Top 10 Takeaways from Verizon DBIR 2024 Report
Verizon’s 17th annual Data Breach Investigations Report (DBIR) for 2024 offers an in-depth look at the latest trends in data breaches and cyber security incidents. Analyzing data from over 30,458 incidents and 10,626 confirmed breaches between November 2022 and October 2023, Verizon DBIR 2024 provides crucial insights into the evolving threat landscape.
Here are the top ten detailed takeaways from the 2024 Verizon DBIR:
1. Refinement in Social Engineering Techniques
Social engineering remains a primary attack vector, and phishing and pretexting via email contribute to social engineering attacks in approximately 73% of all breaches.
This year, there was a notable increase in the sophistication of social engineering attacks, with phishing attempts using AI-generated voices and deepfake videos rising. As these deceptive tactics evolve, the role of GenAI technology in facilitating such threats becomes more significant.
Expanding on GenAI’s applications in malware, phishing, and identifying vulnerabilities, its impact on successful attacks is among top cybersecurity discussions. The report highlights that, despite previous social engineering patterns suggesting succesful attacks may not require such tactics (or sophistication), GenAI’s role in creation of deepfakes raises concerns about heightened risks in tricking victims.
SOCRadar’s Digital Risk Protection suite combats this challenge, offering VIP Protection and Brand Protection services.
The VIP Protection feature ensures the continuous monitoring of exposed personal data and credentials for key individuals, which could lead to impersonation and potential security breaches. Moreover, with the Brand Protection service, you can track down replicated sites, applications, and accounts for your brand.
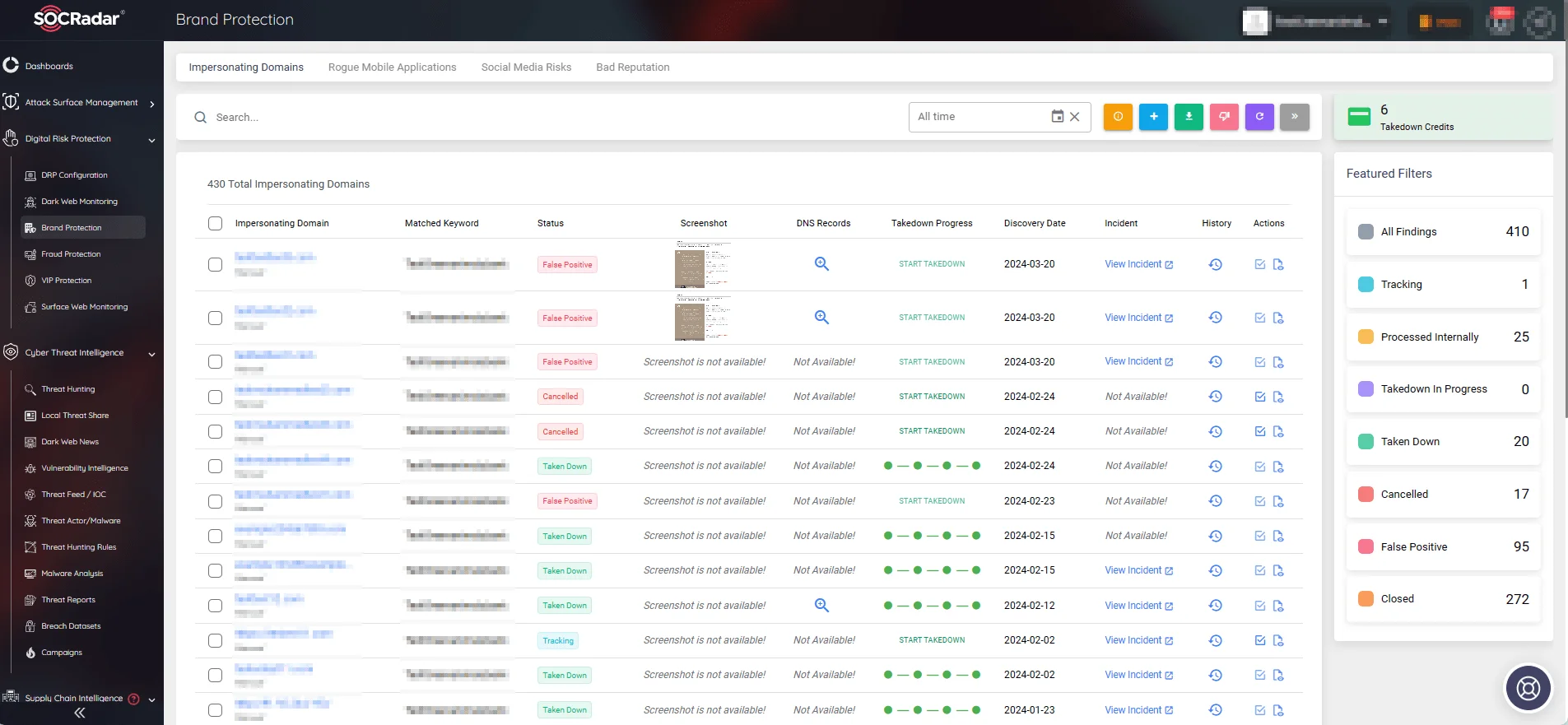
SOCRadar’s Brand Protection module
Also, our on-demand takedown services provide seasoned analysts to handle high-risk situations, ensuring your brand reputation and financial health are safeguarded.
