CVE-2024-4367 in PDF.js Allows JavaScript Execution, Potentially Affecting Millions of Websites: Update Now
Security experts identified a significant vulnerability in PDF.js, a widely used JavaScript library for displaying PDF documents in web browsers, which is actively maintained by Mozilla.
Aside from being an integral component of web browsers like Firefox, PDF.js is also distributed as a module on NPM (Node Package Manager) under the name pdfjs-dist, receiving nearly 2.8 million weekly downloads.
PDF.js (pdjs-dist) on NPM
Although a fixed version of PDF.js was released on May 14, 2024, along with Firefox and Thunderbird security advisories, technical details and a Proof-of-Concept (PoC) exploit of the vulnerability have only recently become available.
What is the CVE-2024-4367 vulnerability in PDF.js?
The vulnerability, identified as CVE-2024-4367, involves a missing type check when dealing with fonts in PDF.js. According to Mozilla’s advisory, this allows arbitrary JavaScript execution in the PDF.js context when a malicious PDF file is opened.
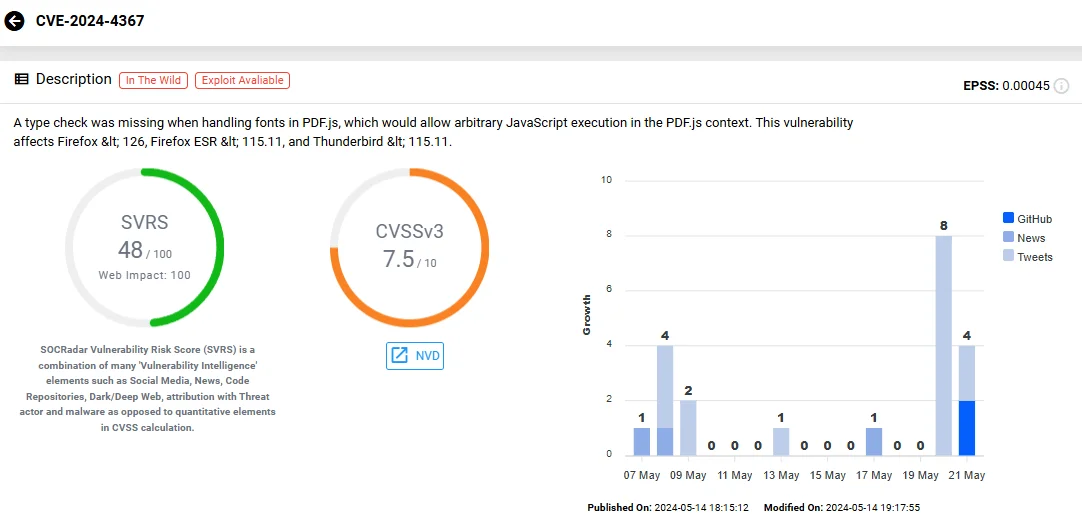
Vulnerability card of CVE-2024-4367 (SOCRadar Vulnerability Intelligence)
Thomas Rinsma from Codean Labs is credited with discovering and reporting the vulnerability.
How critical is CVE-2024-4367?
The CVE-2024-4367 vulnerability has yet to receive an official CVSS score from the NVD (National Vulnerability Database).
Mozilla’s security advisories classify this vulnerability as ‘high impact’. It poses a serious risk because it could allow attackers to execute arbitrary code on a victim’s system through manipulated PDF files.
Exploitation of CVE-2024-4367
The vulnerability identified as CVE-2024-4367 in PDF.js does not stem from the PDF format’s scripting features but rather from an oversight within the font rendering mechanisms. Specifically, the issue arises in how PDF.js handles certain font formats and the subsequent rendering of glyphs, or characters.
It is mentioned that for contemporary font formats like TrueType, PDF.js relies on the browser’s native font renderer. However, for other types, it must manually render each glyph. To enhance performance, a path generator function for each glyph is pre-compiled. This compilation, under certain conditions, involves creating a JavaScript Function object with a series of rendering instructions.
The vulnerability surfaces when these rendering instructions, which are supposed to be benign commands to shape a glyph, can be manipulated. If an attacker modifies these commands by inserting malicious code, the code will execute when the glyph is rendered. This manipulation is facilitated through the compileGlyph method, where commands like ‘save’, ‘transform’, ‘scale’, and ‘restore’ are initialized.
Notably, the ‘transform’ command, which uses a fontMatrix supposed to contain numeric values, can be hijacked by embedding a custom FontMatrix in the PDF’s metadata, allowing arbitrary JavaScript code to be inserted and executed.
