Organizations depend on their security analyst to detect, investigate, and respond to any security incident, but might not always give them the right tools for their job. They focus too much on delivering them a tool but not enough on solving their operational challenges.
In other words, better threat detection, investigation, and response shouldn’t compromise the analyst’s operational experience. Security operations platforms should be scalable and sustain their own evolution. Otherwise, SOC teams will witness how they start losing control over the IT and security environment.
With this premise of offering a better experience to analysts and more control over security operations, we have released several updates in Logpoint during the last months. Users can expect improvements on usability, performance, access control, automation, and log storage.
Usability as a control enabler
While usability in itself isn’t a synonym for more control, it nonetheless enables control over a tool. Therefore, we are making sure that SIEM engineers save time and headaches and regain control over the configuration of log sources through Syslog connectors.
In this update, they get access to more than 50 prepopulated log source templates for Syslog, and more to come in the future. Engineers can easily create custom configurations thanks to this support of templated Syslog log sources.
This is of extreme importance for engineers and MSSPs, as the configuration needs to be done only once and reused elsewhere. With this template-based system, engineers will reduce the time spent onboarding hosts and gain more control when they distribute these templates to other Logpoint systems.
Improvements to log source configuration don’t stop here. By updating our URAF API Fetcher, SIEM engineers can seamlessly configure log sources (RESTful APIs) and still meet specific application custom requirements, such as pagination and subsequent request handling.
Control over the interface with dark mode
Committed to improving usability, we are also making it possible to switch between dark and light modes. With a more eye-friendly interface, dark mode provides better readability and accessibility, especially for tasks that require in-depth focus on the screen, like incident investigation.
With one click, users can switch between light and dark mode. As with everything in life, it’s all about preferences. For those who work late at night and require an interface with less intense light with high contrast, Logpoint’s dark mode will do wonders.
Control the outcome of querying large volume of logs
Ease of use and smart UX flows allow user to stay on top of their platform and expect the outcome of their actions performed in it.
However, usability as a control enabler can only do so much without performance improvements. That’s why we are ensuring that analysts can have control over the queries they run, even if they try to retrieve large volumes of logs.
Now, they can perform Distinct_count() type queries to enhance security use cases, perform audits, or run in-depth investigations without worrying about timeouts or impacting the analytics pipeline. We’ve exponentially reduced the computational pressure required to perform a Distinct_count() type query so analysts regain control over the outcome.
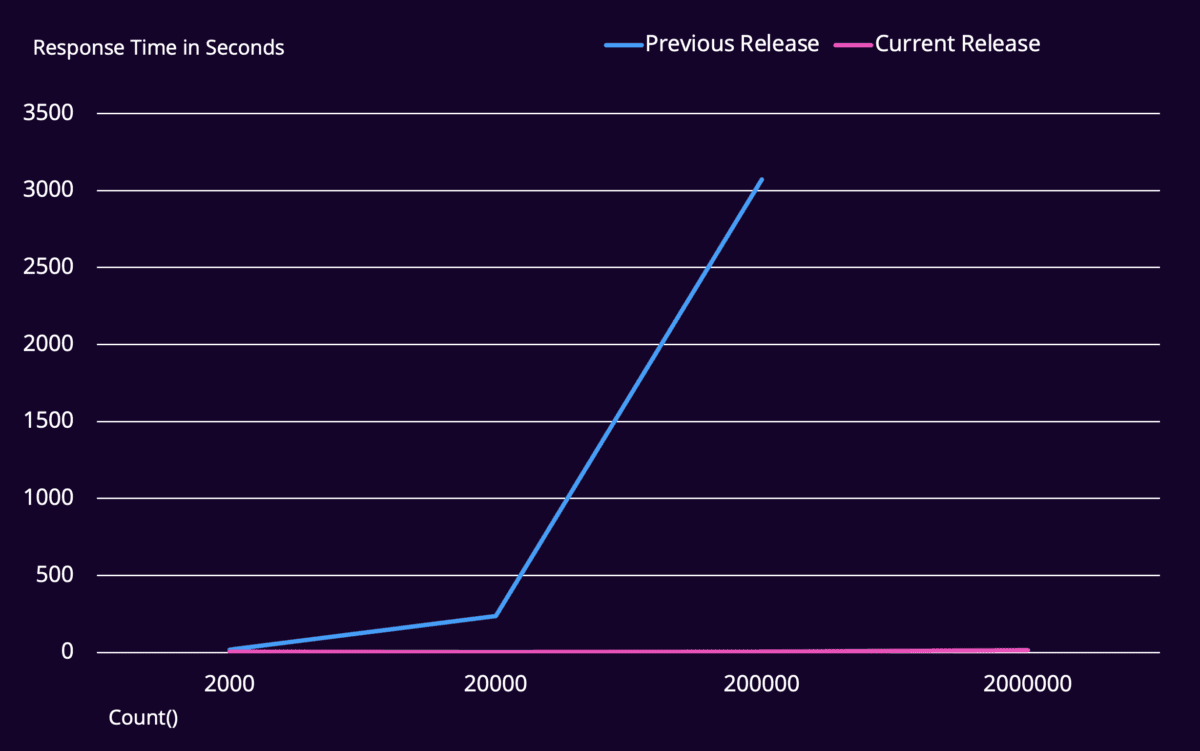
In turn, the time the query spent running in the background reduced from hours, or even timeouts, to seconds. What does this mean? The less time and computational pressure spent on running the queries, the fewer resources the system uses, maximizing its efficiency.
