Exploit Title: XAMPP 1.7.0 Reflected Cross-Site Scripting
Date: 14 June 2019
Vendor Homepage: https://www.apachefriends.org/index.html
Version: 1.7.0
CVE: CVE-2019-8920
Description:
What is cross-site scripting (XSS)?
Cross-site scripting (also known as XSS) is a web application vulnerability that allows an attacker to compromise the interaction of users with a vulnerable web application. Typically on exploiting an XSS vulnerability the attacker masquerades itself as the victim user and gains access to all the data and privileges of the victim. If the victim user has privileged access within the application, then the attacker might be able to gain full control over all of the application's functionality and data.
How does XSS work?
Cross-site scripting works by manipulating a vulnerable web site so that it returns malicious JavaScript to users. When the malicious code executes inside a victim's browser, the attacker can fully compromise their interaction with the application.
Reference: https://portswigger.net/web-security/cross-site-scripting
There are three major types of XSS attacks.
- Reflected XSS, where the malicious script comes from the current HTTP request.
- Stored XSS, where the malicious script comes from the website's database.
- DOM-based XSS, where the vulnerability exists in client-side code rather than server-side code
In this post, we will be focusing on Reflected XSS.
Reflected XSS is the most basic among the three and is quite trivial to perform. Typically in a Reflected XSS vulnerable Web Application the URL received in the backend is not sanitized which allows an attacker to insert javascript payload in the request and then returned as the response body simply executes the payload. This leads to Reflected Cross-Site Scripting vulnerability. It helps the attacker to exploit mostly the client side risks which include phishing, temporary deface, browser key-logger among others. Exploitation frameworks like BeEF ease the offensive attack.
Now, let us look at the steps of exploitation for the attack.
Proof-of-concept:
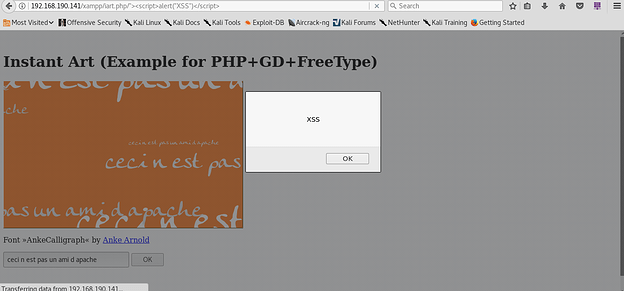
- Go to the following http://domain.com/xampp/iart.php
- Append the following string to the above URL: ”abcd><script>alert(“XSS”)</script>xyzj
- Click the “Enter” button
- You’ll see a Javascript popup box showing your domain
Criticality Assessment
An attacker can use XSS to send a malicious script to an unsuspecting user. The end user’s browser has no way to know that the script should not be trusted, and will execute the script. Because it thinks the script came from a trusted source, the malicious script can access any cookies, session tokens, or other sensitive information retained by the browser and used with that site. These scripts can even rewrite the content of the HTML page.
Tools:
Firefox ESR 52.7.3 (64 Bit)
Attachments:
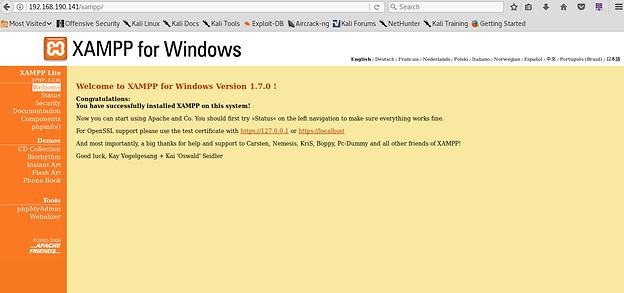
Exhibit 1, shows the version details of the XAMPP that was tested
Exhibit 1
Exhibit 2, shows that the malformed URL makes the application vulnerable to Reflected XSS.
Exhibit 2
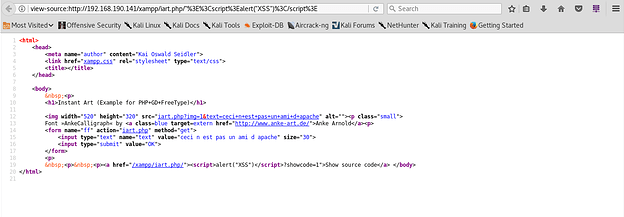
Exhibit 3, shows the response body of the server after receiving the malformed URL.
Exhibit 3
Article Link: https://blog.lucideus.com/2019/07/xampp-170-reflected-cross-site-scripting.html