Zero-Day Exploits for Windows, Atlassian, Mastodon Data Leak, DDoS Attack on FC Bayern Munich
The SOCRadar Dark Web Team has recently uncovered several alarming posts on hacker forums and Telegram channels, revealing the sale of zero-day vulnerabilities and unauthorized access, alongside claims of a disruptive DDoS attack.
Notable incidents include a zero-day exploit for Windows 8.1, 10, and 11, API access to a British bank, a zero-day exploit for Atlassian’s Jira, and a leaked database from Mastodon.
Additionally, a threat actor has claimed responsibility for a DDoS attack on FC Bayern Munich, targeting the football club’s website and causing significant disruptions.
Receive a Free Dark Web Report for Your Organization:
An Alleged 0-Day Vulnerability of Windows 8.1, 10 and 11 is on Sale
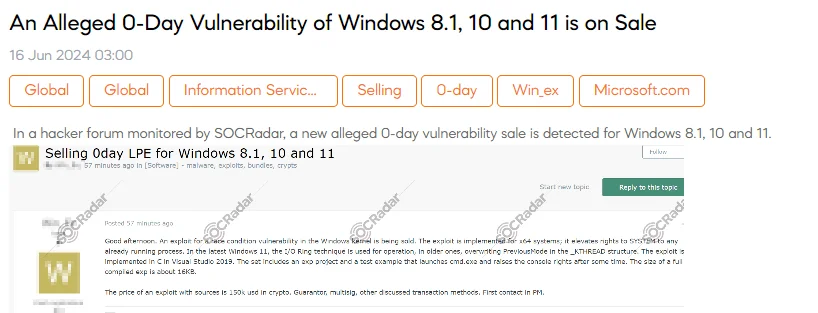
The SOCRadar Dark Web Team detected a post in a hacker forum that a threat actor claims to have a new zero-day vulnerability for sale, targeting Windows 8.1, 10, and 11.
The threat actor describes the exploit as targeting a race condition vulnerability in the Windows kernel. The exploit, implemented for x64 systems, elevates privileges to SYSTEM for any already running process. In the latest Windows 11, it uses the I/O Ring technique, while in older versions, it overwrites PreviousMode in the _KTHREAD structure. The exploit is written in C using Visual Studio 2019 and includes a project and a test example that launches cmd.exe and elevates console rights after some time. The compiled exploit size is approximately 16KB.
The price for the exploit with source code is $150,000 in cryptocurrency.
Unauthorized API Access Sale is Detected for a British Bank
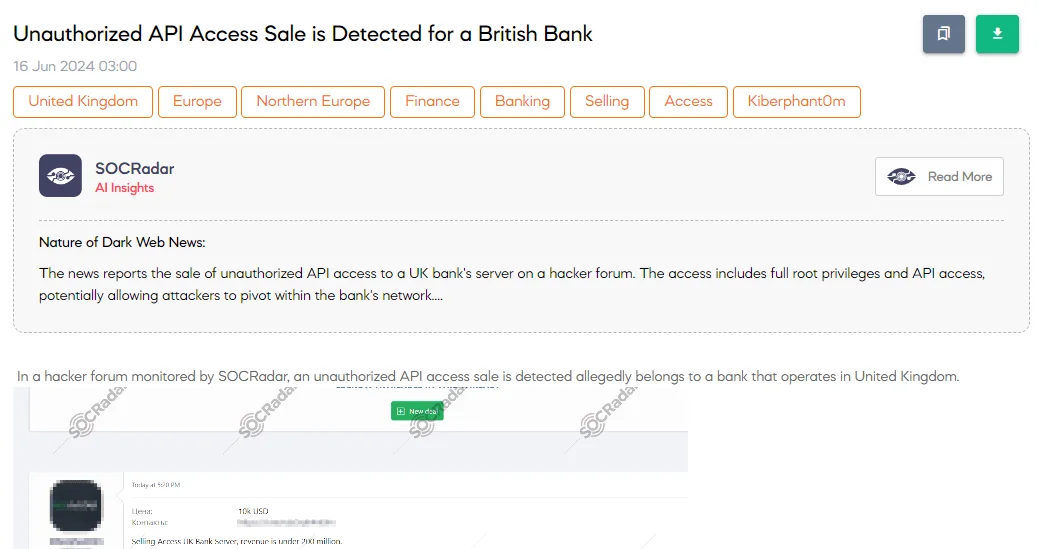
The SOCRadar Dark Web Team detected a post in a hacker forum that a threat actor is allegedly selling API access to a bank operating in the United Kingdom. The threat actor claims to have full root privileges, API access, and more, with the server connected to a local LAN for potential pivot techniques. The asking price is $10,000.