2. Ransomware Dominates Cyber Threats
Ransomware attacks make up the majority of System Intrusion breaches, accounting for 70% of them, while the System Intrusion itself leads the pack of all breaches with 36%. The data shows that according to the FBI’s Internet Crime Complaint Center (IC3) ransomware complaint data while the median loss from ransomware attacks is $46,000.
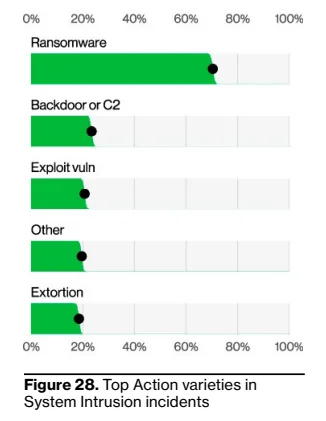
System Intrusion breaches percentages
Among the ransomware groups that have undoubtedly dominated the past year are LockBit, Cl0p, and BlackCat (ALPHV) groups. You can visit the Dark Web Profile articles for these threat actors on SOCRadar blog for deep insights.
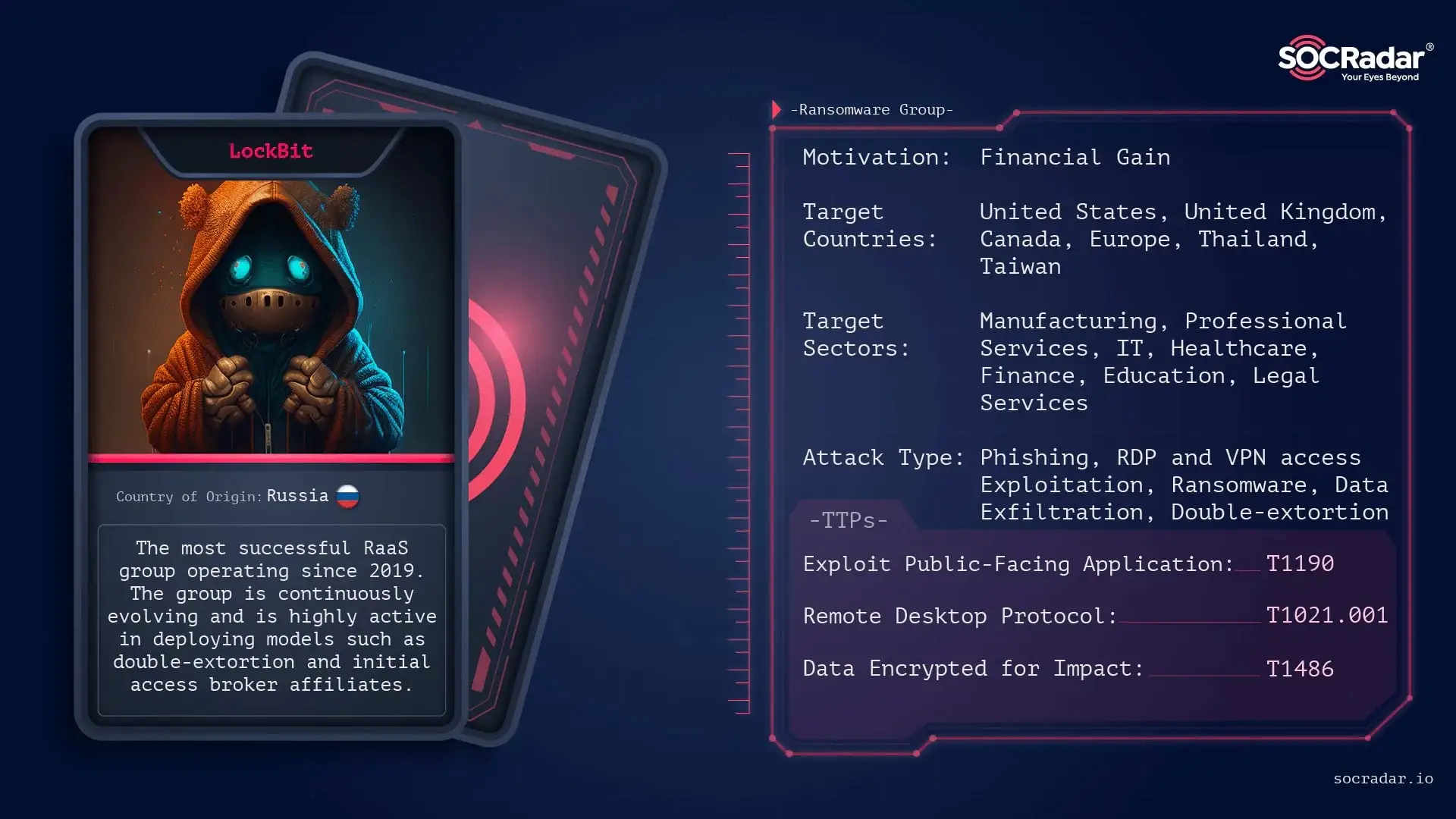
SOCRadar threat actor card of LockBit Ransomware
Read our whitepaper, “A 100M+ USD Negotiator’s Guide to Surviving Ransomware,” for a comprehensive guide on how businesses can continue to operate successfully even when they are the target of ransomware operations.
3. Stolen Credentials Pervade
Approximately 77% of web application breaches involved stolen credentials, reinforcing their status as a preferred method for cybercriminals. This statistic underscores the ongoing vulnerability of organizations to credential stuffing and brute force attacks.
