APT28 Deploys ‘GooseEgg’ in Attacks Exploiting the Windows Print Spooler Vulnerability, CVE-2022-38028
Microsoft recently shed light on a campaign orchestrated by the Russian-based threat actor Forest Blizzard, employing a custom tool named ‘GooseEgg’ to escalate privileges and pilfer credentials from networks.
Of significant concern, the threat actors exploit the CVE-2022-38028 vulnerability present in the Windows Print Spooler service. CISA, acknowledging its exploitation, promptly added the vulnerability to its Known Exploited Vulnerabilities (KEV) Catalog on April 23, 2024.
In an alert, the agency stressed the prevalence of such privilege escalation vulnerabilities as common attack vectors. Urging organizations to prioritize patching, CISA set a deadline of May 14, 2024 for Federal Civilian Executive Branch (FCEB) entities to address the vulnerability.
What is GooseEgg?
Since at least June 2020, and potentially as early as April 2019, Forest Blizzard has leveraged a tool, identified by Microsoft as GooseEgg, to exploit the CVE-2022-38028 vulnerability within the Windows Print Spooler service.
This exploit involves the modification of a JavaScript constraints file, subsequently executed with SYSTEM-level permissions.
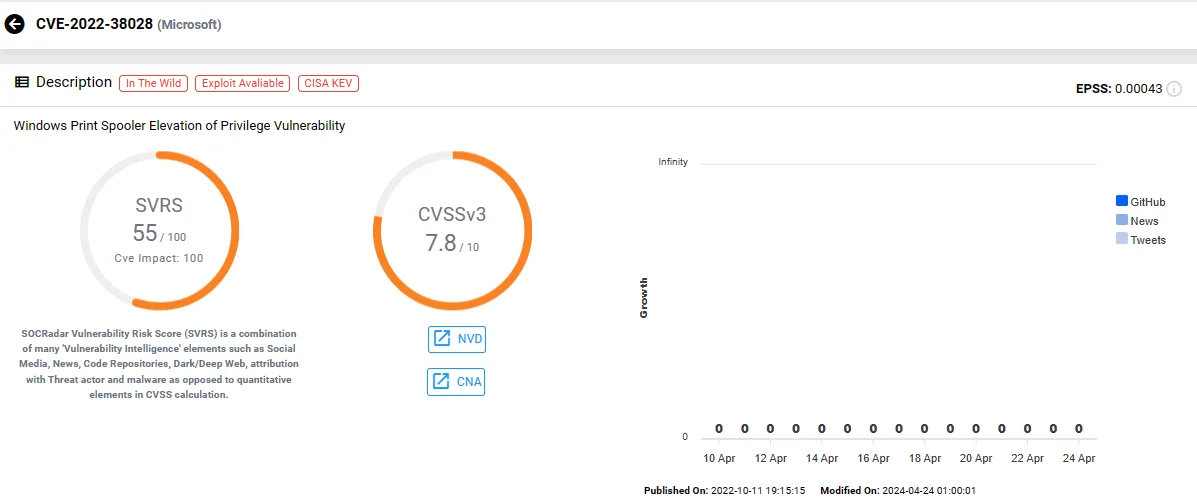
Vulnerability card of CVE-2022-38028 on SOCRadar
Forest Blizzard has wielded GooseEgg as part of post-compromise activities targeting various entities, including governmental, non-governmental, educational, and transportation organizations across Ukraine, Western Europe, and North America.
GooseEgg has the ability to launch additional applications that are specified via the command line with elevated permissions. It also gives threat actors the ability to install backdoors, run remote code, and navigate compromised networks laterally.
The widespread popularity of Microsoft products makes them prime targets for threat actors. With millions of users globally, these products offer a broad attack surface, attracting malicious actors who continuously exploit vulnerabilities. As a result, threat actors capitalize on the extensive usage of Microsoft software to their advantage, consistently discovering and targeting vulnerabilities to compromise systems and networks.
Utilize SOCRadar’s Attack Surface Management (ASM) module to stay informed about emerging security vulnerabilities and receive timely alerts regarding threats to your digital assets.
