Summary:
This is Part 3 of Natto Thoughts’ “Ransom-War.” The series argues that Russian ransomware actors are not solely financially motivated; rather, whether they like it or not, they are immersed in a geopolitical context and mindset of confrontation with the “collective West”; in at least some cases the targeting and timing of their attacks align with Russian strategic interests, suggesting some degree of state inspiration by or even coordination.
Part 1 introduced the concept of hybrid ransomware: how ransomware attacks serve both financial and political motives and may play a role in Russia's ongoing "hybrid warfare" against the West. In part 2a we looked at how Russian cybercriminals are willing to act as warriors for the Russian state against its enemies, particularly the United States. Part 2b showed that Russian cybercriminals are still vulnerable to state repression in Russia’s highly controlled dictatorship, and they face tension between profit-making and their duty to the Russian motherland.
The present section looks at the words and actions of Russian government-linked entities. They offer clues to evolving Russian attitudes on taking advantage of Russian criminal ransomware as part of a perceived ongoing hybrid war against the West.
Former President Dmitry Medvedev’s June 13 2024 call to “find critical vulnerabilities” and “do maximum harm” to Western infrastructures sounds like unusually explicit encouragement of Russian ransomware actors.
However, statements from as early as 2016 suggest the Russian military was already thinking about how ransomware could play a role in cyber-enabled information operations to force enemy countries to choose leadership and policies favorable to Russia.
Russian military hackers attempted to overthrow the Ukrainian government, under the guise of ransomware, in 2016 and 2017.
After these attempts failed, developments after 2017 are consistent with subtler Russian encouragement of ransomware attacks on Ukraine and its allies.
2024: Medvedev’s Call to “Inflict Maximum Damage”: Marching Orders for Russian Cybercriminals?
On June 12, 2024, the US issued tough new sanctions on Russia, unsettling Russia’s banking system and causing values on the Moscow stock exchange to plummet briefly. On June 13, Russian Security Council deputy chairman Dmitry Medvedev posted on his Telegram social media account an appeal for Russians and friends of Russia to retaliate by inflicting “maximum damage” against Western societies and economies. The Russian-language original reads, in part:
We need to [react]. Not only the authorities, the state, but all our people in general.... After all, they - the U.S. and its crappy allies - have declared a war on us without rules! ....Every day we should try to do maximum harm to those countries that have imposed these restrictions on us and our citizens.... Harm their economies, their institutions and their rulers. Harm the well-being of their citizens. Their confidence in the future. To do this, we need to continue to search for critical vulnerabilities in their economies and hit them in all spheres (надо и дальше искать критические уязвимости их экономик и бить по ним во всех сферах). Damage them everywhere, paralyzing the work of their companies and state institutions. Find problems in their most important technologies and mercilessly strike blows at them. Literally destroy their energy systems, industry, transport, banking and social services. Instill fear through the inexorable collapse of [their] entire critical infrastructure.
Patriotic Russian cybercriminals, such as Mikhail Matveev (a.k.a. “Wazawaka”) and others featured in Natto Thoughts’ “Ransom-War” series, could well see Medvedev’s statement as a call to action and marching orders. Medvedev specifically called for finding “critical vulnerabilities” (критические уязвимости),” using a term for technical flaws that cyber threat actors exploit to hack into victim computer systems. And he called for “continuing” this effort, implying that the pursuit and exploitation of vulnerabilities has gone on for some time.
In some ways, Medvedev’s statement sounds like bluster to influence global debates on whether to further support Ukraine’s war effort or pressure Ukraine to accept Russia’s territorial conquests. Known as Russian President Vladimir Putin’s “attack dog” and a “scaremonger whose job is to deter Western action over Ukraine,” Medvedev issues threats that are not always followed by action. However, Medvedev has growing clout in Putin’s entourage, according to emigre Russian analyst Mikhail Zygar, and “the idiocies he continually repeats are obviously not antithetical to Putin’s own views,” as US analyst Alexander Motyl points out. Putin sometimes echoes Medvedev’s extreme statements; the maximalist demands Putin made in a June 14 speech in essence resembled those Medvedev had made in March.
Anxiety in Europe Over In-Real-Life Russian Sabotage Campaign:
Medvedev’s call to “instill fear through the inexorable collapse of [their] entire critical infrastructure” is capitalizing on an atmosphere of alarm already present in Europe and other NATO countries. For months, European, NATO, and US officials have been warning that Russia has carried out and continues to plot “violent acts of sabotage across the [European] continent as it commits to a course of permanent conflict with the West,” as the Financial Times wrote on May 5.
