Threat Intelligence Feeds are an essential part of your cybersecurity perimeter — if you use this tool correctly, you can increase your chances of detecting an attack — it’s like getting near real-time reports about the enemy from the front lines.
But do you know how to effectively use and operationalize threat intelligence feeds? Let’s discuss this in today’s article.
What are threat intelligence feeds?
First, let’s review what threat intelligence feeds are. Threat Intelligence (TI) feeds are a real-time subscription service for the latest cyber threat information, like malicious IPs, and URLs.
And just as you can sign up for a newsletter to receive news about world events, you can sign up for updates on the latest malicious indicators that security experts have discovered in the wild.
Think of it this way: when an organization is attacked somewhere, they analyze the threat and get IOCs from it. They can then choose to share the details with a feed vendor like ANY.RUN.
(Learn more about TI Feeds from ANY.RUN)
This vendor then pre-processes the indicators, removes false positives, and makes them available for anyone to use. The benefit is that you can digest these IOCs in your security systems and your organization obtains immunity to these attacks.
Types of TI Feeds
TI Feeds can be either commercial or open source. Let’s discuss the difference:
Commercial threat intelligence feeds contain data collected and pre-processed by a cybersecurity vendor in a proprietary manner.
They are typically more limited in scope, but the data contains fewer false positives and benefits from unique processing and sourcing — for example, ANY.RUN sources data from interactive sandbox analysis sessions, where 400,000 cybersecurity professionals detonate and analyze behaviour of ream malware samples.
(Read how we source and process indicators for ANY.RUN TI Feeds)
For example, in ANY.RUN TI Feeds, indicators are enriched with links to sandbox analysis sessions where the indicator was pulled from, which looks like this:
"external_references": [
{
"source_name": "ANY.RUN task c761d29c-a02a-4666-bc34-b89c4aab5cd1",
"url": "https://app.any.run/tasks/c761d29c-a02a-4666-bc34-b89c4aab5cd1"
},
{
"source_name": "ANY.RUN task 49e5fc75-a203-4d98-b055-ce41b0597a42",
"url": "https://app.any.run/tasks/49e5fc75-a203-4d98-b055-ce41b0597a42"
},
{
"source_name": "ANY.RUN task 3438d5ce-3cfa-4ccc-9638-5d92ad34b406",
"url": "https://app.any.run/tasks/3438d5ce-3cfa-4ccc-9638-5d92ad34b406"
}
] This is valuable, because security professionals can open these recordings and study how the threat behaves within a system.
That’s a unique benefit of ANY.RUN’s TI Feeds that no other vendor can provide.
Learn more about TI Feeds on a quick call
Schedule a demoIn summary:
 Pros of commercial TI feeds:
Pros of commercial TI feeds:- More accurate pre-processing.
- Information about the latest threat.
Open source threat intelligence feeds contain data that companies have chosen to share with a non-profit or government agency that has taken it upon itself to centralize that data and distribute it to other companies.
In open source TI feeds, the sheer volume of data can far exceed what many commercial feeds can provide, but the data is less accurate.
Remember that the database of commercial feeds relies on data provided by the community, and if a company contributing to the feed has unreliable reporting, its errors will be carried over into the feed.
Below we’ve listed 5 examples of popular open source feeds and who runs them:
- Automated Indicator Sharing, Department of Homeland Security
- InfraGard Portal, FBI
- Abuse.ch
- Internet Storm Center, Sans
- The Spamhaus Project
In summary, the benefits of this category of TI feeds are:
 Pros of open-source TI feeds:
Pros of open-source TI feeds:- Wider threat coverage.
- Free to integrate.
Which type of feed is best for you?
The short answer is that you should consider both.
It’s rare for data from two vendors to contradict each other, so the more data you process, the more threats you can keep on your radar at all times.
Why consider commercial feeds: Because they can provide more relevant and accurate data about the latest threats.
Why consider open source feeds: Because they exponentially increase your overall threat coverage.
 But be mindful of indicator fatigue.
But be mindful of indicator fatigue.