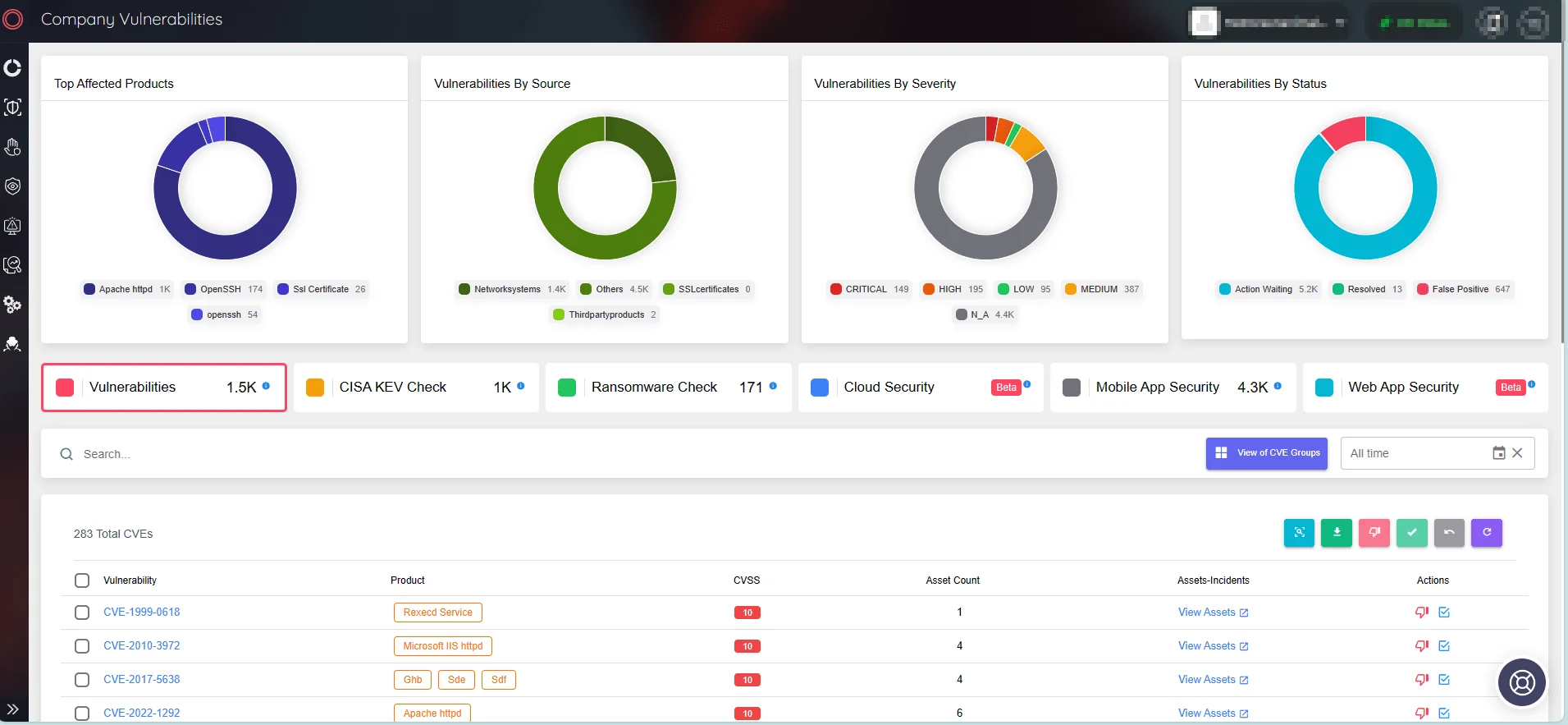
SOCRadar’s Attack Surface Management, Company Vulnerabilities
The Attack Scheme: How Do Attackers Deploy GooseEgg?
Microsoft Threat Intelligence has determined Forest Blizzard’s objective in deploying GooseEgg as gaining elevated access to target systems and stealing credentials and information.