The FT and other reports cited events occurring in recent months that appear linked to the Russian state and its proxies:
alleged plots to attack or sabotage military sites in Germany and France;
arson at facilities that supply aid for Ukraine, as well as at giant retail outlets;
GPS jamming;
signalling disruptions and actual or planned derailments on rail lines in Sweden, Czechia and Poland ;
and vandalism against the automobiles of the interior minister and a journalist in Estonia.
Motives: The aims of these Russian sabotage plots appear to include promoting disunity among Ukraine’s allies, disrupting military supplies to Kyiv, and testing western resolve. Officials and commentators have characterized Russia’s goal as “to sap support for the Ukrainian war effort”; to destabilize and intimidate Europe; and “to send a message that it is omnipotent and can disturb our societies . . . to instigate fear and to find ways to make our lives more miserable,” as Latvia’s President Edgars Rinkēvičs put it. Security analyst Keir Giles characterized these incidents as “pinprick attacks” aimed at disruption and disinformation and even as “’practice runs’ in preparation for if they want to immobilize Europe for real.”
Proxies: These “grey zone” physical sabotage operations, which security officials said were mostly organized by Russia’s GRU military intelligence service, often use local criminals, members of the Russian diaspora or other nonstate actors as proxies in target countries. This may be intended to obscure the state’s involvement and make the attacks in those countries “appear to be the result of domestic opposition to supporting Ukraine,” the The New York Times put it.
Marching orders for Russian ransomware actors?
The Europeans warn that Russian sabotage campaign includes not just physical but also disruptive cyberattacks. A May 3 2024 German statement read, “Russia also considers cyber sabotage as options for action, with collateral damage and spillover effects being ruthlessly accepted.” On the same day, NATO said Russian GRU hacker group APT28 had targeted critical infrastructure operators in several countries, likely with the goal of disrupting essential national functions.
Like the physical attacks, Russia conducts the cyber attacks not just directly but also through proxies. Anne Keast-Butler, director of the UK’s GCHQ intelligence agency, speaking at the CyberUK 2024 conference on May 14, 2024, specifically accused the Russian government of encouraging non-state actors in both cyber attacks and physical sabotage:
We are increasingly concerned about growing links between the Russian intelligence services and proxy groups to conduct cyber-attacks – as well as suspected physical surveillance and sabotage operations. Before, Russia simply created the right environments for these groups to operate… but now they are nurturing and inspiring these non-state cyber actors.....
While they did not specifically mention ransomware, it is logical to assume that the European and NATO officials also had it in mind, given that ransomware represents the most disruptive type of Russian criminal cyber-attack. As examples of Russian criminals’ power to inflict massive disruption, a February 2024 attack on Change Healthcare disrupted insurance coverage for prescriptions, leaving patients struggling to pay for essential medicines; and in June an operation crippling a key supplier to the UK National Health Service in early June led to desperate appeals for blood donations.
Medvedev’s statement – a call to arms to continue undermining Western countries – is the clearest statement the Natto Team has found of apparent Russian government encouragement and inspiration for cybercriminal attacks.
However, Russian government-linked entities have been talking about and experimenting with the weaponization of ransomware since at least 2016. We already know, as Part I of this series has also explored, that various Russian agencies had had a “symbiotic relationship” with Russian hackers for years. But a series of events and statements in 2016-2017 showed people in Russian government service exploring the idea of using ransomware as a particularly potent and deniable tool of information warfare to disrupt adversary societies. One of the first of these was an unlikely character: a fictional persona called “Alice Donovan.”