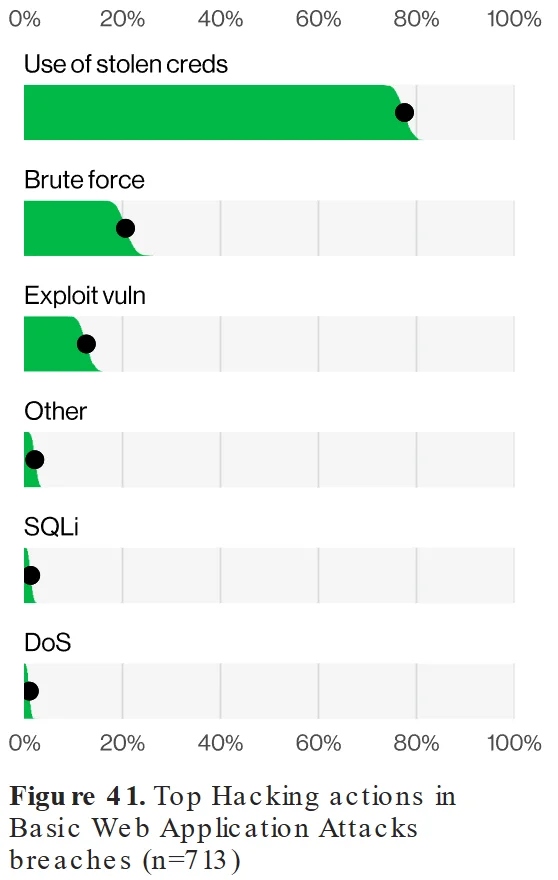
Top hacking methods (Verizon DBIR 2024)
The report also lists the top stealer malware, as indicated by their postings, as shown in the chart below:
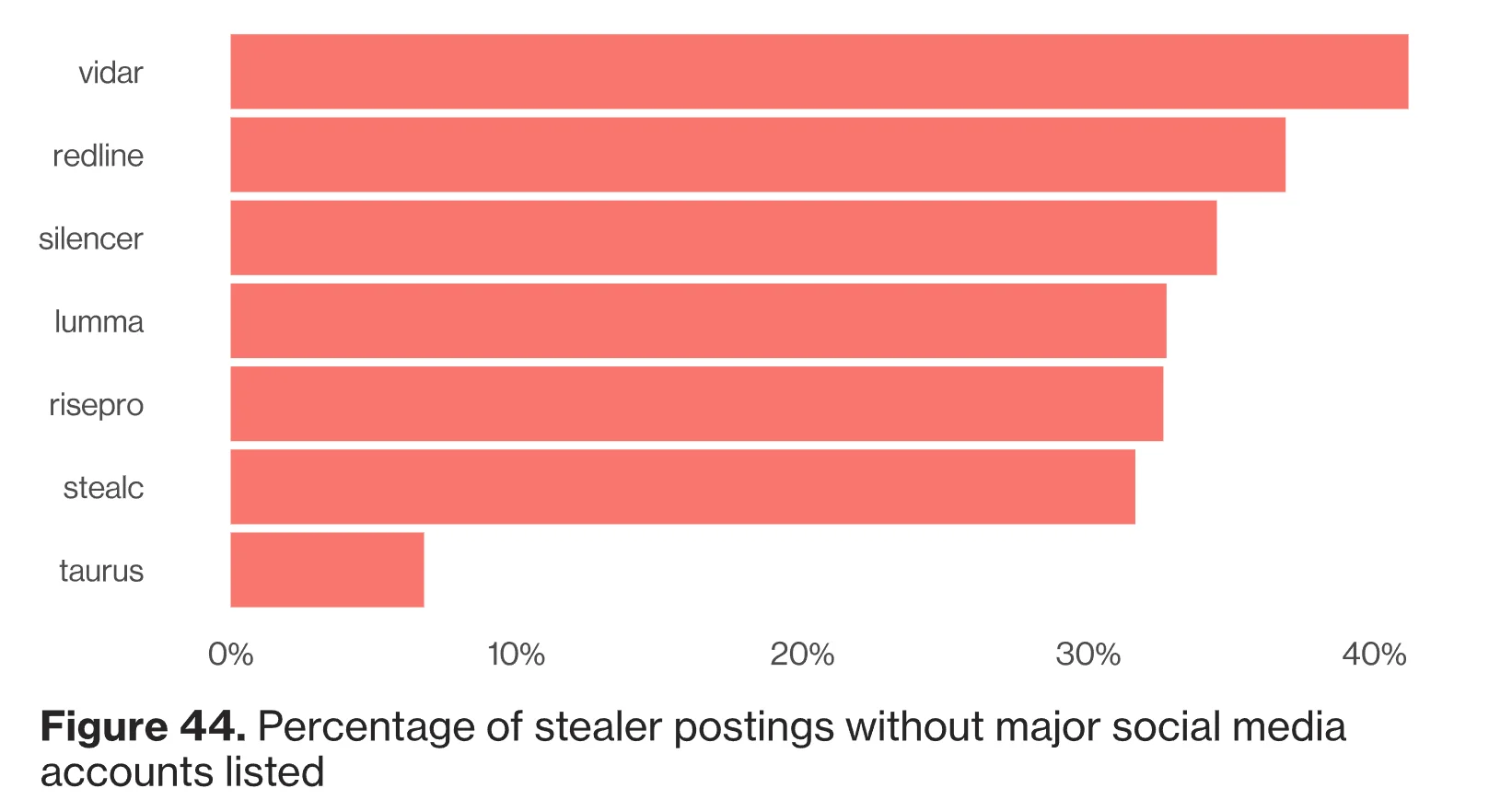
Top stealer malware from postings (Verizon DBIR 2024)
Threat actors frequently obtain user credentials from stealer logs that are traded on cybercriminal forums; these logs serve vast amounts of sensitive data that have been stolen by stealer malware from various domains, and include financial information, credentials, and personal information.