Indicator fatigue affects the security team when their workspace is constantly flooded with alerts, many of which are false.
It creates a deceptive sense of security and blunts the response time when a real alert rolls in. It can even cause the alert to be ignored.
To avoid indicator fatigue, filter indicators based on the reputation of the source, how old the indicator is, and whether it contains contextual information.
In which format do TI feeds send data
For consistency, all major threat intelligence feeds use the same format called STIX (Structured Threat Information Expression) — this is an industry-standard format for exchanging cyber threat information (CTI).
Mostsecurity systems — and certainly all from major vendors — are capable of ingesting STIX-formatted data.
So the good news is that integrating threat feeds requires very little setup from a technical standpoint. While the exact steps vary from vendor to vendor, all you need to do is obtain an API key and plug it into your SIEM (Security Information and Event Management) or TIP (Threat Intelligence Platform) system.
{
"type": "ipv4-addr",
"id": "ipv4-addr--8c851c0c-ee42-5e7e-af06-f849efc0ffb4",
"value": "194.104.136.5",
"created": "2022-04-20T15:05:54.181Z",
"modified": "2024-02-19T11:21:47.728Z",
"external_references": [
{
"source_name": "ANY.RUN task c761d29c-a02a-4666-bc34-b89c4aab5cd1",
"url": "https://app.any.run/tasks/c761d29c-a02a-4666-bc34-b89c4aab5cd1"
}
],
"labels": [
"RedLine"
]
} STIX is a JSON-based data format. The example above shows how a single object is structured in ANY.RUN TI feeds.
Integrate ANY.RUN TI Feeds into your security systems
Contact SalesNote the fields for type (what this IOC is), value, timestamps (how new it is and when it was last updated), external references (in which sandbox session or sessions it was captured), and label (what threat it is associated with).
How to operationalize data from TI feeds
As we mentioned earlier, TI feeds are typically ingested into SIEM and TIP systems.
- SIEM systems: Collect, analyze, and correlate security events from multiple sources; data from TI feeds helps to better analyze these events.
- TIP systems: Contextualize indicators and build them into threat objects to get a more holistic view of the attack, enabling better prioritization and decision-making.
With the right setup, you can get more value out of this data. Here are a few things to consider:
Configure the ingestion frequency
Ingestion frequency controls how often you receive new data from TI feeds.
This setting depends on your cybersecurity strategy, and largely on how confident you are in your ability to structure and filter usable data from open source sources.
For example, one strategy might be to ingest data from more accurate commercial feeds as often as possible, and update open source feeds that have more data but are less accurate periodically to reduce noise and put less strain on your network.
For commercial feeds: Refresh commercial feeds in real time or as often as the vendor allows to minimize the time lag between when the indicator appears in the vendor’s database and when it enters your security systems.
For open source feeds: To minimize noise and avoid information overload, consider refreshing open source feeds periodically. Use them to enrich data from commercial feeds or to expand your coverage.
Set up data enrichment rules in your TIP to add context to the ingested indicators
Enriching TI data provides additional context to help you prioritize threats and make more accurate incident response decisions.