Alleged New 0-Day Exploit for Atlassian is on Sale
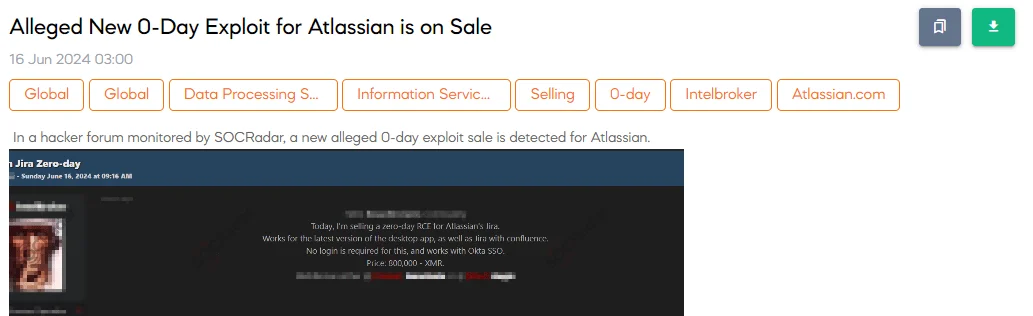
The SOCRadar Dark Web Team detected a post in a hacker forum that a threat actor claims to be selling a new 0-day exploit for Atlassian. The notorious threat actor, IntelBroker, is behind this alleged sale.
According to IntelBroker, the exploit is a zero-day Remote Code Execution (RCE) for Atlassian’s Jira. It works on the latest version of the desktop app, as well as Jira with Confluence, and does not require login credentials. Additionally, it is compatible with Okta SSO. The asking price for this exploit is $800,000 in cryptocurrency.
The Alleged Database of Mastodon is on Sale
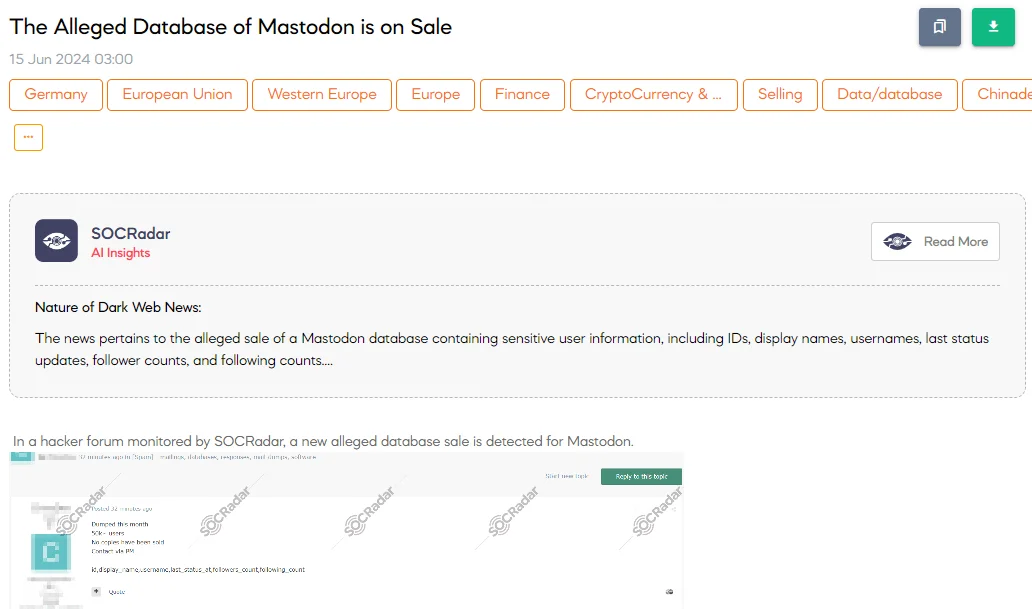
The SOCRadar Dark Web Team uncovered a post in a hacker forum that a threat actor claims to have an alleged database of Mastodon for sale. Mastodon is an open-source, decentralized social media platform that allows users to create and interact within independent communities, providing an alternative to traditional social networks. The threat actor claims the database, dumped in June 2024, contains information on approximately 50,000 users.
The data includes user IDs, display names, usernames, last status dates, follower counts, and following counts. The threat actor stated that no copies have been sold yet and interested buyers should contact them via private message.
CyberArmy Conducted DDoS Attack on FC Bayern Munich
The SOCRadar Dark Web Team detected a post in a Telegram channel where a threat actor claims to have conducted a DDoS attack on FC Bayern Munich. The threat actor announced their participation in a campaign targeting Germany, stating that they targeted the famous football club, FC Bayern Munich.
According to the threat actor, the attack caused significant disruptions to the club’s website, making it experience serious issues despite its resilience. They also provided a link to a report as evidence of the attack.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.