We have examined stealer logs in previous blog posts to identify trends that have impacted users of ChatGPT and top email providers, among others.
You can also read our “The Anatomy of Stealer Logs” article to gain a better understanding of their threat, and the “Snapshot of 70 Million Stealer Logs” whitepaper for comprehensive insights.
4. Extortion and Exploitation
Persistent gaps in patching and evolving cyber threats reshape the cybersecurity landscape.
Extortion tactics in ransomware attacks were frequently accompanied by vulnerability exploitation, constituting 10% of breaches. This tandem underscores the significant impact on systems like MOVEit and similar vulnerabilities.
As vulnerabilities linger unaddressed, particularly in cloud environments, the risk of exploitation escalates. This dynamic is further complicated by the surge in ransomware and extortion tactics, which leverage these vulnerabilities.
The need for proactive security measures is underscored, emphasizing the importance of timely patching and comprehensive defense strategies to mitigate evolving risks.
5. Breaches Resulting from Insider Threats
Insider-related breaches, involving data theft for personal gain and collaboration with external actors, remain a significant concern, though fraudulent transactions have decreased from last year.
Collusion, once at 7%, has dropped to less than 1%, signaling a return to normalcy. This decrease is critical, as collusion between employees and outsiders exacerbates data breach risks.
Implementing a zero-trust approach can strengthen security against insider threats by continuously verifying user identities and enforcing strict access controls, regardless of whether users are inside or outside the network perimeter.