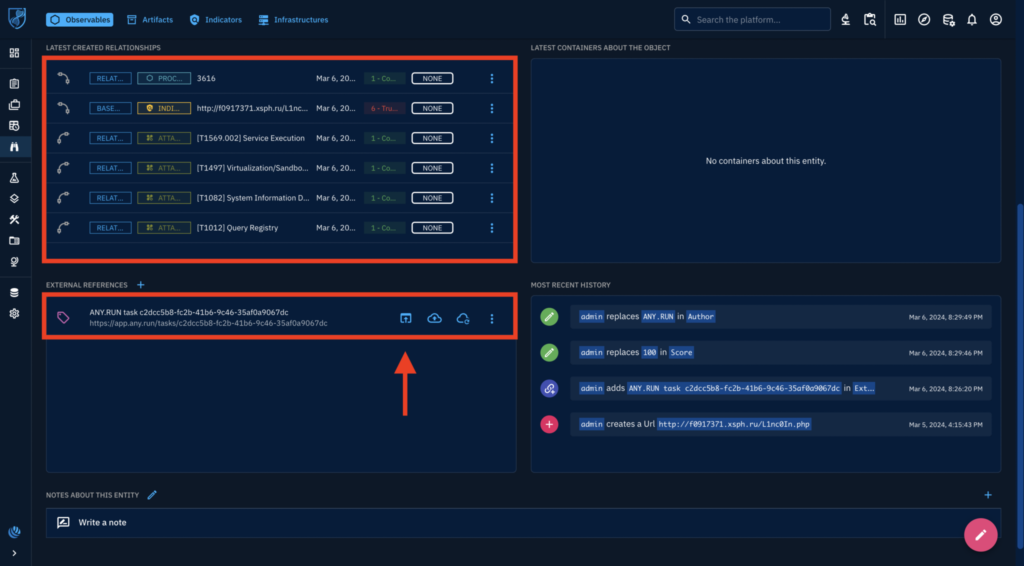 Enrich the data you receive from feeds with additional context in a TIP platform such as OpenCTI.
Enrich the data you receive from feeds with additional context in a TIP platform such as OpenCTI.For example, in OpenCTI, you can use the ANY.RUN sandbox connector to enrich the data you receive from feeds with more context, such as TTPs and maliciousness scores.
(Read how ANY.RUN integrates with OpenCTI)
Configure SIEM correlation rules to detect patterns and threats
Once you have ingested and enriched the data from TI feeds, the next step is to configure correlation rules in your SIEM system.
These rules help identify patterns and detect potential threats by analyzing the data from various sources, including TI feeds.
Prioritize high-confidence indicators: Focus on indicators with high confidence scores to reduce false positives and avoid indicator fatigue.
Combine multiple indicators: Create correlation rules that look for multiple related indicators, such as a combination of IP addresses, domain names, and file hashes associated with a specific threat.
You can then use this data to automatically trigger response actions based on the severity and confidence of the threats detected.For example, you can configure your system to automatically block IP addresses or domain names associated with high confidence indicators.
Wrapping up
With TI Feeds integration, you can get indicators from real attacks that have happened elsewhere in the world before they hit your organization.
If you are interested in integrating TI Feeds, consider a solution from ANY.RUN.
We would be happy to tell you more about how we collect and pre-process indicators — and why we are able to extract IOCs from threats that no other vendor can, helping you protect against the latest emerging malware.
Learn more about TI Feeds on a quick call
Talk to our teamAbout ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Advantages of ANY.RUN
ANY.RUN helps you analyze threats faster while improving detection rates. The platform detects common malware families with YARA and Suricata rules and identifies malware behavior with signatures when detection by family is not possible.
With ANY.RUN you can:
- Detect malware in under 40s: ANY.RUN detects malware within about 40 seconds of a file upload. It identifies prevalent malware families using YARA and Suricata rules and uses behavioral signatures to detect malicious actions when you encounter a new threat.
- Interact with samples in real time: ANY.RUN is an interactive cloud sandbox powered by VNC, which means that you can do everything you could on a real system: browse webpages, click through installers, open password-protected archives.
- Save time and money on sandbox setup and maintenance: ANY.RUN’s cloud-based nature eliminates the need for setup or maintenance by your DevOps team, making it a cost-effective solution for businesses.
- Record and study all aspects of malware behavior: ANY.RUN provides a detailed analysis of malware behavior, including network traffic, system calls, and file system changes.
- Collaborate with your team: easily share analysis results, or, as a senior team member, check work of junior analysts by viewing recordings of their analysis sessions.
- Scale as you need: as a cloud service, you can easily scale your team, simply by adding more licenses.
We’ll show you in an interactive presentation how ANY.RUN can help your security team.
The post How to Use Threat Intelligence Feeds appeared first on ANY.RUN's Cybersecurity Blog.
Article Link: How to Use Threat Intelligence Feeds - ANY.RUN's Cybersecurity Blog