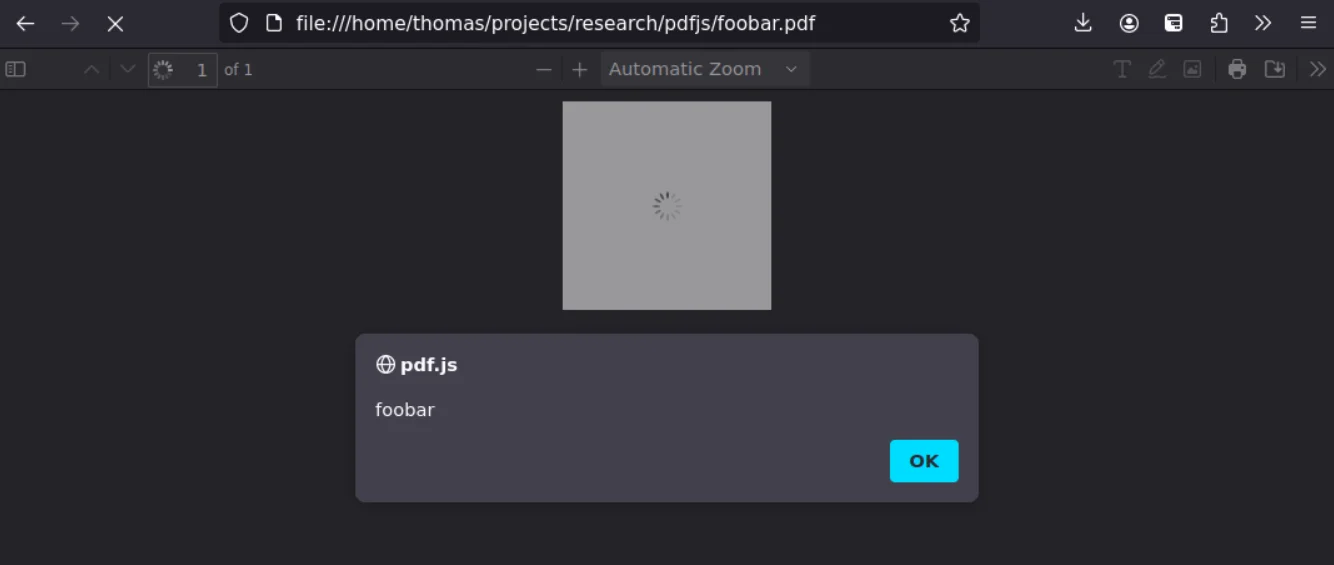
CVE-2024-4367 exploited to trigger an alert (CodeanLabs)
According to researchers, in environments where PDF.js is embedded without adequate security measures, this vulnerability could enable Cross-site Scripting (XSS) attacks, data breaches, unauthorized actions, or even full account takeovers.
Track updates on known vulnerabilities, including exploits, repositories, and emerging hacker trends with the Vulnerability Intelligence feature. Gain insights that assist your organization in improving vulnerability management and prioritization, ultimately protecting against potential breaches.
Hacker trends and latest CVEs (SOCRadar Vulnerability Intelligence)
Which Firefox versions are affected by CVE-2024-4367?
The CVE-2024-4367 vulnerability impacts all versions of Firefox prior to version 126 due to its integral use of PDF.js for displaying PDF files within the browser. Moreover, the implications of this vulnerability extend beyond just Firefox, affecting a myriad of web and Electron-based applications that incorporate PDF.js for PDF preview functionality.
Verifying the version of PDF.js being used is critical for developers and organizations that utilize JavaScript or TypeScript-based applications that handle PDF files.
How to mitigate CVE-2024-4367?
To fully address the vulnerability, it is advised to update PDF.js to version 4.2.67 or higher.
Applications that fail to update to a secured version of PDF.js risk exposing themselves and their users to potential security breaches. This vulnerability can be exploited to perform malicious actions, ranging from data theft to complete system compromise, particularly in applications that lack proper sandboxing or security constraints.
Developers should act swiftly to assess their use of PDF.js and update to the latest, patched version as provided in the recent security releases. By doing so, they can safeguard their applications against the exploits enabled by CVE-2024-4367 and ensure a secure user experience.
As a workaround, PDF.js users can disable the vulnerable code path by setting ‘isEvalSupported’ to ‘false’.
Secure your systems and protect your data by staying current on cybersecurity developments and responding quickly to emerging vulnerabilities. SOCRadar’s Attack Surface Management (ASM) module helps you stay ahead of security vulnerabilities and exploitation by continuously monitoring your digital assets, delivering timely alerts about threats, and enabling you to take proactive measures to protect your digital assets effectively.
Monitor company vulnerabilities and digital assets via SOCRadar’s ASM module. Sign up now for the Free Edition to try out the platform’s features.