Upon accessing a target device, Forest Blizzard deploys GooseEgg with a batch script, named execute[.]bat and doit[.]bat, which generates the servtask[.]bat file. This file contains commands for saving and compressing registry hives and activates the paired GooseEgg executable to establish persistence through a scheduled task running servtask[.]bat.
The GooseEgg binary, labeled justice[.]exe and DefragmentSrv[.]exe, executes four commands with different run paths to conceal its activity. It triggers exploits and launches malicious components like the “wayzgoose” DLL, embedded within installation subdirectories under ‘C:ProgramData’, including Microsoft, Adobe, Comms, Intel, Kaspersky Lab, Bitdefender, ESET, NVIDIA, UbiSoft, and Steam.
Furthermore, the exploit creates registry keys, custom protocol handlers, and new CLSIDs, redirecting the PrintSpooler to the actor-controlled directory.
The “MPDW-constraints[.]js” within this directory is patched to invoke the “rogue” search protocol handler’s CLSID, leading to the launch of wayzgoose[.]dll within the PrintSpooler service. This auxiliary DLL is capable of performing malicious activities with SYSTEM-level permissions, such as installing backdoors, lateral movement within networks, and remote code execution.
Who is Forest Blizzard?
Forest Blizzard, also known as APT28, Fancy Bear, STRONTIUM, Sednit, and Unit 26165, is linked to the Russian General Staff Main Intelligence Directorate (GRU) and primarily targets strategic intelligence objectives.
