This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports does not include. This article covers the monitoring results for the period of January to March 2024. The scan trends observed with TSUBAME sensors in Japan are presented in graphs here.
Impacts in Japan from Observations in FY2023
JPCERT/CC analyzes the data collected by TSUBAME on a daily basis. In this article, I will focus on incidents in Japan based on observations in FY2023. Of the packets sent to sensors installed in Japan and abroad, the largest number of packets were addressed to 23/TCP, and of the packets addressed to 23/TCP, approximately 70% were Mirai-type packets, both for packets sent from overseas IP addresses to sensors installed in Japan and for packets sent from Japan to sensors installed overseas. In addition, when information was collected using web browsers and SHODAN for IP addresses in Japan to identify devices, surveillance cameras and DVRs made by overseas vendors were the most common products identified, followed by NASs and routers made by overseas vendors. There were changes in the nature of the attacks, including the use of vulnerabilities newly discovered in 2023, as well as packet combinations to port numbers other than 23/TCP. Although the number is small, there were cases where DVRs made by domestic vendors or products under development by vendors were affected by attacks. Based on the results of observations and investigations by JPCERT/CC, we provided information on the vulnerabilities used in the attacks to the relevant product developers and discussed countermeasures with them. We also visited the site to see the equipment and logs and discussed countermeasures. In addition, we investigated information related to the source IP addresses using WHOIS and provided observation data to domestic companies through communities such as CSIRTs. As a result, we have confirmed that the problem has been resolved. When installing new devices in an organization, it is recommended to check what kind of rules are in place for access from the Internet. After installation, it is also recommended to perform a port scan to check whether any unnecessary ports are open, or to use SHODAN or other tools for checking. Assuming that there will be such attack information on domestic products and suspicious packet sources in FY2024, TSUBAME plans to continue to provide observation data and to help solve problems.
Comparison of the observation trends in Japan and overseas
Figure 1 is a monthly comparison of the average number of packets received in Japan and overseas. Overseas sensors received more packets than those in Japan.
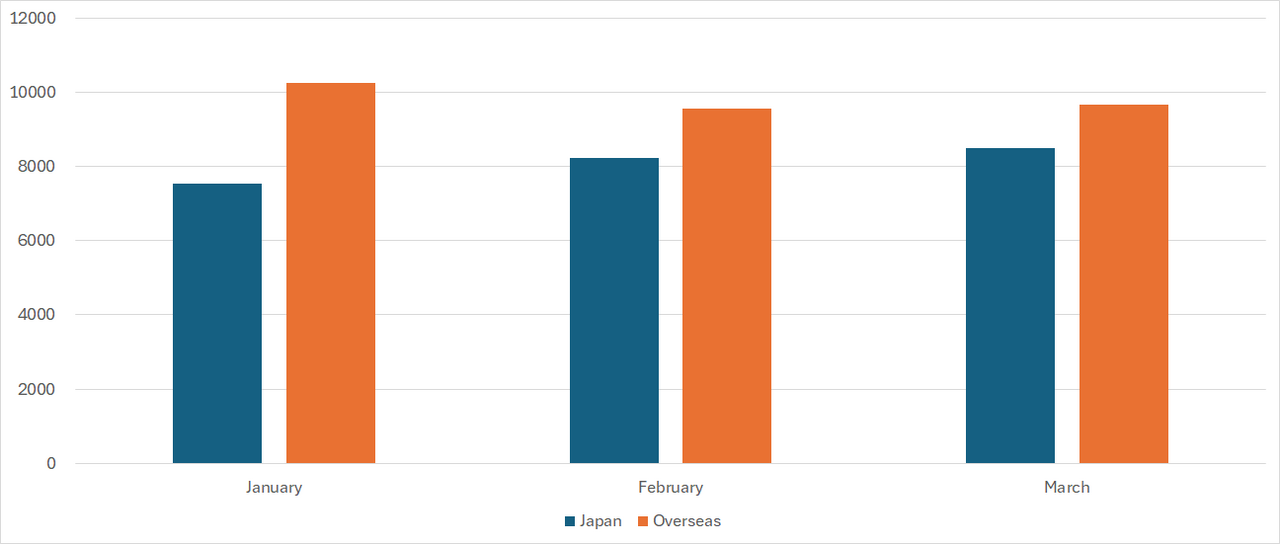
|
| Figure 1: Monthly comparison of the average number of packets received in Japan and overseas |
Comparison of monitoring trends by sensor
A global IP address is assigned to each TSUBAME sensor. Table 1 shows the top 10 ports of each sensor which received packets the most. Although the order is different in each sensor, almost all the sensors observed the packets for 23/TCP, 6379/TCP, 22/TCP, 8080/TCP, 80/TCP and ICMP. This suggests that these protocols are being scanned in a wide range of networks.
Table 1: Comparison of top 10 packets by domestic and overseas sensors
| #1 | #2 | #3 | #4 | #5 | #6 | #7 | #8 | #9 | #10 | |
| Sensor in Japan #1 | 23/TCP | 6379/TCP | 22/TCP | 80/TCP | 3389/TCP | 8080/TCP | ICMP | 443/TCP | 8728/TCP | 445/TCP |
| Sensor in Japan #2 | 23/TCP | ICMP | 80/TCP | 443/TCP | 6379/TCP | 8080/TCP | 22/TCP | 8088/TCP | 8443/TCP | 445/TCP |
| Sensor in Japan #3 | 23/TCP | 6379/TCP | 22/TCP | ICMP | 80/TCP | 3389/TCP | 8080/TCP | 8728/TCP | 443/TCP | 37215/TCP |
| Sensor overseas #1 | 445/TCP | 23/TCP | 443/TCP | 80/TCP | ICMP | 37215/TCP | 6379/TCP | 22/TCP | 3389/TCP | 8080/TCP |
| Sensor overseas #2 | 23/TCP | 445/TCP | 80/TCP | 3389/TCP | 6379/TCP | 22/TCP | 8080/TCP | 443/TCP | ICMP | 8728/TCP |
| Sensor overseas #3 | ICMP | 23/TCP | 80/TCP | 443/TCP | 6379/TCP | 8080/TCP | 8088/TCP | 22/TCP | 8443/TCP | 3389/TCP |
In closing
Monitoring at multiple locations enables us to determine if certain changes are occurring only in a particular network. Although we have not published any special alerts as an extra issue or other information this quarter, it is important to pay attention to scanners. We will continue to publish blog articles as the Internet Threat Monitoring Quarterly Report becomes available every quarter. We will also publish an extra issue when we observe any unusual change. Your feedback on this series is much appreciated. Please use the below comment form to let us know which topic you would like us to introduce or discuss further. Thank you for reading.
Keisuke Shikano
(Translated by Takumi Nakano)
Article Link: TSUBAME Report Overflow (Jan-Mar 2024) - JPCERT/CC Eyes | JPCERT Coordination Center official Blog