On March 29th, 2024, a backdoor in a popular package called XZ Utils was announced on the Openwall mailing list. This utility includes a library called liblzma which is used by SSHD, a critical part of the Internet infrastructure used for remote access. When loaded, the CVE-2024-3094 affects the authentication of SSHD potentially allowing intruders access regardless of the method.
Affected versions: 5.6.0, 5.6.1
Affected Distributions: Fedora 41, Fedora Rawhide
*At the time of this writing
Background
A malicious threat actor was able to commit code to the XZ Utils Github repository on February 23, 2024 which included obfuscated malicious code that altered the build process. The altered build process then included the malicious file during compilation of the liblzma library, At no point was the malicious code in cleartext making it difficult to detect. A primary target of this attack is Linux distributions, as they will include the compiled version of the liblzma library which SSHD uses while also spread it to many users.
Once SSHD loads the now malicious library, the authentication flow is redirected during the RSA key checking. With control over the authentication flow, the library can grant access based on the criteria set by the attacker. This is most likely their RSA keys or some other data which only the attacker knows. None of the password or PKI based authentication would be effective at this point.
Detection
This malicious library can be detected by Vulnerability Management solutions which look for the affected packages installed. CVE-2024-3094 can also be detected at runtime using Falco or the Sysdig Secure CNAPP Platform. For runtime detection, one way to go about it is to watch for the loading of the malicious library by SSHD. These shared libraries often include the version in their filename. In the example below, here is what is loaded by SSHD in a test system.
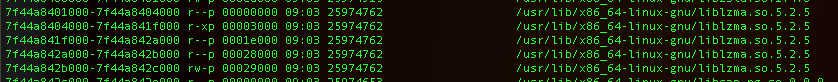
SSHD is a daemon which is executed at startup, this can make detection tricky sometimes if the detection agent doesn’t load in time. However, when a user logs in with SSH a new SSHD process is spawned which also loads the affected libraries. This gives us two places where we can detect the loading of the shared library. Below is a Falco rule demonstrating how to do exactly that.
For Sysdig Secure users, this rule is called “Backdoored library loaded into SSHD (CVE-2024-3094)” and can be found in the Sysdig Runtime Threat Detection policy.
- rule: Backdoored library loaded into SSHD (CVE-2024-3094)
desc: A version of the liblzma library was seen loading which was backdoored by a malicious user in order to bypass SSHD authentication.
condition: open_read_new and proc.name=sshd and (fd.name endswith "liblzma.so.5.6.0" or fd.name endswith "liblzma.so.5.6.1")
output: SSHD Loaded a vulnerable library (| file=%fd.name | proc.pname=%proc.pname gparent=%proc.aname[2] ggparent=%proc.aname[3] gggparent=%proc.aname[4] image=%container.image.repository | proc.cmdline=%proc.cmdline | container.name=%container.name | proc.cwd=%proc.cwd proc.pcmdline=%proc.pcmdline user.name=%user.name user.loginuid=%user.loginuid user.uid=%user.uid user.loginname=%user.loginname image=%container.image.repository | container.id=%container.id | container_name=%container.name| proc.cwd=%proc.cwd )
priority: WARNING
tags: [host,container]Code language: JavaScript (javascript)Secure your cloud today with end-to-end detection
At the heart of Sysdig Secure lies Falco’s unified detection engine. This cutting‑edge engine leverages real‑time behavioral insights and threat intelligence to continuously monitor the multi‑layered infrastructure, identifying potential security breaches. Whether it’s anomalous container activities, unauthorized access attempts, supply chain vulnerabilities, or identity‑based threats, Sysdig ensures that organizations have a unified and proactive defense against evolving threats.
Dig deeper into how Sysdig provides continuous cloud security across AWS, GCP, and Azure.
Conclusion
Supply chain attacks are becoming increasingly common. As we saw in this attack against SSHD, the code made it past reviews and approvals. It was obfuscated in a way that didn’t raise any concerns. This is one of the drawbacks when it comes to relying on statically scanning source code. Runtime threat detection becomes a critical part of ensuring all of the components in your supply chain are operating as expected. It was very fortunate that the malicious library didn’t make it even into more distributions before it was caught.
The post CVE-2024-3094: Detecting the SSHD backdoor in XZ Utils appeared first on Sysdig.
Article Link: CVE-2024-3094: Detecting the SSHD backdoor in XZ Utils – Sysdig