Since at least 2010, Forest Blizzard has focused on gathering intelligence in support of Russian foreign policy goals, targeting government, energy, transportation, and non-governmental organizations in the United States, Europe, and the Middle East. Additionally, it has been observed targeting media, IT, sports, and educational institutions globally.
SOCRadar monitors all identified threat actors and malware to provide the most recent insights. With the Cyber Threat Intelligence module’s Threat Actor/Malware page, users can search for particular threats and access the latest updates, including news and mentions, targeted countries, associated vulnerabilities, threat actors, malware, and indicators of compromise.
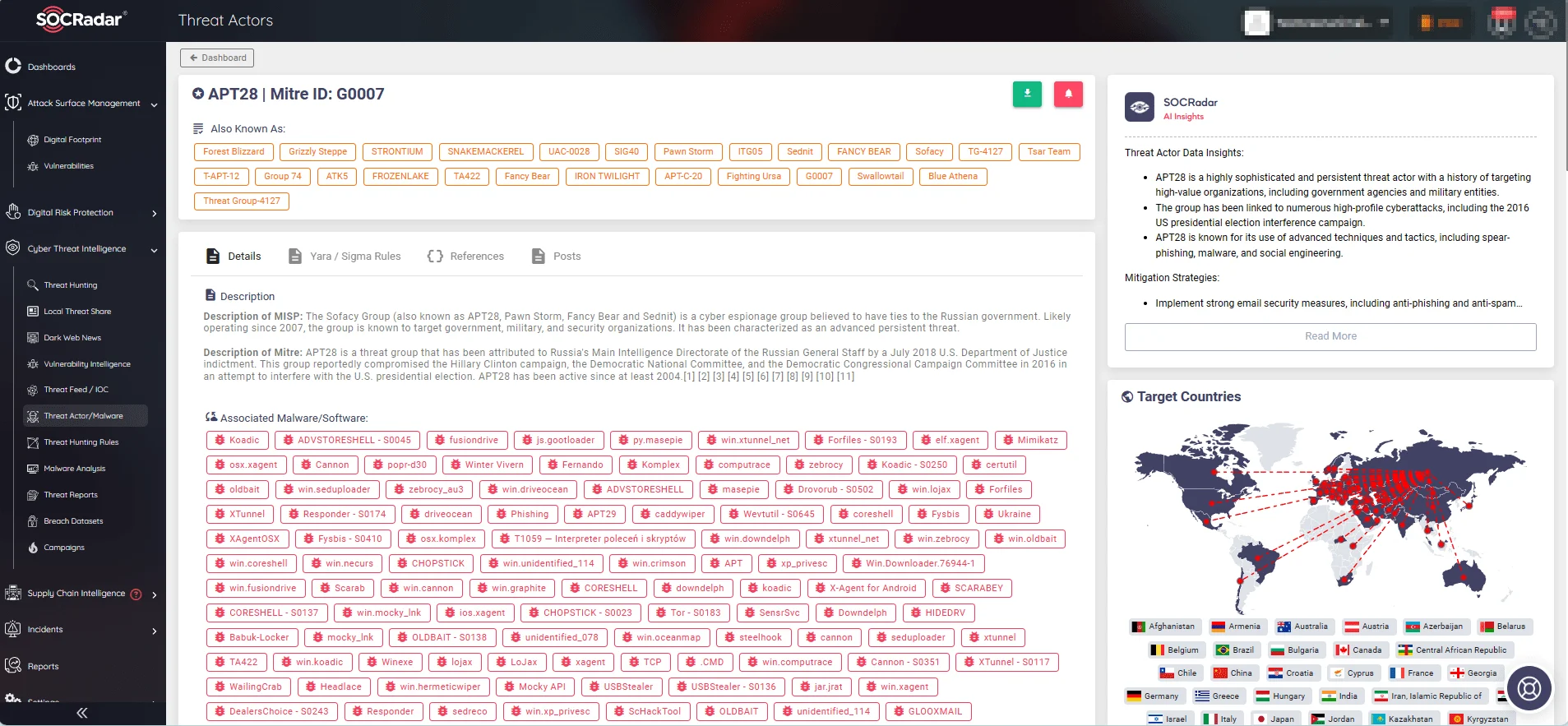
APT28 profile on SOCRadar’s CTI module, Threat Actor/Malware page
Forest Blizzard has been observed employing other publicly available exploits alongside CVE-2022-38028, such as CVE-2023-23397 (Microsoft Outlook Elevation of Privilege Vulnerability).
While various Russian threat actors have previously exploited similar vulnerabilities (such as PrintNightmare vulnerabilities), the use of GooseEgg in Forest Blizzard operations is a novel discovery not previously reported by security providers, as cited by Microsoft.
About the PrintNightmare Vulnerabilities
The name “PrintNightmare” refers to critical vulnerabilities (CVE-2021-34527 and CVE-2021-1675) within the Windows Print Spooler service, enabling remote code execution with elevated privileges.
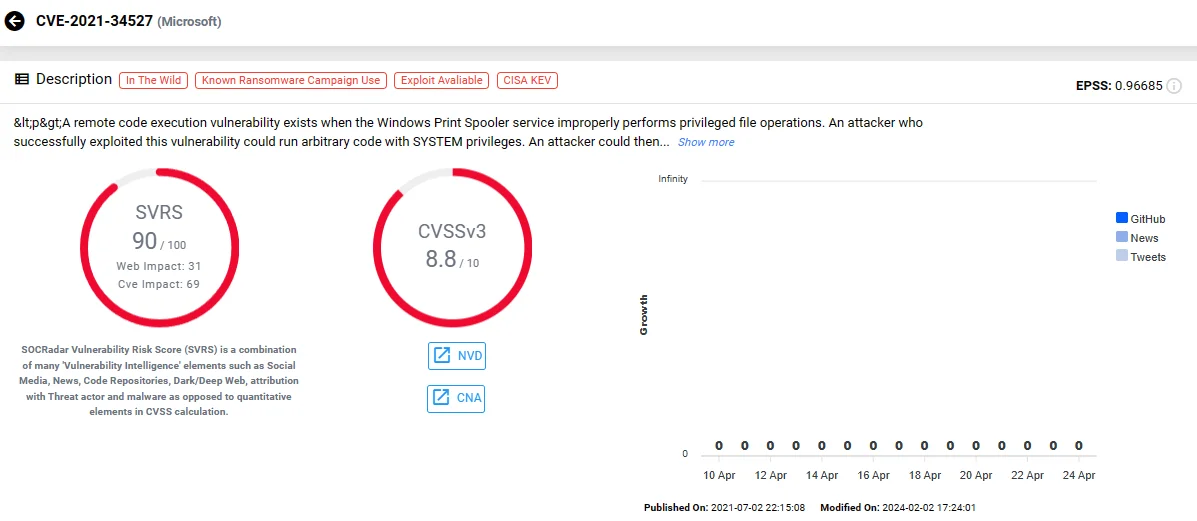
Vulnerability card of CVE-2021-34527 on SOCRadar
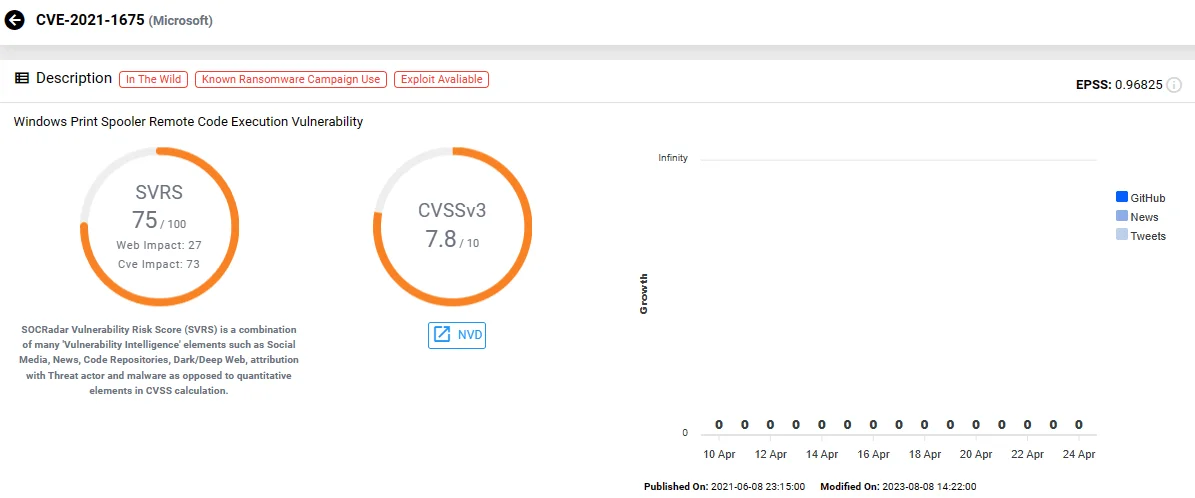
Vulnerability card of CVE-2021-1675 on SOCRadar