2016: “Alice Donovan”: “To ransom a whole country”
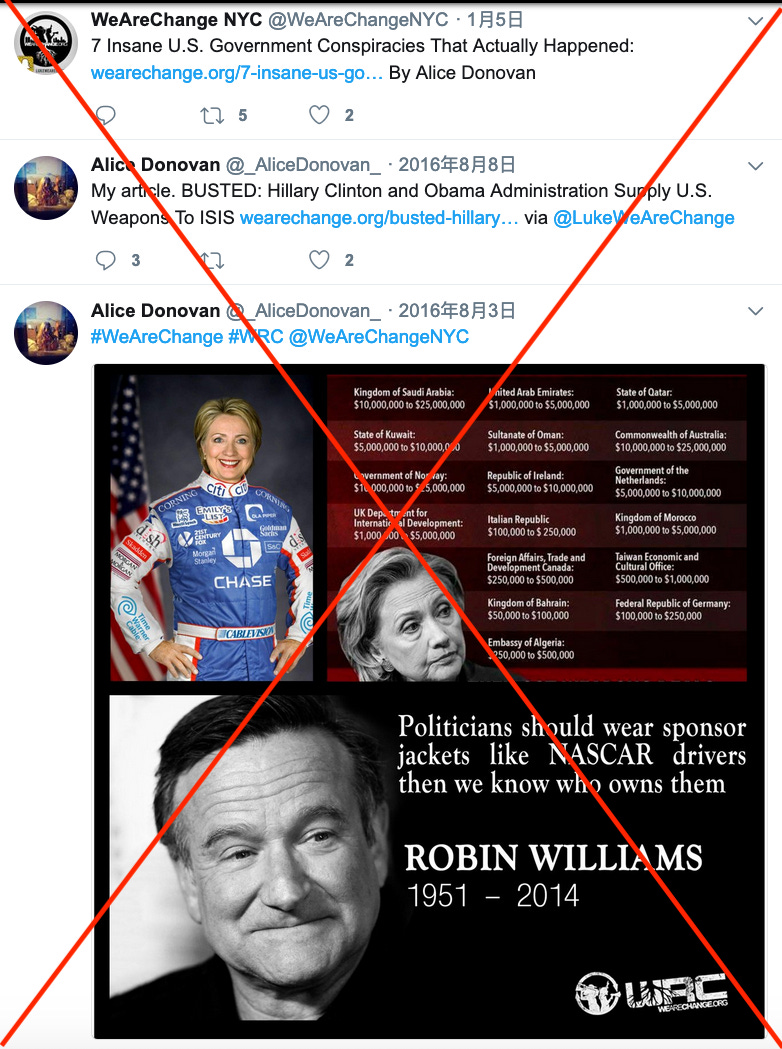
In late February 2016 an email arrived in the in-box of left-leaning American media outlet Counter-Punch: “Hello, my name is Alice Donovan and I’m a beginner freelance journalist.” Throughout that tumultuous – amid a vitriolic election campaign between Hillary Clinton and Donald Trump, turmoil in the Middle East, and protests in US cities over police killings of young Black men – “Alice Donovan” published commentaries in US alternative media. Her articles, critical of Hillary Clinton and of US domestic and Middle East policies, sometimes promoted conspiracy theories and misleading information. The articles bore titles like ““Busted: Hillary Clinton and Obama Administration Supply Weapons to ISIS,” referring to the Islamic State jihadist group against whom the US and other countries were fighting in Iraq and Syria; “Is Dallas Shooting the First Spark of Potential Powder Keg?,” referring to the July 7 2016 killing or injuring of a dozen Dallas police officers in an ambush by an angry citizen; and “US-led Coalition Airstrike On Assad’s Forces Was Not Accidental,” referring to Syrian dictator Bashar Al-Assad. “Alice” also attempted to infiltrate the Black Lives Matter community by promoting a social media group called“Baltimore is Everywhere”; and “she” allegedly used her account to create the DCLeaks Facebook page that would leak explosive data that Russian hackers had stolen from the US Democratic party in an effort to undermine Clinton’s candidacy.
Screenshot from “Alice Donovan”s Twitter account, cached December 26, 2017
“Alice Donovan” turned out to be a cover persona for members of Russian Military Unit 74455, hackers from Russia’s GRU military intelligence agency who are also known as the Sandworm group. On July 13, 2018, the US Justice Department charged 12 GRU officers with conspiring to hack and leak documents “to interfere with the 2016 U.S. presidential election.” It said they posed as ordinary American citizens by creating and using various false social media personas, including “Alice Donovan.”1
We don’t know which GRU employee(s) allegedly sat at the keyboard and spoke with “Alice’s” voice. However, the US Justice Department alleges that they accessed “her” account via computers managed by Aleksey Potemkin, a GRU officer who supervised a department in Military Unit 74455. His photo appears in the middle of the bottom row of the FBI wanted poster on the group.