6. Supply Chain Compromises Intensify:
Attacks exploiting supply chain vulnerabilities are at 15%, illustrating the interconnected nature of security risks. Attackers often targeted smaller, less secure businesses as entry points to larger enterprises.
With insights on over 50 million companies across numerous industries and nations, SOCRadar’s Supply Chain Intelligence offers a highly advanced solution, giving you clear visibility into your entire supply chain and facilitating well-informed decision-making.
Strategic decisions are backed by comprehensive data through the module’s Analytics Dashboard, which makes it simple to monitor third-party companies and analyze global trends in-depth.
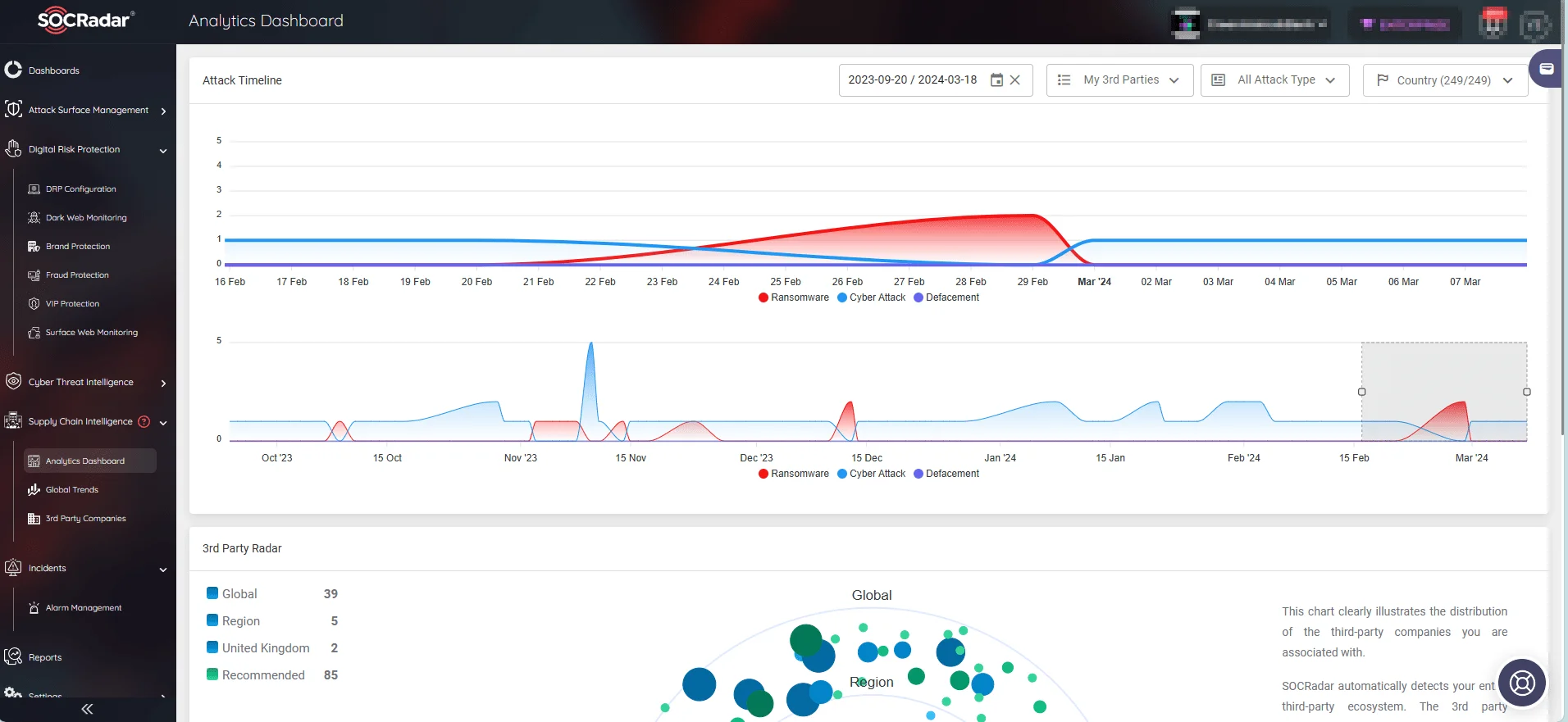
SOCRadar Supply Chain Intelligence module
Furthermore, by making use of the SOCRadar platform’s Vulnerability Intelligence feature, you can obtain comprehensive information about newly discovered vulnerabilities, including those that arise through your supply chain, and achieve better patch management.
7. IoT Devices as Breach Gateways:
Breaches involving IoT devices have seen a significant increase, often resulting from loss or theft, in addition to vulnerabilities due to weak security protocols.
The report reveals a startling rise in confirmed data breaches caused by lost or stolen IoT assets, climbing from 8% last year to an alarming 91% this year.
As vital as physical protection of these assets may be, digital protection is equally essential. Organizations can enhance the security of their assets with SOCRadar’s Attack Surface Management (ASM) module. By continuously monitoring digital assets and delivering timely alerts about vulnerabilities and security issues, ASM empowers organizations to proactively safeguard their IoT devices and infrastructure.