Exploitation of these flaws, disclosed in June and July 2021, leads to malware installation or the creation of new user accounts with full privileges.
Beyond GRU actors, ransomware organizations such as Vice Society and Magniber also took advantage of PrintNightmare vulnerabilities, indicating a persistent weakness in the Print Spooler service.
SOCRadar’s Vulnerability Intelligence provides real-time monitoring of CVE and exploitation trends. Utilize its extensive capabilities and advanced analytics to track updates, detect exploits, and gain actionable insights for proactive vulnerability management.
SOCRadar’s Vulnerability Intelligence, CVE trends
How to protect against GooseEgg attacks?
Microsoft recommends protecting against GooseEgg attacks by installing security updates for the Print Spooler vulnerability.
Additionally, organizations should address the PrintNightmare vulnerabilities (CVE-2021-1675, CVE-2021-34527) and harden credentials to enhance security against exploitation.
Indicators of Compromise
The following are the indicators of compromise associated with APT28’s use of CVE-2022-38028 and deployment of GooseEgg as provided by MS Threat Intelligence:
Batch script artifacts:
- execute[.]bat
- doit[.]bat
- servtask[.]bat
- 7d51e5cc51c43da5deae5fbc2dce9b85c0656c465bb25ab6bd063a503c1806a9
GooseEgg artifacts:
- justice[.]pdb
- wayzgoose[.]pdb
SHA256 hashes:
- c60ead92cd376b689d1b4450f2578b36ea0bf64f3963cfa5546279fa4424c2a5 (DefragmentSrv[.]exe)
- 6b311c0a977d21e772ac4e99762234da852bbf84293386fbe78622a96c0b052f (justice[.]exe)
- 41a9784f8787ed86f1e5d20f9895059dac7a030d8d6e426b9ddcaf547c3393aa (wayzgoose[%n].dll)