Description automatically generated" width=“789” />
FBI poster showing those wanted for interference in the US 2016 elections
As analysts at the Stanford Internet Project pointed out in 2019, “Alice” clearly served to promote the various priorities and foreign policy goals of the Russian Defense Ministry to US audiences – such as in “her” vocal support for Syrian dictator Bashar Al-Assad. In contrast, the false social media personas that Russian mercenary and information warrior Yevgeniy Prigozhin’s Internet Research Agency troll farm created focused mainly on the US election.
Given how closely “Alice”s writing reflects the views of the Russian military, an article “she” wrote about weaponizing ransomware gives us clues to their thinking on that topic. Ever since Soviet days, when publicly available information was often sparse or misleading, Russia-watchers have practiced “Kremlinology,” parsing government words, actions, and even visual images such as the lineup of officials on the viewing stand during a military parade, to deduce government thinking and intentions. A Kremlinological analysis of “Alice’s” article suggests that the GRU officers who created her had thought about the weaponization of criminal ransomware and even planned scenarios for using it.
On April 26, 2016, “Alice Donovan” published in Veterans Today an article entitled “Cyberwarfare: Challenge of Tomorrow,” warning of the threat of government cyber attacks on civilian critical infrastructure. After describing examples of ransomware in the health sector, “Alice Donovan” wrote,
Today such ransomware attacks are largely the work of criminal actors looking for a quick payoff, but the underlying techniques are already part of military planning for state-sponsored cyberwarfare. … Moreover, the US has been designing crippling cyberattack plans targeting the civilian sector. In case its nuclear negotiations with Iran failed2, the US was prepared to shut down the country’s power grid and communications networks…
“Imagine a future “first strike” cyberattack in which a nation burrowed its way deeply into the industrial and commercial networks of another state and deployed ransomware across its entire private sector, flipping a single switch to hold the entire country for ransom. Such a nightmare scenario is unfortunately far closer than anyone might think.
Several details in the article suggest that the GRU officers who created her had thought about the weaponization of ransomware. The article purportedly focuses on US plans and actions. This is typical of Russian political writing: they focus on aggressive actions somebody else is taking but often seem to be describing and trying to justify what they are doing themselves:
“…Today such ransomware attacks are largely the work of criminal actors looking for a quick payoff, but the underlying techniques are already part of military planning for state-sponsored cyberwarfare.” The article provides no evidence to prove US government intentions for military use of criminal ransomware.
“…In case its nuclear negotiations with Iran failed the US was prepared to shut down the country’s power grid and communications networks.” The article provides no evidence on specific US planning to cripple Iran’s civilian infrastructure. Ironically, at this very time, cyber threat actors within Iran were developing the SamSam ransomware, which would cripple numerous American cities in 2018 (see Appendix below).
“… deployed ransomware across its entire private sector”: This shows that the GRU has thought about how a military can carry out disruptive activity under the guise of non-state actors. This is important because cyber defenders often narrowly conceive of state threat activity only in terms of espionage or military targeting, and cybercriminal activity only in terms of profit-making. This may cause them to overlook state activity disguised as criminal activity.
“…to hold the entire country for ransom”: This provides a clue as to what the GRU envisioned doing by using ransomware. Holding a country for ransom implies getting it to do what you want, whether replace a government or change its policies, such as lifting sanctions on Russia or ending support to Ukraine. Strategic theorists use terms like “compellance” or “coercion” to describe this form of extortion.
The GRU officers allegedly behind “Alice Donovan” did not pen this article themselves. They plagiarized most of it from an essay by tech futurologist Kalev Leetaru. However, they omitted a key sentence from Leetaru’s original article, as American national security journalist Marcy Wheeler noticed. They neglected to include the sentence where Leetaru pointed to aggressive Russian activity: “Russia showcased the civilian targeting of modern hybrid operations in its attack on Ukraine’s power grid, which included software designed to physically destroy computer equipment.” By modifying and republishing someone else’s work, the GRU officers behind “Alice” were in effect sending their own message – blaming the US for aggressive cyber threat activity, implying that the US would do so under the guise of criminal ransomware, and thus justifying future malicious activity that Russia’s own military would carry out in the same way.