More control to work in multitenant environments
For system administrators, whether they work in MSSPs or large organizations with multiple tenants, control over what groups can view or who can make changes to log sources is paramount. Now, they can easily implement better security and privacy measures by adding object permission to log sources from the Log Source feature.
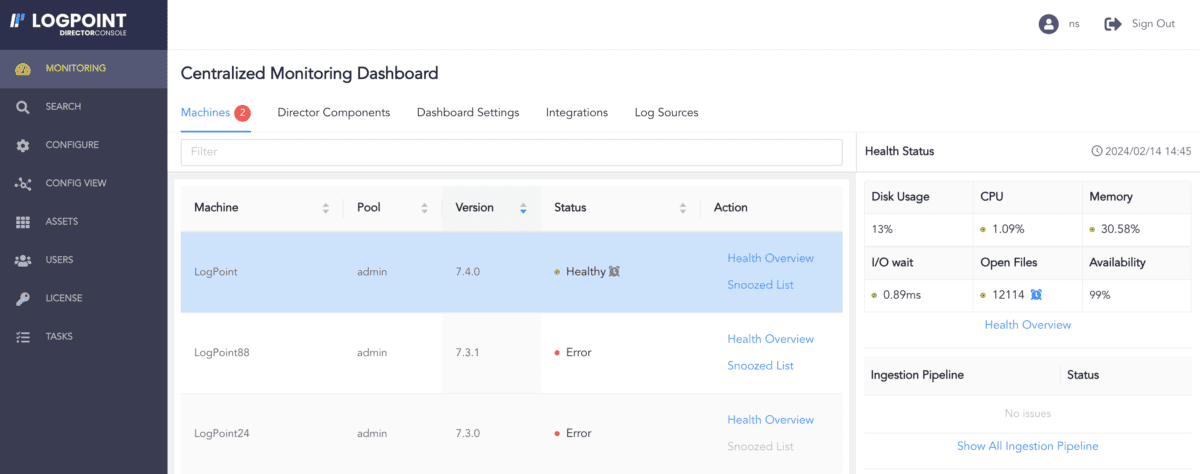
In addition to this, we made it easier for system administrators to sell all activities and detect all system issues across tenants to resolve them faster. Director’s latest update comes with a centralized monitoring dashboard of various systems and performance metrics in the last 24 hours. With this data available at a glance, administrators can always uncover issues and act proactively to mitigate what is causing them.
Better control over access extends to SaaS deployment, especially for SOC administrators who need to manage the access of several analysts across multiple tenants. With the introduction of Logpoint Portal for centralized access management, analysts can use central authentication to access several tenants without logging in and logging out. This not only simplifies the job of SOC administrators as they don’t have to create user accounts for each analyst in each tenant, but it also reduces the risk of accidental access and compliance failure.
Never lose control over your automation
Even if analysts let automation take control of most of your investigation and response tasks, it's important to understand what happened when a playbook failed. By using breadcrumbs, incident responders can read and execute actions through sub-playbooks and return to the relevant point in the parent playbook. Moreover, the monitoring tab now has a hierarchical view, allowing analysts to see the status of sub-playbooks and have more control over what’s going on in them – identifying and resolving issues in sub-playbooks was never that easy.
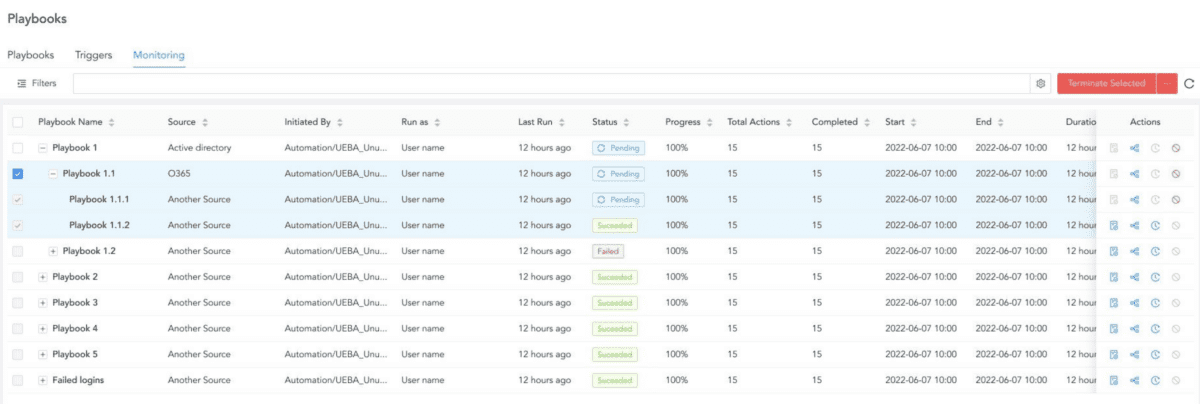
This update also comes with the encrypted backup of product credentials, so analysts avoid losing control when they restore an integration. Moreover, we improved the navigation to the content of a newly imported package. All this is coupled with persistent views of playbooks and graphs in cases, so even if the user navigates away or logs out, the view remains.
At Logpoint, we are eager to continue improving and innovating to make cybersecurity accessible to businesses, whether it is through ease of use or maximizing the potential of our solutions to address specific use cases.
If you want to know more about these releases, you can always reach out to our team, who’ll be happy to guide you through the update.
The post Logpoint’s latest release: Gain control over your security operations appeared first on Logpoint.
Article Link: Logpoint’s latest release: Gain control over your security operations
