Security teams are being asked to protect a broader range of devices than ever before—IT, OT, IoT, ICS—many of which may not provide much in the way of visibility or monitoring for security risk. The situation gets even more difficult if you think about the number and complexity of components that go into those devices. There are few tools that provide visibility into hardware and firmware components, and certainly nothing to date that provides broad and continuous coverage for production assets.
A Security Engineer’s Toolbox for IT, OT, IoT Devices
Today, we’re announcing Eclypsium Toolbox, a framework for extending the Eclypsium supply chain security platform. Eclypsium is the industry’s first solution that provides organizations visibility into the components and subcomponents inside their IT infrastructure assets, but the ecosystem is incredibly complex and changes fast. As a result, there will inevitably be some devices and components that we don’t cover in our analysis, or use cases that we do not support. Toolbox will help with these situations, enabling security engineering teams to quickly support new requirements using the Eclypsium platform’s capabilities for data acquisition, our back-end orchestration, and reporting and presentation.
When it comes to how people will use Eclypsium Toolbox, we look forward to being surprised—we expect the unexpected! That said, here are some example use cases that might give you an idea of what is possible:
- Gather forensic data during incident response – Users can use Toolbox to run scripts on devices to gather forensic data for investigations such as running processes, executable files, configuration files, and user and system logs. This could include open-source tools built for this purpose, such as the Unix-like Artifacts Collector.
- Remediate vulnerabilities, ensure secure configurations, or quarantine systems – These are advanced use cases but potentially very valuable in that they enable automated responses to fix critical issues fast. For example, if the Eclypsium platform detects an implant in a system, then Toolbox would allow for a custom script to automatically quarantine the system (although if the customer has a SOAR in place, the quarantine workflow could be automated that way as well). Users can also run scripts to fix other issues, such as updating security configurations.
- Enrich analysis with threat intelligence – If an organization subscribes to proprietary threat intelligence feeds—from an industry-specific Information Sharing and Analysis Center (ISAC), for example—they will be able to check binaries gathered by Eclypsium against those STIX files for matching hashes and other indicators of compromise.
- Generate SBOMs – Eclypsium also generates SPDX-formatted BOMs for devices including hardware and firmware components, but with Toolbox users will be able to additionally send binaries to third-party tools such as cdxgen to generate SBOMs enriched with vulnerability data, etc.
- Analyze firmware on devices that Eclypsium doesn’t currently support – While we continue to expand our platform coverage, Eclypsium is focused on PCs, servers, and enterprise network appliances. Toolbox enables users to gather and analyze firmware binaries that are not currently supported—such as for ICS, OT, and IoT devices—leveraging third-party analyzers such as EMBA.
How It Works
Toolbox enables users to extend the Eclypsium platform’s data acquisition, analysis orchestration, and presentation and reporting capabilities. Note: We plan enhancements for orchestration and presentation in future releases.
- Data acquisition – One of the biggest challenges to monitoring the components of IT assets is the mechanism for acquiring the needed data. Toolbox enables users to use Eclypsium’s sensors to gather information from new components or devices, or run scripts for remediation or forensics.
- Analysis orchestration – Once data is acquired, Toolbox makes it possible to incorporate third-party tools and feeds to enrich data or produce new types of analysis. In future releases, we will add more capabilities to orchestrate analysis.
- Display – With Toolbox, users will be able to deliver reports through the Eclypsium platform. In future releases, we will add the ability to integrate this data with data in the Eclypsium platform for even more powerful visualizations in the user interface and reports.
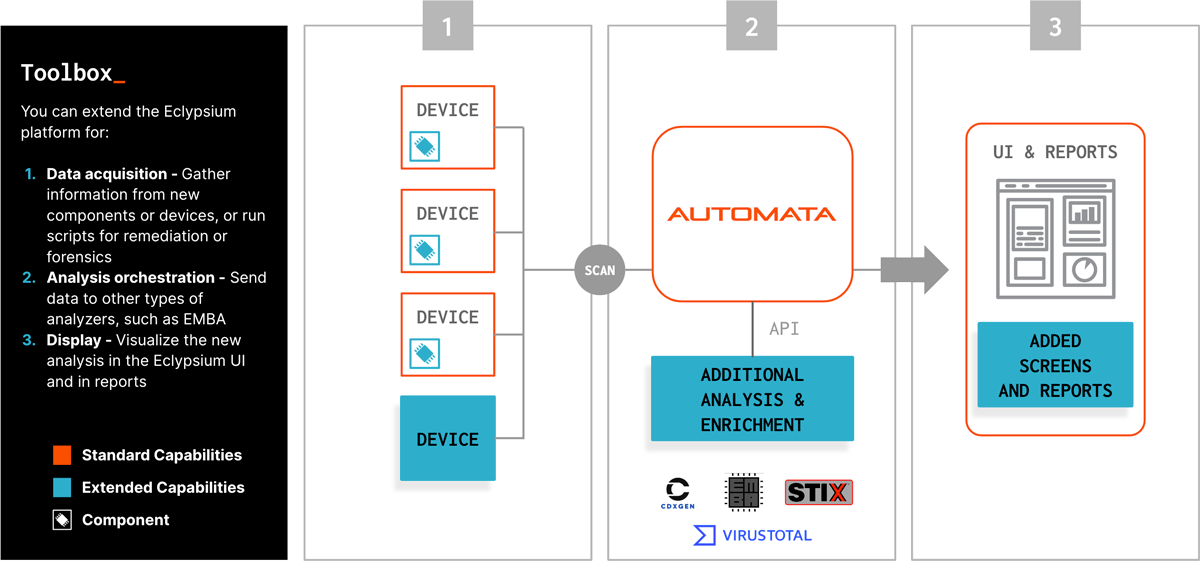 Eclypsium Toolbox makes it possible for users to extend the platform for new user cases.
Eclypsium Toolbox makes it possible for users to extend the platform for new user cases.We are excited to open the Eclypsium platform to our customers so they can solve new challenges related to IT infrastructure assets and components. Anything related to hardware and firmware components at scale and in production will likely be a candidate.
If you are an existing customer and have questions about Toolbox, please reach out to your customer success engineer. If you are not yet an Eclypsium customer and have a difficult-to-solve problem in this space, we’d love to chat.
Related resources
- Below-the-Surface Podcast: Supply Chains, Firmware, And Patching – Jason Kikta
- Blog: UEFIcanhazbufferoverflow: Widespread Impact from Vulnerability in Popular PC and Server Firmware
- White Paper: The Ultimate Guide to Supply Chain Security
The post Eclypsium Toolbox: Extending Supply Chain Security to New IT/OT/IoT Devices appeared first on Eclypsium | Supply Chain Security for the Modern Enterprise.