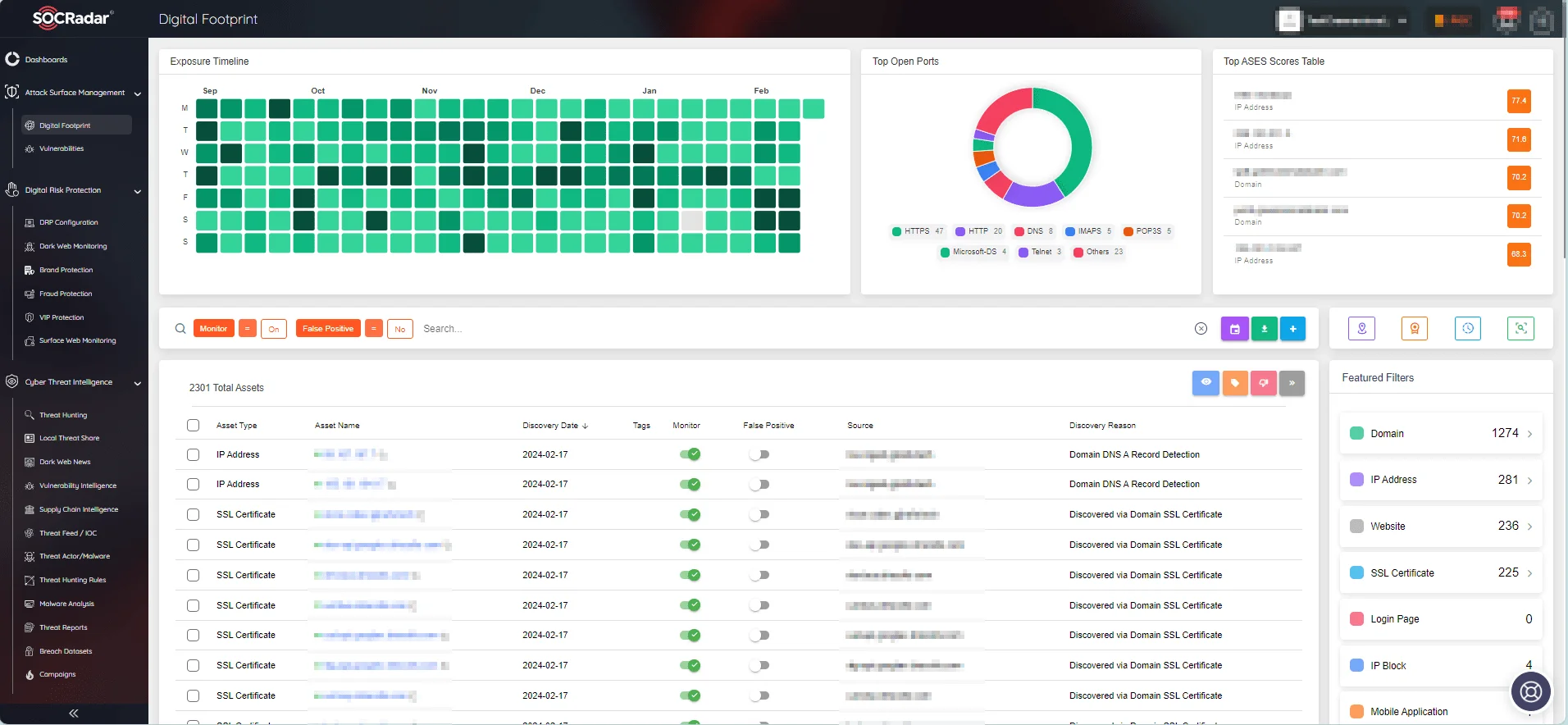
SOCRadar Attack Surface Management module, Digital Footprint
8. Financial Motives Drive Attacks:
Financial motives are propelling cyberattacks, with ransomware and extortion tactics gaining prominence alongside credential theft. Ransomware, accompanied by extortion, constitutes a substantial portion of breaches, highlighting the profitability of these actions.
Vulnerability exploitation has doubled, significantly impacting intrusion methods, while pretexting supersedes phishing in social engineering, notably in Business Email Compromise (BEC) attacks.
Incidents in the past year were dominated by ransomware (accounting for 70% of intrusion cases), notably targeting vulnerabilities, like in the MOVEit incident.
This high percentage highlights the ongoing importance of protecting financial data to deter cybercriminal activity.
For deeper insights into threats faced by the finance sector, explore our Financial Industry and Cryptocurrency & NFT Threat Landscape reports.
9. Severe Impact of DDoS Attacks:
DDoS attacks were the most common incident pattern, accounting for over 50% of all incidents that were analyzed. This growth is likely attributed to the increased availability of DDoS-for-hire services and the exploitation of more powerful botnets.
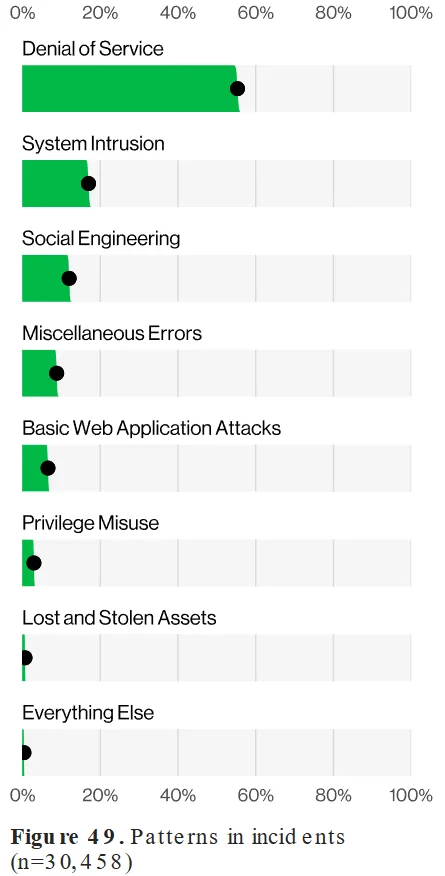
Attack patterns in all analyzed incidents (Verizon DBIR 2024)
Enhance your organization’s resistance to Denial-of-Service (DoS) threats with the aid of SOCRadar Labs’ DoS Resilience module. Assess the ability of your domain or subnet to endure DoS assaults.