Alice must have considered “her” article important because “she” posted it three times. The third publication came just days after a mysterious persona called ShadowBrokers publicized sensitive cyber weapons associated with the US National Security Agency (NSA). (The jury is still out on who stands behind ShadowBrokers, though some suspect Russia.) It was as if “Alice Donovan” was encouraging hackers everywhere to try out the newly leaked NSA tools and see how much havoc they could cause. Hackers using the tools did cause havoc, first in the May 2017 WannaCry global pseudo-ransomware outbreak — which the US and the UK attributed to the North Korean state — and later the Petya.A (NotPetya) attack of June 2017, which the US has attributed to the GRU. That is, a year after publishing “Alice”s article, the GRU itself would try out the scenario “Alice” described in her article.
2016-2017: GRU Tries Direct Attacks on Ukraine with Pseudo-Ransomware
Military attempts at overthrowing the Ukrainian government under the guise of ransomware in 2016 and 2017 failed—though all-out war since 2022 has pursued some of the same destructive goals in a cruder physical way.
The Russian military tried to take out the entire information infrastructure and overthrow the government of Ukraine on at least two occasions, both times using pseudo-ransomware that was designed to allow the state to deny involvement. ESET, a Slovakia-based cybersecurity company, chronicled how Russian military hacker group Sandworm (which it referred to as Telebots) experimented with the use of fake ransomware in late 2016 and 2017, from the Crashoverride attacks of December 2016 to the Petya.A/NotPetya attack of June 2017.
Crashoverride: Throughout much of December 2016, Sandworm carried out a series of attacks on numerous Ukrainian agencies, beginning with the pension system, treasury, and other agencies, culminating in a blackout that left parts of Kyiv in darkness for hours. The attacks used Crashoverride (a.k.a Industroyer) and Killdisk malware, disguising a wiper attack as criminal ransomware or hacktivism. The hackers apparently intended the malware to cause physical damage to the transmission station when the utility tried to turn the equipment back on, according to subsequent analysis.
During this December 2016 campaign the Telebots/Sandworm actors began to add ransom messages, with demands for what appeared at that time an unrealistically high ransom of 222 Bitcoin, or approximately $250,000 at 2016 prices. However, this was really fake ransomware. The malware did not allow for the decryption of bricked-up systems even if the victim paid the ransom; “collecting ransom money was never the top priority for the TeleBots group,” according to ESET.
The Sandworm attackers appear to have intended to collapse the government of then-president Petro Poroshenko and to bring in a more pliable government. The message the attackers displayed on victims’ computer terminals suggests this. The malware overwrote files with strings “mrR0b07” or "fS0cie7y,” borrowing terms from the TV show “MrRobot,” about an anti-social computer programmer who works as a cybersecurity engineer during the day but a vigilante hacker at night. The compromised terminals linked to a “MrRobot” promotional website. Ukrainian news sites soberly reproduced text from the fan website as if it were a message directed at the Ukrainian government: “We lit the fuse of revolution. Now we decide if it sputters and dies, or truly ignites. Our real work is just beginning.” The Sandworm hackers appear to have intended that their disruption of Ukraine’s public services could inflame popular discontent and inspire the Ukrainian public to overthrow its government.
Indeed, one Ukrainian official speculated that the Crashoverride attacks was Russia’s attempt to execute the so-called “Shatun Plan,” a document that Ukrainian hackers leaked in October 2016 after purportedly stealing it from the email account of Putin’s top Ukraine aide, Vladislav Surkov. The Shatun Plan document called for destabilizing Ukrainian society by fanning popular discontent over public services. Though that document itself is of dubious authenticity, it does represent techniques Russia has used against Ukraine in the past. Regardless, President Putin considered the Crashoverride attacks and other efforts insufficient. He berated Surkov in May 2017 for not having destabilized the sociopolitical situation in Ukraine and called for a “reset of the ruling regime” there, according to Ukraine’s security service chief.
In the following months, as ESET researchers detail, Sandworm hackers further experimented in using ransomware to make it appear as if destructive attacks were financially motivated.
Petya.A/NotPetya:
Sandworm’s most dramatic attempt at using fake ransomware to destabilize Ukraine was the June 27, 2017 attack using Petya, a widely available ransomware code. (Reports refer to the incident as “NotPetya” or by various other names, but the Ukrainians refer to it as “Petya.A”) The incident crippled government offices and businesses in Ukraine and paralyzed logistics company Maersk and numerous other multinational businesses, causing some $10 billion in damage worldwide and changing the landscape of the insurance sector. Again, the pseudo-ransomware did not even allow for paying the ransom, showing its intent was purely destructive.
