SectorJ06, SectorJ09, SectorJ56 and SectorJ84.
SectorJ03 group was found to be active in India, Ecuador, and Germany. The group used an Android malware disguised as an app for streaming World Cup livestreams, which carried out various malicious activities that collected information from the target’s smartphone.
SectorJ05 group was found to be active in the United States, Mexico, Pakistan, and Brazil. The group used a downloader malware that collects information from the target’s system and downloads and executes additional malware depending on the command received, and encrypted the system using the Clop ransomware in the final stage with the aim of securing financial resources.
SectorJ06 group was found to be active in India, Colombia, China, the United States, Brazil, Germany, Russia, Italy, France, Latvia, Japan, Chile, Bolivia, Romania, Iran, Moldova, Hong Kong, Belarus, Belgium, England, Turkey, Pakistan, Vietnam, New Zealand, Poland, Ukraine, and the Philippines. The group targeted on energy industries to use the BlackCat ransomware, for data encryption and stealing purposes.
SectorJ09 group inserted an obfuscated skimming script in websites to collect information such as username, address, email, phone number and credit card details from the payment page.
SectorJ56 group was found to be active in Italy, the United States, France, Canada, England, Germany, India, China, and Spain. The group used malware disguised as tax invoice PDF documents, and uses a backdoor malware to take over system controls in the final stage.
SectorJ84 group was found to be active in Russia, Hungary, Brazil, Denmark, the United States, Singapore, England, China, Spain, Mexico, Pakistan, Netherlands, the Philippines, Poland, France, Turkey, Italy, Ukraine, Lithuania, Malaysia, Greece, Azerbaijan, Slovenia, Switzerland, Sweden, and Saudi Arabia. The group used YouTube videos and phishing websites to disseminate malware disguised as cracked versions of paid software, and attempted to steal information such as credentials across various browsers and cryptocurrency wallet related data.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact [email protected].
Article Link: 2022 Activities Summary of SectorJ groups (ENG) – Red Alert