SOCRadar Labs, DoS Resilience
10. Sector-Specific Security Challenges:
Each sector faces unique challenges, with the healthcare sector sees a resurgence in insider breaches, with personal data becoming the preferred target in breaches over medical data. Insider threats, especially privilege misuse, and error patterns like misdelivery, dominate this sector’s landscape.
Similarly, in the retail sector, threat actors have changed their focus from payment card data to credentials. This shift is evident in the drop of payment card breaches from 37% to 25%. Denial-of-Service (DoS) attacks continue to disrupt retail operations; notably, “Magecart” actors remain a threat, skilled at injecting malicious code into e-commerce sites.
Confirmed data breaches by industry and attack types are depicted in the following table, showcasing the threats encountered in other sectors:
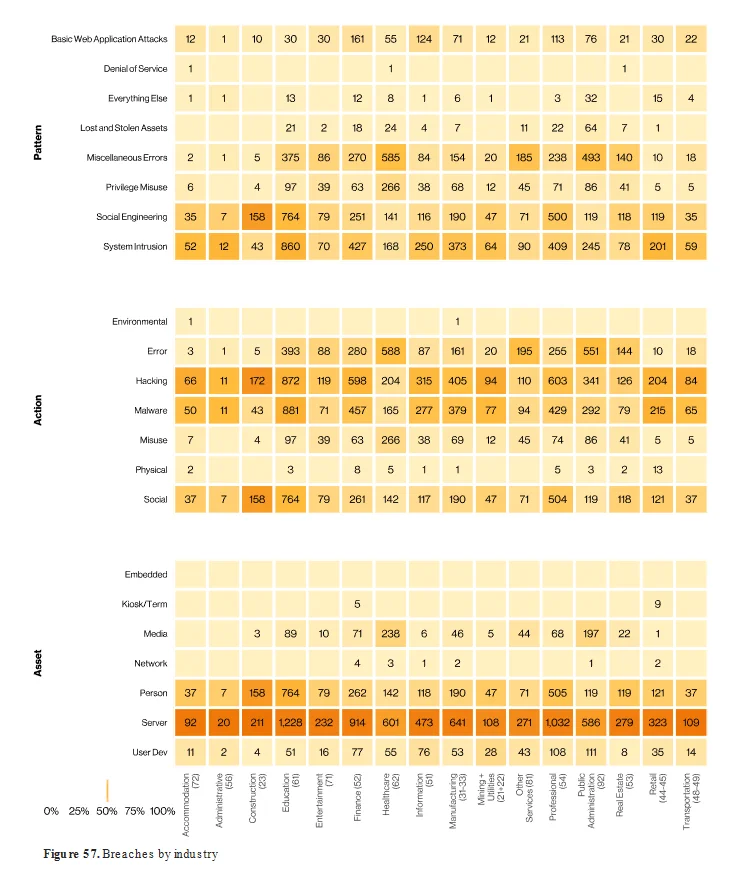
All breaches by industry and other filters (Verizon DBIR 2024)
SOCRadar periodically releases reports on various industries, including aviation, energy, manufacturing, healthcare, and more. You can access these reports on the Industry Reports page of our website.
Industry reports for the latest trends and key statistics are freely available on SOCRadar Labs’ Industry Threat Landscape Report page. These reports include information about the prevalence of specific cyber threats aimed at an industry, as well as information on ransomware groups targeting the sector and the top target countries.
Industry Threat Landscape Report on SOCRadar Labs
Conclusion
Verizon DBIR 2024 reveals significant trends that demand attention from cybersecurity professionals. As cyber threats evolve in sophistication and scale, organizations must adopt a proactive and informed approach to cybersecurity. Implementing strong security measures, continuous monitoring, and employee training are essential steps in protecting sensitive information and preventing data breaches.
Article Link: Top 10 Takeaways from Verizon DBIR 2024 Report - SOCRadar® Cyber Intelligence Inc.