Again, the authors intended the attack to cause maximum pain to the entire country of Ukraine. The malware was delivered via a document delivery program almost universally used for official business in that country and had its greatest impact in Ukrainian government offices. Again, the Sandworm hackers’ intent appears to have been the toppling of Ukrainian President Petro Poroshenko. Their choice of the Petya.A version of malware code was in itself a snipe at the Ukrainian president. “Petya” is a dimunitive form of Poroshenko’s first name – an insult when applied to a president – and the “A” matches the first letter of Poroshenko’s middle name in its Russian spelling, Alekseyevich. Just days earlier, on June 15, 2017, during President Putin’s annual call-in show aired on Russian TV, Putin had touted his friend Viktor Medvedchuk as a potential leader for Ukraine, suggesting he expected the overthrow of Poroshenko soon.
However, the Sandworm authors also appeared to have tried to limit the malware’s reach to avoid spilling outside Ukraine’s borders. They used a leaked US tool to allow the malware’s rapid spread, but only within local area networks (LANs). Possibly they were attempting to avoid the devastating global destruction that WannaCry, the pseudo-ransomware attributed to North Korea, had unleashed just weeks previously. Petya’s massive collateral damage was likely unintentional. Putin and his military hackers likely did not want to start World War III. In the words of a 2023 report by the Chatham House think tank, “Russia was keen to confine the impact of its attacks to Ukraine in order to avoid a confrontation with NATO nations.”
Continued state hacker use of pseudo-ransomware against Ukraine
The Petya attack failed to stay within the bounds of Ukraine and also failed to bring down the Poroshenko government. Apart from some later and more narrowly targeted pseudo-ransomware attacks, such as BadRabbit, the Sandworm hackers cut back on massive pseudo-ransomware attacks on the Ukrainian government for a few years. In 2022 Sandworm again used wiper malware with a decoy ransom note in the WhisperGate campaign a month before the full-scale invasion of Ukraine , and several times thereafter. The so-called HermeticWiper malware, deployed during the full-scale invasion itself, contained a pseudo-ransom component call Elections GoRansom.
After the full-scale invasion, tanks and missiles have been more effective at wiping out Ukraine’s public services, and arguably there has been less need to mask wipers as ransomware. However, in early 2023 Wired reported an “explosion of new wiper variants” targeting Ukraine since late 2022, some of them posing as ransomware. Wired said ESET views this “a kind of brute-force approach. Russia appears to be throwing every possible destructive tool at Ukraine in an effort to stay ahead of its defenders and inflict whatever additional chaos it can in the midst of a grinding physical conflict.”
Against Western Countries: Avoid Escalation Through Indirect Approach
Russian state-linked hackers’ pseudo-ransomware has spilled over to Russia’s neighbors on a few occasions. During the full-scale invasion of Ukraine in February 2022, the HermeticWiper malware and its Elections GoRansom component affected financial entities and government contractors in Ukraine, Latvia, and Lithuania. (Some of the victims outside Ukraine may have been foreign branches of Ukrainian companies, Trellix points out. Sandworm reportedly used the Prestige ransomware strain against logistics entities in Europe and Poland in October 2022.
But otherwise, little evidence exists of direct Russian military cyber threat activity disguised as ransomware and targeting Western countries. Certainly, the scenario “Alice Donovan” outlined in 2016, of a state hacker infiltrating multiple critical infrastructures of a Western country and then “flipping a single switch to hold the entire country for ransom” seems unlikely.
Russian intelligence services have long drawn on cybercriminals for deniable operations, such as the patriotic hackers who brought Estonia to a standstill in 2007. As of 2013, Major-General Igor Dylevskiy, Deputy Head of the Main Operations Directorate of the Russian General Staff, seemed to think this is permissible. He and coauthors stressed in a military journal article3 that
under international law, only those attacks that are either conducted or directed by the armed forces of a specific country can be classified as legal aggression. Cyberattacks by nonstate actors, therefore, should be treated as criminal acts such as terrorism or extremism, but not as acts of aggression. The country that “hosts” such an attacker is not responsible for their actions unless a link between them and the armed forces or political leadership of that country is proven.
By 2021, Russia would sign on to UN norms saying states should refrain from knowingly allowing their territory to be used for hacking other countries’ critical infrastructure, and indeed should help mitigate such activity. Russia’s actions, however, show they have no intention to abide by these norms.
