WordPress 5.6, the final major release planned for 2020, came out today, on December 8, 2020. It includes a few major features and updates, as well as a huge number of minor enhancements and bug fixes. A few changes have immediate implications for security and compatibility which we’ve highlighted in this post for WordPress users.
Application Passwords add functionality, and risk
WordPress 5.6 will come with a new feature that allows external applications to request permission to connect to a site and generate a password specific to that application. Once the application has been granted access, it can perform actions on behalf of a user via the WordPress REST API.
Unfortunately, socially engineering a site administrator into granting application passwords to a malicious application is trivial. An attacker could trick a site owner into clicking a link requesting an application password, naming their malicious application whatever they wanted:

Worse yet, the application password request URLs are set up to send the newly generated password to the requester’s site via a redirect URL. Since application passwords function with the permissions of the user that generated them, an attacker could use this to gain control of a website. We demonstrated how an attacker could use a social engineering attack using application passwords on Wordfence Live.
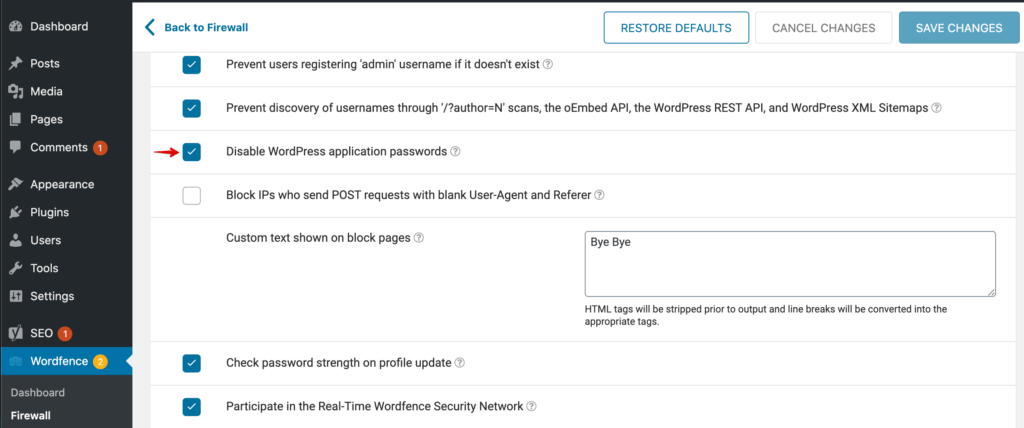
For this reason, the latest version of Wordfence, 7.4.14, disables application passwords by default. If you have a specific use case for application passwords and would like to re-enable application passwords, you can do so under Wordfence->Firewall->Manage Brute Force Protection:
Despite the risk, application passwords are likely to offer some utility in the future. Some examples of how they could be used include publishing posts to a WordPress site from other interfaces, accessing or updating data in the WordPress database, or even creating users.
This functionality is, on the surface, similar to XML-RPC, but the REST API offers significantly broader capabilities. Additionally, application passwords are securely generated and are 24 characters long, so brute force and credential stuffing attacks are unlikely to be successful.
If you decide to make use of application passwords, we strongly recommend setting up a user with minimal permissions, ideally with only the necessary capabilities specifically for the application you wish to connect to.
The jQuery update continues
WordPress 5.5, released in August 2020, removed the jQuery Migrate script. This caused many sites using plugins dependent upon older versions of jQuery to experience issues.
If your site was affected and you’re currently using the Enable jQuery Migrate Helper plugin to work around these issues, you’ll want to make sure your site works without it before updating to WordPress 5.6.
This is because WordPress 5.6 will update to the latest version of jQuery and add jQuery Migrate 3.3.2, which can conflict with the version re-enabled by the Enable jQuery Migrate Helper plugin, which is jQuery Migrate 1.4.1.
WordPress has been using outdated versions of the jQuery library for several years now.
WordPress 5.6 is step 2 of a 3-step plan to get WordPress on an up-to-date version of jQuery. This plan has been:
- WordPress 5.5: Remove the jQuery Migrate 1.x script. (August 2020)
- WordPress 5.6: Update to the latest jQuery, jQuery UI, and jQuery Migrate scripts. (December 2020)
- WordPress 5.7: Remove the jQuery Migrate script. (March 2021)
Because of this timeline, jQuery compatibility is actually significantly more urgent than PHP 8.0 compatibility. Plugin and theme developers should use the next few months before the release of WordPress 5.7 to completely transition their code to be compatible with the latest version of jQuery without the assistance of jQuery Migrate.
Although security fixes have been backported into the versions of jQuery used by previous versions of WordPress, many tools, such as Google’s Lighthouse, have reported that WordPress sites were vulnerable due to running an older version of jQuery. One bit of good news is that these site auditing tools should no longer show WordPress 5.6 sites as being vulnerable.
WPTavern has an excellent article that goes into more detail about the situation.
PHP 8 Compatibility
WordPress 5.6 is intended to be “beta compatible” with PHP 8. This means that during normal usage, a site running WordPress 5.6 on PHP 8 with a default theme and no plugins will be unlikely to run into any problems. Our previous article dives into some of the challenges plugin authors will face when it comes to compatibility with PHP 8.
If you’re a typical WordPress site owner using a fair number of plugins, it may be some time before it’s safe to update to PHP 8. On the other hand, if you’re creating a brand new site from scratch, you’ll be able to get ahead of many issues by starting with the latest version of PHP and WordPress.
Automatic major version updates
We’ve discussed automatic updates in the past, and how they can be essential for some use cases and potentially catastrophic for others. Currently, WordPress core automatically applies minor updates, which are typically much safer than automatic plugin updates due to extensive testing.
Starting with WordPress 5.6, all new WordPress installations will receive automatic updates for major versions. This means that if you create a fresh WordPress site with WordPress 5.6, it will automatically be updated to WordPress 5.7 when it comes out. While this has a higher likelihood of causing issues, bear in mind that the most likely problems will be with incompatible plugins, which will be much less prevalent on brand new sites.
Existing sites that have updated to WordPress 5.6 from previous versions will retain the current behavior of automatically updating only for minor versions and security patches, so current site owners do not have to worry about this. If desired, a current site owner can now opt in to automatic major version updates and even Beta and RC releases.
A brand new theme
Since 5.6 is the final major version of WordPress to be released for 2020, it includes a new default theme for next year, titled Twenty Twenty-One. Like previous default WordPress themes, it is based on an existing theme, Seedlet, and is fairly minimal, though it does include support for Dark Mode.
Conclusion
WordPress 5.6 includes a number of changes, improvements, and bug fixes, including many we haven’t covered. We’ve focused on the items we feel are most relevant to our users and most likely to cause issues. As with all major updates to WordPress, whether or not you wish to update right away will depend on your use case. There are a number of promising new features as well as some potential for growing pains, but these will be applicable to developers rather than users.
Special thanks to QA Lead Matt Rusnak and Threat Analyst Chloe Chamberland for their findings and assistance with this article.
The post WordPress 5.6 Introduces a New Risk to Your Site: What to Do appeared first on Wordfence.
Article Link: https://www.wordfence.com/blog/2020/12/wordpress-5-6-introduces-a-new-risk-to-your-site-what-to-do/