The browser has become one of the most vulnerable and frequently targeted attack vectors for businesses.
Browser-based attacks—Web skimming, Cryptocurrency Miners, Fingerprinters, and Waterholing (including exploitation) encounters—are responsible for some of the most high-profile breaches in recent history, such as the hack of British Airways.
Given the frequency by which RiskIQ researchers now encounter these attacks, they should be taken just as seriously by businesses as threat mainstays like phishing and ransomware. When it comes to browser-based attack vectors, RiskIQ researchers encounter them in a variety of flavors.
Browser-based attacks are poised to carve out a significant portion of the threat landscape for years to come, so it’s essential to understand what makes them tick. And the first step to doing so is understanding what they all have in common: malicious injects.
Browser-based threats need malicious injects to execute their code, so that is where all these attacks begin. With RiskIQ telemetry data, we determined the six most common and interesting injection techniques that lead to these browser threats:
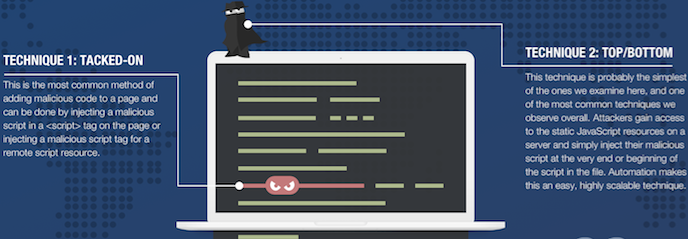
1. Tacked-on
2. Top/Bottom
3. Supply Chain
4. Executable Scope
5. Function Inlining
6. RFC Edge Cases
For a high-level, illustrated look at these six injection techniques or comprehensive analysis of each, download the infographic or full report here.
Tackle Browser Threats
Going forward, combating browser threats will be one of the most critical security endeavors organizations undertake. Having visibility into your web-facing assets will be vital to detecting these malicious injects.
A key feature of RiskIQ’s integrated digital threat platform is our worldwide network of web crawlers that continuously crawl the internet, collecting not just rendered pages but also the entire sequence of requests and responses that make up a web page—headers, dependent requests, certificates, and more. These crawls give our customers insight into what’s happening on a web server at any given point in time, and how that server would interact with a real user.
Earlier this year we added the ability to detect any changes in the JavaScript that are rendered in the user’s browser, generating an alert event when such changes occur. In this way, RiskIQ browsers act as the first victim, allowing the compromised page to be remediated quickly.
Through these capabilities, RiskIQ allows customers to defend themselves from this whole class of browser-based attacks.
The post What’s in a Browser Threat? Malicious Injects Are Redefining the Threat Landscape appeared first on RiskIQ.
Article Link: https://www.riskiq.com/blog/external-threat-management/browser-threat-malicious-injects/