Since 2017, ransomware and data leak extortion against critical infrastructure in Western countries have surged. Circumstantial evidence supports an assessment that Russian intelligence services have means and motive to encourage and take advantage of the ransomware criminals’ activity to pressure Western decisionmakers to make decisions favorable to Russia, but with deniability to prevent escalation.
2017-2019: Upsurge in Ransomware
The years 2017-2019 saw a growth in the volume, sophistication and social cost of ransomware. Municipalities, schools and healthcare and other Western public services were particularly vulnerable to this surge. “Publicly acknowledged ransomware attacks against state and local governments jumped 39 percent in 2018,” according to Recorded Future. Those years also saw the growth of double extortion – where the perpetrators stole sensitive data and demanded extra ransom in return for a promise not to publicize it. Ransomware has also become more professionalized; the growth of markets for stolen passwords and ransomware-as-a-service made it easy for even inexperienced hackers to attack targets.
All of these factors are consistent with the hybrid use of ransomware for combined political and financial motives.
Double extortion potentially serves hybrid purposes, addressing both the financial motives of the cybercriminals and the political motives of any intelligence agencies who might draw on their help.
The targeting of public services grew even though such organizations were less likely to pay the ransom than other entities. Recorded Future reported in 2019 that “only 17.1 percent of state and local government entities that were hit definitely paid the ransom,” compared with 45% of victims overall. The 2019 Recorded Future report hypothesized that the “outsized media coverage” generated by attacks on public services led attackers to mistakenly consider them “potentially profitable targets.” However, it is also plausible that Russian intelligence services encourage ransomware actors to attack such entities for political purposes, whether or not they make a profit. The leaking of sensitive data from schools, hospitals or municipalities can potentially undermine confidence in those public services, as well as providing data for espionage or future attacks.
As mentioned in Natto Thoughts’ “Ransom-War: Part 1” report, Stanford Internet Project researchers found Russia-origin ransomware attacks clustered around politically significant dates such as the eve of elections in democratic countries
Variety of Russian Intelligence Service Sponsors
In contrast to the GRU’s blunt approach, other Russian government agencies besides the GRU work more subtly with ransomware actors and tools. Will Thomas (@BushidoToken) of the Equinix Threat Analysis Center, speaking at the May 24 2024 Sleuthcon cybersecurity conference on “the intersection between state-sponsored intelligence operations and state-permitted organized cybercrime,” provided a useful overview of the different approaches of Russian agencies toward the use of criminal tools or personnel.
As he phrased it:
The GRU uses crimeware and adapts it for their own operations.
The Federal Security Service (FSB) — mostly a domestic intelligence and law enforcement agency but with international reach — recruits cybercriminals for their own operations. They can use the threat of arrest to coopt or extort bribes from criminals.
The Foreign Intelligence Service (SVR) keeps an eye on the cybercrime underground and purchases credentials for high-value compromised targets from crime markets, but otherwise keeps their distance from criminals, Thomas said.
SVR Links Likely Closer: The Natto Team’s findings largely overlap with the findings of Will Thomas, but with some additions. Contrary to Thomas’ assertion that the SVR avoids working directly with cybercriminals, we saw in our previous reports that Conti member Professor said he had paying clients “по внешке,” likely referring to the SVR, whose name in Russian is Служба внешней разведки. This suggests a closer relationship between the SVR and Conti. “Professor” said the “CozyBears” (an SVR hacker group also known as APT29) were “going through the list,” likely referring to lists of compromised computer systems, presumably to see whether Cozy Bear would pay for access to those targets or for Conti actors to further breach them.
War Without Rules?
Arguably the campaign that came closest to “Alice Donovan”s vision of ransoming an entire country is the series of attacks using Conti ransomware that crippled Costa Rica for months in 2022. Mikhail Matveev (Wazawaka) took credit for these attacks and tauntingly called for the people to overthrow Costa Rica’s pro-US government. Ransomware actors have also managed to cripple massive segments of global economies for weeks at a time through supply-chain attacks – targeting those entities that provide software or other products or services to multiple clients.
Over the years the Russian government feared escalation. “They want to take the war to Europe, but they don’t want a war with NATO,” according to Andrea Kendall-Taylor, a former US intelligence official now at the Center for a New American Security think tank, speaking about the recent sabotage attacks in Europe. But Dmitry Medvedev’s June 13 posting claimed that the US and its allies had declared a “war…. without rules!” against Russia, implying that Russians and their friends should consider themselves to be waging a war without rules against the West as well.
Russian cybercriminals, knowing they live in a strange situation of impunity but also vulnerability, might wonder: does Medvedev’s bluster about inflicting maximum damage really mean the gloves are off in this virtual global war. Or will the Russian government yanked up short lest their activity unintentionally sparks World War III?
The next installment of the “Ransom-War” series tries to make sense of the sporadic Russian crackdowns on ransomware actors over the years. They seem less aimed at genuine international cooperation against cybercrime than at ensuring Russian cybercriminals’ cooperation with Russian government priorities. Later we will discuss particular incidents and their possible links with Russian intelligence services.
Thanks for reading Natto Thoughts! Subscribe for free to receive new posts and support the Natto Team’s work.
Appendix: Iran as model
If indeed Russian intelligence services consciously encouraged criminal ransomware for their own purposes, they may have drawn inspiration from Iran, a country cybersecurity expert Dmitri Alperovitch called a “ransomware innovator.” Iran had a long history of ransomware activity, including apparent state-based use. In 2018 the SamSam ransomware group crippled numerous municipalities such as the city of Atlanta, including some services at its airport, a major global hub. The ransom demand of about $50,000 was large by 2018 standards but seems laughably small compared to the damage to the city, leading the Natto Team to suspect the goal was politically motivated disruption rather than profit. A US PhD dissertation provided further evidence of non-financial motivation, although the author instead posited “emotional thrill” as the perpetrators’ motive. The US indicted two Iranians, but the FBI said it did not have evidence the campaign was state-backed. The Treasury department, however, when sanctioning two SamSam facilitators, implied that they had some link to the “Iranian regime.” More recently, analysts have pointed to Iranian regime-sponsored “lock-and-leak” attacks disguised as ransomware.
Regardless of the SamSam actors’ motives, Russian strategists may have viewed the attacks on municipalities as a model to imitate.
Selected Studies on Information Warfare.
The Natto Team is aware of many Western research reports that have mined Russian government documents and academic literature to understand evolving Russian views on cyber conflict and information warfare – though sadly not on ransomware in particular. Some of these studies appear in the following list. See also the secondary sources described in Part 1 of this “Ransom-War” series, as well as Natto Thoughts series on disinformation and postings on the hacktivist persona Solntsepek.
Keir Giles, “Handbook of Russian Information Warfare,” Fellowship Monograph 9, Research Division, NATO Defense College, November 2016.
Michael Connell and Sarah Vogler, “Russia’s Approach to Cyber Warfare,” Center for Naval Analyses, March 2017.
Joss Meakins, “Living in (Digital) Denial: Russia’s Approach to Cyber Deterrence,” Euro-Atlantic Security Report, European Leadership Network, July 2018,
Bilyana Lilly and Joe Cheravitch, “The Past, Present, and Future of Russia’s Cyber Strategy and Forces,” 2020 12th International Conference on Cyber Conflict, NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE),
“Russian Cyber Gambits,” Chapter 3 of the series “Great-Power Offensive Cyber Campaigns: Experiments in Strategy,” International Institute for Strategic Studies, February 2022.
Michelle Grisé et al, “Rivalry in the Information Sphere: Russian Conceptions of Information Confrontation,” RAND Corporation, research completed April 2021, published 2022
Keir Giles, “Russian cyber and information warfare in practice. Lessons observed from the war on Ukraine,” Russia and Eurasia Programme Research Paper, Chatham House (Royal Institute of International Affairs), December 2023
For more detail on Alice Donovan, see profiles in the New Yorker and Counterpunch. On Russian state hackers’ creation of other fictitious personas, see this report from the Carnegie Endowment, a US-based think tank, and Natto Thoughts’ report on the Solntsepek persona.
“nuclear negotiations with Iran” refers to the intense US-led negotiations leading to the 2015 Joint Comprehensive Plan of Action (JCPOA) that limited Iran’s nuclear weapons development in return for an easing of sanctions on Iran.
I. N. Dylevskii, S. A. Komov, and A. N. Petrunin, “Ob Informatsionnykh Aspektakh Mezhdunarodno-Pravovogo Poniatiya ‘Agressiya’ [On Information Aspects of the International Legal Definition of ‘Aggression’],” Voennaya Mysl’ [Military Thought], No. 10, 2013
Article Link: Ransom-War Part 3: Inflict Maximum Damage - by Natto Team